Prisma Access Agent
Configure Gateways for the Prisma Access Agent
Table of Contents
Configure Gateways for the Prisma Access Agent
Configure gateways to provide security enforcement for
traffic from Prisma Access Agents.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Gateways provide security enforcement for traffic from Prisma
Access Agents. Additionally, if the host information profile (HIP) feature is
enabled, the gateway generates a HIP report from the raw host data that the
endpoints submit, which it can use for policy enforcement.
Prisma Access Agent supports the following types of gateways:
- Internal—An internal gateway is an interface on the internal network that is configured as a gateway and applies security policies for internal resource access. When used with HIP checks, an internal gateway can be used to provide a secure, accurate method of identifying and controlling traffic based on user state, device state, or both. Internal gateways are useful in sensitive environments where authenticated access to critical resources is required. The Prisma Access Agent connects to the internal gateway after performing internal host detection to determine the location of the endpoint. If internal host detection isn't configured, the Prisma Access Agent first connects to the internal gateway followed by the external gateway upon connection failure.
- External gateway—An external gateway resides outside of the corporate network and provides security enforcement, tunnel access, or both for your remote users. By default, the Prisma Access Agent automatically connects to the Best Location external gateway, based on the priority you assign to the gateway, source region, and the response time.
After configuring the agent app settings, you can add the gateways that users can select in the Prisma Access Agent.
By default, all the gateways in your Prisma Access locations are
available to users. If you have on-premises gateways (internal or external) that you
want your users to connect to, you can add those gateways here.
You can configure gateways for Prisma Access or NGFW deployments.
Configure Gateways for the Prisma Access Agent (Prisma Access Deployment)
Configure gateways to provide security enforcement for
traffic from Prisma Access Agents in Prisma Access deployments.
Complete the steps to configure gateways for Prisma Access Agents.
The following procedure applies to both Strata Cloud Manager Managed Prisma Access and Panorama Managed
Prisma Access
deployments.
- Navigate to the Prisma Access Agent setup.
- From Strata Cloud Manager:
- Select ConfigurationNGFW and Prisma AccessConfiguration ScopeAccess AgentSetupPrisma Access Agent.
- From Panorama:
- From the Cloud Services plugin in Panorama, select PanoramaCloud ServicesPrisma Access AgentLaunch Prisma Access Agent.
- Select ConfigurationPrisma Access AgentSettingsPrisma Access Agent.
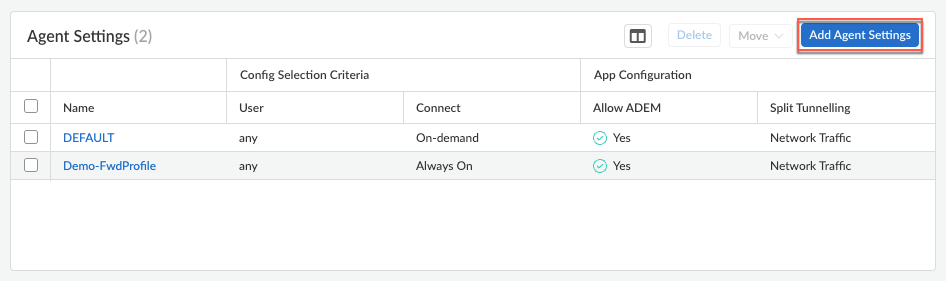
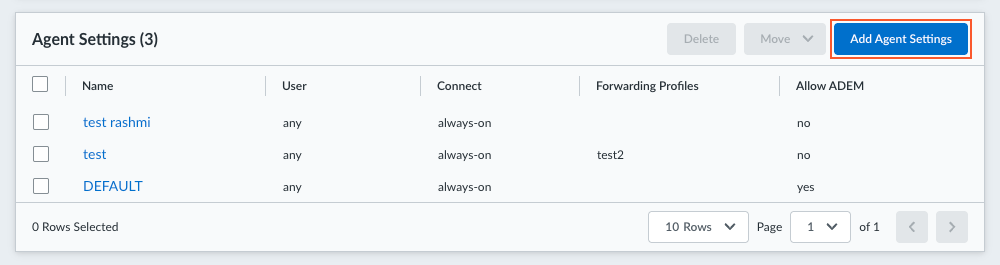
Select an existing agent configuration or Add Agent Settings to create a new configuration.![]() If you need to create or update an app configuration rule, follow the instructions in Configure Agent Settings for the Prisma Access Agent. Otherwise, go to the next step.To add an External Gateway to which your users can connect:
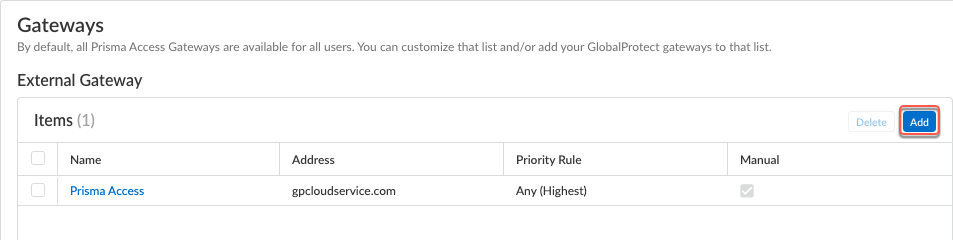
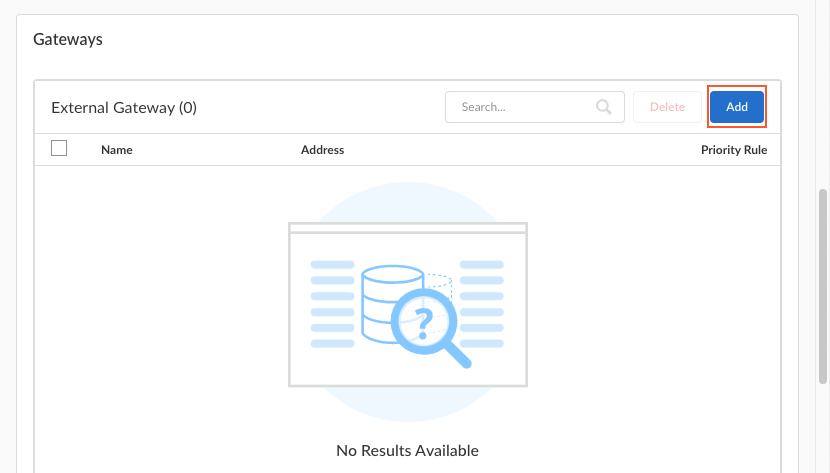
If you need to create or update an app configuration rule, follow the instructions in Configure Agent Settings for the Prisma Access Agent. Otherwise, go to the next step.To add an External Gateway to which your users can connect:- Click Add.
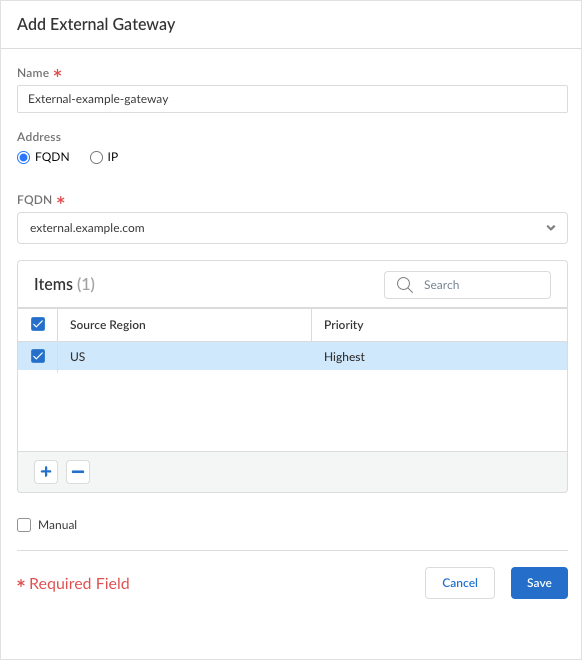
![]() Enter a descriptive Name for the gateway. The name you enter here should match the name you defined when you configured the gateway and should be descriptive enough for users to know the location of the gateway they are connected to.For Panorama Managed Prisma Access, you can only select a gateway that's already configured in Panorama.Enter the FQDN or IP address of the interface where the gateway is configured.You can configure an IPv4. The address you specify must exactly match the Common Name (CN) in the gateway server certificate.For Panorama Managed Prisma Access, this FQDN and IP values are inherited from Panorama. You cannot update them.Click the + sign to add one or more Source Regions for the gateway, or select Any to make the gateway available to all regions. When users connect, the Prisma Access Agent recognizes the region, and only allows users to connect to gateways that are configured for that region. For gateway selection, the source region is considered first, then gateway priority.Set the Priority of the gateway by clicking the field and selecting one of the following values:
Enter a descriptive Name for the gateway. The name you enter here should match the name you defined when you configured the gateway and should be descriptive enough for users to know the location of the gateway they are connected to.For Panorama Managed Prisma Access, you can only select a gateway that's already configured in Panorama.Enter the FQDN or IP address of the interface where the gateway is configured.You can configure an IPv4. The address you specify must exactly match the Common Name (CN) in the gateway server certificate.For Panorama Managed Prisma Access, this FQDN and IP values are inherited from Panorama. You cannot update them.Click the + sign to add one or more Source Regions for the gateway, or select Any to make the gateway available to all regions. When users connect, the Prisma Access Agent recognizes the region, and only allows users to connect to gateways that are configured for that region. For gateway selection, the source region is considered first, then gateway priority.Set the Priority of the gateway by clicking the field and selecting one of the following values:- If you have only one external gateway, leave the value as Highest (the default).
- If you have multiple external gateways, you can modify the priority values (ranging from Highest to Lowest) to indicate a preference for the specific user group to which this configuration applies. For example, if you prefer that the user group connects to a local gateway, you would set the priority higher than that of more geographically distant gateways. The priority value is then used to weight the agent’s gateway selection algorithm.
- If you don't want apps to automatically establish connections with the gateway, select Manual only. This setting is useful in testing environments.
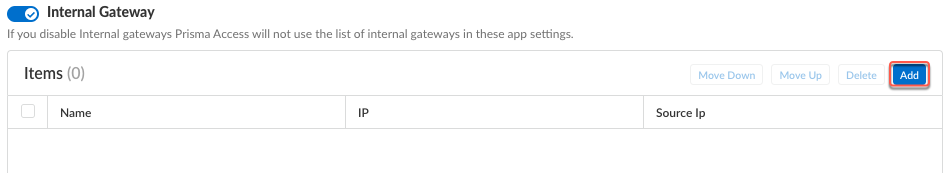
Select Manual to identify the external gateway as a manual gateway.A manual external gateway resides outside of the corporate network and provides security enforcement, tunnel access, or both for your remote users. The difference between the autodiscovery external gateway and the manual external gateway is that the Prisma Access Agent only connects to a manual external gateway when the user initiates a connection. You can also configure different authentication requirements for manual external gateways.Save your settings. For Panorama Managed Prisma Access, Update your settings.![]() Specify the internal gateways to which users with this configuration can connect.
