SaaS Security
Configure Syslog Monitoring on Data Security
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
Configure Syslog Monitoring on Data Security
Use these steps to configure a syslog server profile
on Data Security.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Data Security license:
|
Data Security supports the following log
types:
- Incidents log
- Policy Violation log
- Remediation log
- Activity Monitoring log
- Admin Audit log
- Behavior Threats log
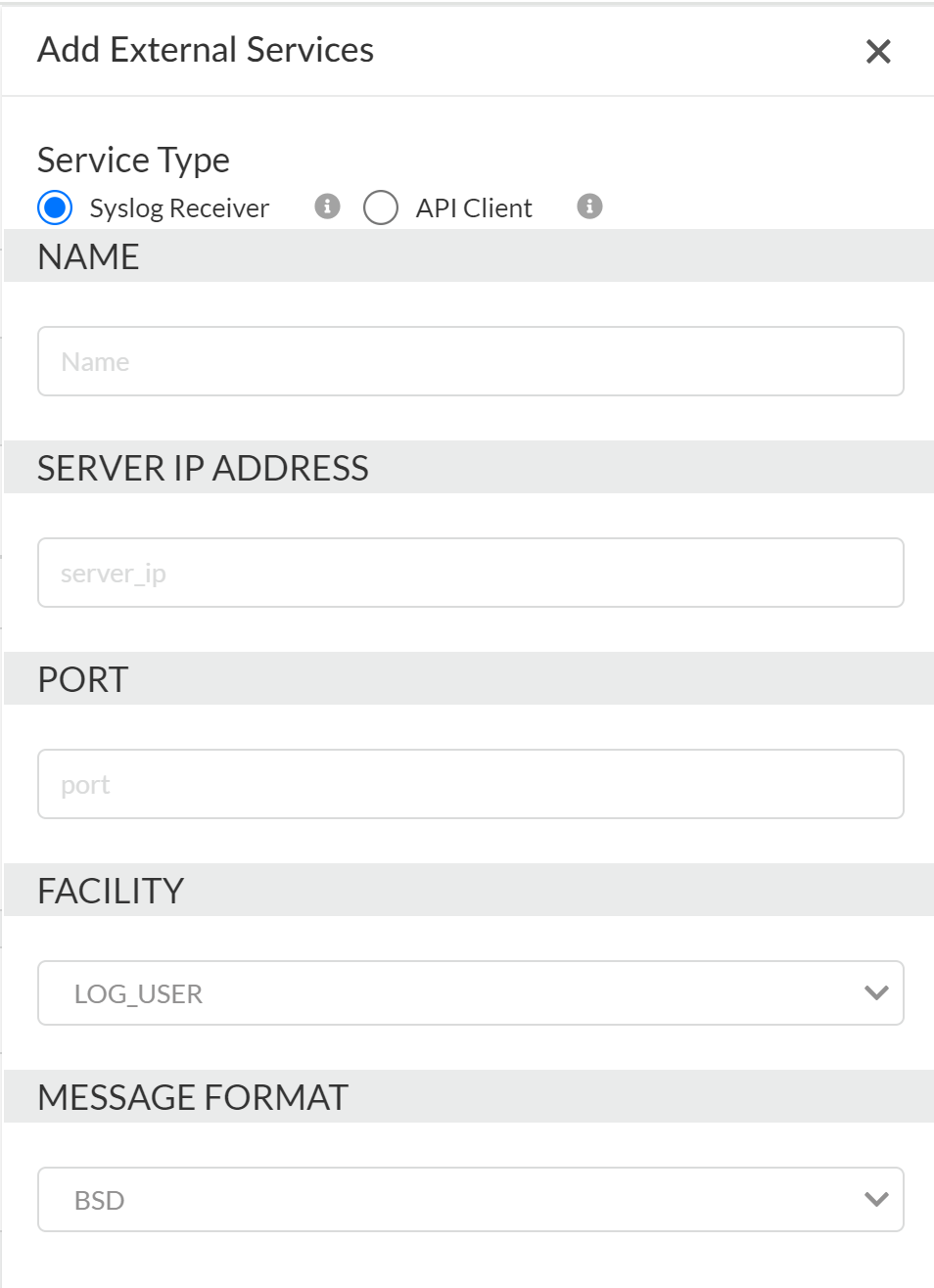
- Log in to Strata Cloud Manager.Select ConfigurationSaaS SecuritySettingsDirectory & External ServicesExternal ServicesAdd Syslog/API Client.Select Syslog Receiver to create a Syslog server profile.You can add only external service — forward logs to a syslog receiver or Onboard Sanctioned SaaS Apps to Data Security.Enter a Name for the profile.Add the information Data Security requires to connect to it:
- Name—Unique name for the server profile.
- Server IP—IP address of the syslog server.
- Port—The port number on which you send syslog messages. You must use the same port number for Data Security and the syslog server.
- Facility—Select a syslog standard value (for example, LOG_USER) to calculate the priority (PRI) field in your syslog server implementation. The PRI part of the syslog message represents the Facility and Severity of the message. Select the value that maps to how you use the PRI field to manage your syslog messages. Values can be LOG_USER or LOG_LOCAL0 through LOG_LOCAL7. There is no default.
- Message format—Select the syslog message format to use: BSD (the default) or IETF. Traditionally, IETF format is used over TCP or SSL.
Save your changes.![]() On the Syslog server, self-sign your server and create the SSL certificate, then enable TLS in the syslog configuration, setting the TLS option to peer-verify(optional-untrusted).TCP is required as the reliable transport.
On the Syslog server, self-sign your server and create the SSL certificate, then enable TLS in the syslog configuration, setting the TLS option to peer-verify(optional-untrusted).TCP is required as the reliable transport.