Device Security
Set up Cisco ISE to Identify IoT Devices
Table of Contents
Expand All
|
Collapse All
Device Security Docs
Set up Cisco ISE to Identify IoT Devices
Integrate Device Security through Cortex XSOAR with Cisco ISE to identify IoT
devices for VLAN segmentation.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
One of the following subscriptions:
One of the following Cortex XSOAR setups:
|
To send IoT device data to ISE, configure
the following on your Cisco ISE system:
- Enable External RESTful Services (ERS) with read/write permission
- Create an ERS admin user account that the XSOAR engine will use to authenticate itself to ISE when sending it data
- Create custom endpoint attributes for the IoT device data that Device Security sends
Cisco ISE configuration
instructions are based on Cisco Identity Services Engine version
2.4.
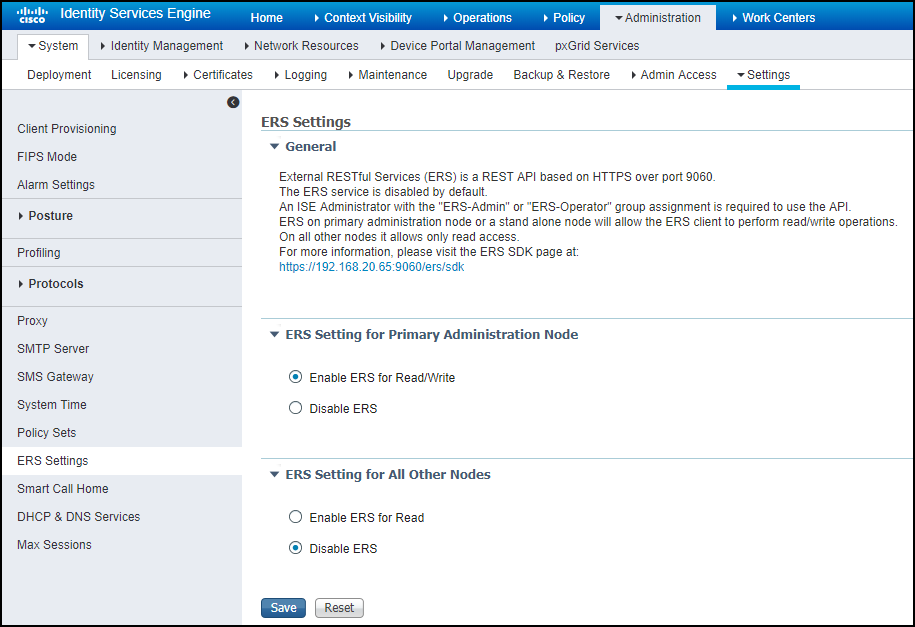
- Enable External RESTful Services.Log in to the Cisco Identity Services Engine management interface, click AdministrationSystemSettingsERS Settings, select Enable ERS for Read/Write in the ERS Setting for Primary Administration Node section, and then click Save.The setting in ERS Setting for All Other Nodes is not relevant to IoT Security integration.
![]() Create an ERS admin account.
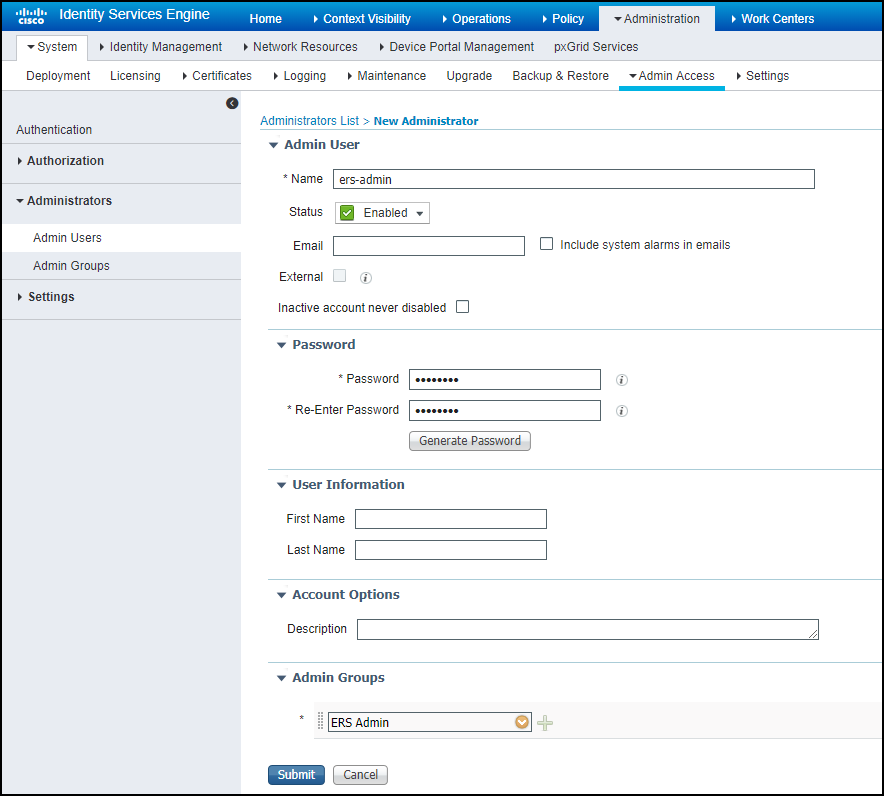
Create an ERS admin account.- Click AdministrationSystemAdmin AccessAdministratorsAdmin Users and then click AddCreate an Admin User.
- Enter the following on the New Administrator page and leave the other settings as they are:Name: Enter a name for the admin user account. This is the account that the XSOAR engine will use when making an HTTPS connection to the Cisco ISE system.Status: EnabledPassword and Re-Enter Password: Enter a password for the admin user account.Admin Groups: ERS Admin (This is a predefined admin group.)
![]()
- Submit the configuration.
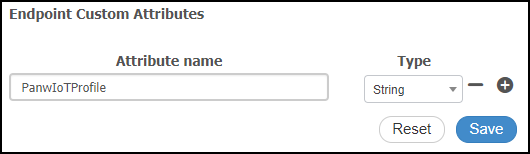
Create custom Device Security attributes.- Click AdministrationIdentity ManagementSettingsEndpoint Custom Attributes, enter PanwIoTProfile in the Attribute name field, choose String from the Type drop-down list, and then click Save.If you want to enter a different attribute name for the profile here, change the attribute name for the profile in Cortex XSOAR so they match each other. Similarly, if you customize any other attribute names in ISE, change the default names for their corresponding attributes in XSOAR. The attribute names are editable in the incremental and bulk export job settings for Cisco ISE in the Cortex XSOAR module. See Configure Device Security and Cortex XSOAR.
![]()
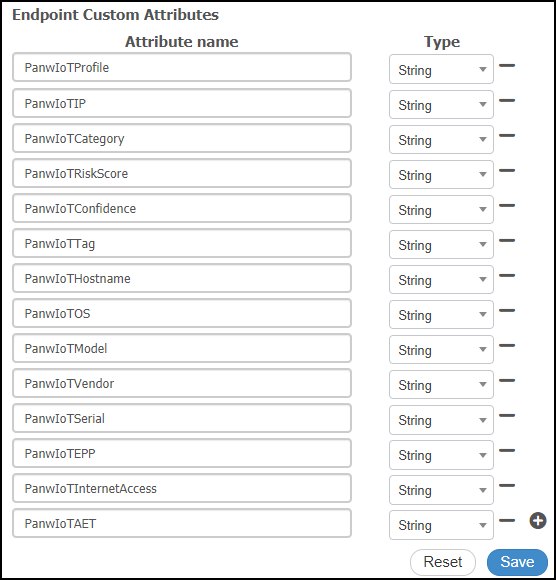
- Add more endpoint custom attributes, such as the following:PanwIoTProfile, PanwIoTIP, PanwIoTCategory, PanwIoTRiskScore, PanwIoTConfidence, PanwIoTTag, PanwIoTHostname, PanwIoTOS, PanwIoTModel, PanwIoTVendor, PanwIoTSerial, PanwIoTEPP, PanwIoTInternetAccess, PanwIoTAET
![]()
- Continue adding more custom endpoint attributes to ISE with names that match the attributes that Device Security sends through Cortex XSOAR.
- When done, Save the configuration.
Example: Assign VLANs by Device Type
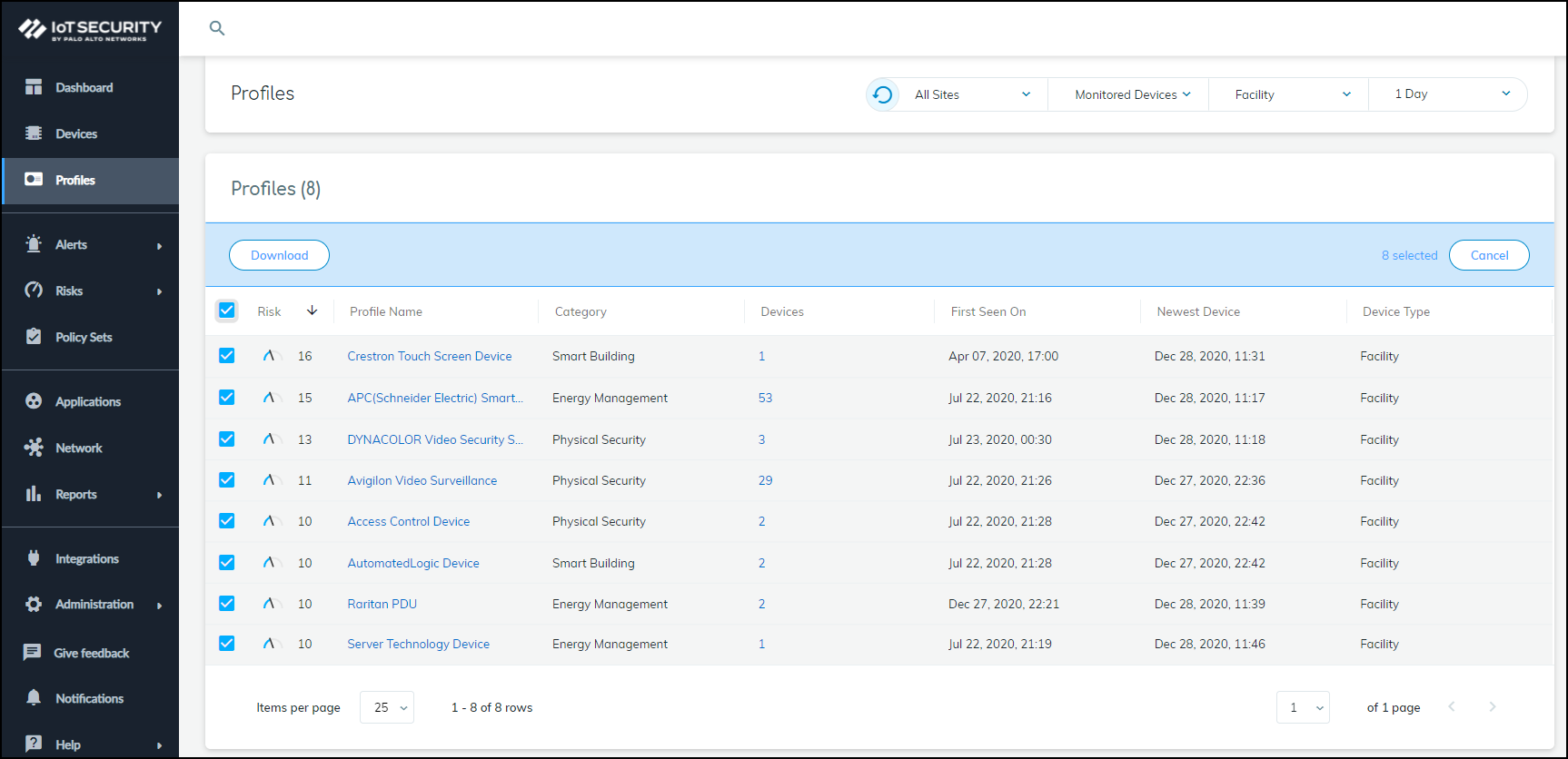
Segmenting, or microsegmenting, your network into VLANs by device type creates barriers that can thwart intruders from moving laterally and slow down their reconnaissance efforts, giving yourself more time to discover and respond to the intrusion. Device Security can assist in microsegmentation by coordinating with Cisco ISE. Device Security formulates IoT device profiles and then shares them with ISE so that it can assign devices to VLANs based on these profiles.- Download a list of IoT device profiles.
- In Device Security, click AssetsProfiles, optionally apply filters to display the device profiles you want to use, select them all by selecting the check box in the heading column, and then click Download.
![]()
- Save the downloaded .csv file and open it so you can copy IoT device profile names and paste them into the Cisco ISE interface.
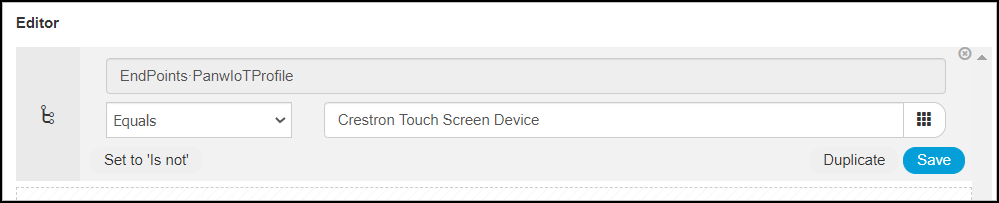
Log in to Cisco ISE and create a condition for an exception rule.- Click PolicyPolicy ElementsConditionsLibrary Conditions, enter the following in Editor:Click to add an attribute: EndpointsPanwIoTProfileOperator: EqualsAttribute value: Paste the IoT device profile name.
![]()
- Save the configuration.
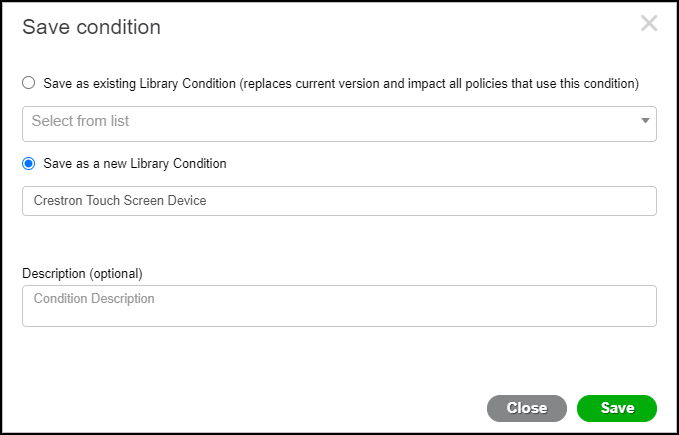
- In the Save condition dialog box, select Save as a new Library Condition, paste the profile name in the Condition Name field, and then Save the condition.The name of a library condition can contain letters, numbers, hyphens, underscores, periods, and spaces. If the IoT device profile name has any other characters such as parentheses, either remove or replace them with characters that are supported.
![]()
- Repeat these steps for all the other IoT device profiles.
