SaaS Security
Determine the Risks Posed by a Third-Party Plugin
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
Determine the Risks Posed by a Third-Party Plugin
Examine the access scopes that users granted to a third-party plugin to assess the
risks to your environment.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Data Security license:
|
Examine each unreviewed third-party plugin to determine if you want to allow it in
your environment.
You can examine unreviewed plugins in
the following two ways:
- Across all marketplace apps from the 3rd Party Plugins page (Posture Security 3rd Party Plugins). The 3rd Party Plugins page displays a table of all the third-party plugins that were installed across all the marketplace app instances that you have onboarded to SaaS Security Posture Management. The Status column of this table shows whether the plugin was Reviewed or Not Reviewed. Other columns of the table, such as the Severity and Risk columns, help you identify high-risk plugins.
- For one marketplace app instance, from the Connected Applications tab of the app's details page. The Status column of the Connected Applications table shows whether the plugin was Reviewed or Not Reviewed. The Severity column of the table helps you identify high-risk plugins.
SSPM gathers the information for the 3rd Party Plugins page
from the third-party plugin scans that SSPM runs for marketplace apps. If SSPM isn’t
running third-party plugin scans for a particular marketplace app instance, the 3rd
Party Plugins page won’t show information for that marketplace app instance. For
example, you can onboard Google Workspace with reduced permissions, in which case
SSPM won’t perform third-party plugin scans for that Google Workspace instance. The
3rd Party Plugins page won’t display information for that Google Workspace instance.
For more information about any of the marketplace apps, you can review the information
shown in the catalog of third-party plugins.
Determine the Risks Posed by a Third-Party Plugin Across All Marketplace Apps
Review the information on the 3rd Party Plugins page to identify the riskiest
plugins.
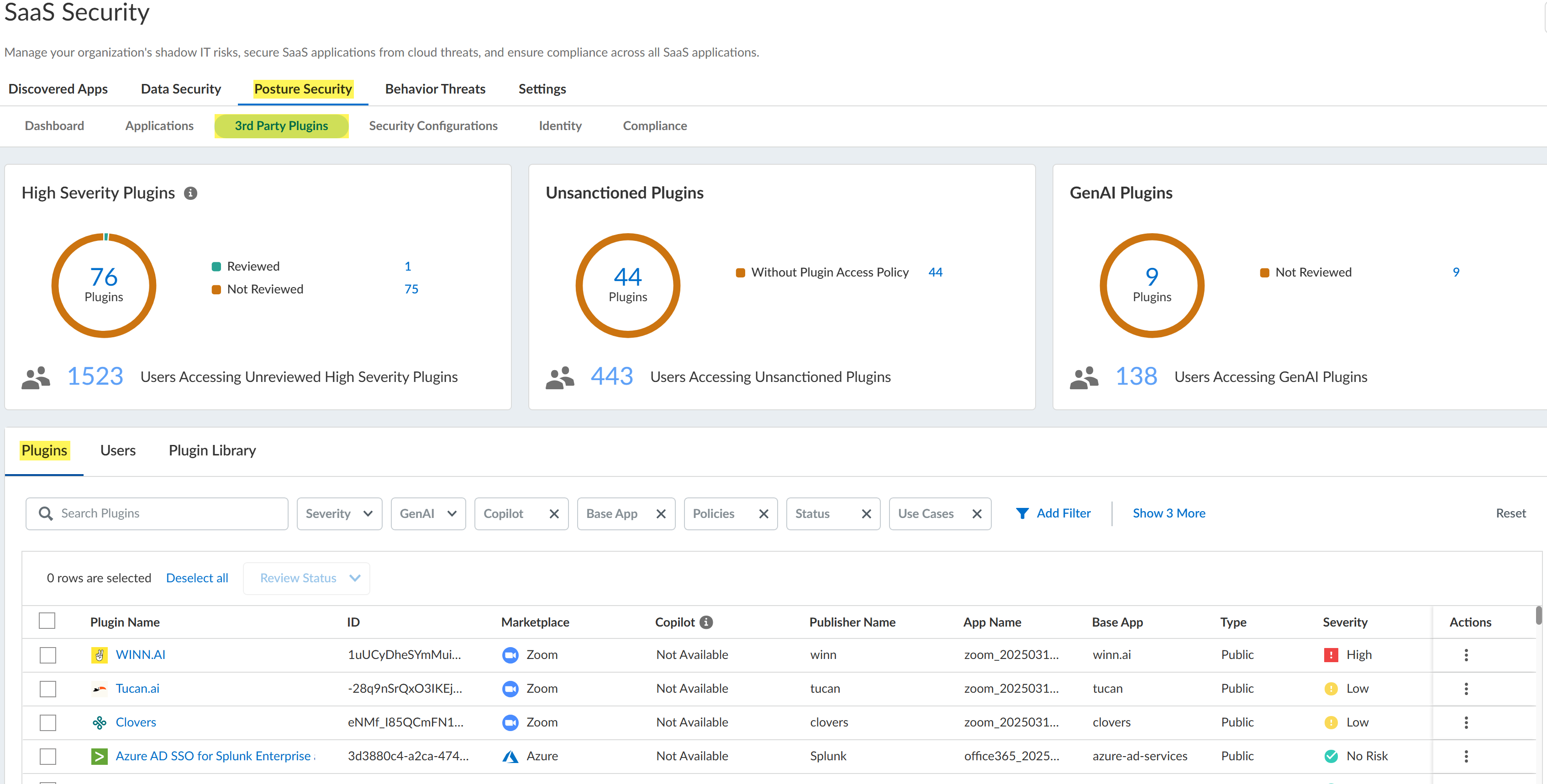
The 3rd Party Plugins page provides an overview of the third-party plugins that have
been installed across all the marketplace app instances that you have onboarded to
SaaS Security Posture Management. Review the plugins to determine if you want to allow them
in your environment. The 3rd Party Plugins page helps you easily identify the
riskiest plugins, so you can revoke user access to the plugins. You can also mark
plugins as Reviewed if you decide to allow them in your environment. By marking a
plugin as Reviewed, administrators who view this page later don’t have to reassess
whether the plugin is a threat.
- Log in to Strata Cloud Manager.Select ManageConfigurationSaaS SecurityPosture Security3rd Party Plugins.Navigate to the Plugins tab to review the third-party plugins.The Status column of the table identifies which plugins were Not Reviewed yet.
![]() Apply one or more filters to the Plugins table to view only the plugins of interest.
Apply one or more filters to the Plugins table to view only the plugins of interest.- From the summary information at the top of the page, you can filter the table to show only the High Severity Plugins the were Not Reviewed.
- Because the recent and rapid proliferation of generative artificial intelligence (GenAI) apps has introduced new vulnerabilities for data leakage or deliberate attacks, the 3rd Party Plugins page highlights GenAI apps. From the summary information at the top of the page, you can filter the table to show only the GenAI Plugins that were Not Reviewed.
- You can Add Filter to the Plugins table to filter the table by various plugin attributes, such as the type of marketplace app, the risk severity of the plugin, and the plugin's review status.
Review each third-party plugin whose Status is Not Reviewed to decide whether you want to allow the plugin in your environment.To identify high-risk plugins, examine the information in the Severity and Risk columns of the table.The Severity is based on the marketplace app scopes that were granted to the third-party plugin. The greater the access to the marketplace app's data and actions, the higher the Severity. To view the scopes that the third-party plugin can access, click on Plugin Name in the table and, in the Plugin Details panel, navigate to view the plugin's Permissions.This Risk column shows the app's risk score. The risk score is between 1 (low risk) and 5 (high risk) and is calculated from over 55 app attributes including compliance attributes, security and privacy attributes, identity access management attributes, and, if applicable, generative AI attributes.To determine the popularity of the plugin in your organization, and the number of users who will be affected if you revoke access to the plugin, examine the information in the Active Users column. For more details about the users, click on Plugin Name in the table and, in the Plugin Details panel, navigate to view the plugin's Users.Take action on the third-party plugin.From the Actions column, you can specify that you Reviewed the plugin and will allow its continued use. From the Actions column you can also, in some cases, Revoke Access to the plugin for all active users of the plugin. To revoke access for individual users, click on Plugin Name in the table and, in the Plugin Details panel, navigate to view the plugin's Users. Whether the Revoke Access action is available depends on the level of permission that SSPM has to the marketplace app, and on the capabilities that the marketplace app's API provides. If the Revoke Access action isn’t available, you can instead log in to the SaaS app's administration console, and follow its documentation to remove the plugin.Although you can revoke access to a plugin that does not prevent a user from subsequently installing the same plugin. To instruct SSPM to periodically scan marketplace apps for certain plugins, you can create a Plugin Access Control policy. When the policy is enabled, SSPM can notify you when users install plugins that you don’t want in your environment.Determine the Risks Posed by Third-Party Plugins for One Marketplace App
The Connected Applications tab shows the third-party plugins that are hosted in a marketplace app. Review the plugins to determine if you want to allow them in your environment.- Log in to Strata Cloud Manager.Select ManageConfigurationSaaS Security.Navigate to the third-party plugins for a marketplace app. Do one of the following:
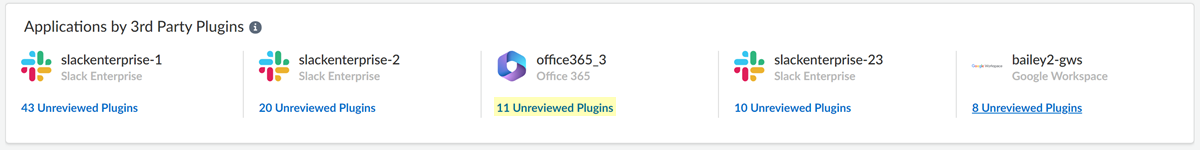
- Navigate to the third-party plugins from the dashboard:
- Select Posture SecurityDashboard, and locate the Applications by 3rd Party
Plugins area. This area shows the marketplace apps that
have the most unreviewed plugins. The area shows the number of
unreviewed plugins for each app.Investigate each unreviewed plugin to judge whether it threatens your organization's security.
- For the marketplace app whose third-party plugins you want to
review, click the Unreviewed Plugins
link.
![]()
- Select Posture SecurityDashboard, and locate the Applications by 3rd Party
Plugins area. This area shows the marketplace apps that
have the most unreviewed plugins. The area shows the number of
unreviewed plugins for each app.
- Navigate to the third-party plugins for a marketplace app from the
Applications page.
- Select Posture SecurityApplications.
- Locate the SaaS app, then View Details.
- Select the Connected Applications tab.
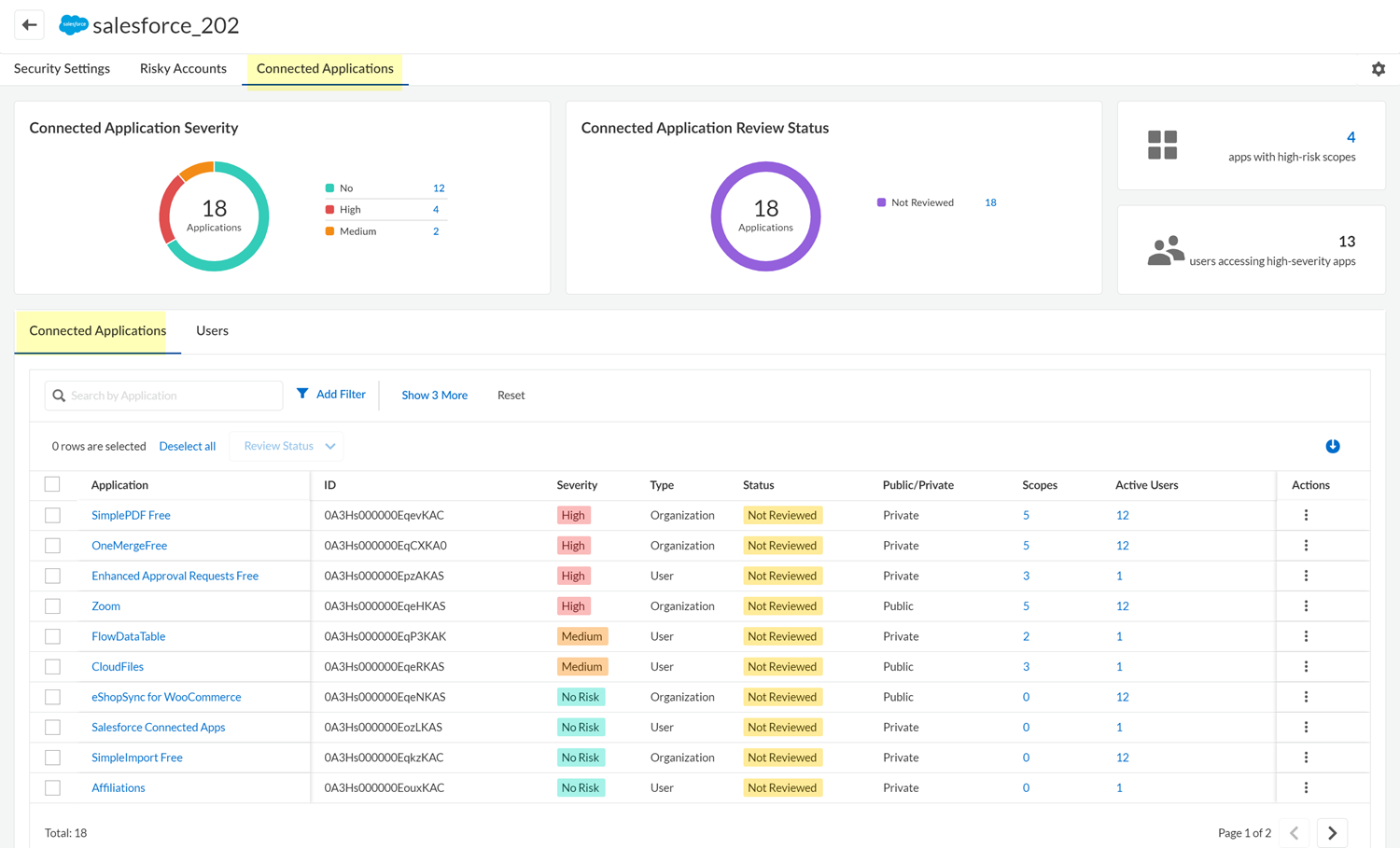
On the Connected ApplicationsConnected Applications tab, view the list of third-party plugins that one or more users added to the marketplace app.![]() The table on this page lists the plugin apps that were connected to the marketplace app. The table displays information for each plugin, such as its severity (based on the scopes that were granted to the plugin), whether the plugin was installed for the organization or for individual users, and whether the plugin is a public or private app. The information that SSPM can display in the table depends on the type of marketplace app that’s hosting the third-party plugin.The Status column of the table identifies which plugins were Not Reviewed. Assess these plugins to determine if they are a risk to your environment.To filter the table to show only certain apps, click any of the app counts displayed in the upper section of the page, such as the app severity or review status counts. In the table, you can also Add Filter to filter the table by attributes such as the app severity, review status, or accessed scopes.Click the table's download icon to export the table information to a CSV file. The file will contain all the apps unless you applied a filter to the table.In the Applications column, click the name of the third-party plugin that you want to review.
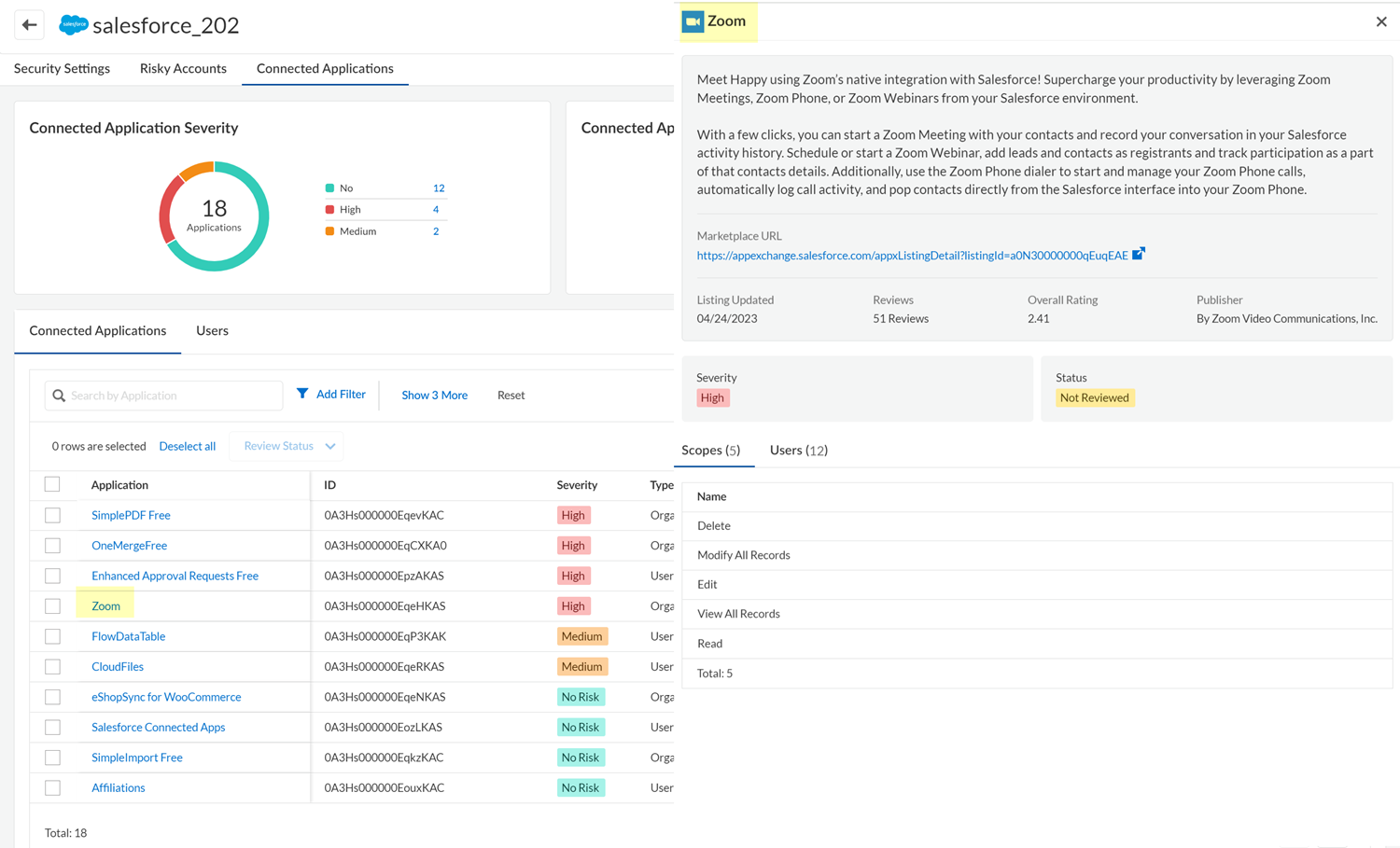
The table on this page lists the plugin apps that were connected to the marketplace app. The table displays information for each plugin, such as its severity (based on the scopes that were granted to the plugin), whether the plugin was installed for the organization or for individual users, and whether the plugin is a public or private app. The information that SSPM can display in the table depends on the type of marketplace app that’s hosting the third-party plugin.The Status column of the table identifies which plugins were Not Reviewed. Assess these plugins to determine if they are a risk to your environment.To filter the table to show only certain apps, click any of the app counts displayed in the upper section of the page, such as the app severity or review status counts. In the table, you can also Add Filter to filter the table by attributes such as the app severity, review status, or accessed scopes.Click the table's download icon to export the table information to a CSV file. The file will contain all the apps unless you applied a filter to the table.In the Applications column, click the name of the third-party plugin that you want to review.![]() Examine the details of the third-party plugin.Take action on the third-party plugin.From the Actions column, you can specify that the plugin was Reviewed, or you can Revoke Access to the plugin. From the Users tab, you can also Revoke Access for individual users (if SSPM supports the Revoke Access action for the marketplace app).Although you can revoke access to a plugin that does not prevent a user from subsequently installing the same plugin. To instruct SSPM to periodically scan marketplace apps for certain plugins, you can create a Plugin Access Control policy. When the policy is enabled, SSPM can notify you when users install plugins that you don’t want in your environment.
Examine the details of the third-party plugin.Take action on the third-party plugin.From the Actions column, you can specify that the plugin was Reviewed, or you can Revoke Access to the plugin. From the Users tab, you can also Revoke Access for individual users (if SSPM supports the Revoke Access action for the marketplace app).Although you can revoke access to a plugin that does not prevent a user from subsequently installing the same plugin. To instruct SSPM to periodically scan marketplace apps for certain plugins, you can create a Plugin Access Control policy. When the policy is enabled, SSPM can notify you when users install plugins that you don’t want in your environment.