Download PDF
GlobalProtect
Remote Access VPN with Pre-Logon
Table of Contents
Expand All
|
Collapse All
GlobalProtect Docs
-
-
-
-
- 6.3
- 6.2
- 6.1
- 6.0
-
- 6.3
- 6.2
- 6.1
- 6.0
Remote Access VPN with Pre-Logon
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
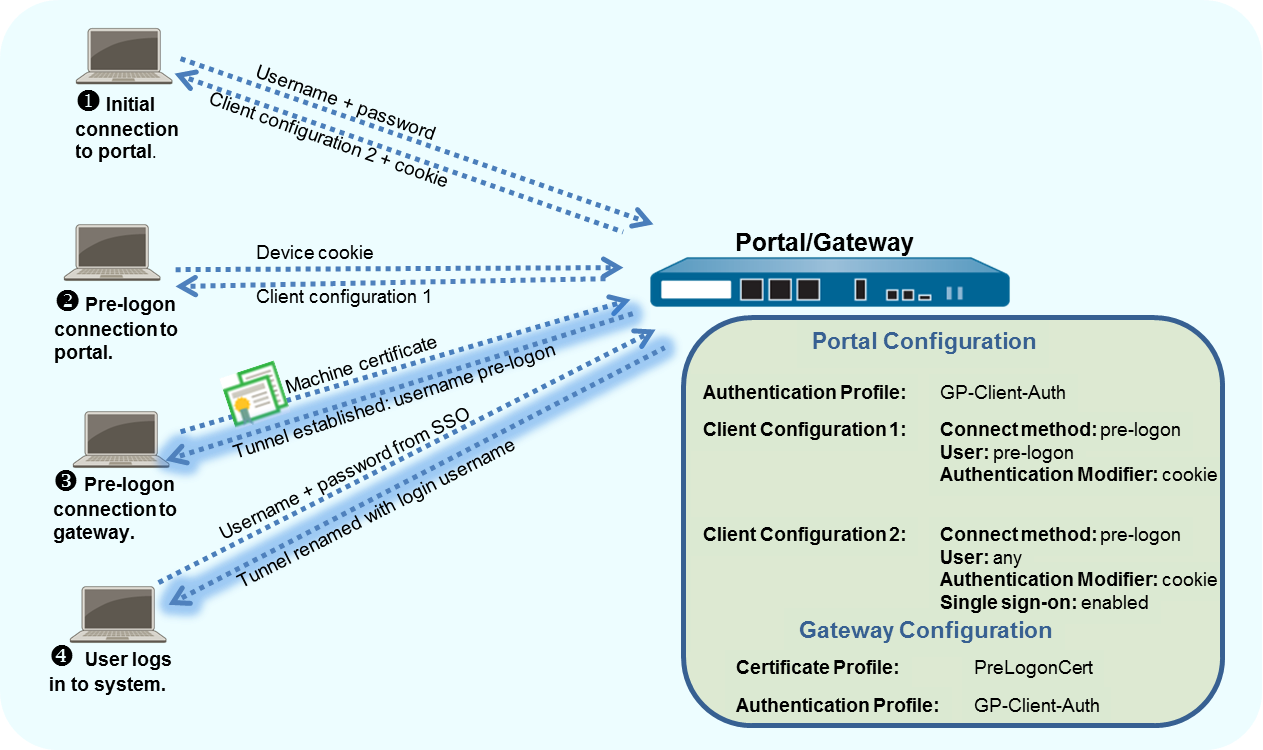
Pre-logon is a connect method
that establishes a VPN tunnel before a user logs in. The purpose
of pre-logon is to authenticate the endpoint (not the user) and
enable domain scripts or other tasks to run as soon as the endpoint
powers on. Machine certificates enable the endpoint to establish
a VPN tunnel to the GlobalProtect gateway. A common practice for
IT administrators is to install the machine certificate while staging
the endpoint for the user.
