Prisma SD-WAN
Configure the AWS Transit Gateway Integration
Table of Contents
Expand All
|
Collapse All
Prisma SD-WAN Docs
-
-
- Prisma SD-WAN Controller
-
- CloudBlade Integrations
- CloudBlades Integration with Prisma Access
-
-
-
-
- 6.5
- 6.4
- 6.3
- 6.1
- 5.6
- Prisma SD-WAN Controller
- Prisma SD-WAN On-Premises Controller
- Prisma SD-WAN CloudBlades
- Prisma Access CloudBlade Cloud Managed
- Prisma Access CloudBlade Panorama Managed
Configure the AWS Transit Gateway Integration
Learn how to configure the AWS transit gateway cloudBlade and Prisma
SD-WAN
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
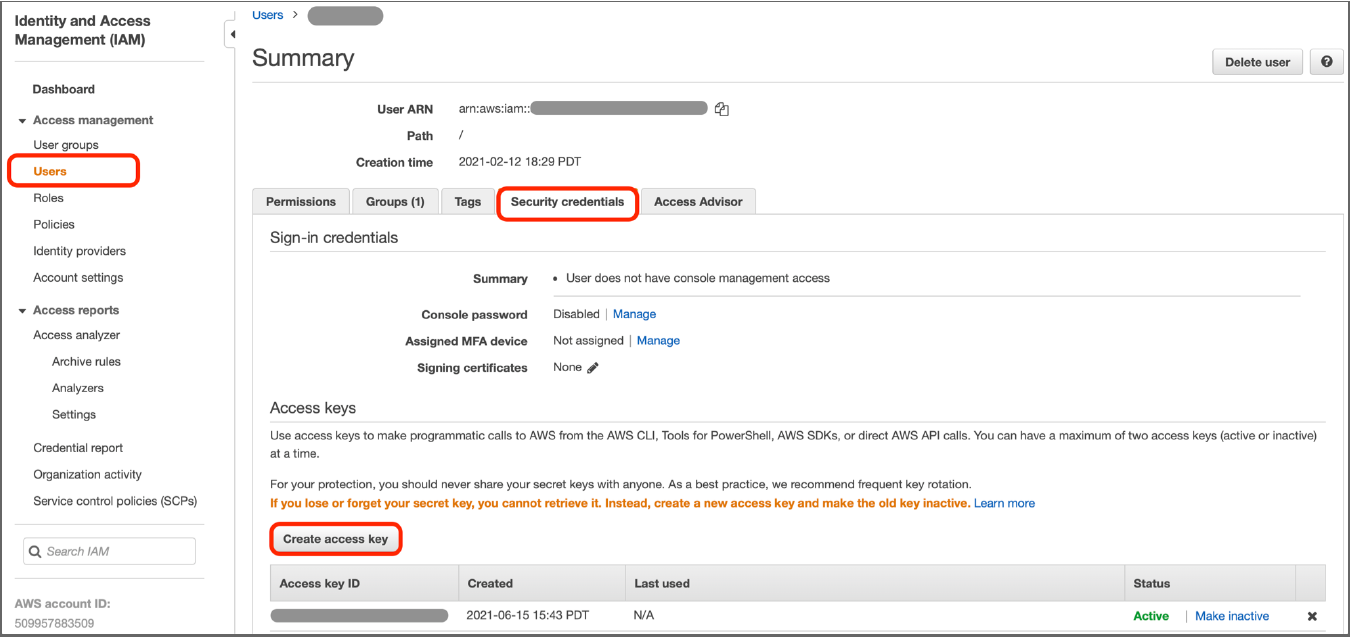
To configure the AWS Transit Gateway Integration CloudBlade, retrieve the following
information from your AWS account:
- Generate AWS Access key ID and secret access key.
![]() The AWS Transit Gateway CloudBlade adds a CIDR block in one of the fields. Ensure that the CIDR block does not overlap with the VPC CIDR.
