Identification and Quarantine of Compromised Devices
Table of Contents
10.0 (EoL)
Expand all | Collapse all
-
- Automatic Content Updates Through Offline Panorama
- Enhanced Authentication for Dedicated Log Collectors and WildFire Appliances
- Syslog Forwarding Using Ethernet Interfaces
- Increased Configuration Size for Panorama
- Access Domain Enhancements for Multi-Tenancy
- Enhanced Performance for Panorama Query and Reporting
- Log Query Debugging
- Configurable Key Limits in Scheduled Reports
- Multiple Plugin Support for Panorama
End-of-Life (EoL)
Identification and Quarantine of Compromised Devices
Add compromised devices to a quarantine list and optionally
block users from logging in to them.
GlobalProtect now makes it
easier for you to block compromised devices from your network. GlobalProtect
identifies a compromised device with its Host ID and, optionally,
serial number instead of its source IP address. See Quarantine Devices Using Host
Information in the GlobalProtect Administrator’s
Guide for more information.
After you identify a device
as compromised (for example, if a device has been infected with
malware and is performing command and control actions), you can manually
add the device’s Host ID to a quarantine list and configure GlobalProtect to
prevent users from connecting to the GlobalProtect gateway from
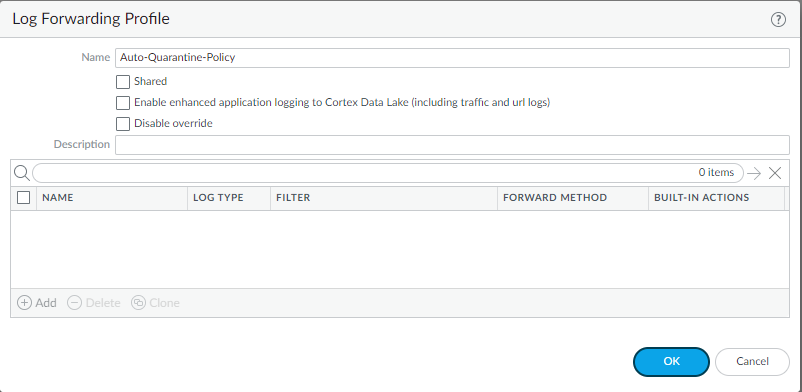
a quarantined device. You can also automatically quarantine the
device using security policies, log forwarding profiles, and log
settings.
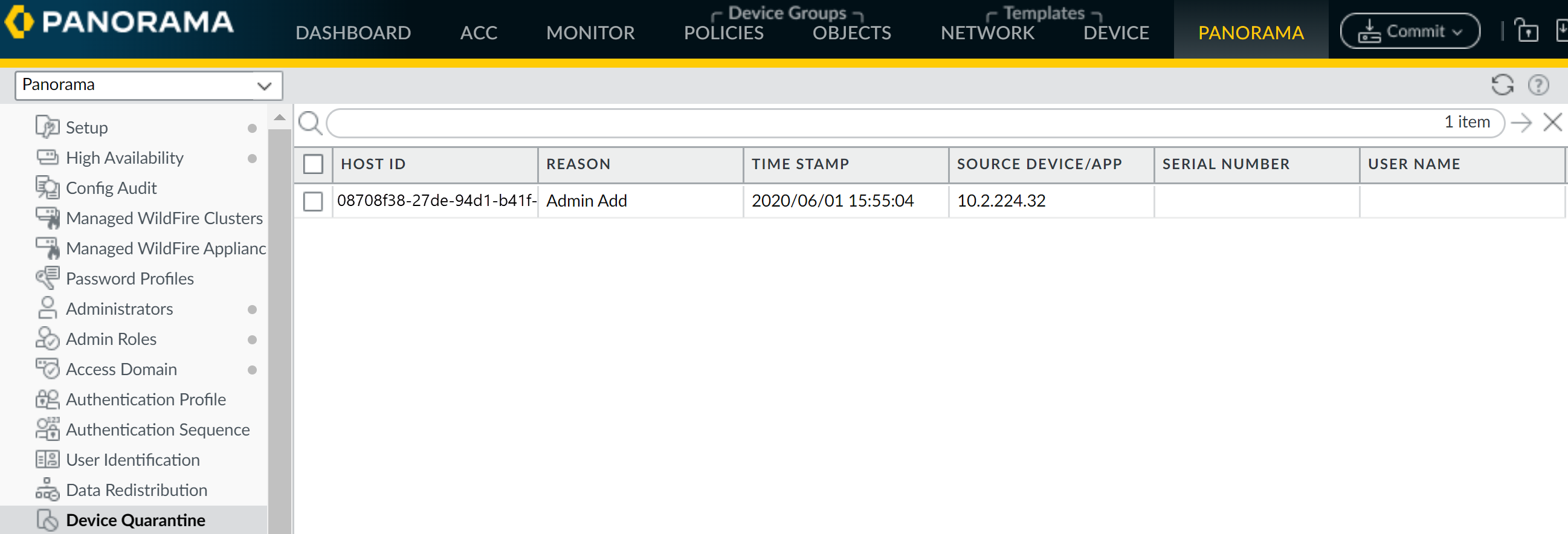
To view, add, and set actions for quarantined devices,
complete the following steps.
- Make sure a valid GlobalProtect subscription license is present on the firewall.View quarantined device information (either DeviceDevice Quarantine for next-generation firewalls or PanoramaDevice Quarantine for Panorama appliances).
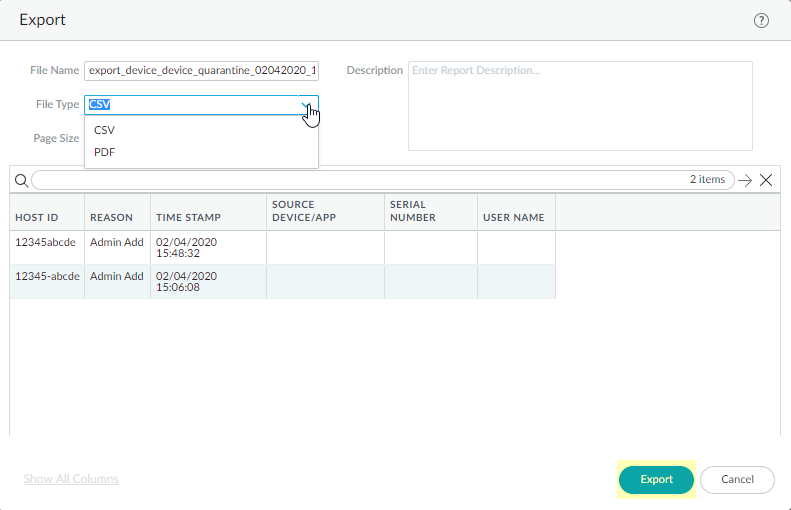
![]() You can export the list of quarantined devices to a pdf or csv file by selecting PDF/CSV at the bottom of the Device Quarantine page to open the Export page.
You can export the list of quarantined devices to a pdf or csv file by selecting PDF/CSV at the bottom of the Device Quarantine page to open the Export page.![]()
- (Optional) View quarantined device information from the ACC.
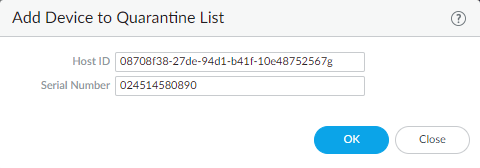
Manually quarantine a device.You can manually add a device to the quarantine list from the Device Quarantine page, add it from the GlobalProtect, Threat, Traffic, or Unified logs, or add it using an API.![]() Automatically quarantine a device.
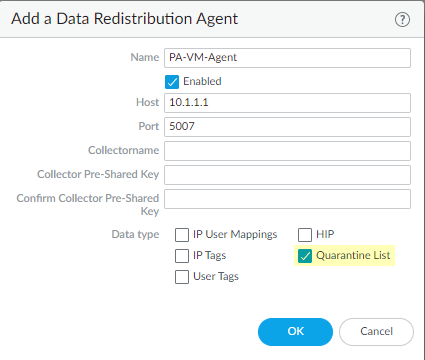
Automatically quarantine a device.![]() (Optional) Delete a device from the quarantine list.(Optional) Block quarantined devices from accessing the network, or block users from logging into the network from a quarantined device.(Optional) Redistribute device quarantine information.
(Optional) Delete a device from the quarantine list.(Optional) Block quarantined devices from accessing the network, or block users from logging into the network from a quarantined device.(Optional) Redistribute device quarantine information.![]()