Download PDF
Configure an Admin Role Profile for Selective Push to Managed Firewalls
Table of Contents
11.0 (EoL)
Expand all | Collapse all
-
- Determine Panorama Log Storage Requirements
-
- Setup Prerequisites for the Panorama Virtual Appliance
- Perform Initial Configuration of the Panorama Virtual Appliance
- Set Up The Panorama Virtual Appliance as a Log Collector
- Set Up the Panorama Virtual Appliance with Local Log Collector
- Set up a Panorama Virtual Appliance in Panorama Mode
- Set up a Panorama Virtual Appliance in Management Only Mode
-
- Preserve Existing Logs When Adding Storage on Panorama Virtual Appliance in Legacy Mode
- Add a Virtual Disk to Panorama on an ESXi Server
- Add a Virtual Disk to Panorama on vCloud Air
- Add a Virtual Disk to Panorama on Alibaba Cloud
- Add a Virtual Disk to Panorama on AWS
- Add a Virtual Disk to Panorama on Azure
- Add a Virtual Disk to Panorama on Google Cloud Platform
- Add a Virtual Disk to Panorama on KVM
- Add a Virtual Disk to Panorama on Hyper-V
- Add a Virtual Disk to Panorama on Oracle Cloud Infrastructure (OCI)
- Mount the Panorama ESXi Server to an NFS Datastore
-
- Increase CPUs and Memory for Panorama on an ESXi Server
- Increase CPUs and Memory for Panorama on vCloud Air
- Increase CPUs and Memory for Panorama on Alibaba Cloud
- Increase CPUs and Memory for Panorama on AWS
- Increase CPUs and Memory for Panorama on Azure
- Increase CPUs and Memory for Panorama on Google Cloud Platform
- Increase CPUs and Memory for Panorama on KVM
- Increase CPUs and Memory for Panorama on Hyper-V
- Increase the CPUs and Memory for Panorama on Oracle Cloud Infrastructure (OCI)
- Complete the Panorama Virtual Appliance Setup
-
- Convert Your Evaluation Panorama to a Production Panorama with Local Log Collector
- Convert Your Evaluation Panorama to a Production Panorama without Local Log Collector
- Convert Your Evaluation Panorama to VM-Flex Licensing with Local Log Collector
- Convert Your Evaluation Panorama to VM-Flex Licensing without Local Log Collector
- Convert Your Production Panorama to an ELA Panorama
-
- Register Panorama
- Activate a Panorama Support License
- Activate/Retrieve a Firewall Management License when the Panorama Virtual Appliance is Internet-connected
- Activate/Retrieve a Firewall Management License when the Panorama Virtual Appliance is not Internet-connected
- Activate/Retrieve a Firewall Management License on the M-Series Appliance
- Install the Panorama Device Certificate
- Install the Device Certificate for a Dedicated Log Collector
-
- Migrate from a Panorama Virtual Appliance to an M-Series Appliance
- Migrate a Panorama Virtual Appliance to a Different Hypervisor
- Migrate from an M-Series Appliance to a Panorama Virtual Appliance
- Migrate from an M-500 Appliance to an M-700 Appliance
- Migrate from an M-600 Appliance to an M-700 Appliance
- Migrate from an M-100 Appliance to an M-500 Appliance
- Migrate from an M-100 or M-500 Appliance to an M-200 or M-600 Appliance
-
- Configure an Admin Role Profile
- Configure an Admin Role Profile for Selective Push to Managed Firewalls
- Configure an Access Domain
-
- Configure a Panorama Administrator Account
- Configure Local or External Authentication for Panorama Administrators
- Configure a Panorama Administrator with Certificate-Based Authentication for the Web Interface
- Configure an Administrator with SSH Key-Based Authentication for the CLI
- Configure RADIUS Authentication for Panorama Administrators
- Configure TACACS+ Authentication for Panorama Administrators
- Configure SAML Authentication for Panorama Administrators
- Configure Tracking of Administrator Activity
-
- Add a Firewall as a Managed Device
- Change Between Panorama Management and Cloud Management
-
- Add a Device Group
- Create a Device Group Hierarchy
- Create Objects for Use in Shared or Device Group Policy
- Revert to Inherited Object Values
- Manage Unused Shared Objects
- Manage Precedence of Inherited Objects
- Move or Clone a Policy Rule or Object to a Different Device Group
- Push a Policy Rule to a Subset of Firewalls
- Device Group Push to a Multi-VSYS Firewall
- Manage the Rule Hierarchy
- Manage the Master Key from Panorama
- Schedule a Configuration Push to Managed Firewalls
- Redistribute Data to Managed Firewalls
-
- Plan the Transition to Panorama Management
- Migrate a Firewall to Panorama Management and Reuse Existing Configuration
- Migrate a Firewall to Panorama Management and Push a New Configuration
- Migrate a Firewall HA Pair to Panorama Management and Reuse Existing Configuration
- Migrate a Firewall HA Pair to Panorama Management and Push a New Configuration
- Load a Partial Firewall Configuration into Panorama
- Localize a Panorama Pushed Configuration on a Managed Firewall
-
- Configure a Managed Collector
- Monitor Managed Collector Health Status
- Configure Log Forwarding to Panorama
- Configure Syslog Forwarding to External Destinations
- Forward Logs to Strata Logging Service
- Verify Log Forwarding to Panorama
- Modify Log Forwarding and Buffering Defaults
- Configure Log Forwarding from Panorama to External Destinations
-
- Add Standalone WildFire Appliances to Manage with Panorama
- Remove a WildFire Appliance from Panorama Management
-
-
- Configure a Cluster and Add Nodes on Panorama
- Configure General Cluster Settings on Panorama
- Remove a Cluster from Panorama Management
- Configure Appliance-to-Appliance Encryption Using Predefined Certificates Centrally on Panorama
- Configure Appliance-to-Appliance Encryption Using Custom Certificates Centrally on Panorama
- View WildFire Cluster Status Using Panorama
-
-
- Preview, Validate, or Commit Configuration Changes
- Commit Selective Configuration Changes for Managed Devices
- Push Selective Configuration Changes to Managed Devices
- Enable Automated Commit Recovery
- Compare Changes in Panorama Configurations
- Manage Locks for Restricting Configuration Changes
- Add Custom Logos to Panorama
- Use the Panorama Task Manager
- Reboot or Shut Down Panorama
- Configure Panorama Password Profiles and Complexity
-
-
- Verify Panorama Port Usage
- Resolve Zero Log Storage for a Collector Group
- Replace a Failed Disk on an M-Series Appliance
- Replace the Virtual Disk on an ESXi Server
- Replace the Virtual Disk on vCloud Air
- Migrate Logs to a New M-Series Appliance in Log Collector Mode
- Migrate Logs to a New M-Series Appliance in Panorama Mode
- Migrate Logs to a New M-Series Appliance Model in Panorama Mode in High Availability
- Migrate Logs to the Same M-Series Appliance Model in Panorama Mode in High Availability
- Migrate Log Collectors after Failure/RMA of Non-HA Panorama
- Regenerate Metadata for M-Series Appliance RAID Pairs
- View Log Query Jobs
- Troubleshoot Registration or Serial Number Errors
- Troubleshoot Reporting Errors
- Troubleshoot Device Management License Errors
- Troubleshoot Automatically Reverted Firewall Configurations
- View Task Success or Failure Status
- Generate a Stats Dump File for a Managed Firewall
- Recover Managed Device Connectivity to Panorama
- Restore an Expired Device Certificate
End-of-Life (EoL)
Configure an Admin Role Profile for Selective Push to Managed Firewalls
Create an admin role profile to push individual device
group and template configuration objects to specific firewalls managed
by the Panorama™ management server.
To allow for greater control of configuration changes of managed firewalls, create an
admin role profile to enable a Panorama administrator to push configuration for one
or more Panorama administrators from the Panorama™ management server to managed
firewalls. After you commit
selective configuration changes to Panorama, you can select
specific Panorama admin changes to review the configuration changes and
then push only those changes made by the selected admins to your managed firewalls.
Leveraging selective pushes to managed firewalls also reduces the risk of pushing
incomplete device group and template configurations to managed firewalls by allowing
you to explicitly exclude incomplete configuration changes when you push to managed
firewalls. This helps mitigate and avoid potential outages and configuration related
issues that could cause network disruptions,.
Administrators with Superuser or Panorama admin
role privileges can push and review object level changes of other
administrators by default. However, you can modify the Panorama
administrator admin roles to modify the object level configuration
privileges as needed.
