Device Security
Perform a Vulnerability Scan Using Tenable Security Center
Table of Contents
Expand All
|
Collapse All
Device Security Docs
Perform a Vulnerability Scan Using Tenable Security Center
Initiate and manage vulnerability scans from Device Security using Tenable Security Center
to identify security risks on IoT devices.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
One of the following subscriptions:
One of the following Cortex XSOAR setups:
|
Because active scanning can be disruptive to the services running on a scanned
device, only account owners have permission to perform vulnerability scans by
default. Owners can also set scanning permissions per administrator account,
thereby delegating it to just a few individuals.
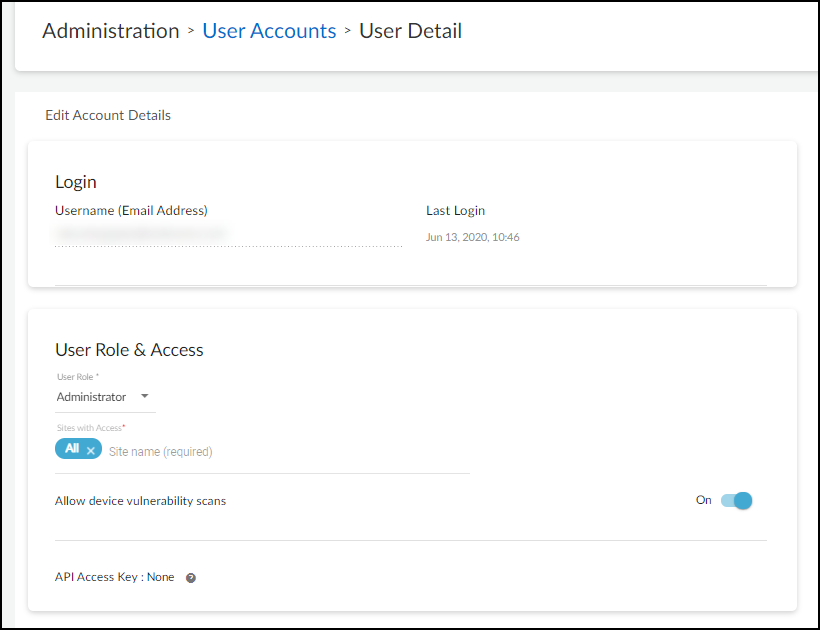
Standalone portal By default, vulnerability scanning is disabled for
new administrator accounts. To enable it, log in to the Device Security portal
as an owner, click AdministrationUser Accounts, and then click the email address (username) of an administrator for
whom you want to enable vulnerability scanning. Slide the
Allow device vulnerability scans toggle to
On and then Save.
When using the Device Security standalone portal, the ability to do
vulnerability scanning is only available to owners and administrators. There is
no option to enable vulnerability scanning for deployment and read-only users.
When using Device Security in Strata Cloud Manager, the ability to do
vulnerability scanning is available to all accounts with the Superuser role.
There is no option to enable or disable vulnerability scanning for individual
users.
- Before initiating a Tenable Security Center vulnerability scan, create a job to run the "Get Tenable SC Policies, Repositories and Reports - PANW Device Security 3rd Party Integration" playbook.Run this playbook to get Tenable Security Center asset information to Device Security. Without running this playbook first, Device Security can't learn information from the Tenable Security Center vulnerability scan.Initiate a Tenable Security Center vulnerability scan from Device Security.
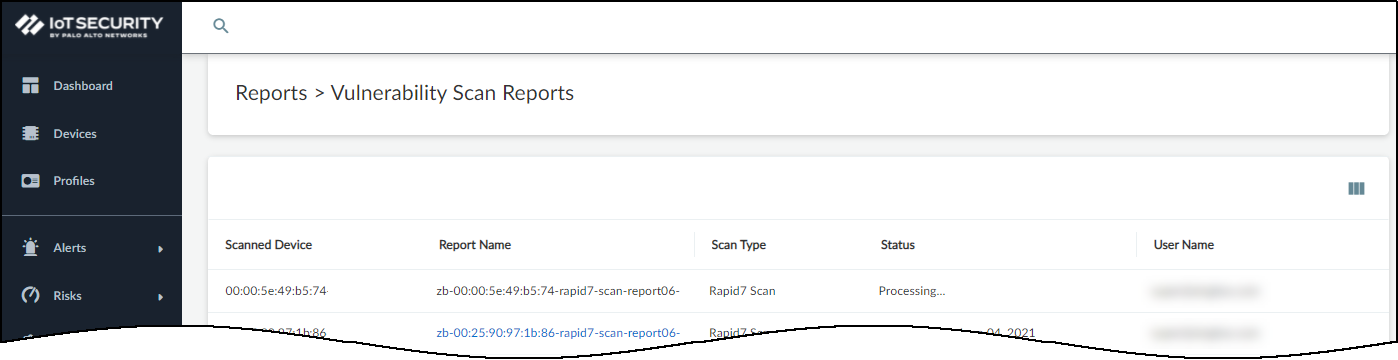
- Log in as an owner or administrator who has vulnerability scanning enabled, click AssetsDevices, and then click the entry in the Device Name column for the device you want to scan.Because Device Security only supports one vulnerability scan of a device at a time, make sure no other scans of this device are in progress.Click ReportsVulnerability Scan Reports and check the Status column. If you see Processing… for the device you want to scan, wait until the current scan finishes before starting a new one.
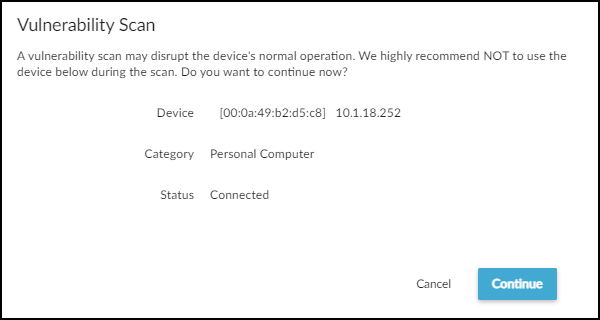
![]() When you see that the device isn't already being scanned, you can continue with a new scan.Only initiate a scan of a device that's in the Tenable Security Center inventory and that's not currently active (and will remain inactive until the scan completes).Click AssetsDevices, and then click the entry in the Device Name column for the device you want to scan.At the top of the Device Details page, click the Action menu (three vertical dots) and then click Scan.Read the caution about scanning active devices and, if the device is currently inactive, Continue.
When you see that the device isn't already being scanned, you can continue with a new scan.Only initiate a scan of a device that's in the Tenable Security Center inventory and that's not currently active (and will remain inactive until the scan completes).Click AssetsDevices, and then click the entry in the Device Name column for the device you want to scan.At the top of the Device Details page, click the Action menu (three vertical dots) and then click Scan.Read the caution about scanning active devices and, if the device is currently inactive, Continue.![]() Set parameters for the vulnerability scan you want Tenable Security Center to perform.Select the scan engine to perform the vulnerability scan and a profile to define the type of scan to run. Tenable Security Center provides a set of predefined profiles. You can also define and use your own.Scan the device.Depending on the type of scan you choose, it can take anywhere from a few minutes to half an hour, and sometimes even longer. However, it's common for scans to take 20-30 minutes. If there is an issue, such as the scanner being unable to reach the target device, the effort eventually times out after two hours.If the scan discovers any Common Vulnerabilities and Exposures (CVEs), Device Security adds them to the Risks section on the Device Details page and to the Vulnerabilities inventory. Device Security learns the vulnerability CVE ID number, severity level (CVSS), and service port number from Tenable Security Center. Device Security retrieves a description for the vulnerability from the NIST page for the CVE.After the scan completes, view the results.You have two options to view the results:
Set parameters for the vulnerability scan you want Tenable Security Center to perform.Select the scan engine to perform the vulnerability scan and a profile to define the type of scan to run. Tenable Security Center provides a set of predefined profiles. You can also define and use your own.Scan the device.Depending on the type of scan you choose, it can take anywhere from a few minutes to half an hour, and sometimes even longer. However, it's common for scans to take 20-30 minutes. If there is an issue, such as the scanner being unable to reach the target device, the effort eventually times out after two hours.If the scan discovers any Common Vulnerabilities and Exposures (CVEs), Device Security adds them to the Risks section on the Device Details page and to the Vulnerabilities inventory. Device Security learns the vulnerability CVE ID number, severity level (CVSS), and service port number from Tenable Security Center. Device Security retrieves a description for the vulnerability from the NIST page for the CVE.After the scan completes, view the results.You have two options to view the results:- Click Devicesdevice_name and then click the Vulnerability Report Ready chip at the top of the page.
- View the Vulnerability Scan Reports page, and then click the link in the Report Name column for the scanned device whose report you want to see. This downloads the report as a PDF.