Prisma Access Agent
Set Up Anti-Tampering for Prisma Access Agent
Table of Contents
Set Up Anti-Tampering for Prisma Access Agent
Learn how to enable the anti-tamper feature, which prevents users from tampering with
the Prisma Access Agent.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
(Prisma Access Agent version 25.4 in
Strata Cloud Manager Managed deployments) The Anti-Tamper
Password configuration section is no longer in the global agent
settings. It now resides in the Agent Settings page to provide anti-tamper
protection at a more granular level, with the ability to enable or disable
protection for specific users and user groups. You can review the feature, migration
approach, and learn how to configure Anti-Tamper Protection for Prisma Access Agents.
(Prisma Access Agent 25.3.1
and earlier versions in Panorama Managed deployments) Certain
users, including those with administrative privileges, might attempt to bypass
security controls by tampering with secure access agents, creating significant
vulnerabilities in your security posture. Prisma Access Agent's anti-tamper
feature addresses this challenge by preventing unauthorized modifications to
your security infrastructure, ensuring that your Zero Trust security controls
remain continuously operational.
The feature prevents always-on security bypass attempts by blocking actions such
as stopping, killing, or uninstalling the agent, or modifying critical agent
registries and plists. You're also protected against agent spoofing, where
insider threats or compromised endpoints might attempt to modify agent files,
folders, processes, or HIP reports to circumvent security measures. By
implementing this protection, you ensure that your security controls remain
intact and effective, regardless of user privilege levels or sophisticated
bypass attempts.
The anti-tamper feature can protect the following Prisma Access Agent
resources on your endpoints:
- Prisma Access Agent folders and files—Users can’t modify any Prisma Access Agent-related files and folders, including rewriting, renaming, or deleting the files and folders.
- Prisma Access Agent services and host information profile (HIP) processes—Users can’t spoof any Prisma Access Agent-related services and HIP processes. The HIP processes collect information about the host that the Prisma Access Agent is running on and submits the host information to Prisma Access for inspection. If a user tries to stop a process, they must supply the anti-tamper unlock password.
- Prisma Access Agent Registry keys (on Windows) or .plist file (on macOS)—Users can’t modify the Windows Registry keys or .plist file for Prisma Access Agent.
- The PACli command-line interface—Users can’t disable the Prisma Access Agent or the anti-tamper feature using the PACli command-line interface. Administrators and authorized users who need to perform certain actions for troubleshooting at the command line must provide an anti-tamper unlock password when prompted.
- Navigate to the Prisma Access Agent setup page.
- For Prisma Access (Managed by Panorama) deployments:
- From the Cloud Services plugin in Panorama, select PanoramaCloud ServicesPrisma Access Agent.
- Click Launch Prisma Access Agent.
![]()
- Select ConfigurationPrisma Access AgentSettingsPrisma Access Agent.
- For NGFW (Managed by Panorama) deployments:
- Log in to Strata Cloud Manager as the administrator.
- Select ConfigurationPrisma Access AgentSettingsPrisma Access Agent.
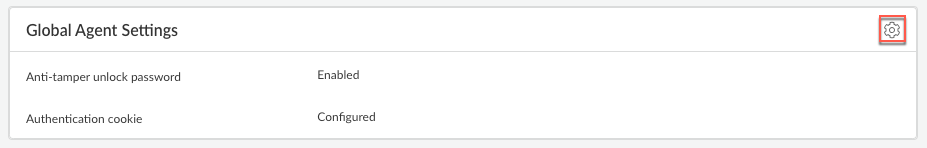
Edit the Global Agent Settings.![]() Configure an anti-tamper unlock password (also known as the supervisor password), which you will need to enter when performing certain actions to troubleshoot the agent, such as agent upgrades or downgrades.
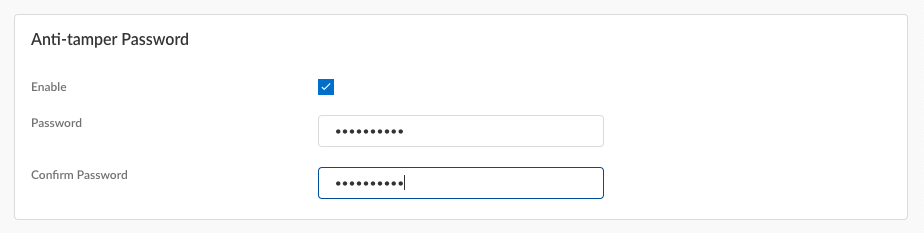
Configure an anti-tamper unlock password (also known as the supervisor password), which you will need to enter when performing certain actions to troubleshoot the agent, such as agent upgrades or downgrades.- Enable the anti-tamper feature.You can set up an anti-tamper unlock password only if you enable the anti-tamper feature.
- Enter the anti-tamper unlock Password and Confirm Password. The password must have a minimum of eight alphanumeric characters. If you enable the anti-tamper feature but don’t provide an anti-tamper unlock password, the push configuration will fail.
![]()
Save your settings and push the configuration.Verify that anti-tamper protection is enabled for the Prisma Access Agent on an endpoint by using the Prisma Access Agent command-line tool (PACli).- Check the status of the anti-tamper protection by running the following command on an endpoint:
- On macOS
agents:
/Applications/Prisma\ Access\ Agent.app/Contents/Helpers/pacli protect status
- On Windows
agents:
"C:\Program Files\Palo Alto Networks\Prisma Access Agent\pacli" protect status
If you successfully enabled anti-tamper protection, the following output should appear:Protection State --------------- ---------- File Enabled Process Enabled Registry Enabled Service Enabled
Try to disable the Prisma Access Agent by running the following command:pacli disable
If you successfully enabled anti-tamper protection, the agent will prompt you for the anti-tamper unlock password. - On macOS
agents:
- For Prisma Access (Managed by Panorama) deployments: