Prisma Access
Integrate a Shared Desktop VDI with Prisma Access Using Terminal Server
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Integrate a Shared Desktop VDI with Prisma Access Using Terminal Server
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Virtual Desktop Infrastructure (VDI) is a
technology that uses virtual machines to provision and manage virtual
desktops. VDI deploys desktop environments using a managed server
and deploys them to end-users on request. End-users access the resources
they need, such as public apps and resources that are internet-based
or private apps and resources available from an FTP connection,
from their provisioned VDI desktops.
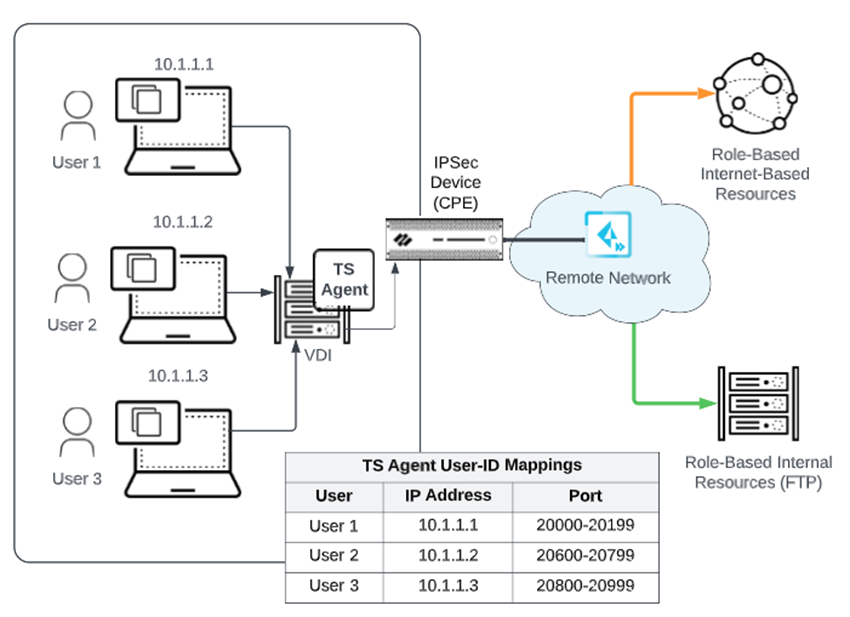
A VDI topology can be
implemented using either shared or dedicated desktops. If the desktops
are shared, multiple users are behind a single IP address and ports
are used to differentiate the users.
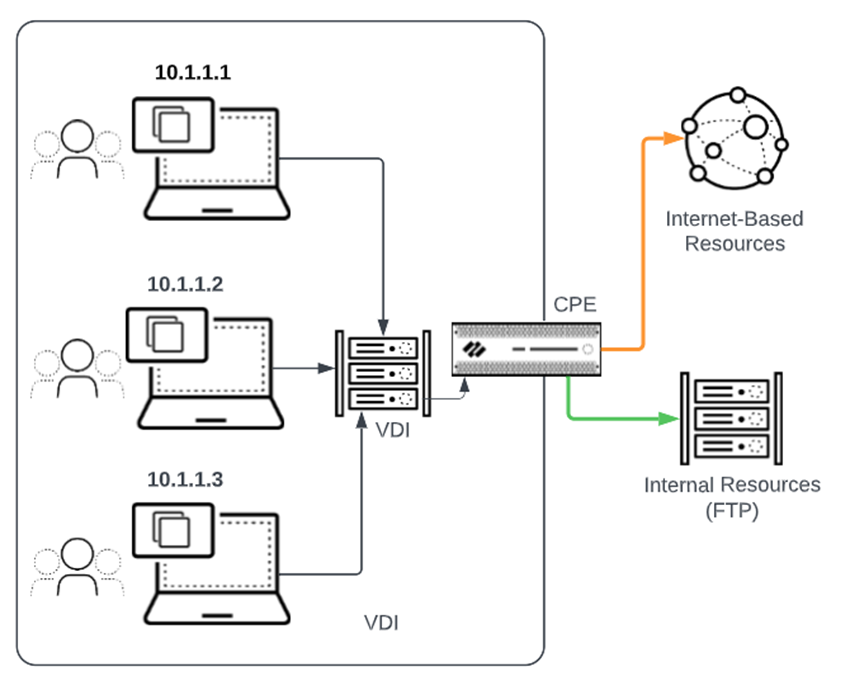
If your
VDI deployment uses a shared desktop implementation, Prisma Access
offers a solution that allows end users to securely access internet
and FTP resources using a single login, while protecting your organization’s
VDI users and internal and external resources. This solution uses
the Palo Alto Networks TS Agent that you install on the VDI servers.
The
TS Agent is a User-ID software installed to solve the challenge
associated with identifying username-to-IP address mappings when
users share IP addresses. After the TS Agent is installed, all logged-on
users are monitored and individual users are assigned with a specific
set of ports. When Prisma Access receives this VDI network traffic
from the VDI, it identifies the user based on the User's source
port. This deployment provides you with a cloud-based solution that
allows administrators to create security policy rules for VDI end
users to control their access to internet and internal sites.
If
your network has a default route, you can onboard one or more remote
networks and implement the TS agent to easily and simply protect
the users and resources in your organization.
In this deployment:
- You specify a port range on the TS agent to identify specific users on Windows-based terminal servers. The TS agent notifies Prisma Access of the allocated port ranges, so that Prisma Access can enforce policy based on users and user groups.
- The Remote Network enforces security and access control for FTP and internet-based resources.
You
cannot redistribute user mapping information collected from a TS
Agent.
To integrate a VDI using the TS Agent and a Prisma Access remote network in Cloud
Managed Prisma Access, complete the following steps.
- Install and configure the Palo Alto Networks TS Agent on the VDI servers.To map all your users, you must install the TS agent on all terminal servers to which your users log in.
- On the VDI Windows servers, Install and configure the Palo Alto Networks Terminal Server (TS) Agent.Define the range of ports that the TS agent allocates to end users.Verify the supported scale count for the TS agent from the Compatibility Matrix.(Optional) If there are multiple VDI servers, configure a TS Agent on each one.Onboard a remote network and connect it to the VDI branch site in Cloud Managed Prisma Access (if you haven’t done so already).Configure options on the IPSec device (CPE) at the branch to allow the Remote Network to communicate with the VDI.
- Configure IPSec and IKE crypto parameters for the IPSec tunnel that match the parameters you configured in Prisma Access.
- Use the Service IP address (ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessRemote NetworksService IP) as the Prisma Access side of the IPSec tunnel for the Remote Network.
- Configure a route on the IPSec device to allow VDI traffic to the Remote Network tunnel.
- Configure a route on the IPSec device to allow the remote network traffic to the TS Agent over the tunnel.
- If required, configure a security policy on the IPSec device to allow the traffic to go through the tunnel.
