Prisma Access Agent
Configure HIP Data Collection Settings for the Prisma Access Agent
Table of Contents
Configure HIP Data Collection Settings for the Prisma Access Agent
Define the custom host information profile data that you want the Prisma Access Agent
to collect.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
The Prisma Access Agent collects information about the host it's
running on and submits this host information to the gateway upon successful
connection. The gateway matches this raw host information submitted by the Prisma
Access Agent against any host information profile (HIP) objects and HIP Profiles
that you have defined. If it finds a match, it generates an entry in the HIP Match
log. Additionally, if it finds a HIP Profile match in a policy rule, it enforces the
corresponding security policy.
Prisma Access Agent uses OPSWAT technology
primarily for the HIP feature to assess the security posture of endpoints connecting
to the network. You can define custom HIP data that you want the Prisma Access Agent
to collect or exclude. When this option is enabled, the Prisma Access Agent collects
data from the endpoints.
For example, a custom check could enable you to know whether a certain
application is installed or running on an endpoint. The data that you define to be
collected in a custom check is included in the raw host information data that the
Prisma Access Agent collects and then submits to the gateway when the Prisma Access
Agent connects.
You can configure HIP data collection settings for Strata Cloud Manager Managed or
Panorama managed deployments.
Configure HIP Data Collection Settings for the Prisma Access Agent (Strata Cloud Manager)
Define the custom host information profile data that you want the Prisma Access Agent
to collect for Strata Cloud Manager managed deployments.
Define the custom HIP data that you want Prisma Access Agent to collect for Strata
Cloud Manager managed deployments.
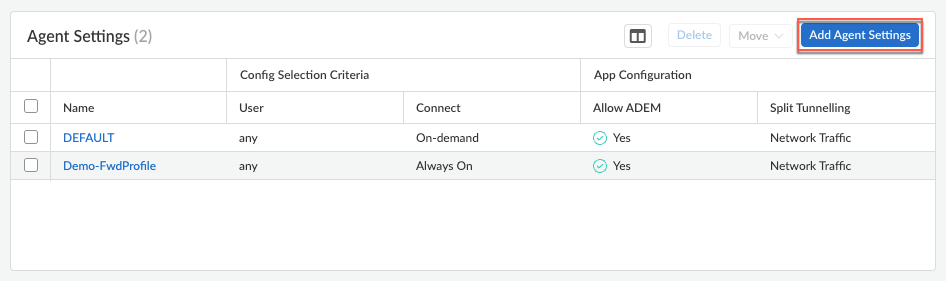
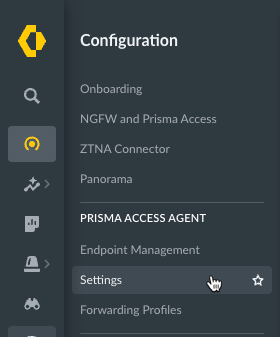
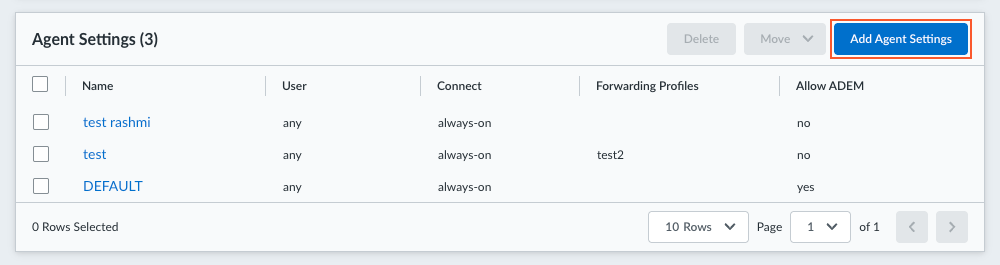
- From Strata Cloud Manager, select ConfigurationNGFW and Prisma AccessConfiguration ScopeAccess AgentSetupPrisma Access Agent.Select an existing agent configuration or Add Agent Settings to create a new configuration.
![]() If you need to create or update an app configuration rule, follow the instructions in Configure Agent Settings for Prisma Access Agent. Otherwise, go to the next step.In the HIP Data Collection section, select Collect HIP Data to enable HIP data collection on the endpoints that are logged in to the gateway. (Default: Enabled)Select Show Advanced Options.