The AWS Transit Gateway CloudBlade adds a CIDR block in one of the fields. Ensure that the CIDR block does not overlap with the VPC CIDR.![]()
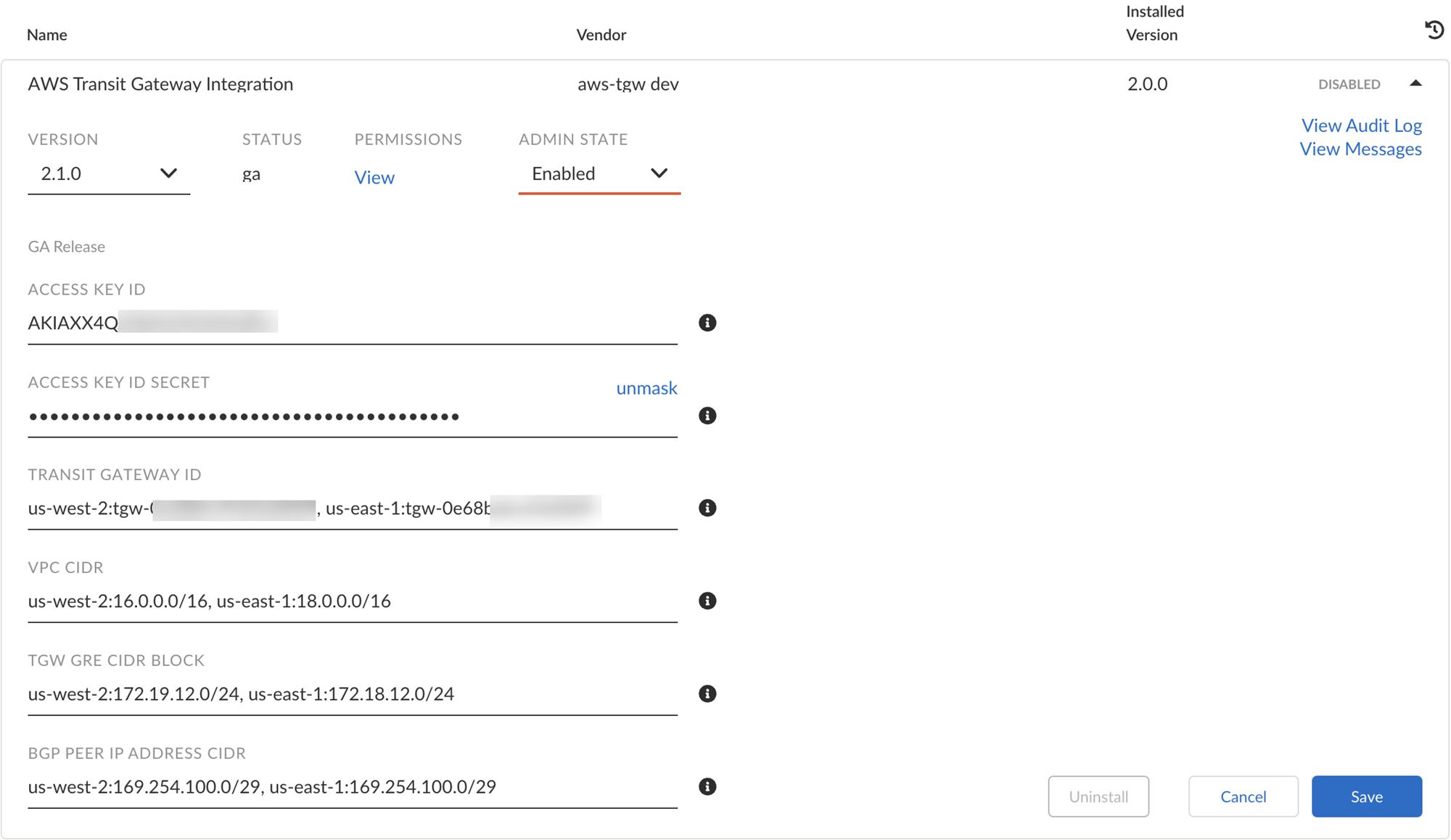
Configure and Install the AWS Transit Gateway Integration CloudBlade
- Go to Strata Cloud ManagerConfigurationPrisma SD-WANCloudBlades.Locate the AWS Transit Gateway CloudBlade and click Configure.If this CloudBlade does not appear in the list, contact the Palo Alto Support team.Provide the AWS Access Key ID and the Access Key ID Secret retrieved from the previous step.Provide the Transit Gateway ID in the format Region:TGW-ID.Only one region must be mapped to one TGW ID. Multiple TGW entries can be populated in a comma separated format.Provide a VPC CIDR block in the format <AWS Region:VPC_CIDR> for region based CIDRs and <CIDR> for global CIDRs for all regions in the TGW field.The VPC CIDR block must have a subnet mask between /16 and /26. Four distinct subnets are carved out for the public and private subnets on each vION. This should be in the RFC 1918 address space. The same VPC CIDR is reused on all regions in multi-region deployments.Provide the TGW GRE CIDR Block in the format <AWS Region:GRE_CIDR> for region based CIDRs and <CIDR> for global CIDRs for all regions in the TGW field.The TGW GRE Tunnel CIDR block must not overlap the VPC CIDR block. The GRE CIDR block can have any one of the following subnet masks /8, /16, or /24. The same VPC CIDR is reused on all regions in multi-region deployments.Provide the BGP Peer IP Address CIDR in the format <AWS Region:BGP_CIDR> for region based CIDRs or <CIDR> for global CIDRs for all regions in the TGW field. Allocate a /29 IP subnet for the GRE tunnel interface on both the ends.This address block can also be used for establishing core peering from both the Data Center virtual IONs with the Transit Gateway’s connect peers. The CIDR block has to be in the “169.254.x.x/29” subnet as required by AWS. Only one /29 prefix is needed, the CloudBlade uses this as a base and increments as many /29 subnets required based on the number of regions deployed.
![]() Ensure at least 2 licenses are available to deploy both v7108 IONs, for each region you wish to deploy the Data Center site.Select Install once all fields in the CloudBlade configuration is populated.
Ensure at least 2 licenses are available to deploy both v7108 IONs, for each region you wish to deploy the Data Center site.Select Install once all fields in the CloudBlade configuration is populated.