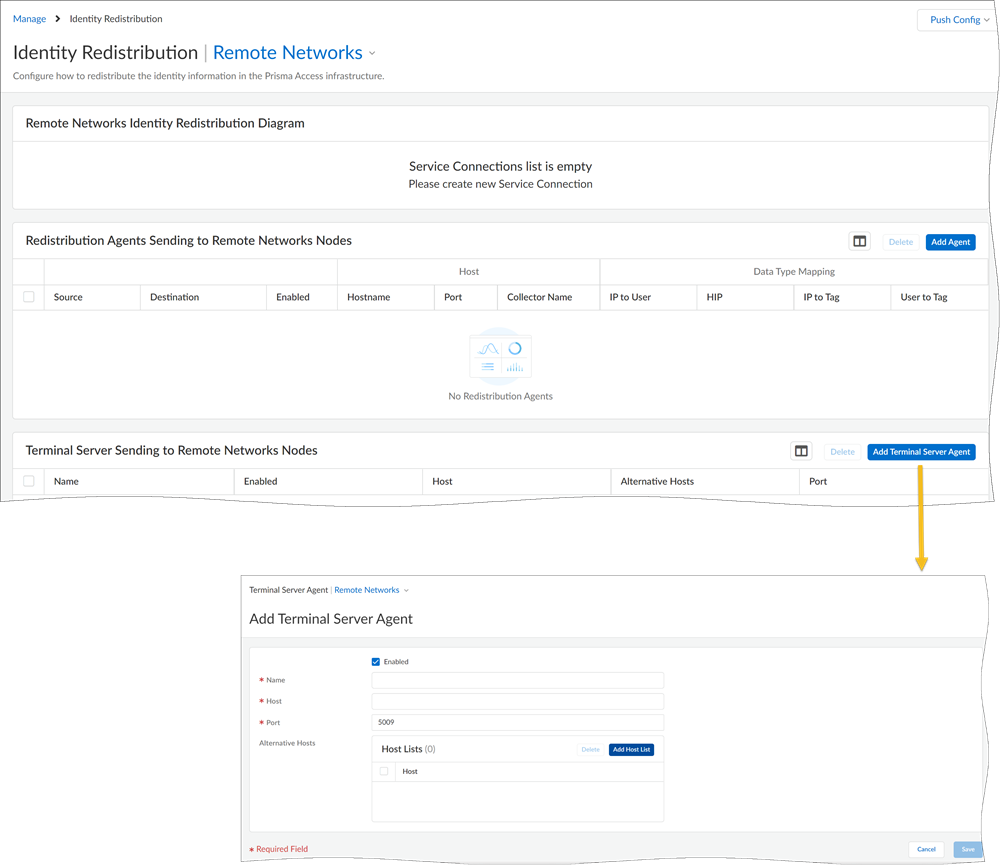
Configure the TS Agent to allow user mapping in the remote network.Go to ConfigurationNGFW and Prisma AccessIdentity ServicesIdentity Redistribution, set the Configuration Scope to Remote Networks, and Add Terminal Server Agent.- Make sure that the agent is Enabled.
- Enter a Name for the TS Agent.
- Enter the IP address of the Windows Host on which the TS Agent is installed.
- Enter the Port number on which the agent listens for user mapping requests.The port is set to 5009 by default.
- Save your changes.
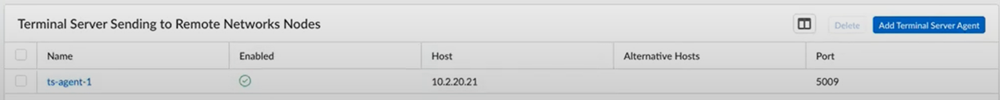
![]() The following example has an agent configured with the Host address of 10.2.20.21 and a Port of 5009.
The following example has an agent configured with the Host address of 10.2.20.21 and a Port of 5009.![]() Allow routing between the VDI and the Prisma Access remote network.
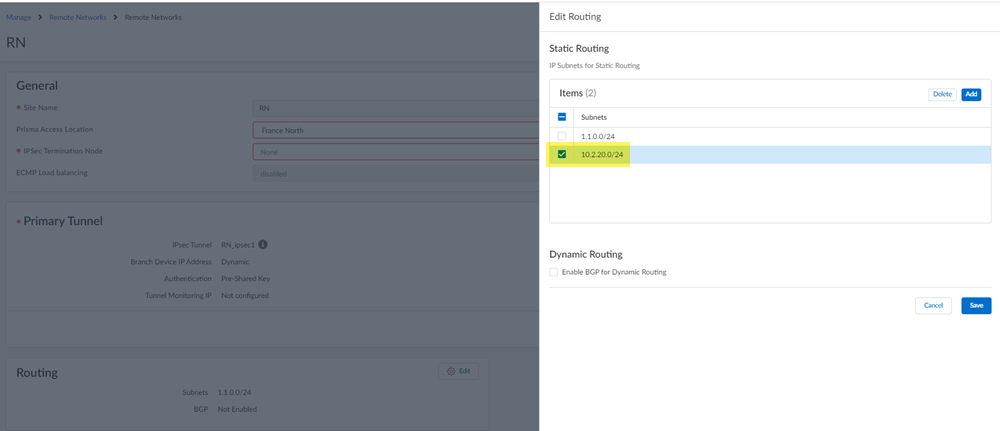
Allow routing between the VDI and the Prisma Access remote network.- Go to ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessRemote Networksremote-network-nameRouting and Add a route to the VDI subnet.Adding this subnet allows the TS Agent to communicate to the remote network. In the following example screenshot, the VDI subnet is 10.2.20.0/24.