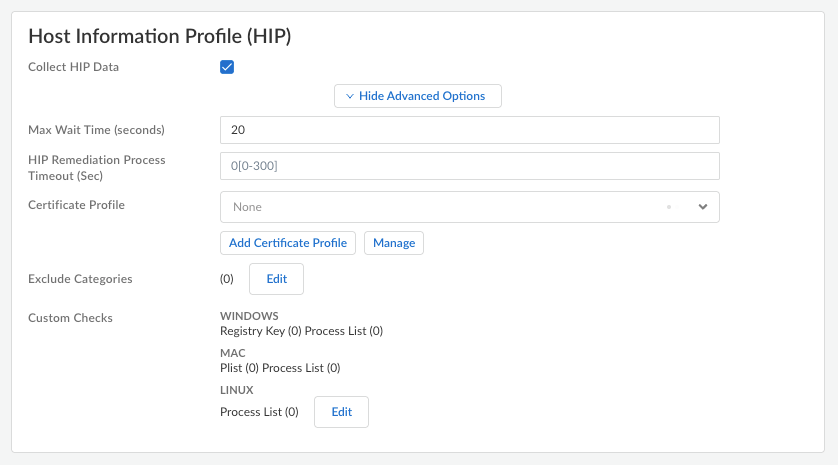
If you need to create or update an app configuration rule, follow the instructions in Configure Agent Settings for Prisma Access Agent. Otherwise, go to the next step.In the HIP Data Collection section, select Collect HIP Data to enable HIP data collection on the endpoints that are logged in to the gateway. (Default: Enabled)Select Show Advanced Options.![]() Specify the Max Wait Time (in seconds) that the Prisma Access Agent should search for HIP data before submitting the available data. The range is 10-60 seconds; the default is 20 seconds.Select the Certificate Profile that the gateway uses to match the machine certificate sent by the Prisma Access Agent.If you want to use a certificate profile that isn't on the list, Add Certificate Profile.
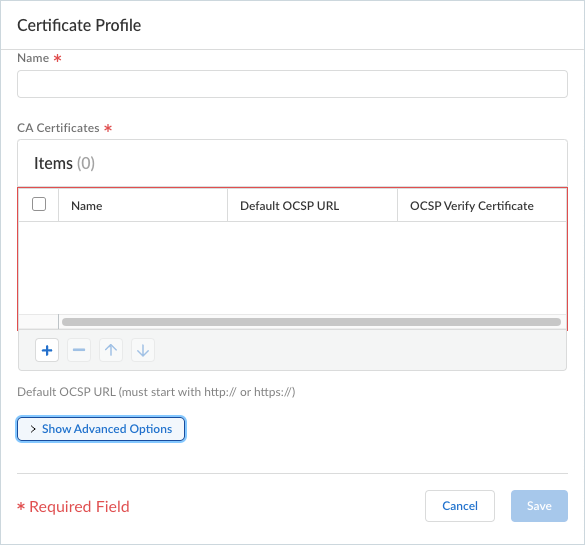
Specify the Max Wait Time (in seconds) that the Prisma Access Agent should search for HIP data before submitting the available data. The range is 10-60 seconds; the default is 20 seconds.Select the Certificate Profile that the gateway uses to match the machine certificate sent by the Prisma Access Agent.If you want to use a certificate profile that isn't on the list, Add Certificate Profile.- (Required) Name—Enter a name for the certificate profile. The name is case-sensitive and must be unique. Use only letters, numbers, spaces, hyphens, and underscores.
![]()
- (Required) CA Certificates—Add a CA Certificate to assign to the profile.Optionally, if the gateway uses the Online Certificate Status Protocol (OCSP) to verify certificate revocation status, configure the following fields to override the default behavior. For most deployments, these fields do not apply.
- By default, the gateway uses the Authority Information Access (AIA) information from the certificate to extract the OCSP responder information. To override the AIA information, enter a Default OCSP URL (starting with http:// or https://).
- By default, the gateway uses the certificate selected in the CA Certificate field to validate OCSP responses. To use a different certificate for validation, select it in the OCSP Verify CA Certificate field.
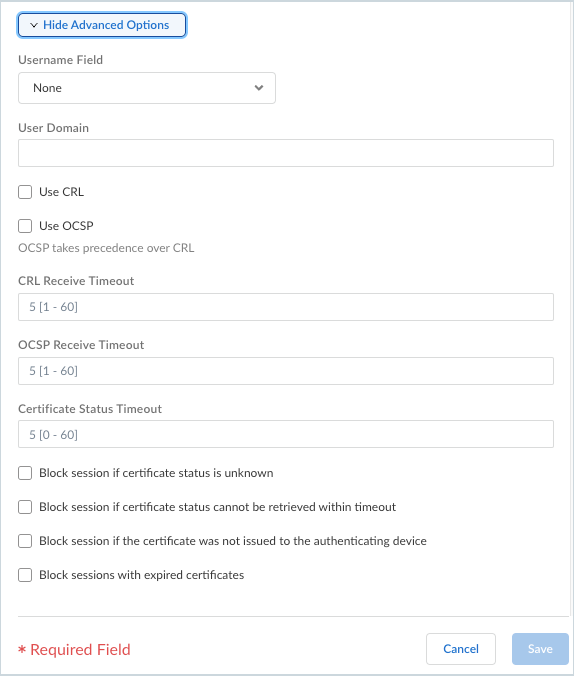
- Show Advance Options—Shows more options for the certificate profile.
![]()
- Username Field—If Prisma Access Agent uses only certificates for gateway authentication, Prisma Access uses the certificate field you select in the Username Field drop-down as the username and matches it to the IP address for the User-ID service:
- Subject—The Common Name.
- Subject Alt—The Email or Principal Name.
- None—Typically for the Prisma Access Agent device authentication.
- User Domain—Enter the NetBIOS domain so that Prisma Access can map users through the User-ID.
- Use CRL—Select this option to use a certificate revocation list (CRL) to verify the revocation status of certificates.
- USE OCSP—Select this option to use OCSP to verify the revocation status of certificates.If you select both OCSP and CRL, the gateway first tries OCSP, and only falls back to the CRL method if the OCSP responder is unavailable.
- CRL Receive Timeout—Specify the interval (1-60 seconds) after which the gateway stops waiting for a response from the CRL service.
- OCSP Receive Timeout—Specify the interval (1-60 seconds) after which the gateway stops waiting for a response from the OCSP responder.
- Certificate Status Timeout—Specify the interval (1-60 seconds) after which the gateway stops waiting for a response from any certificate status service and applies any session blocking logic you define.
- Block session if certificate status is unknown—Select this option if you want the gateway to block sessions when the OCSP or CRL service returns a certificate revocation status of unknown. Otherwise, the gateway proceeds with the sessions.
- Block sessions if certificate status cannot be retrieved within timeout—Select this option if you want the gateway to block sessions after it registers an OCSP or CRL request timeout. Otherwise, the gateway proceeds with the sessions.
- Block sessions if the certificate was not issued to the authenticating device—Select this option if you want the gateway to block sessions when the serial number attribute in the subject of the client certificate does not match the host ID that the Prisma Access Agent reports for the endpoint. Otherwise, the gateway allows the sessions. This option applies only to Prisma Access Agent certificate authentication.
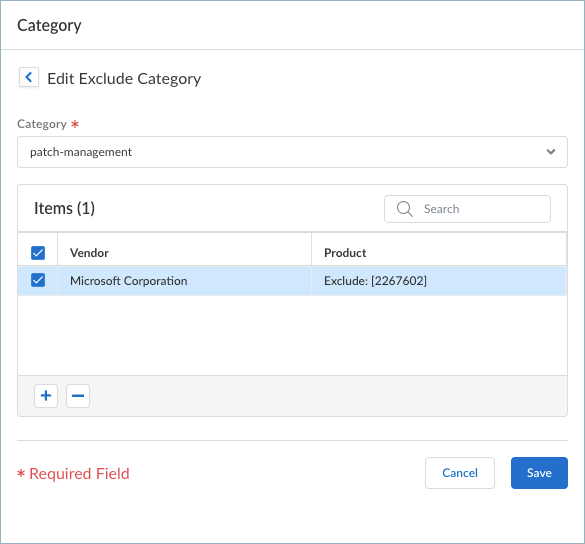
Save your settings when you're done.(Prisma Access Agent 25.7) Edit Exclude Categories to select entire HIP categories to exclude from data collection. (Not supported on Prisma Access Agent Linux)![]() When you exclude a complete category such as patch management, firewall, or anti-malware, the agent skips the OPSWAT query for that category, reducing HIP report generation time and network overhead. Within each category, you can exclude specific vendors or applications from HIP data collection.To specify categories to exclude in the Edit Exclude Category window:
When you exclude a complete category such as patch management, firewall, or anti-malware, the agent skips the OPSWAT query for that category, reducing HIP report generation time and network overhead. Within each category, you can exclude specific vendors or applications from HIP data collection.To specify categories to exclude in the Edit Exclude Category window:- Add a category.Select a Category (such as data-loss-prevention) to exclude from HIP collection.Click the + sign and select a particular Vendor from the list, and then add a specific Product from the vendor to further refine the exclusion as needed. You can add multiple vendors and products to the exclude list.For example:
![]() If you don't add a vendor and product, the entire category is excluded from HIP collection. Also, if you add a vendor but don't select a product, all products from the vendor be excluded.Save your settings in each dialog.Patch Exceptions: When you exclude the patch-management category entirely, the agent skips all patch-related OPSWAT queries, significantly improving performance for environments where patch compliance is managed through other systems. If you want to exclude specific patches, you can specify the patch name or number and optionally a date until which you want to exclude the patch updates from the HIP report using the following format:
If you don't add a vendor and product, the entire category is excluded from HIP collection. Also, if you add a vendor but don't select a product, all products from the vendor be excluded.Save your settings in each dialog.Patch Exceptions: When you exclude the patch-management category entirely, the agent skips all patch-related OPSWAT queries, significantly improving performance for environments where patch compliance is managed through other systems. If you want to exclude specific patches, you can specify the patch name or number and optionally a date until which you want to exclude the patch updates from the HIP report using the following format:Exclude: [kb-article-id1: MM/DD/YYYY], [kb-article-id2: MM/DD/YYYY]
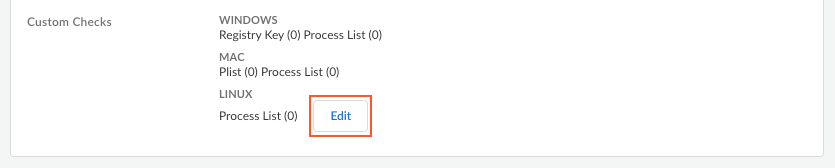
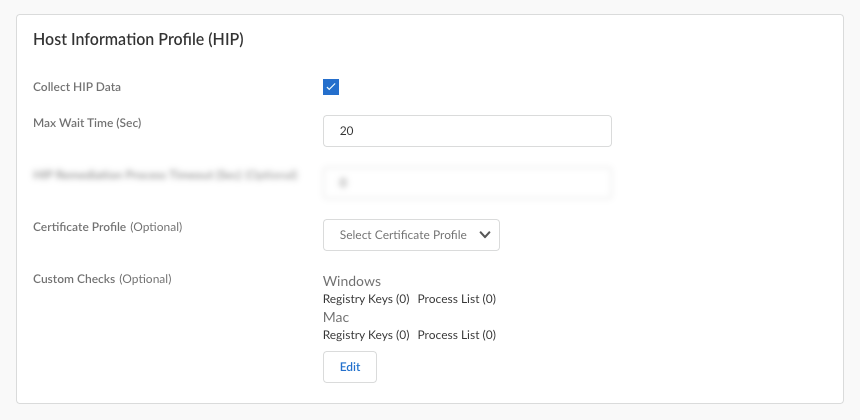
where <kb-article-id> is the name or number in the attribute (for example, KB2267602 without the KB prefix) and the MM/DD/YYYY specifies the date up to which the patch is excluded from the HIP report. If you do not set a date, the patch will be excluded from the HIP report indefinitely. If you choose to set a date, the patch will be excluded until the specified date.For example, to exclude Windows Defender definition updates (KB2267602) that frequently trigger false compliance failures, select Categorypatch-management, add any Vendor, and then specify Exclude: [2267602] in the Product column. (The vendor doesn't matter in the context of patch exceptions. All patches with the same KB article ID from any vendor will be excluded.)![]() Edit Custom Checks to specify any custom data you want to collect from the hosts running this configuration.
