Device Security
Set up Device Security and Cortex XSOAR for Microsoft Defender XDR Integration
Table of Contents
Expand All
|
Collapse All
Device Security Docs
Set up Device Security and Cortex XSOAR for Microsoft Defender XDR Integration
Set up Device Security and Cortex XSOAR to integrate with Microsoft Defender XDR.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
One of the following subscriptions:
One of the following Cortex XSOAR setups:
|
Configure Cortex XSOAR with a Microsoft Defender XDR integration instance and
jobs to import device and vulnerability information from Microsoft Defender XDR. You
can set the jobs to run on demand or at regular intervals. The configuration
requires the following information from Microsoft Defender XDR:
- Domain URL for Microsoft Defender XDR
- Tenant ID
- Client ID
- Client Secret ID
- Log in to Device Security, and from there access the Microsoft Defender XDR integration settings in Cortex XSOAR.
- Log in to Device Security and then click Integrations.Launch Cortex XSOAR from Device Security.Device Security uses Cortex XSOAR to integrate with Microsoft Defender XDR. The settings you must configure are in the Cortex XSOAR interface. To access these settings from the Integrations page, Launch Cortex XSOAR. The Cortex XSOAR interface opens in a new browser tab or window.Find the Microsoft Defender XDR integration.Click Settings in the left navigation menu. Search for Microsoft Defender XDR to locate it among other integrations.
![]() Configure the Microsoft Defender XDR integration instance.
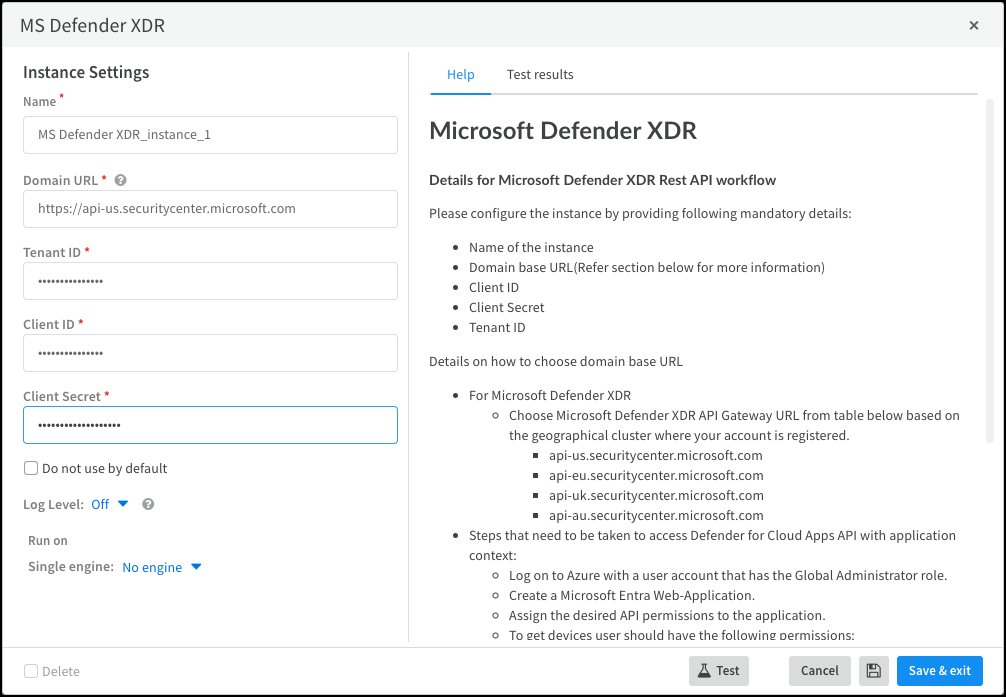
Configure the Microsoft Defender XDR integration instance.- Click Add instance to open the settings panel.In the settings panel, configure the following settings:
- Name: Use the default name of the instance or enter a new one.Remember the instance name because you're going to use it again when creating the jobs that Cortex XSOAR runs to gather device data and vulnerability information from Microsoft Defender XDR.
- Domain URL: Select the Microsoft Defender XDR API Gateway URL based on the geographical cluster where your account is registered. The possible domain URL options are:
- https://api-us.securitycenter.microsoft.com
- https://api-eu.securitycenter.microsoft.com
- https://api-uk.securitycenter.microsoft.com
- https://api-au.securitycenter.microsoft.com
- Tenant ID: Enter the Tenant ID from your Microsoft application.
- Client ID: Enter the Client ID from your Microsoft application.
- Client Secret: Enter the Client Secret ID from your Microsoft application.
- Run on Single engine: Choose No engine.
![]() When finished, click Test to test the integration instance.If the test is successful, a Success message appears. If not, check that the settings were entered correctly, and then test the configuration again.
When finished, click Test to test the integration instance.If the test is successful, a Success message appears. If not, check that the settings were entered correctly, and then test the configuration again.![]() After the test succeeds, click Save & exit to save your changes and close the settings panel.Create a job for Cortex XSOAR to query Microsoft Defender XDR for devices and device attributes and import them to Device Security.
After the test succeeds, click Save & exit to save your changes and close the settings panel.Create a job for Cortex XSOAR to query Microsoft Defender XDR for devices and device attributes and import them to Device Security.- Create a new Cortex XSOAR job.Copy the name of the instance you created, click Jobs near the bottom of the left navigation menu, and then click New Job at the top of the page.Configure the new Cortex XSOAR job.In the New Job panel that appears, configure the following and leave the other settings at their default values:
- Recurring: Select this if you want to periodically import device information from Microsoft Defender XDR. Clear it if you want to import device details on demand.
- Every: If you select Recurring, enter a number and set the interval value (Minutes, Hours, Days, or Weeks) and select the days on which to run the job. If you don't select specific days, then the job will run every day by default. This determines how often Cortex XSOAR queries Microsoft Defender XDR for information about device details.
- Name: Enter a name for the job.
- Playbook: Choose Import MS Defender devices to PANW IoT cloud.
- Integration Instance Name: Paste the instance name of your Microsoft Defender XDR integration instance.
Click Create new job and verify that the job appears in the Jobs list.Create a job for Cortex XSOAR to query Microsoft Defender XDR for vulnerabilities and vulnerability details and import them to Device Security.- Create a new Cortex XSOAR job.Stay on the Jobs page, and click New Job at the top of the page.Configure the new Cortex XSOAR job.In the New Job panel that appears, configure the following and leave the other settings at their default values:
- Recurring: Select this if you want to periodically import vulnerabilities and vulnerability information from Microsoft Defender XDR. Clear it if you want to import vulnerability information on demand.
- Every: If you select Recurring, enter a number and set the interval value (Minutes, Hours, Days, or Weeks) and select the days on which to run the job. If you don't select specific days, then the job will run every day by default. This determines how often Cortex XSOAR queries Microsoft Defender XDR for information about vulnerabilities.
- Name: Enter a name for the job.
- Playbook: Choose Import MS Defender Vulnerabilities to PANW IoT cloud.
- Integration Instance Name: Paste the same instance name you used for the device details job.
- Optional Playbook Duration in days: Choose the number of days that you want to poll for discovered vulnerabilities. If the field is blank, then Cortex XSOAR requests vulnerabilities discovered in the last 30 days by default.
- Optional Import vulnerabilities by CVE levels: Choose the CVE severity levels for vulnerabilities that you want to import. You can select multiple levels at once. If no level is selected, then Cortex XSOAR imports only CVEs with a severity level of Critical by default.
Click Create new job and verify that the job appears in the Jobs list.Enable the jobs and run them.- Check the job status for the jobs you created.If the jobs are Disabled, select the appropriate check boxes and then click Enable.Run the device details import job.After you enable the jobs, select only the check box for the device details import job and click Run now. The Run Status should change from Idle to Running.Run the vulnerabilities import job.Once the device details import job's Run Status changes to Completed, deselect that job. Select the check box for the vulnerabilities import job and click Run now. The Run Status should change from Idle to Running.For either job, if you selected Recurring, Cortex XSOAR queries Microsoft Defender XDR for information at the defined intervals and forwards imported information to Device Security.If you cleared Recurring, Cortex XSOAR immediately queries Microsoft Defender XDR and forwards imported information to Device Security.Optional Create additional integration instances, and configure and run jobs for each integration instance as needed.Return to Device Security and check the status of the Microsoft Defender XDR integration.An integration instance can be in one of the following four states, which Device Security displays in the Status column on the Integrations page:
- Active — the integration was configured and enabled and is functioning properly.Disabled — either the integration was configured but intentionally disabled or it was never configured and a job that references it is enabled and running.
- Error — the integration was configured and enabled but is not functioning properly, possibly due to a configuration error or network condition.
- Inactive — the integration was configured and enabled but no job has run for at least the past 60 minutes.
When you see that the status of an integration instance is Active, its setup is complete.