Prisma Access Agent
Configure General Global Settings for the Prisma Access Agent
Table of Contents
Configure General Global Settings for the Prisma Access Agent
Configure general global agent settings for Prisma Access Agent, such as
configuring the anti-tamper protection settings, authentication override settings, and
inactivity timeout settings.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
You can customize the global agent settings that apply to Prisma
Access Agents across all endpoints.
General global agent settings include setting up the anti-tamper
feature that prevents users from tampering with the Prisma Access Agent, such as
uninstalling it from an end user's device. In addition, you can configure the
authentication override settings, the inactivity timeout setting, and block the
login of quarantined devices.
- Navigate to the Prisma Access Agent setup.
- From Strata Cloud Manager:
- Log in to Strata Cloud Manager as the administrator.
- Select ConfigurationNGFW and Prisma AccessConfiguration ScopeAccess AgentSetupPrisma Access Agent.
- From Panorama:
- From the Cloud Services plugin in Panorama, select PanoramaCloud ServicesPrisma Access AgentLaunch Prisma Access Agent.
- Select ConfigurationPrisma Access AgentSettingsPrisma Access Agent.
Edit the Global Agent Settings.![]() (Strata Cloud Manager only) Select General.Configure Authentication Override settings to allow Prisma Access to generate and accept secure, encrypted cookies for user authentication. Authentication override allows the user to provide login credentials only once during the specified Cookie Lifetime.
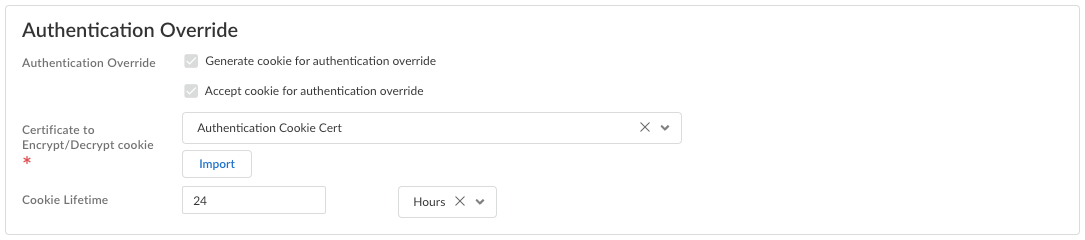
(Strata Cloud Manager only) Select General.Configure Authentication Override settings to allow Prisma Access to generate and accept secure, encrypted cookies for user authentication. Authentication override allows the user to provide login credentials only once during the specified Cookie Lifetime.![]()
- Generate cookie for authentication override—Enables Prisma Access to generate encrypted endpoint-specific cookies and issue authentication cookies to the endpoint. (Default: Enabled)
- Accept cookie for authentication override—Enables Prisma Access to authenticate users with a valid, encrypted cookie. When the app presents a valid cookie, Prisma Access verifies that the cookie was encrypted by Prisma Access originally, decrypts the cookie, and then authenticates the user. (Default: Enabled)
- Certificate to Encrypt/Decrypt Cookie—Select a
certificate to use to encrypt and decrypt the cookie. For NGFW
deployments, this certificate is the same one that you imported in the
Infrastructure
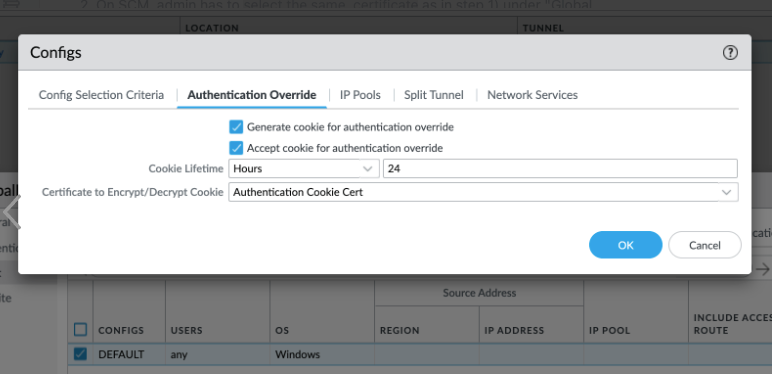
settings.(Panorama Managed Prisma Access and Panorama Managed NGFW deployments) If you updated the Certificate to Encrypt/Decrypt Cookie field in Panorama and pushed the configuration, you must select the same certificate in the Certificate to Encrypt/Decrypt Cookie in Strata Cloud Manager and perform a push config. Otherwise, the Prisma Access Agent will not be able to establish a tunnel to the gateway.For example, in Panorama, you selected Authentication Cookie Cert:
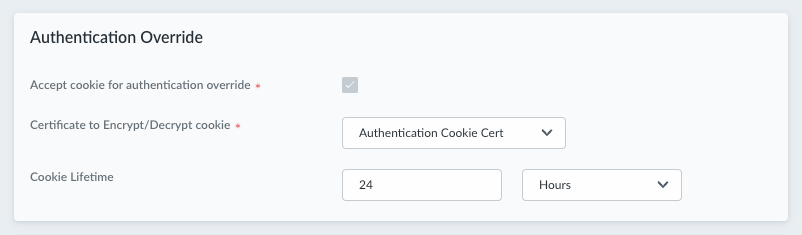
![]() In Strata Cloud Manager, you need to select the same certificate:
In Strata Cloud Manager, you need to select the same certificate:![]()
- Cookie Lifetime—Specifies the hours, days, or weeks for which the cookie is valid (default is 24 hours). The range for hours is 1-72; the range for weeks is 1-52; and the range for days is 1-365. After the cookie expires, the user must reenter their login credentials. Prisma Access then encrypts a new cookie to send to the agent. This value can be the same as or different from the cookie lifetime that you configure.
(Strata Cloud Manager) Configure Timeout settings for the Prisma Access Agent.The Inactivity Logout setting applies to both Prisma Access Agent and GlobalProtect. Any changes you make will be reflected and used for GlobalProtect, and vice versa.- Inactivity Logout—Specify the amount of time
after which idle users are logged out of the Prisma Access Agent.You can use the inactivity logout period to enforce a security policy to monitor traffic from endpoints while connected to Prisma Access and to quickly log out inactive Prisma Access Agent sessions. You can enforce a shorter inactivity logout period. Users are logged out if the Prisma Access Agent has not routed traffic through the tunnel or if the gateway does not receive a HIP check from the endpoint within the configured time period.
- (Not supported on
Prisma Access Agent Linux) Notify Before Inactivity Logout
(min)—Specify when to notify the user before a Prisma Access
Agent session logs out automatically due to inactivity. This period of
time must be less than the period for the Inactivity
Logout. For example, if you set Notify Before Inactivity Logout to 20 minutes, the app will display the notification to the user 20 minutes before the inactive session expires. If you don't want the notification to be displayed, set the value to 0. You can enter a value between 0-120 minutes. The default is 0 minutes.
- (Not supported on Prisma Access Agent Linux) Inactivity Logout Message—Create a custom message that you want to display to users when their inactive sessions are about to end due to inactivity. The maximum length for the message is 127 characters.
(Strata Cloud Manager) (Not supported on Prisma Access Agent Linux) Block Login for Quarantined Devices to prevent Prisma Access Agent users from logging in from quarantined devices.If a user attempts to log in from a quarantined device when this setting is enabled, the Prisma Access Agent notifies the user that the device is quarantined and the user cannot log in from that device. If this setting is not enabled, the user receives the notification but is able to log in from that device.The Block Login for Quarantined Devices setting applies to both Prisma Access Agent and GlobalProtect. Any changes you make will be reflected and used for GlobalProtect, and vice versa.Save your settings. - From Strata Cloud Manager: