Prisma Access Agent
Configure Traffic Enforcement for Non-TCP and Non-UDP Protocols
Table of Contents
Configure Traffic Enforcement for Non-TCP and Non-UDP Protocols
Configure Prisma Access Agent to block non-TCP and non-UDP traffic when connected to
a tunnel, enhancing network security for your enterprise.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Traffic enforcement for non-TCP and non-UDP protocols extends Prisma Access Agent capabilities beyond traditional TCP and UDP traffic control to provide
comprehensive IP protocol coverage. This feature addresses security concerns where
protocols like ICMP, GRE, and IPSec might bypass tunnel enforcement and go direct
without any security enforcement, creating potential attack vectors for your
enterprise.
When enabled, Prisma Access Agent can block any non-TCP and non-UDP traffic
that attempts to circumvent the tunnel when a user is connected. This ensures that
none of the non-TCP and non-UDP traffic goes direct.
Administrators configure this capability through forwarding profiles that manage
agent traffic. Once configured, these settings are pushed to the Prisma Access Agent on your endpoints, which then enforces the policies at the
kernel level. This ensures efficient and reliable traffic enforcement without
impacting system performance.
To address the operational needs of IT teams, you can specifically permit ICMP
traffic for troubleshooting purposes while still blocking other non-TCP and non-UDP
traffic. This flexibility provides a balance between stringent security controls and
practical network management requirements.
Using the PACLI command-line interface, you can verify the current enforcement
status, view traffic statistics, and troubleshoot any potential issues with the
traffic enforcement mechanisms. This visibility ensures that security teams can
confirm proper policy implementation and quickly address any concerns that arise in
their environment.
Key Components
Forwarding Profile configuration—You configure traffic enforcement through
forwarding profiles. The primary configuration option Block Non-TCP
and Non-UDP based traffic when connected to tunnel controls the
enforcement behavior for all non-TCP and non-UDP protocols.
ICMP Exception Handling—The Allow ICMP for
troubleshooting option provides selective control over ICMP
traffic while maintaining enforcement for other protocols. This option becomes
available only when you enable the primary blocking feature, enabling you to
preserve network diagnostic capabilities while enforcing security policies.
Kernel-Level Enforcement—The agent implements traffic control at the
kernel level on both Windows and macOS platforms. This low-level implementation
ensures comprehensive protocol coverage and prevents applications from bypassing
enforcement through alternative network paths.
Logging and Monitoring—The agent generates detailed logs for enforcement
actions. You can access verbose logging through PACLI commands to monitor
blocked traffic and troubleshoot enforcement behavior.
Traffic Behavior
The combination of configuration options determines how the agent handles non-TCP
and non-UDP traffic, including ICMP, GRE, IGMP, IPSec, and other Layer 3
protocols, based on your tunnel state and selected settings. The following table
summarizes the traffic behavior based on the configuration settings.
| Block Non-TCP and Non-UDP Based Traffic When Connected to Tunnel | Allow ICMP for Troubleshooting | Tunnel State | Traffic Behavior |
|---|---|---|---|
| Enabled | Disabled | Connected | Block all non-TCP and non-UDP traffic. |
| Enabled | Enabled | Connected | Block all non-TCP and non-UDP traffic except ICMP. Allow ICMP traffic to pass through for troubleshooting. |
| Disabled
(Default) | Any setting | Connected | Allow all non-TCP and non-UDP traffic. |
| Any setting | Any setting | Disconnected | Allow all non-TCP and non-UDP traffic regardless of configuration; enforcement is inactive when the tunnel is disconnected. |
Key Traffic Behavior Notes:
- Enforcement Scope: The agent only blocks or allows outbound non-TCP and non-UDP traffic; it does not intercept or steer traffic.
- Platform Support: Traffic enforcement operates at kernel level on both Windows and macOS
- Protocol Coverage: Enforcement applies to ICMP, GRE, IGMP, IPSec, and other IP-based Layer 3 protocols
- Default Behavior: Both configuration options default to disabled for backward compatibility
- Tunnel Dependency: Traffic enforcement only activates when connected to the tunnel; disconnected agents operate normally
- ICMP Exception: The Allow ICMP for troubleshooting option only becomes available when the primary blocking feature is enabled
To configure Prisma Access Agent to block non-TCP and non-UDP protocols, complete the
following steps.
