Enterprise DLP
Edit the Cloud Content Settings
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
Edit the Cloud Content Settings
Edit the Cloud Content Settings to specify the server to send your Enterprise Data Loss Prevention (E-DLP) files for inspection.
On May 7, 2025, Palo Alto Networks is introducing new Evidence Storage and Syslog Forwarding service IP
addresses to improve performance and expand availability for these services
globally.
You must allow these new service IP addresses on your network
to avoid disruptions for these services. Review the Enterprise DLP
Release Notes for more
information.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
By default, Enterprise Data Loss Prevention (E-DLP) is configured using a Cloud Content Fully Qualified Domain
Name (FQDN) that automatically resolves to the closet Cloud Services server to
inspect matching traffic. If you have specific data residency requirements, you can
specify a regional Cloud Services server by editing the Cloud Content FQDN to which
to send your Enterprise DLP traffic for inspection.
- Log in to the Panorama web interface.Select DeviceSetupContent-ID and select the Template associated with the managed firewalls using Enterprise DLP.Edit the Cloud Content FQDN.
- Edit the Cloud Content Settings.Modify the Public Cloud Server based on your data residency requirements.Enterprise DLP data and data processing, including DLP incidents, reports, and DLP verdicts, are generated in the specified Public Cloud Server region. The Default Enterprise DLP Public Cloud Server automatically resolves to the closest Public Cloud Server.Review the list of
- Public Cloud Server by Region
- Default—hawkeye.services-edge.paloaltonetworks.comThe default Public Cloud Server automatically resolves to the closest Public Cloud Server to where the inspected traffic originated. If a new Public Cloud Server is deployed in a region closer to where the inspected traffic originated, Enterprise DLP data and data processing is generated in that new region.
- APAC—apac.hawkeye.services-edge.paloaltonetworks.com
- Australia—au.hawkeye.services-edge.paloaltonetworks.com
- Brazil—hawkeye.services-edge.paloaltonetworks.comEnterprise DLP stores scans forwarded traffic, stores traffic contents evidence, time of scan, and snippets in a Brazil storage. However, Enterprise DLP stores incident metadata in the region where you deployed your Strata Cloud Manager tenant.
- Canada—ca.hawkeye.services-edge.paloaltonetworks.com
- Europe—eu.hawkeye.services-edge.paloaltonetworks.com
- France—fr.hawkeye.services-edge.paloaltonetworks.com
- India—in.hawkeye.services-edge.paloaltonetworks.com
- Japan—jp.hawkeye.services-edge.paloaltonetworks.com
- Switzerland—hawkeye.services-edge.paloaltonetworks.comEnterprise DLP stores scans forwarded traffic, stores traffic contents evidence, time of scan, and snippets in a Switzerland storage bucket. However, Enterprise DLP stores incident metadata in the region where you deployed your Strata Cloud Manager tenant.
- United Kingdom—uk.hawkeye.services-edge.paloaltonetworks.com
- United States—us.hawkeye.services-edge.paloaltonetworks.com
- Public Cloud Server for FedRAMPEnterprise DLP requires you add the following Public Cloud Server to successfully forward traffic for inspection and verdict rendering in FedRAMP environments.
- FedRAMP Moderate—hawkeye.services-edge.pubsec-cloud.paloaltonetworks.com
- FedRAMP High—gov-hawkeye.services-edge.paloaltonetworks.com
Click OK.Commit and push the new configuration to your managed firewalls.The Commit and Push command isn’t recommended for Enterprise DLP configuration changes. Using the Commit and Push command requires the additional and unnecessary overheard of manually selecting the impacted templates and managed firewalls in the Push Scope Selection.- Full configuration push from Panorama
- Select CommitCommit to Panorama and Commit.
- Select CommitPush to Devices and Edit Selections.
- Select Device Groups and Include Device and Network Templates.
- Click OK.
- Push your configuration changes to your managed firewalls that are using Enterprise DLP.
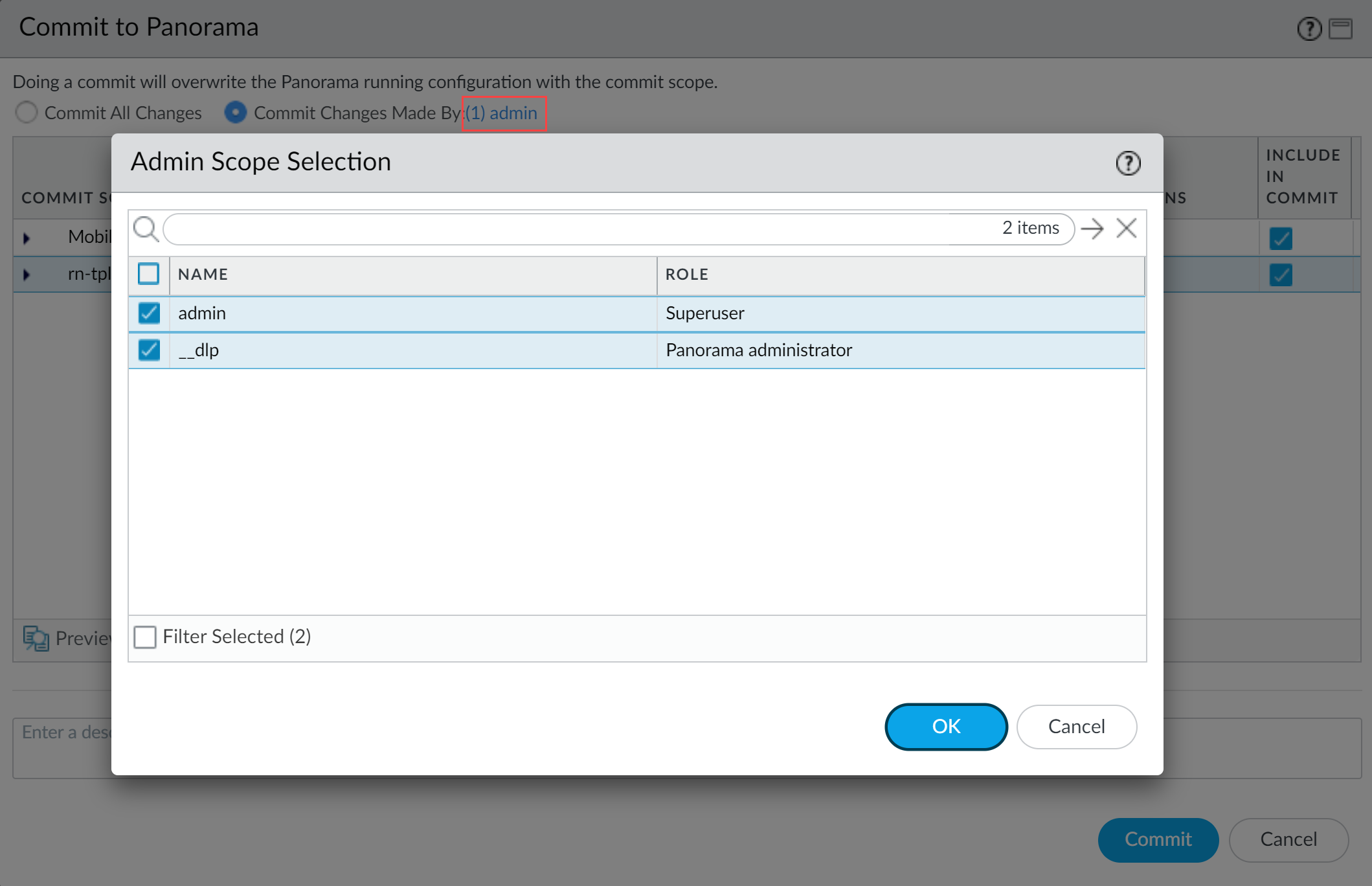
- Partial configuration push from PanoramaYou must always include the temporary __dlp administrator when performing a partial configuration push. This is required to keep Panorama and the DLP cloud service in sync.For example, you have an admin Panorama admin user who is allowed to commit and push configuration changes. The admin user made changes to the Enterprise DLP configuration and only wants to commit and push these changes to managed firewalls. In this case, the admin user is required to also select the __dlp user in the partial commit and push operations.
- Select CommitCommit to Panorama.
- Select Commit Changes Made By and then click the current Panorama admin user to select additional admins to include in the partial commit.In this example, the admin user is currently logged in and performing the commit operation. The admin user must click admin and then select the __dlp user. If there are additional configuration changes made by other Panorama admins they can be selected here as well.Click OK to continue.
![]()
- Commit.
- Select CommitPush to Devices.
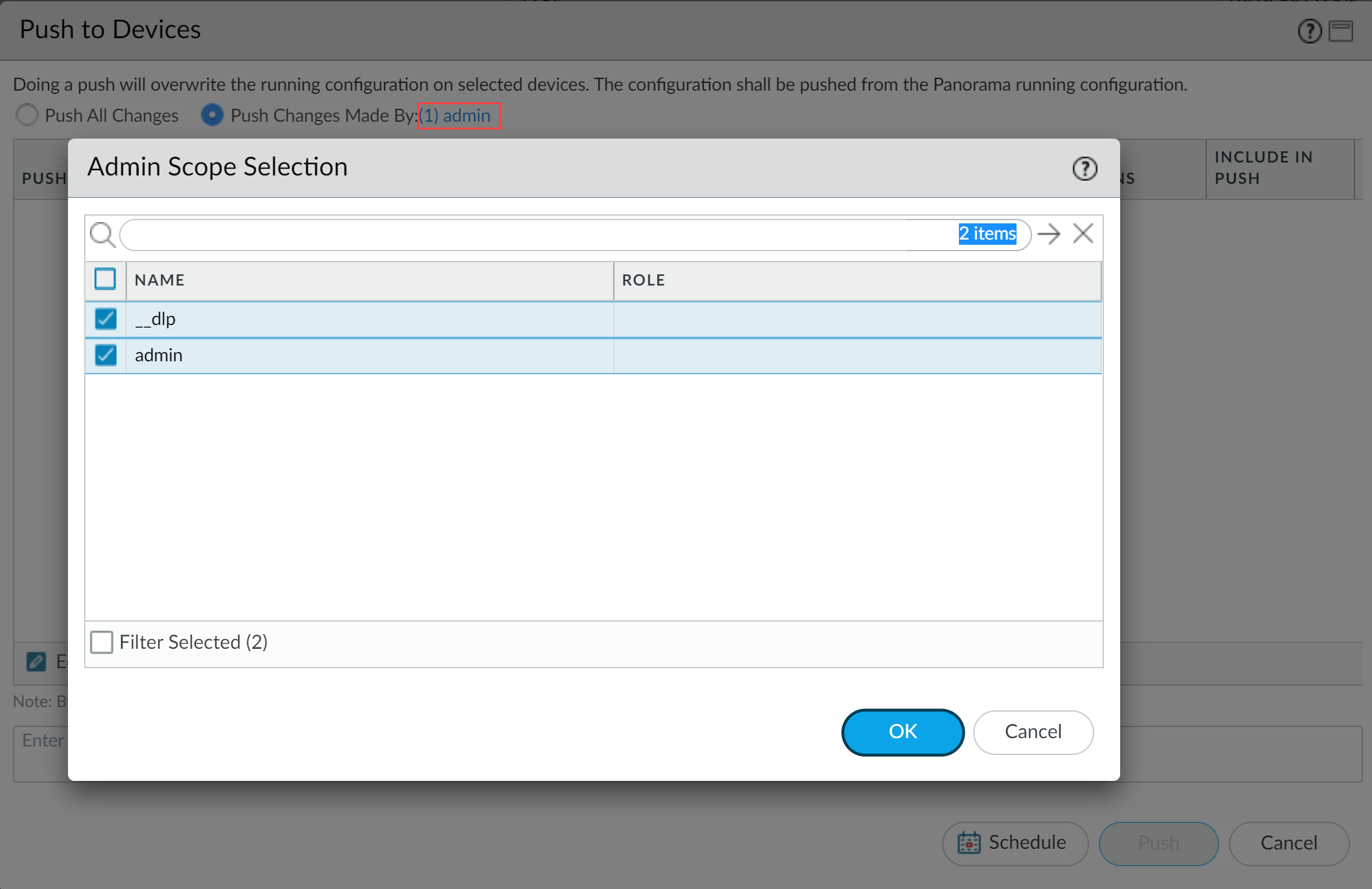
- Select Push Changes Made By and then click the current Panorama admin user to select additional admins to include in the partial push.In this example, the admin user is currently logged in and performing the push operation. The admin user must click admin and then select the __dlp user. If there are additional configuration changes made by other Panorama admins they can be selected here as well.Click OK to continue.
![]()
- Select Device Groups and Include Device and Network Templates.
- Click OK.
- Push your configuration changes to your managed firewalls that are using Enterprise DLP.