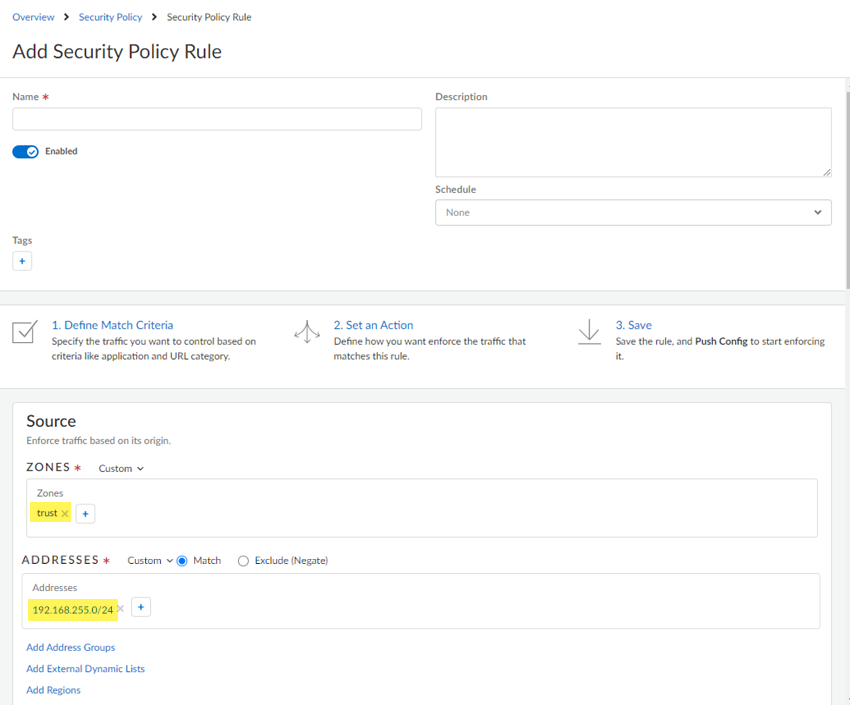
![]() Go to ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessSecurity ServicesSecurity Policy, set the scope to Remote Networks, and add a security policy rule (Add Rule) to allow the traffic between the VDI subnet and the remote network.Users at remote networks who connect to Prisma Access from the VDI are assigned an IP address from the Prisma Access Infrastructure Subnet and you must allow routing between the Infrastructure Subnet and the VDI subnet.
Go to ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessSecurity ServicesSecurity Policy, set the scope to Remote Networks, and add a security policy rule (Add Rule) to allow the traffic between the VDI subnet and the remote network.Users at remote networks who connect to Prisma Access from the VDI are assigned an IP address from the Prisma Access Infrastructure Subnet and you must allow routing between the Infrastructure Subnet and the VDI subnet.- Make sure that the rule is Enabled.
- Source—Set the following parameters:
- Zones—Set to Trust.
- Addresses— Create an address object for the Infrastructure Subnet (ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessPrisma Access InfrastructureInfrastructure Subnet) and add the address object here.An address object is preferred over entering the actual Infrastructure Subnet, because if the subnet changes, you can change the address object and the change is applied to all configuration where the address object is used.
![]()
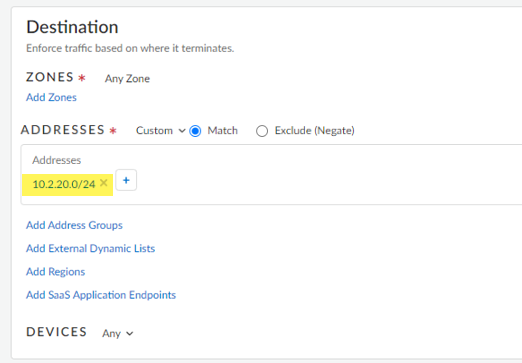
- Destination—Add the VDI host that are running the TS Agent to the Addresses.If you have configured the TS Agent on multiple VDI hosts, add them all here.
![]()
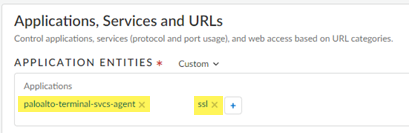
- Applications, Services and URLs—Add the paloalto-terminal-svcs-agent and to the Application Entities.
![]()
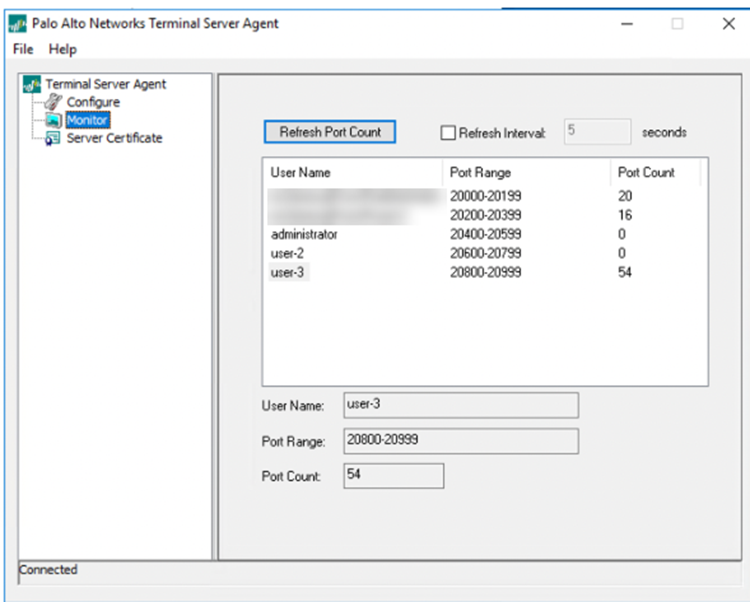
Verify that the implementation is working correctly.- In the TS agent, Monitor the agent’s status and verify that the TS agent reflects the correct username-to-port mapping.
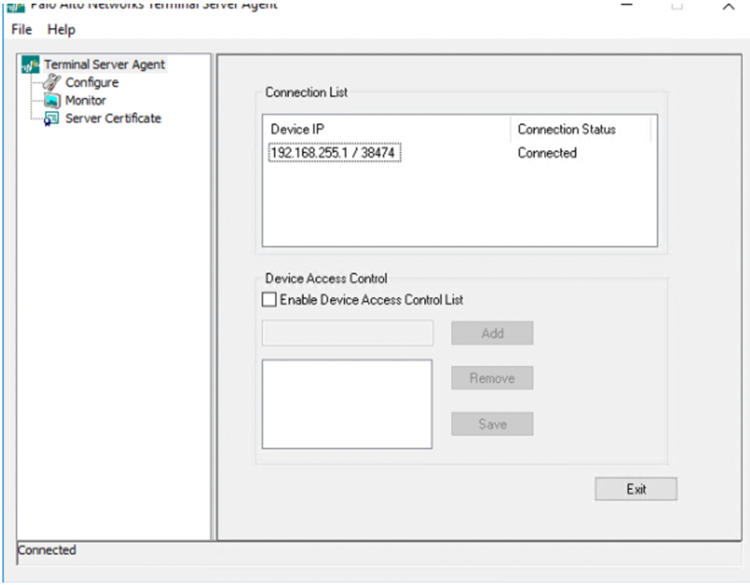
![]() Verify that the Remote Network’s IP address is connected to the TS agent.
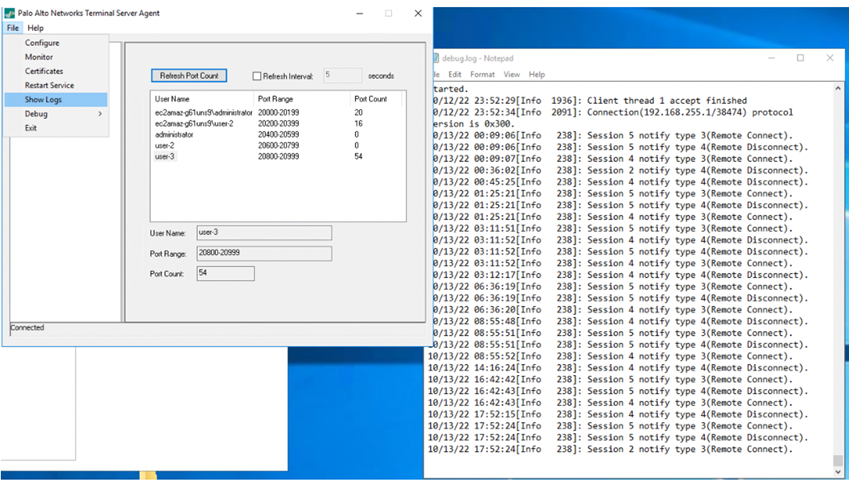
Verify that the Remote Network’s IP address is connected to the TS agent.![]() Go to FileShow Logs and view the log messages for the TS agent.
Go to FileShow Logs and view the log messages for the TS agent.![]() In Prisma Access (Managed by Strata Cloud Manager), go to ActivityLog ViewerCommon/System and verify that the remote networks are able to connect to the TS agent.
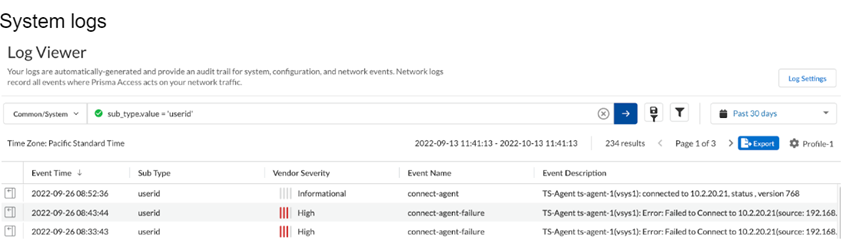
In Prisma Access (Managed by Strata Cloud Manager), go to ActivityLog ViewerCommon/System and verify that the remote networks are able to connect to the TS agent.![]() Go to ActivityLog ViewerFirewall/URL and verify that the remote networks are able to enforce identity-based policies.
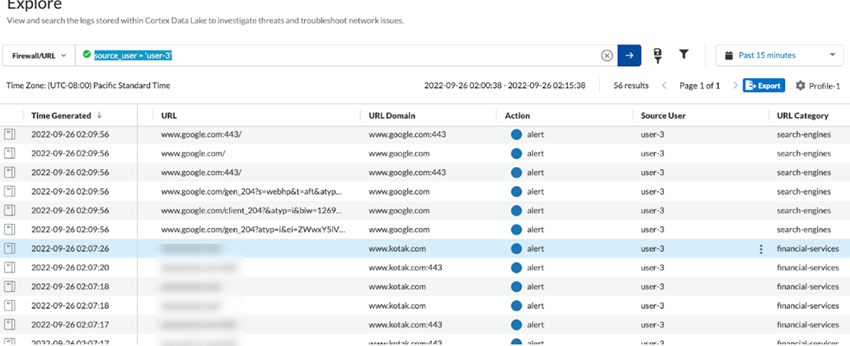
Go to ActivityLog ViewerFirewall/URL and verify that the remote networks are able to enforce identity-based policies.![]()