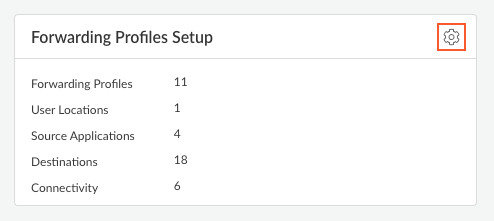
- Navigate to the forwarding profiles setup page.
- Log in to Strata Cloud Manager as the administrator.
- Select ConfigurationNGFW and Prisma AccessConfiguration ScopeMobile Users Container.
- Edit the settings in the Forwarding Profiles Setup section.
![]()
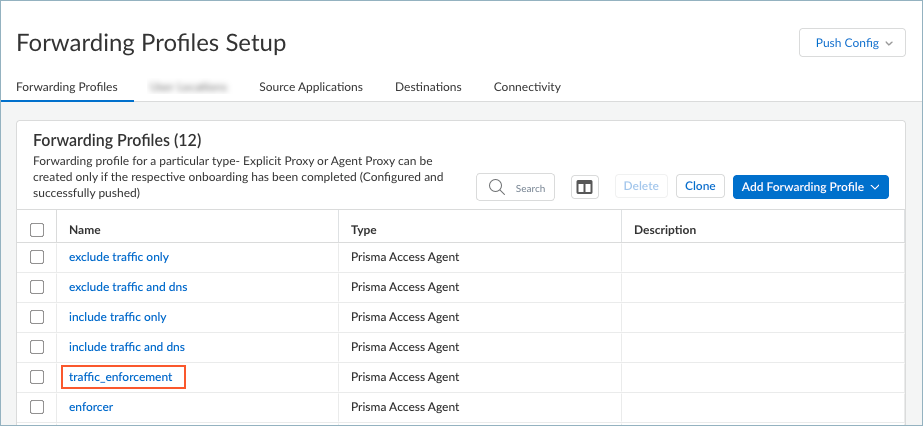
Configure a forwarding profile.- Select an existing forwarding profile you want to modify or add a forwarding profile.For example:
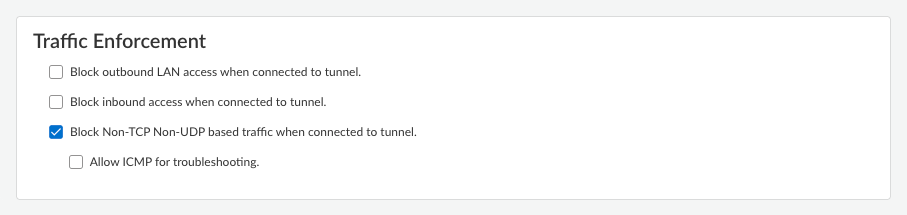
![]() In the forwarding profile, scroll to the Traffic Enforcement section and enable Block Non-TCP and Non-UDP based traffic when connected to tunnel to activate enforcement for non-TCP and non-UDP protocols. The default setting is disabled.
In the forwarding profile, scroll to the Traffic Enforcement section and enable Block Non-TCP and Non-UDP based traffic when connected to tunnel to activate enforcement for non-TCP and non-UDP protocols. The default setting is disabled.![]() (Optional) Enable Allow ICMP for troubleshooting if you need to preserve ICMP functionality for network diagnostics while blocking other protocols. The default setting is disabled.Save your forwarding profile settings.Push the configuration.After configuring the feature, verify the settings using PACLI commands on endpoints where the Prisma Access Agent is deployed.
(Optional) Enable Allow ICMP for troubleshooting if you need to preserve ICMP functionality for network diagnostics while blocking other protocols. The default setting is disabled.Save your forwarding profile settings.Push the configuration.After configuring the feature, verify the settings using PACLI commands on endpoints where the Prisma Access Agent is deployed.- Use the pacli traffic show command on the endpoint to confirm the settings are applied.On macOS:
/Applications/Prisma\ Access\ Agent.app/Contents/Helpers/pacli traffic show
On Windows:"C:\Program Files\Palo Alto Networks\Prisma Access Agent\pacli" trafic show
Check the configuration indicators in the command output:V - Block Non-TCP Non UDP based traffic when connected to tunnel V - Allow ICMP for troubleshooting (if enabled)