A pre-logon VPN tunnel has no username
association because the user has not logged in. To allow endpoints
to access resources, you must create security policies that match
the pre-logon user. These policies should allow access to only the
basic services for starting up the system, for example DHCP, DNS,
specific Active Directory services, antivirus, or operating system
update services. After the user authenticates to the gateway, the
GlobalProtect app reassigns the VPN tunnel to that user (the IP
address mapping on the firewall changes from the pre-logon endpoint
to the authenticated user).
As a best practice,
you must create security policies to allow access to only specific
services (for example, DHCP, DNS, specific Active Directory services, or
operating system update services) that are sufficient for machine
authentication and to enable services that are necessary for the
corporate network. We recommend that you create security policies
to deny pre-logon users access to other resources and applications.
Follow
these guidelines if the user’s endpoint is lost or stolen:
- You must revoke the machine certificate that is issued to the endpoint for pre-logon. Once the machine certificate is revoked for the pre-logon connect method, you cannot use the certificate to authenticate against the portal and gateway because authentication to the endpoint failed and the endpoint is unable to connect to the corporate network.
- You can quarantine lost or stolen endpoints by adding them to the quarantine list, block users from logging into the network from that endpoint, and to prevent VPN connections from these compromised endpoints.
- You must disable the stolen endpoint computer account in the Active Directory to block VPN connections from disabled machine accounts based on the presence of the endpoint serial number. When this feature is used, authentication attempts from the disabled computer account will fail while attempting to prevent VPN connections from the lost or stolen endpoint.
The GlobalProtect
Credential Provider logon screen for Windows 7 and Windows 10 endpoints
also displays the pre-logon connection status prior to user login,
which allows end users to determine whether they can access network
resources upon login. If the GlobalProtect app detects an endpoint
as internal, the logon screen displays the Internal pre-logon
connection status. If the Globalprotect app detects an endpoint
as external, the logon screen displays the Connected or Not
Connected pre-logon connection status.
Windows endpoints
behave differently from macOS endpoints with pre-logon. With macOS
endpoints, the pre-logon tunnel is torn down, and then a new tunnel
is created when the user logs in.
When a user requests
a new connection, the portal authenticates the user through an authentication
profile. The portal can also use an optional certificate profile
that validates the client certificate (if the configuration includes
a client certificate). In this case, the certificate must identify
the user. After authentication, the portal determines if the endpoint’s
GlobalProtect configuration is current. If the portal’s configuration
has changed, it pushes an updated configuration to the endpoint.
If
the configuration on the portal or a gateway includes cookie-based
authentication, the portal or gateway installs an encrypted cookie
on the endpoint. Subsequently, the portal or gateway uses the cookie
to authenticate users and refresh the agent configuration. If an
agent configuration profile includes the pre-logon connect method
in addition to cookie-authentication, the GlobalProtect components
can use the cookie for pre-logon.
If users never log in to
an endpoint (for example, a headless endpoint) or a pre-logon connection
is required on a system that a user has not previously logged in
to, you can let the endpoint initiate a pre-logon tunnel without
first connecting to the portal to download the pre-logon configuration.
To do this, you must override the default behavior by creating entries
in the Windows Registry or macOS plist.
The GlobalProtect
endpoint will then connect to the portal specified in the configuration,
authenticate the endpoint by using its machine certificate (as specified
in a certificate profile configured on the gateway), and then establish
the GlobalProtect connection. When the end-user subsequently logs
in to the machine, and if single sign-on (SSO) is enabled in the
agent configuration, the username and password are captured when
the user logs in. If SSO is not enabled in the agent configuration,
or SSO is not supported on the endpoint (for example, a macOS system) the
user’s credentials must be stored in the app (the Save
User Credentials option must be set to Yes).
After successful authentication to the gateway, the tunnel is renamed
(Windows) or rebuilt (macOS), and user and group-based policy can
be enforced.
This
example uses the GlobalProtect topology shown in GlobalProtect
VPN for Remote Access.
- (Required only on NGFW managed by Panorama or Strata Cloud Manager)Create Interfaces and Zones for GlobalProtect.Use the default virtual router for all interface configurations to avoid having to create inter-zone routing.
- For this example, select the NetworkInterfacesEthernet tab, and then configure the following settings:
- Select ethernet1/2.
- Select Layer 3 from the Interface Type drop-down.
- On the Config tab, Assign interface to the default Virtual Router and the l3-untrust Security Zone.
- On the IPv4 tab, click Add to select the 203.0.113.1 IP address (or the object that maps 203.0.113.1) or add a New Address to create a new object and address mapping (leave the address type as Static). For example, create a DNS “A” record that maps IP address 203.0.113.1 to gp.acme.com.
- Select NetworkInterfacesTunnel to Add a new tunnel interface.
- For the Interface Name, enter tunnel.2.
- On the Config tab, Assign Interface To a new Security Zone called corp-vpn and the default Virtual Router.
- Enable User Identification on the corp-vpn zone.
Create the security policy rules.This configuration requires the following policies (PoliciesSecurity):- For enhanced security, Add a rule that enables pre-logon users access to basic services that are required for the endpoint to come up, such as required authentication services, DNS, DHCP, and Microsoft Updates.You must ensure that all security policy rules are properly setup to allow pre-logon users access to only services that are required for the endpoint.Add a rule to deny pre-logon users access to all other resources and applications.Add any additional rules to enable different users or user groups access to specific resources and applications. Follow the Best Practice Internet Gateway_Security_Policy recommendations for creating these rules.Use one of the following methods to obtain a server certificate for the interface that is hosts the GlobalProtect portal and gateway:Select DeviceCertificate ManagementCertificates to manage certificates with the following criteria:
- Obtain a server certificate. Because the portal and gateway are on the same interface, the same server certificate can be used for both components.
- The CN of the certificate must match the FQDN, gp.acme.com.
- To enable endpoints to connect to the portal without receiving certificate errors, use a server certificate from a public CA.
Generate a machine certificate for each endpoint that connects to GlobalProtect, and then import the certificate into the personal certificate store on each machine.Although you can generate self-signed certificates for each endpoint, as a best practice, use your own public-key infrastructure (PKI) to issue and distribute certificates to your endpoints.- Issue client certificates to GlobalProtect clients and endpoints.Install certificates in the personal certificate store on the endpoints. (Local Computer store on Windows endpoints or System Keychain on macOS endpoints)Import the trusted root CA certificate from the CA that issued the machine certificates onto the portal and gateway(s).You do not have to import the private key.
- Download the CA certificate in Base64 format.Use the following steps to import the certificate onto each firewall that hosts a portal or gateway:
- Do one of the following:
- On Panorama, select DeviceCertificate ManagementCertificatesDevice Certificates and Import the certificate.
- On Strata Cloud Manager, select Manage ConfigurationNGFW and Prisma AccessObjectsCertificate Management and then Import the certificate.
- Enter a Certificate Name that identifies the certificate as your client CA certificate.
- Browse for the Certificate File that you downloaded from the CA.
- Set the File Format to Base64 Encoded Certificate (PEM).
- Click OK to save your certificate.
- On the Device Certificates tab, select the certificate that you just imported.
- Select the check box for Trusted Root CA, and then click OK.
On each firewall that hosts a GlobalProtect gateway, create a certificate profile to identify the CA certificate for validating the machine certificates.If you plan to use client certificate authentication to authenticate users when they log in to the system, make sure that the CA certificate that issues the client certificates is referenced in the certificate profile in addition to the CA certificate that issued the machine certificates (if they are different).- Do one of the following:
- On Panorama, select DeviceCertificatesCertificate ManagementCertificate Profile and Add a new certificate profile.
- On Strata Cloud Manager, select ManageConfigurationNGFW and Prisma AccessObjectsCertificate Management Certificate Profiles and then Add a new certificate profile.
Enter a Name to identify the profile, such as PreLogonCert.Set the Username Field to None.(Optional) If you also use client certificate authentication to authenticate users upon login, add the CA certificate that issued the client certificates if it is different from the one that issued the machine certificates.In the CA Certificates field, Add the CA certificate.Select the Trusted Root CA Certificate that you imported in step 5, and then click OK.Click OK to save the profile.Configure a GlobalProtect Gateway.See the topology diagram shown in GlobalProtect VPN for Remote Access.Although you must create a certificate profile for pre-logon access to the gateway, you can use either client certificate authentication or authentication profile-based authentication for logged in users. In this example, the same LDAP profile is used that is used to authenticate users to the portal.- Do one of the following:
- On Panorama, select NetworkGlobalProtectGateways.
- On Strata Cloud Manager, select Manage ConfigurationNGFW and Prisma AccessDevice SettingsGateways.
Add the following gateway configuration:Interface—ethernet1/2IP Address—203.0.113.1Server Certificate—GP-server-cert.pem issued by GoDaddyCertificate Profile—PreLogonCertAuthentication Profile—Corp-LDAPTunnel Interface—tunnel.2IP Pool—10.31.32.3 - 10.31.32.118Commit the gateway configuration.Configure the GlobalProtect Portals.Configure the Device details (networking parameters, authentication service profile, and certificate for the authentication server).- Do one of the following:
- On Panorama, select NetworkGlobalProtectGateways.
- On Strata Cloud Manager, select ManageConfigurationNGFW and Prisma AccessDevice SettingsGateways.
Add the following portal configuration:- Set Up Access to the GlobalProtect Portal
- Interface—ethernet1/2
- IP Address—203.0.113.1
- Server Certificate—GP-server-cert.pem issued by GoDaddy
- Certificate Profile—None
- Authentication Profile—Corp-LDAP
Define the GlobalProtect agent configurations for pre-logon users and for logged in users.You must create security policy rules to deny access to services not required for pre-logon users and only allow access to services that are mandatory for pre-logon users.Use a single configuration if you want pre-logon users to access the same gateways before and after they log in.To direct pre-logon users to different gateways before and after they log in, create two configuration profiles. In the first configuration’s User/User Group, select the pre-logon filter. With pre-logon, the portal first authenticates the endpoint (not the user) to set up a connection even though the pre-logon parameter is associated with the user. Subsequently, the portal authenticates the user when he or she logs in.After the portal authenticates the user, it deploys the second configuration. In this case, User/User Group is any.As a best practice, enable SSO in the second configuration so that the correct username is immediately reported to the gateway when the user logs in to the endpoint. If SSO is not enabled, the saved username in the Agent settings panel is used.Add one of the following configurations:- Use the same gateway before and after pre-logon users log in:Use single sign-on—enabledConnect Method—pre-logonExternal Gateway Address—gp1.acme.comUser/User Group—anyAuthentication Override—Cookie authentication for transparently authenticating users and for configuration refresh
- Use separate gateways for pre-logon users before and after they log in:First Agent Configuration:Connect Method—pre-logonExternal Gateway Address—gp1.acme.comUser/User Group—pre-logonAuthentication Override—Cookie authentication for transparently authenticating users and for configuration refreshSecond Agent Configuration:Use single sign-on—enabledConnect Method—pre-logonExternal Gateway Address—gp2.acme.comUser/User Group—anyAuthentication Override—Cookie authentication for transparently authenticating users and for configuration refreshMake sure the pre-logon configuration is first in the list of configurations. If it is not, select it and click Move Up.
Save the GlobalProtect configuration.Click Commit.(Optional) If users never log in to an endpoint (for example, a headless endpoint), or a pre-logon connection is required on an endpoint that users have not previously logged in to, create the Prelogon registry entry on the endpoint.You must also pre-deploy the default portal IP address.For more information about registry settings, see Deploy App Settings Transparently.- Go to the following Windows Registry location to view the list of GlobalProtect settings:HKEY_LOCAL_MACHINE\SOFTWARE\Palo Alto Networks\GlobalProtect\PanSetupSelect EditNewString Value to create the following registry entries:
- Create a String Value named Prelogon with a value of 1. This setting enables GlobalProtect to initiate a connection before the user logs in to the endpoint.
- Create a String Value named Portal that specifies the IP address or hostname of the default portal for the GlobalProtect endpoint.
- For this example, select the NetworkInterfacesEthernet tab, and then configure the following settings:
