Device Security
Apply Access Control Lists through Cisco ISE
Table of Contents
Expand All
|
Collapse All
Device Security Docs
Apply Access Control Lists through Cisco ISE
Integrate Device Security with Cisco ISE and apply ACLs
to IoT devices.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
One of the following subscriptions:
One of the following Cortex XSOAR setups:
|
In addition to identifying IoT devices for
Cisco ISE to expand access control and policy enforcement to include
IoT, Device Security can also generate access control lists (ACLs)
based on observed traffic. The ACLs provide a list of rules that
allow the traffic you want with a rule at the end to deny everything else
and thereby block all unwanted traffic.
Device Security supports
the automatic generation of ACL rule sets per device profile and
the automatic creation of authorization profiles using one of the
following three enforcement models in Cisco ISE:
- Downloadable ACL (dACL)
- Security Group-based ACL (SG-ACL)
- WLAN controller ACL (WLC ACL)
The first two
types are ACLs that Cisco ISE supports, and the last type is an ACL
that Cisco WLAN controllers support. ISE applies dACLs and SG-ACLs
to IoT devices through network devices like switches when devices
join the network and go through the authentication and authorization
process. ISE downloads WLC ACLs to WLAN controllers and ISE enforces
the ACL rules on wireless clients when they join a wireless network
and go through processes like authentication, re-authentication, and
change of authorization (CoA). When a switch or WLAN controller
applies an ACL to a device, its traffic is permitted or denied as
specified in the rule set.
In slightly more detail, here’s
how Cisco ISE applies these different types of access control to
IoT devices:
- When a switch or wireless controller receives an authentication request from an IoT device, it extracts device attributes from the request and then provides them to ISE. ISE then checks if the attributes match a device profile. For dACLs and WLC ACLs, it looks up the device profile in a profiling policy. For SG-ACLs, ISE checks for it in a network device authorization policy.
- If the IoT device matches a device profile, ISE next checks its policy rule sets to see if there’s one with rule conditions for this device profile.
- If ISE finds a match, it then checks the rule results, which indicate the action to take. For dACL and WLC ACL, the rule results are in authorization profiles. For SG-ACL, they are in a matrix of source and destination device profiles that are used as security groups.
- Either ISE downloads the dACL or SG-ACL rule set to a switch or sends the WLC ACL name to a wireless controller for ACL enforcement.
- Finally, either the switch or controller enforces the rules in the dACL, WLC ACL, or SG-ACL on traffic from the IoT device.
You
can create ACL rule sets for devices at the device profile level,
not for individual devices.
- Open the recommended ACL rule set for a device profile.
- Click Profiles > profile_name.On the Profile Details page that opens, there’s an ACL Rule Sets widget. If you have Cisco ISE integration enabled, you can create one or more new ACL rule sets to control what the devices in this profile can access. After you create them, they appear in a list in this widget.If a Cisco ISE integration isn’t enabled, you can see the ACL Rule Sets widget but you won’t be able to create any rule sets.
![]()
- Click Create in the ACL Rule Sets widget.The Recommended ACL Rule Set appears. This is the default rule set and is populated with rules based on traffic that Device Security has observed from the various members belonging to this profile.
![]()
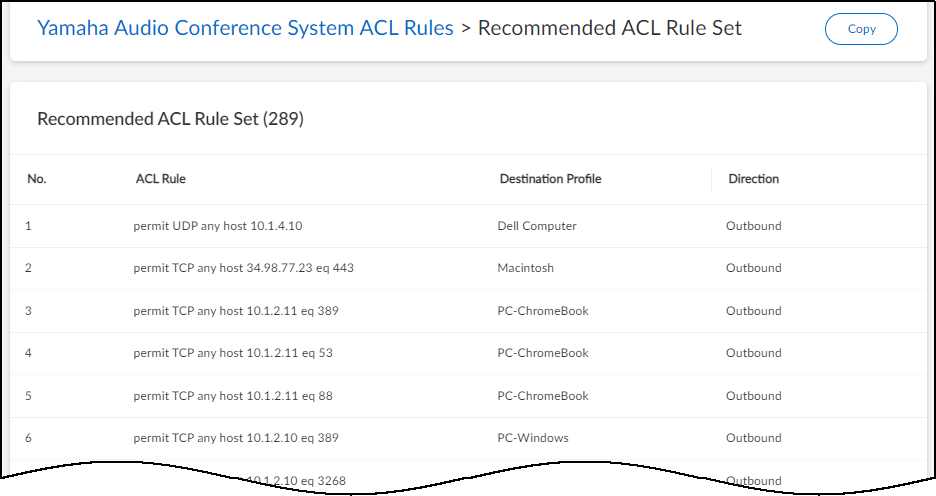
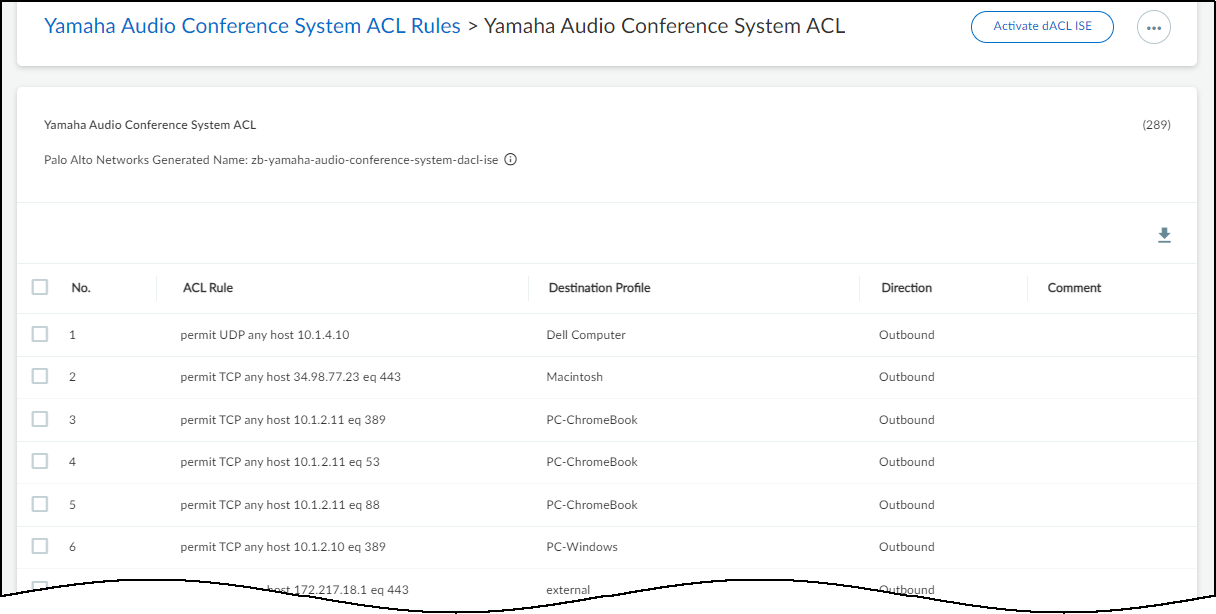
- Click View to see the rules that constitute the rule set.
![]() The source profile is unstated because it’s always this device profile. For destinations with devices that Device Security has identified, typically because they are in the local network that Device Security is monitoring, it displays the appropriate destination profile. For destinations that Device Security cannot identify, typically because they’re beyond the local network, it categorizes them into a destination profile called external.Because these automatically generated rules are based on normal device behavior, each ACL rule permits a type of network behavior. The rule specifies the protocol type it is permitting from “any” IP address within the source profile to the specified host IP address within the destination profile. If the rule includes a destination port number, traffic using the specified protocol is only permitted to the destination host on that port. If no port number is included, then traffic using the protocol is permitted to the destination on any port.The Direction column indicates if the traffic is outbound or inbound from the perspective of the source profile. It’s outbound if traffic originates from a device in the source profile and is bound for a destination in the destination profile, and it’s inbound if traffic originates in the destination profile and is destined for a device in the source profile.
The source profile is unstated because it’s always this device profile. For destinations with devices that Device Security has identified, typically because they are in the local network that Device Security is monitoring, it displays the appropriate destination profile. For destinations that Device Security cannot identify, typically because they’re beyond the local network, it categorizes them into a destination profile called external.Because these automatically generated rules are based on normal device behavior, each ACL rule permits a type of network behavior. The rule specifies the protocol type it is permitting from “any” IP address within the source profile to the specified host IP address within the destination profile. If the rule includes a destination port number, traffic using the specified protocol is only permitted to the destination host on that port. If no port number is included, then traffic using the protocol is permitted to the destination on any port.The Direction column indicates if the traffic is outbound or inbound from the perspective of the source profile. It’s outbound if traffic originates from a device in the source profile and is bound for a destination in the destination profile, and it’s inbound if traffic originates in the destination profile and is destined for a device in the source profile.
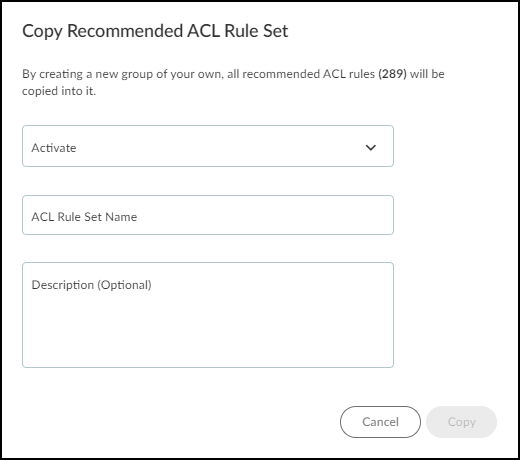
Create a new ACL rule set based on the recommended set.You can also click + to create a new rule set based on the recommended rule set or on another one you’ve previously defined. When creating a new rule set, you have the same options explained below with the additional option of copying rules from a set of your choice.- Click Copy.The Copy Recommended ACL Rule Set dialog box appears.
![]()
- In the Activate field, choose one of these ACL rule set options:dACL ISE – A downloadable access control list consisting of a single rule set containing all the individual rules that IoT Security sends through XSOAR to ISE together with an automatically generated authorization profile referencing the dACL.When Device Security sends these through XSOAR to ISE, ISE adds them if they’re new or update an existing dACL and profile and then download the ACL to switches and WLAN controllers as needed.SGACL ISE – An access control list consisting of multiple groups of rules that share a given source profile and destination profile for use as TrustSec security groups in ISE.As with downloadable ACLs, when Device Security sends these security groups through XSOAR to ISE, ISE adds them as new security groups or update existing ones and then download them to switches and WLAN controllers as needed.Cisco WLAN Controller – An access control list similar to dACL that Device Security sends through XSOAR to Cisco WLAN controllers rather than to ISE.When sending an ACL rule set to WLAN controllers to use for their wireless clients, Device Security also sends a message to ISE informing it that the WLAN controller will be applying this ACL so that ISE will update the corresponding authorization profile.
- Enter a name for the ACL rule set.After you choose a type of access control list and enter a name, the Copy button becomes active.This name is only for use in Device Security, which automatically generates a new name for the ACL to send to Cisco ISE.
- Enter an optional note or comment for future reference in the Description field.
- Click Copy.The new ACL rule set appears.
![]() The ACL rule set name appears near the top of the page. All automatically generated ACL rule set names in the Device Security portal are lowercase, use hyphens, begin with zb-, and end with -dacl-ise. However, in XSOAR the capitalization changes, hyphens become underscores, and the prefix and suffix switch to iot_ and _dACL. For example: (Device Security) zb-yamaha-audio-conference-system-dacl-ise becomes (XSOAR and Cisco ISE) iot_Yamaha_Audio_Conference_System_dACL
The ACL rule set name appears near the top of the page. All automatically generated ACL rule set names in the Device Security portal are lowercase, use hyphens, begin with zb-, and end with -dacl-ise. However, in XSOAR the capitalization changes, hyphens become underscores, and the prefix and suffix switch to iot_ and _dACL. For example: (Device Security) zb-yamaha-audio-conference-system-dacl-ise becomes (XSOAR and Cisco ISE) iot_Yamaha_Audio_Conference_System_dACL
Modify the ACL rule set if necessary.Hover your cursor over a row to display the Edit icon for the ACL rule, an option to add a comment (or edit an existing comment), and an icon to remove a rule.![]() Select one or more rows to display options to add a new rule above the selection (this option only appears when you select a single row), move the selected row or rows up or down—which is important because the order of the rules determines how they’re applied; that is, from the top down—or remove the selections from the rule set.
Select one or more rows to display options to add a new rule above the selection (this option only appears when you select a single row), move the selected row or rows up or down—which is important because the order of the rules determines how they’re applied; that is, from the top down—or remove the selections from the rule set.![]() Click Activate to activate the ACL rule set.Although you can create multiple ACL rule sets, only one for each ACL type can be activated at a time. At most, you can have three active rule sets: one for dACL, one for SGACL, and one for Cisco WLAN controller ACL. If you activate a new rule set when another one for the same ACL type is already activated, Device Security will deactivate the first rule set and then activate the second one.When you activate an ACL rule set in Device Security, it sends all configured ISE instances a dACL or SGACL, or it sends Cisco WLAN controllers a Cisco WLAN controller ACL. Device Security also sends an automatically generated authorization profile (for dACL and Cisco WLAN controller ACL rule sets) or automatically generated security groups and egress policy matrix entries (for SGACL rule sets).You can see downloadable ACLs and Cisco WLAN controller ACLs in Cisco ISE by logging in to the UI and clicking PolicyPolicy ElementsResultsAuthorizationDownloadable ACLs.
Click Activate to activate the ACL rule set.Although you can create multiple ACL rule sets, only one for each ACL type can be activated at a time. At most, you can have three active rule sets: one for dACL, one for SGACL, and one for Cisco WLAN controller ACL. If you activate a new rule set when another one for the same ACL type is already activated, Device Security will deactivate the first rule set and then activate the second one.When you activate an ACL rule set in Device Security, it sends all configured ISE instances a dACL or SGACL, or it sends Cisco WLAN controllers a Cisco WLAN controller ACL. Device Security also sends an automatically generated authorization profile (for dACL and Cisco WLAN controller ACL rule sets) or automatically generated security groups and egress policy matrix entries (for SGACL rule sets).You can see downloadable ACLs and Cisco WLAN controller ACLs in Cisco ISE by logging in to the UI and clicking PolicyPolicy ElementsResultsAuthorizationDownloadable ACLs.- In the Cisco ISE UI, all downloadable ACLs from Device Security begin with the prefix iot_ and end with the suffix _dACL. For example: iot_Yamaha_Audio_Conference_System_dACL
- Similarly all Cisco WLAN controller ACLs from Device Security begin with the prefix iot_ and end with the suffix _WLC. For example: iot_Yamaha_Audio_Conference_System_WLCThe Device Security term Cisco WLAN controller is the same thing as the terms Airspace ACL (used on Cisco ISE) and Cisco WLC ACL (used on Cisco WLAN controllers).
You can see authorization profiles in Cisco ISE by clicking PolicyPolicy ElementsResultsAuthorizationAuthorization Profiles. All automatically generated authorization profiles that Device Security sends ISE begin with the prefix iot_ and end with the suffix _authz_profile. For example: iot_Yamaha_Audio_Conference_System_authz_profileIoT Security and XSOAR create SGACLs, security groups, and egress policies in Cisco ISE on the following pages:- SGACL: PolicyTrustSecComponentsSecurity Group ACLsA security group ACL name is a concatenation of iot + source_profile_name + _destination_ profile_name_ + sgACL. For example: iotYamaha_Audio_Conference_System_external_sgACL
- Security groups: PolicyTrustSecComponentsSecurity GroupsThe source and destination security group names in Cisco ISE are the same as the source and destination device profile group names in Device Security.
- Egress policy: After creating security group ACLs and security groups, XSOAR uses them to automatically create egress policy matrix entries on Work CentersTrustSec PolicyEgress PolicyMatrix. In addition, there are default options configured in the matrix entries such as Status = Monitor, which the ISE administrator can change before applying the policy.
In summary, you are providing Cisco ISE administrators with the necessary components for creating authorization policies to use as they want. Once they validate the ACLs and authorization profiles and use them in authorization policies, they will then activate and deploy them in ISE.