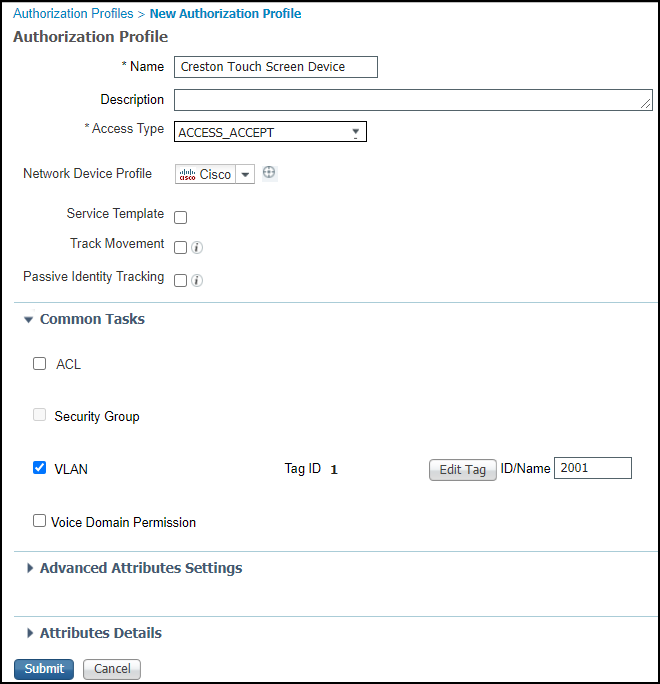
Create authorization profiles that allow IoT devices to access the network, permit them to send and receive network traffic, and associate their device profiles with unique VLAN IDs.- Click PolicyPolicy ElementsResultsAuthorizationAuthorization Profiles and then click Add.
- Enter settings like those described below and leave the other settings at their default values:Name: Enter a name for the authorization profile; for example, Crestron Touch Screen Device.Access Type: ACCESS_ACCEPTDACL Name: PERMIT_ALL_TRAFFICVLAN: (select); Tag ID: 1; ID/Name: 2001, where 2001 is the ID number of the VLAN to which you want to assign all Crestron touch screen devices.
![]()
- Submit the settings.
- Repeat these steps to create authorization profiles that assign each IoT device profile to a unique VLAN.
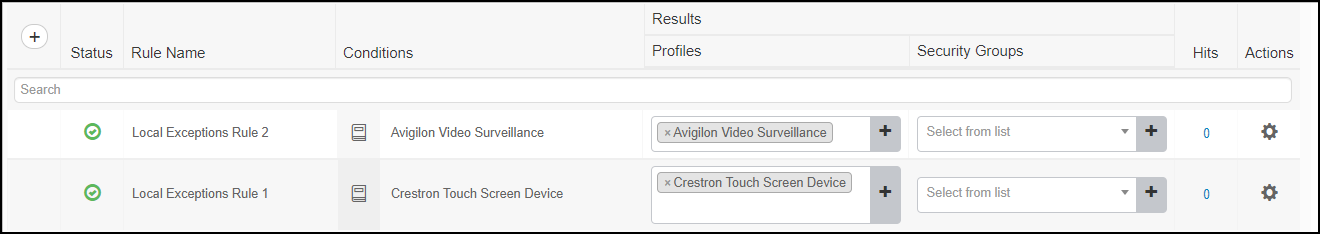
Create authorization policy exception rules to assign devices to VLANs based on IoT device profile data.- Click PolicyPolicy Sets and then click the Arrow icon ( > ) to modify your existing policy set.
- Expand Authorization Policy - Local Exceptions, click the Plus icon ( + ) to add an exception rule, and then click the Plus icon ( + ) to add a condition.
- Click-drag one of the conditions you created from the Library into the Editor and then click Use.
- In Results-Profiles, choose the authorization profile you created for this condition.
![]()
- Repeat these steps to add more exception rules. When devices with these IoT device profiles join the network and request access permission from Cisco ISE, ISE automatically assigns them to appropriate VLANs.
- When done, Save the configuration.