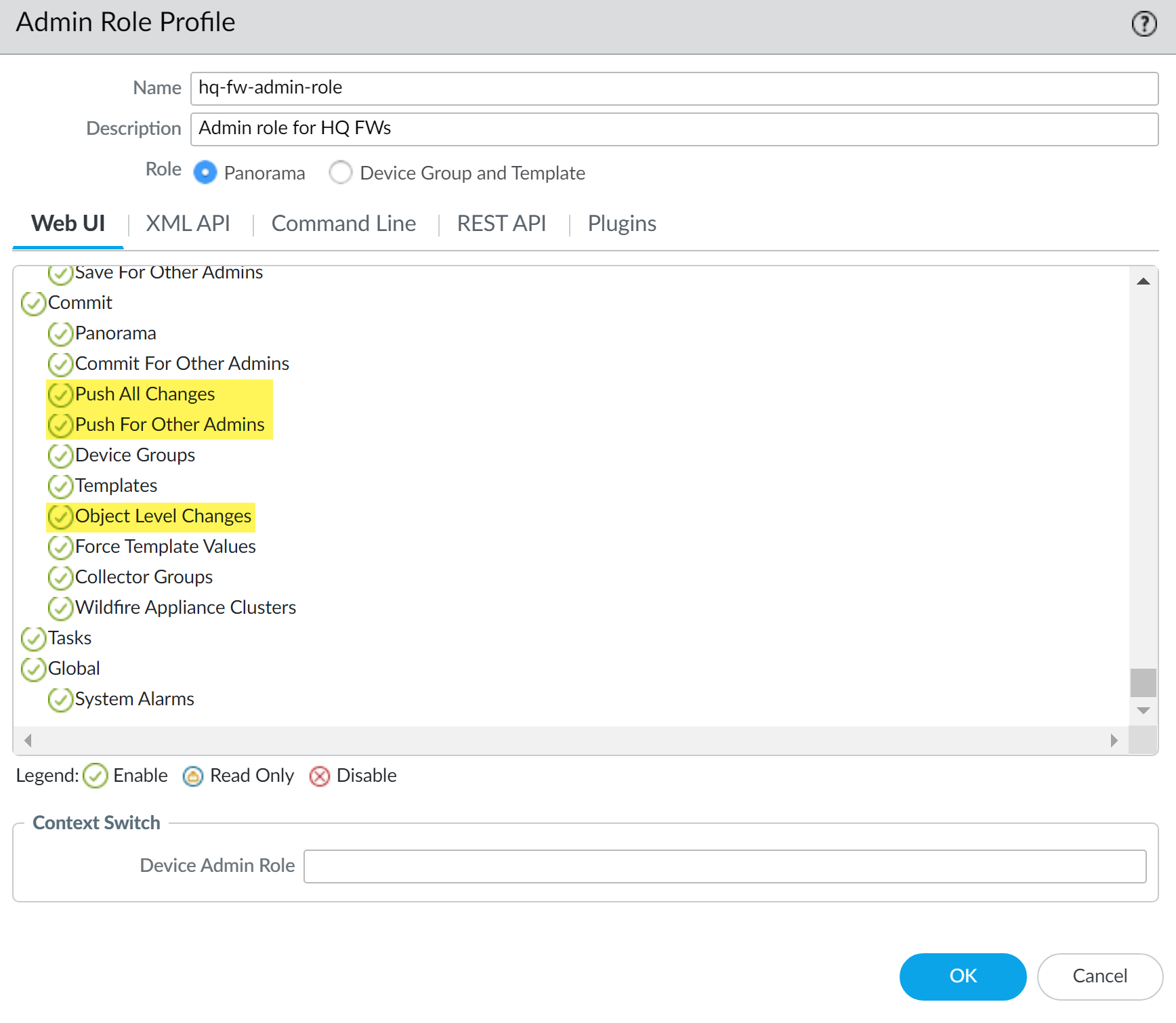
- Log in to the Panorama Web Interface.(Optional) Select DeviceAdmin Roles and select the Template in which to configure a firewall admin role profile.You must create an Admin Role profile on the firewall and assign it to the Panorama management server Admin Role profile to allow administrators to context switch between Panorama and managed firewall web interfaces.Select PanoramaAdmin Roles and Add a new admin role.Enter a descriptive Name for the admin role.Select the Panorama admin role.Select Web UI and navigate to the Commit privileges.Configure the object level configuration privileges as needed.All object level configuration privileges are enabled by default.The default Superuser or Panorama admin role privileges support full object level configuration privileges.
- Push All Changes—Allow the administrator to push all changes made by all admins.
- Push For Other Admins—Allows the administrator select and push configuration changes made by other administrators.
- Object Level Changes—Allows the administrator to view individual configuration objects to push. If disabled, the list of configuration objects is not displayed in the Push Scope.
![]() (Optional) To allow Panorama administrators to Context Switch between the Panorama and firewall web interface, enter the name of Device Admin Role you configured in Step 1.Click OK.Configure a custom Panorama administrator and select the Admin Role you created.Commit and Commit to Panorama.
(Optional) To allow Panorama administrators to Context Switch between the Panorama and firewall web interface, enter the name of Device Admin Role you configured in Step 1.Click OK.Configure a custom Panorama administrator and select the Admin Role you created.Commit and Commit to Panorama.