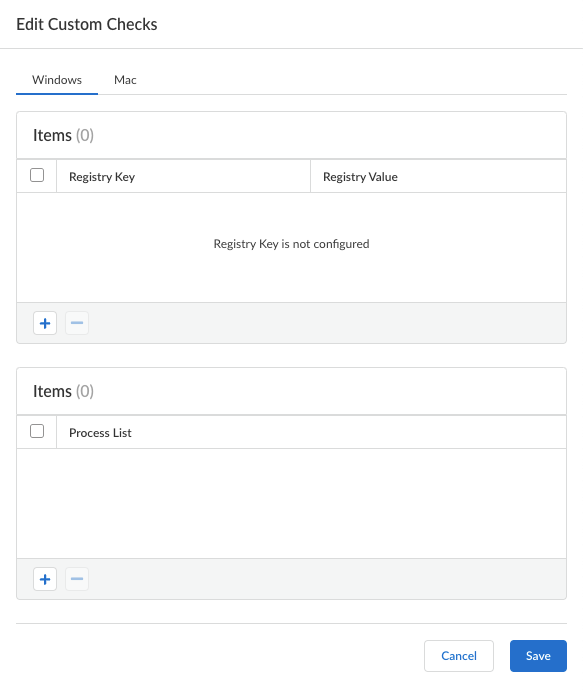
Edit Custom Checks to specify any custom data you want to collect from the hosts running this configuration.![]()
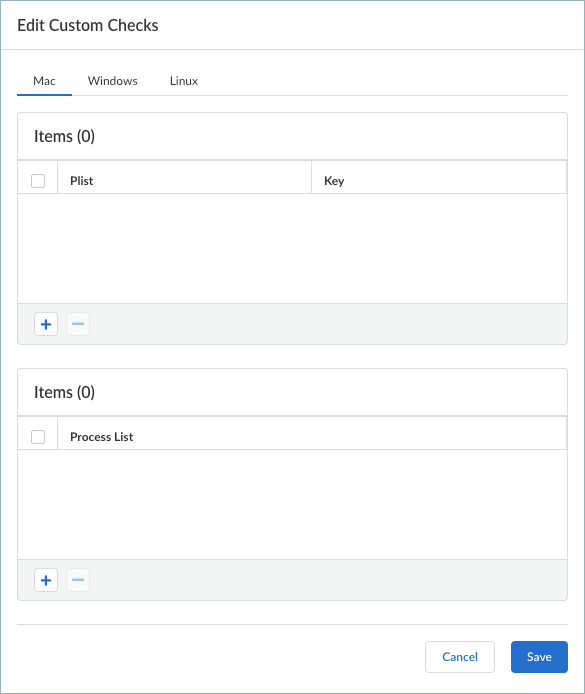
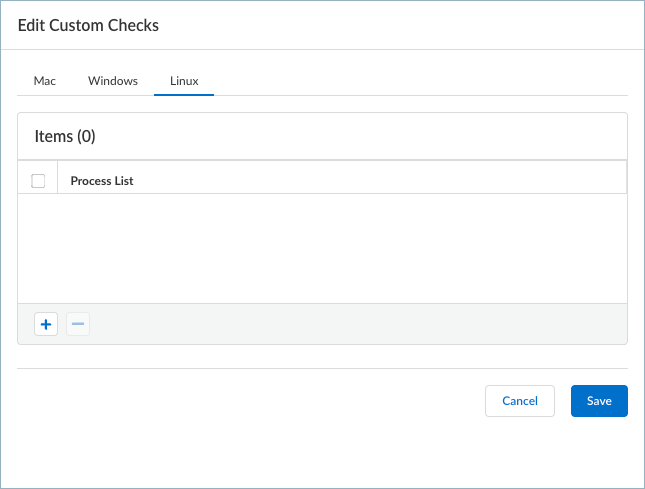
- Define custom checks to determine whether specific applications are installed and verify if particular processes are running on endpoints.
![]() For example, if you have any required applications that are not included in the Vendor or Product lists for creating HIP objects, you can create a custom check to determine whether that application is installed (it has a corresponding Windows registry or Mac plist key) or is currently running (has a corresponding running process).
For example, if you have any required applications that are not included in the Vendor or Product lists for creating HIP objects, you can create a custom check to determine whether that application is installed (it has a corresponding Windows registry or Mac plist key) or is currently running (has a corresponding running process).- Mac—Add a check for a particular Plist key or Key value. To restrict the data collection to specific key values, Add the Key values.Process List—Add the processes you want to check for on endpoints to see if they are running. For example, to determine whether a software application is running, add the name of the executable file to the process list.
- Windows—Add a check for a particular Registry Key or Registry Value. To restrict data collection to a specific Registry Value, Add and then define the specific registry values.Process List—Add the processes you want to check for on endpoints to see if they are running. For example, to determine whether a software application is running, add the name of the executable file to the process list.
- (Prisma Access Agent 26.1) Linux (Process List)—Add the processes you want to check for on endpoints to see if they are running. For example, to determine whether a software application is running, add the name of the executable file to the process list.
![]()
Save the custom check settings when you are done.When you have finished configuring the Prisma Access Agent settings, Save the configuration.
Configure HIP Data Collection Settings for the Prisma Access Agent (Panorama)
Define the custom host information profile data that you want Prisma Access Agent to collect for Panorama Managed Prisma Access or NGFW deployments.Define the custom host information profile (HIP) data that you want Prisma Access Agent to collect for Panorama Managed Prisma Access or NGFW deployments.- Navigate to the Prisma Access Agent setup.
- Prisma Access (Managed by Panorama)From the Cloud Services plugin in Panorama, select PanoramaCloud ServicesPrisma Access AgentLaunch Prisma Access Agent.
- NGFW (Managed by Panorama)Log in to Strata Cloud Manager as the administrator.
Select ConfigurationPrisma Access AgentSettings.![]() Select Prisma Access Agent.Select an existing agent configuration or Add Agent Settings to create a new configuration.
Select Prisma Access Agent.Select an existing agent configuration or Add Agent Settings to create a new configuration.![]() If you need to create or update an app configuration rule, follow the instructions in Configure Agent Settings for the Prisma Access Agent (Panorama). Otherwise, go to the next step.In the Host Information Profile (HIP) section, configure the HIP data collection settings.
If you need to create or update an app configuration rule, follow the instructions in Configure Agent Settings for the Prisma Access Agent (Panorama). Otherwise, go to the next step.In the Host Information Profile (HIP) section, configure the HIP data collection settings.![]()
- Select Collect HIP Data to enable HIP data collection on the endpoints that logged in to the gateway.Specify the Max Wait Time (in seconds) that the Prisma Access Agent should search for HIP data before submitting the available data. The range is 10-60 seconds; the default is 20 seconds.Select the Certificate Profile that the gateway uses to match the machine certificate sent by the Prisma Access Agent.For NGFW deployments, this certificate profile is the same one that you configured in the Infrastructure settings.Click Add Custom Checks to specify any custom data you want to collect from the hosts running this configuration.
- Define custom checks to determine whether specific applications are installed and verify if particular processes are running on endpoints.
![]() For example, if you have any required applications that are not included in the Vendor or Product lists for creating HIP objects, you can create a custom check to determine whether that application is installed (it has a corresponding Windows registry or Mac plist key) or is currently running (has a corresponding running process).
For example, if you have any required applications that are not included in the Vendor or Product lists for creating HIP objects, you can create a custom check to determine whether that application is installed (it has a corresponding Windows registry or Mac plist key) or is currently running (has a corresponding running process).- Mac—Add a check for a particular Plist key or Key value. To restrict the data collection to specific key values, Add the Key values.Process List—Add the processes you want to check for on endpoints to see if they are running. For example, to determine whether a software application is running, add the name of the executable file to the process list.
- Windows—Add a check for a particular Registry Key or Registry Value. To restrict data collection to a specific Registry Value, Add and then define the specific registry values.Process List—Add the processes you want to check for on endpoints to see if they are running. For example, to determine whether a software application is running, add the name of the executable file to the process list.
Save the custom check settings when you are done.When you have finished configuring the Prisma Access Agent settings, Create the configuration.
- Prisma Access (Managed by Panorama)