SaaS Security
View Threats and Incidents
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
View Threats and Incidents
Use the Behavior Threats dashboard to view detects threats and incidents.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Data Security license:
|
Depending on when you first activated and configured Data Security, up to 90
days of historical user data is available to Behavior Threats. Behavior Threats examines
this historical user data, and, using data-driven machine learning models, assigns a
risk score to each user.
The Behavior Threats dashboard in the Strata Cloud Manager prominently displays the
Top 3 Risky Users and you can also View All Risky
Users. To determine whether a user poses a threat to your organization,
you can view user details (such as the threat incidents associated with the user and the
user's risk score). You can also view the most risky users for individual policies on
the Policies tab.
The Incidents tab on the Behavior Threats page displays the threat
incidents that Behavior Threats detected. Depending on how you set the time-range filter
on the Behavior Threats dashboard, you can view up to 90 days of threat incidents.
The Users tab on the Behavior Threats page displays threat details
for each user on your tenant, such as the user's risk score and number of threat
incidents. From there, you can display more detailed information for a particular user.
To track a particular user more closely, you can add them to the watchlist in Behavior
Threats. For example, if the user appears as one of the Top 3 Risky
Users in the Behavior Threats dashboard, you might want to add them to
the watchlist to track them more carefully. Or you might want to track users for reasons
unrelated to the information that Behavior Threats has logged. For example, if a user
has recently tendered their resignation, you might want to add them to the watchlist so
you can more easily observe any suspicious download activities. Such activities might
indicate an attempt to take proprietary information to their next job.
To track a particular user more closely, you can add them to the watchlist in Behavior Threats. To view all the
users on the watchlist, you apply the Watchlist filter to the
Users table.
- View Details for the Most Risky Users
- View All Threat Incidents
- View Threat Details for All Users
- Add Users of Interest to the Watchlist
- View the Users on the Watchlist
View Details for the Most Risky Users
Get visibility into the most risky users on your tenant, based on the number and
severity of threat incidents logged by Behavior Threats.
View the Most Risky Users
The Behavior Threats dashboard displays the most risky users on your tenant. The
most risky users are those with the highest risk scores for your organization.
Investigate these most risky users to determine if they pose a threat to your
organization.
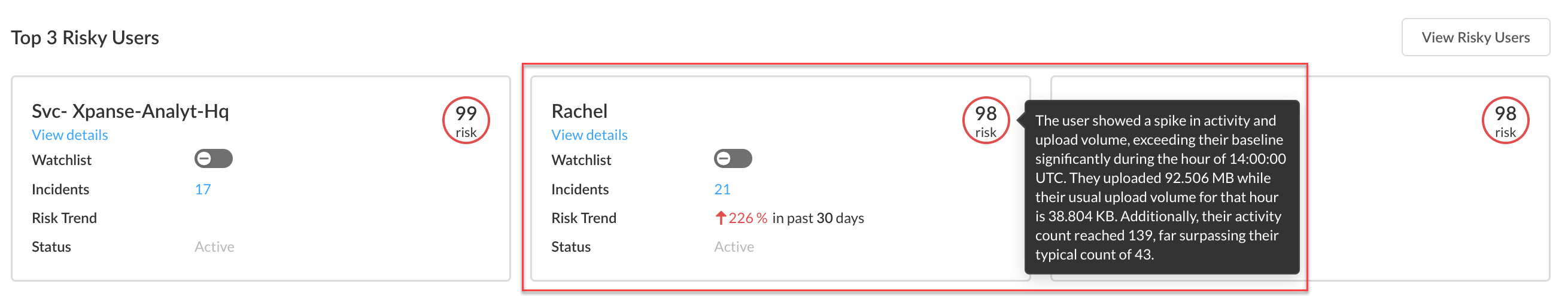
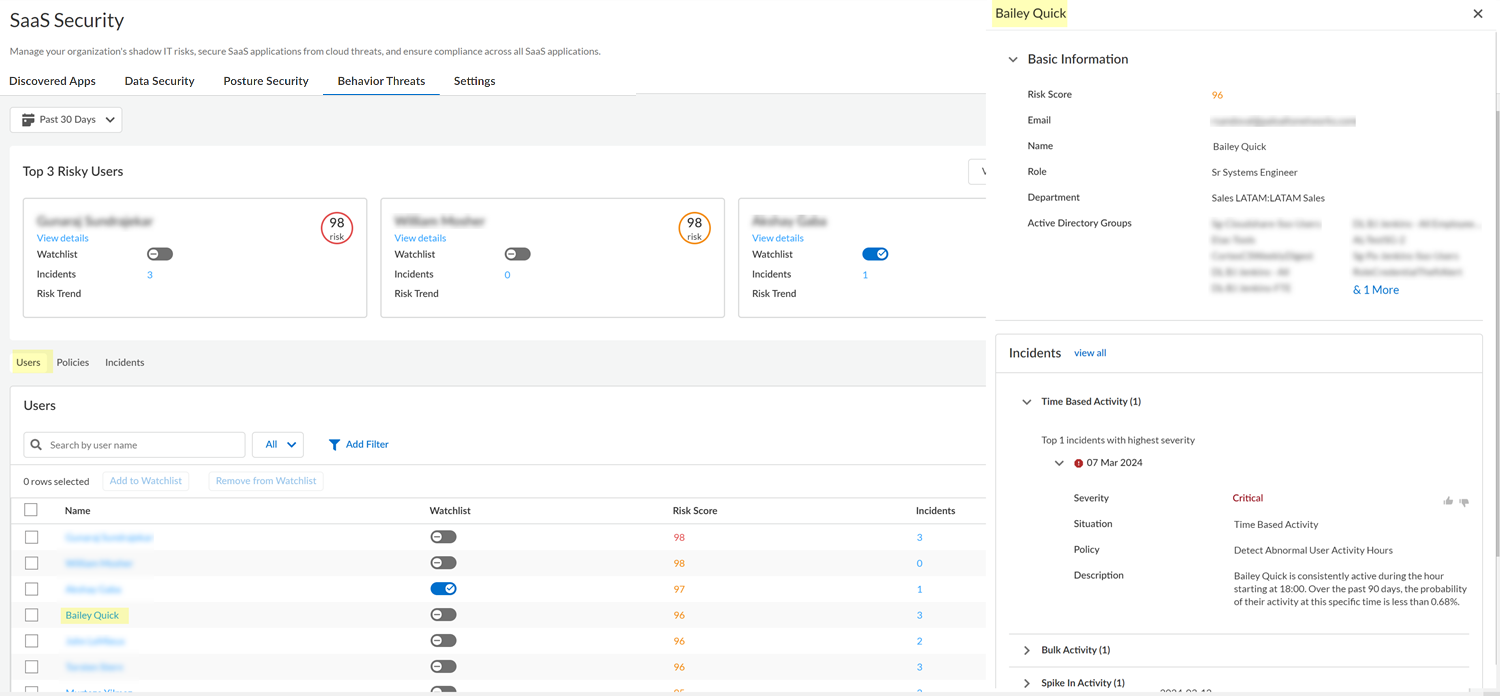
- Log in to Strata Cloud Manager.Select to ManageConfigurationSaaS SecurityBehavior Threats.View details for each of the Top 3 Risky Users. The details include more information about the threat incidents associated with the user. Investigate any suspicious activity and take action as needed.LLM Powered User Risk SummaryBehavior Threats provides an LLM-powered user risk summary of the top 0.1% of risky users. This summary provides detailed insights into unusual activities, data access patterns, and potential security concerns even when incidents are not generated, enabling security administrators like you to understand and assess user risk more effectively.In the following example, a mouse hover on Rachel's risk score displays the LLM-powered risk summary.
![]() If you want to monitor a user more closely, you can add them to the watchlist.After investigating the Top 3 Risky Users, you can View All Risky Users. View details for these users and take action as needed.
If you want to monitor a user more closely, you can add them to the watchlist.After investigating the Top 3 Risky Users, you can View All Risky Users. View details for these users and take action as needed.View the Most Risky Users for Individual Policies
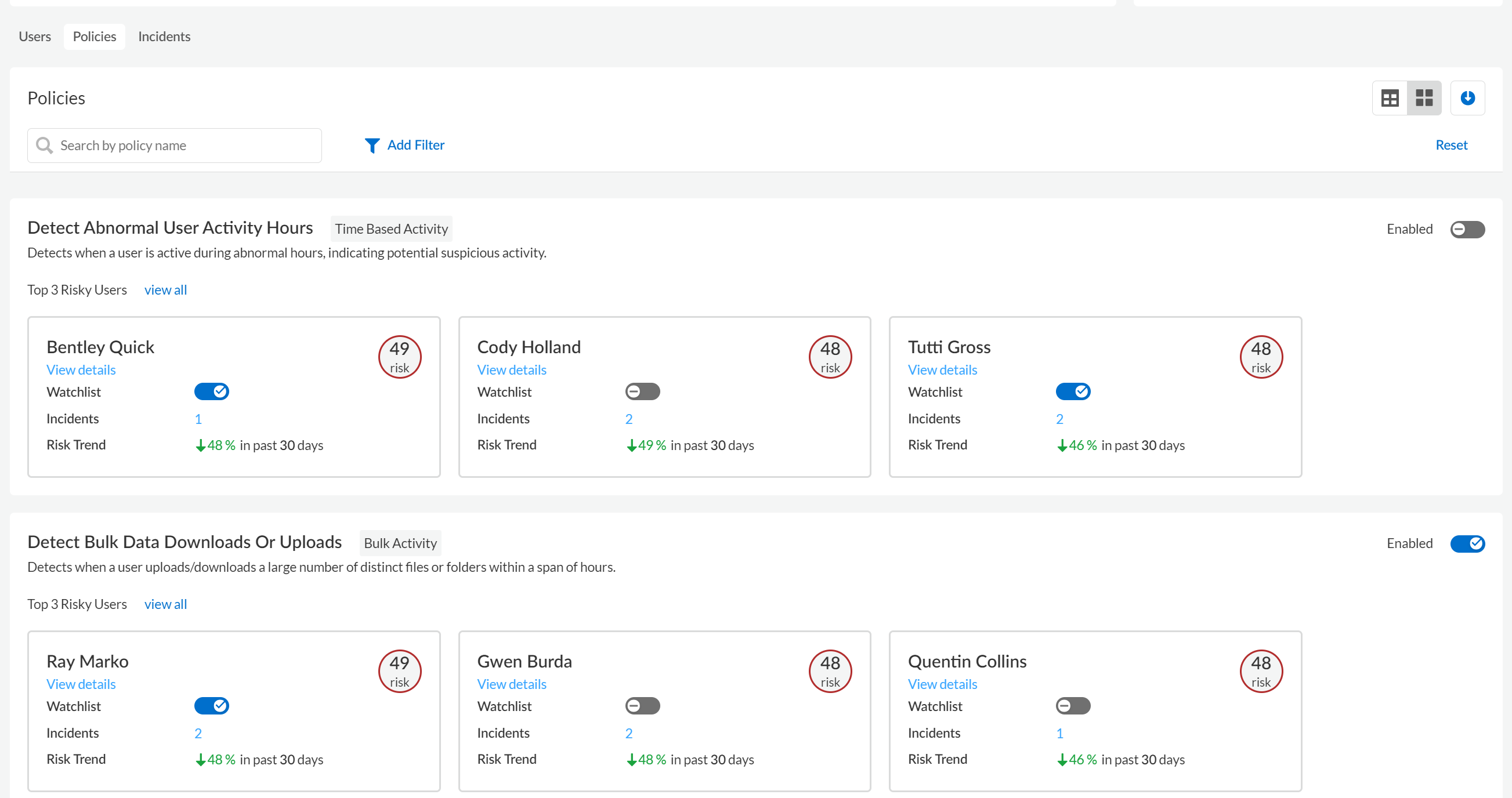
The Policies tab on the Behavior Threats dashboard shows the most risky users for each policy. These risky users are the users with the highest risk scores who are associated with threat incidents for the policy.- Navigate to the Behavior Threats dashboard.Navigate to Policies.You can display the Policies in a grid view or a list view. By default, the policies display in a grid view.In the Policies grid, locate the policy that you're interested in and view the Top 3 Risky Users for the policy.The displayed information includes the user's risk score and the number of threat incidents associated with the user for the policy.
![]() View details for each of the Top 3 Risky Users. The details include more information about the threat incidents associated with the user. Investigate any suspicious activity and take action as needed.If you want to monitor a user more closely, you can add them to the watchlist.After investigating the Top 3 Risky Users, you can view all risky users for the policy. View details for these users and take action as needed.
View details for each of the Top 3 Risky Users. The details include more information about the threat incidents associated with the user. Investigate any suspicious activity and take action as needed.If you want to monitor a user more closely, you can add them to the watchlist.After investigating the Top 3 Risky Users, you can view all risky users for the policy. View details for these users and take action as needed.
View All Threat Incidents
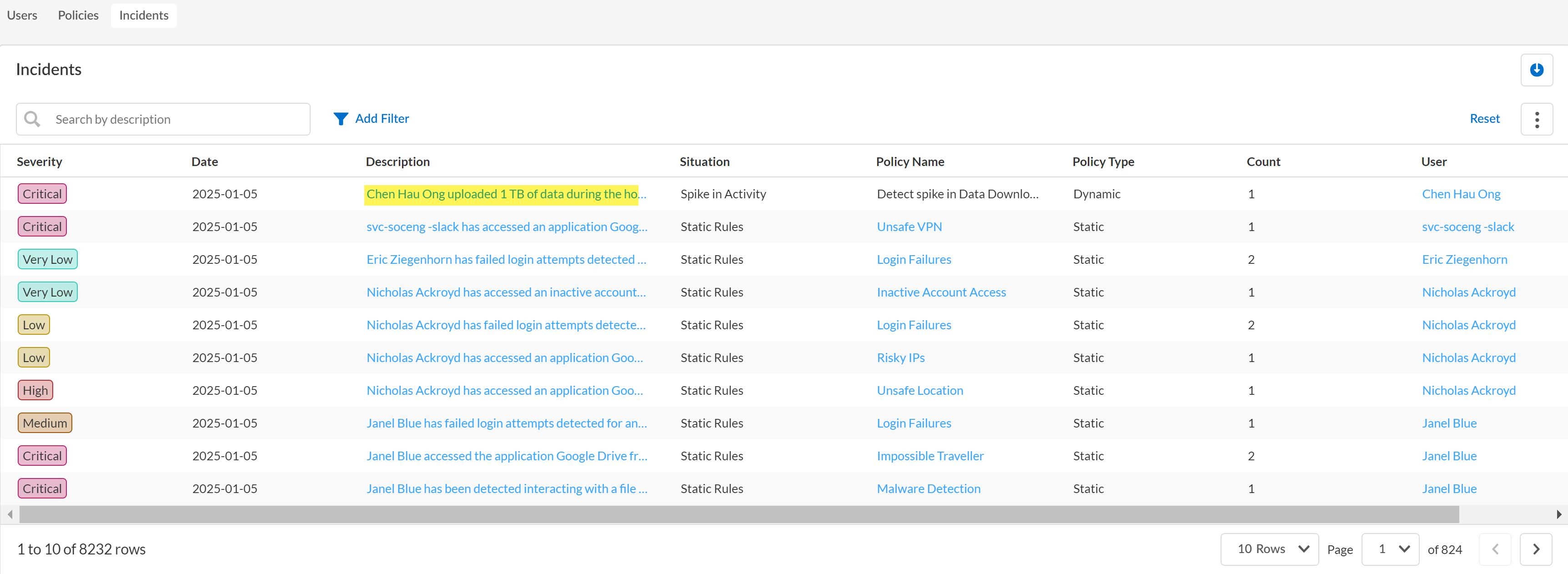
The Incidents tab on the Behavior Threats page displays the threat incidents that Behavior Threats detected.- Log in to Strata Cloud Manager.Select to ManageConfigurationSaaS SecurityBehavior ThreatsIncidents.In the Incidents table, review the information about the threat incidents.The displayed information includes the name of the policy that describes this type of incident, the severity of the incident, the user whose actions caused the incident, and the date that the incident occurred. You can sort the Incidents table according to any of these attributes by clicking the appropriate column.(Optional) Add Filter to the table to view only the incidents for a particular severity, user, or situation type (such as a spike in activity).(Optional) To view more information about the policy or user associated with the incident, click the name in the Policy Name or User column of the table.Click the incident Description to view in-depth details about a particular incident.
![]()
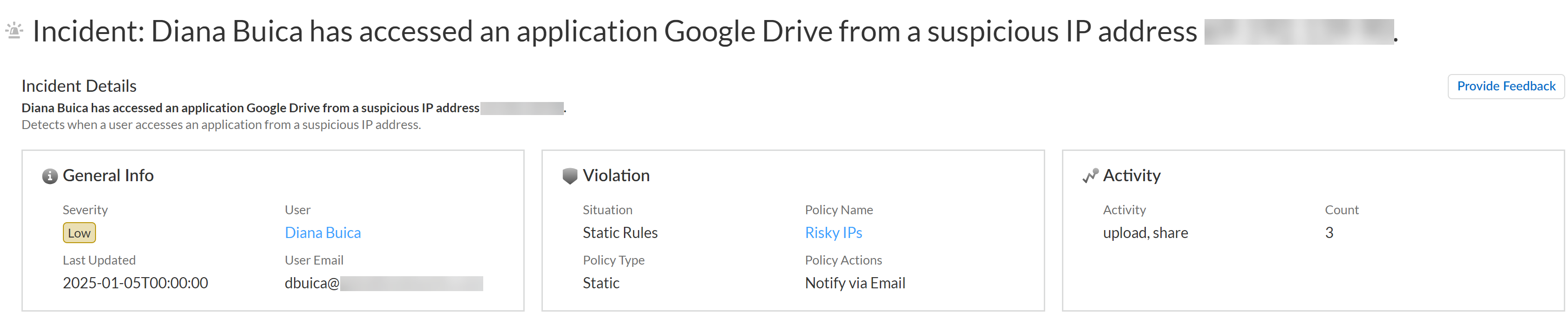
- Incident DetailsThis section provides a written summary of the incident that describes which user accessed which app, and why it generated an incident. Additionally, it provides the following information:
- General Info—Describes the severity level of the incident, the user who generated the incident, the email of the user, and the last time the incident was updated.
- Violation—Describes the violation situation, the name of the policy rule and policy rule type the incident generated against, and the action taken as configured in the policy rule.
- Activity—Describes the activity that generated the incident and the number of individual events associated with the incident.
![]()
- EventsPresents a bar graph displaying the total number of event counts associated with the incident, and the time each event occurred.
![]()
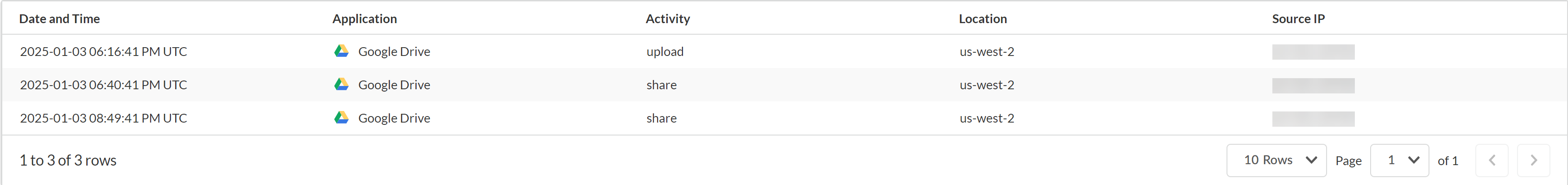
- Incident List(Dynamic Policy Rules Only) You can filter and narrow down the list of incidents generated from predefined dynamic user activity policy rules based on the Application and Activity you want to investigate.A list of all events associated with the incident that includes the following information displays for both dynamic and static user activity policy rules.
- Date and time the event occurred in YYYY-MM-DD:HH:MM:SS UTC format.
- App associated with the incident.
- Activity that occurred that generated the incident.
- Location or region where the incident occurred.
- Source IP address of the user who generated the incidents.
![]()
Click the Incidents link at the top of the page to return to the Behavior Threats Incidents page.(Optional) Click the table's download icon to export a CSV file with a list of the incidents. The list will contain all incidents unless you applied a filter to the table.View Threat Details for All Users
The Users tab on the Behavior Threats page displays threat details for each user on your tenant, such as the user's risk score and number of threat incidents.- Log in to Strata Cloud Manager.Select to ManageConfigurationSaaS SecurityBehavior ThreatsUsers.In the Users table, review high-level information.The displayed information includes the user's risk score and the number of threat incidents associated with the user for the policy.(Optional) Add Filter to the table to view only the users on the watchlist, or only the users with threat incidents for a situation type (such as a spike in activity).(Optional) Click the table's download icon to export a CSV file with a list of the users. The list will contain all users unless you applied a filter to the table.To view more details for a user, including threat-incident details, click the name of the user.
![]()
Add Users of Interest to the Watchlist
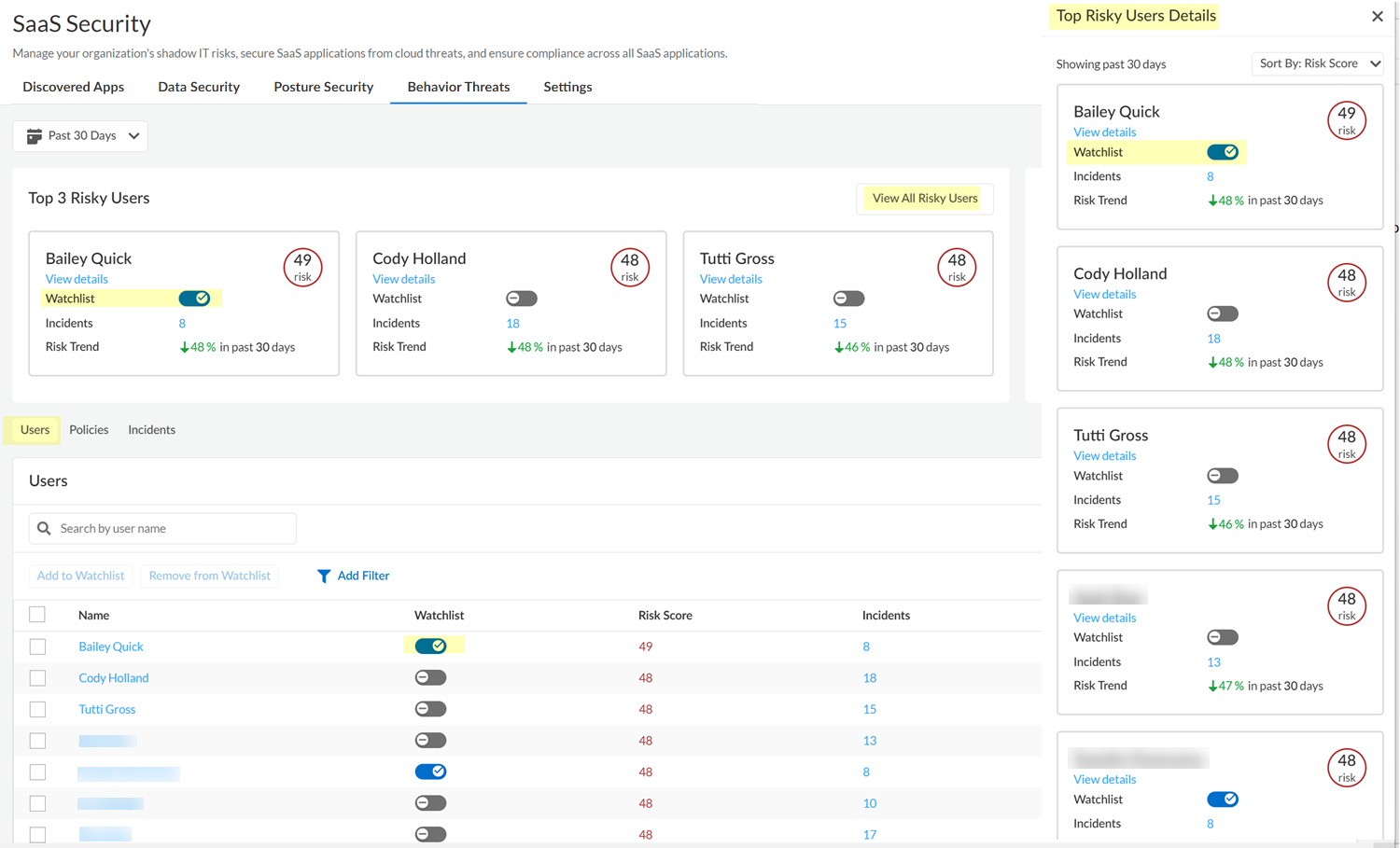
In Behavior Threats, you can monitor a user more closely by adding them to the watchlist. You can filter the Users table to show only users in the watchlist.To view all the users who you added to the watchlist, you can Add Filter to the Users table.- Log in to Strata Cloud Manager.Select to ManageConfigurationSaaS SecurityBehavior Threats.To add any of the Top 3 Risky Users to the watchlist, complete the following steps:
- Locate the user in the Top 3 Risky Users or View All Risky Users to locate the user in the Top Risky Users Details.
- Position the Watchlist toggle for the user to the On position.
To add any user to the watchlist, complete the following steps:- Navigate to Users.
- Locate the user in the list.
- Position the Watchlist toggle for the user to the On position.
![]()
View the Users on the Watchlist
In Behavior Threats, you can monitor a user more closely by adding them to the watchlist. You can filter the Users table to show only users in the watchlist.- Log in to Strata Cloud Manager.Select to ManageConfigurationSaaS SecurityBehavior ThreatsUsers.Add Filter to the table and add the Watchlist filter.Set the Watchlist filter to show only the users in the watchlist (WatchlistIn Watchlist).In the Userstable, review high-level information for the users on the watchlist.The displayed information includes the user's risk score and the number of threat incidents associated with the user for the policy.(Optional) Click the table's download icon to export a CSV file with a list of the users in the watchlist.To view more details for a user, including threat-incident details, click the name of the user.