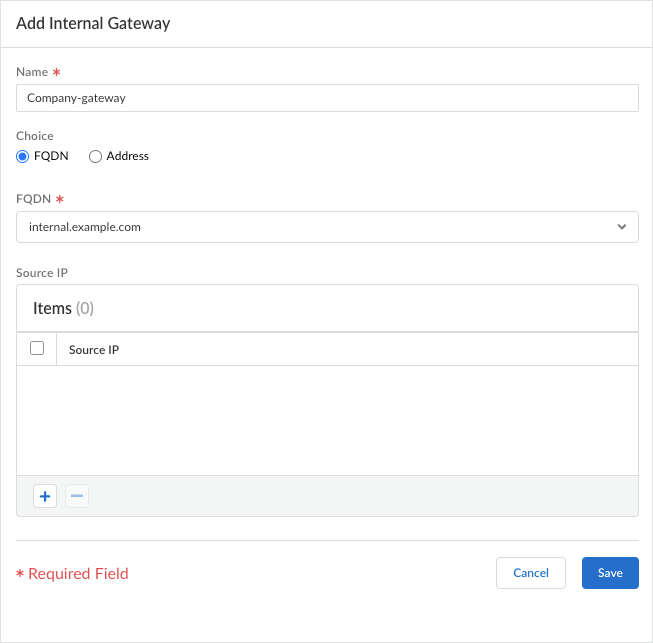
Specify the internal gateways to which users with this configuration can connect.- Select Internal Gateway and click Add.
![]() Enter a descriptive Name for the gateway. The name you enter here should match the name you defined when you configured the gateway and should be descriptive enough for users to know the location of the gateway they are connected to.For Panorama Managed Prisma Access, you can only select a gateway that's already configured in Panorama.Enter the FQDN or IP address of the interface where the gateway is configured.You can configure an IPv4. The address you specify must exactly match the Common Name (CN) in the gateway server certificate.For Panorama Managed Prisma Access, this FQDN and IP values are inherited from Panorama. You cannot update them.(Optional) Click the + sign to add one or more Source IP to the gateway configuration. The source IP address can be an IP subnet, range, or predefined address. The Prisma Access Agent supports IPv4 addresses. When users connect, the Prisma Access Agent recognizes the source address of the endpoint, and only allows users to connect to gateways that are configured for that address.Save your settings.For Panorama Managed Prisma Access, Update your settings.
Enter a descriptive Name for the gateway. The name you enter here should match the name you defined when you configured the gateway and should be descriptive enough for users to know the location of the gateway they are connected to.For Panorama Managed Prisma Access, you can only select a gateway that's already configured in Panorama.Enter the FQDN or IP address of the interface where the gateway is configured.You can configure an IPv4. The address you specify must exactly match the Common Name (CN) in the gateway server certificate.For Panorama Managed Prisma Access, this FQDN and IP values are inherited from Panorama. You cannot update them.(Optional) Click the + sign to add one or more Source IP to the gateway configuration. The source IP address can be an IP subnet, range, or predefined address. The Prisma Access Agent supports IPv4 addresses. When users connect, the Prisma Access Agent recognizes the source address of the endpoint, and only allows users to connect to gateways that are configured for that address.Save your settings.For Panorama Managed Prisma Access, Update your settings.![]()
Configure Gateways for the Prisma Access Agent (NGFW Deployment)
Configure gateways to provide security enforcement for traffic from Prisma Access Agents in NGFW deployments.You can add external and external gateways for Prisma Access Agent by selecting the external and internal gateways that you configured in the Infrastructure tab.The following procedure applies to NGFW (Managed by Panorama) deployments.- Navigate to the Prisma Access Agent setup.
- Log in to Strata Cloud Manager as the administrator.Select ConfigurationPrisma Access AgentSettings.
![]() Select Prisma Access Agent.Select an existing agent configuration or Add Agent Settings to create a new configuration.
Select Prisma Access Agent.Select an existing agent configuration or Add Agent Settings to create a new configuration.![]() If you need to create or update an app configuration rule, follow the instructions in Configure Agent Settings for the Prisma Access Agent (Panorama). Otherwise, go to the next step.Add an external gateway.
If you need to create or update an app configuration rule, follow the instructions in Configure Agent Settings for the Prisma Access Agent (Panorama). Otherwise, go to the next step.Add an external gateway.![]()
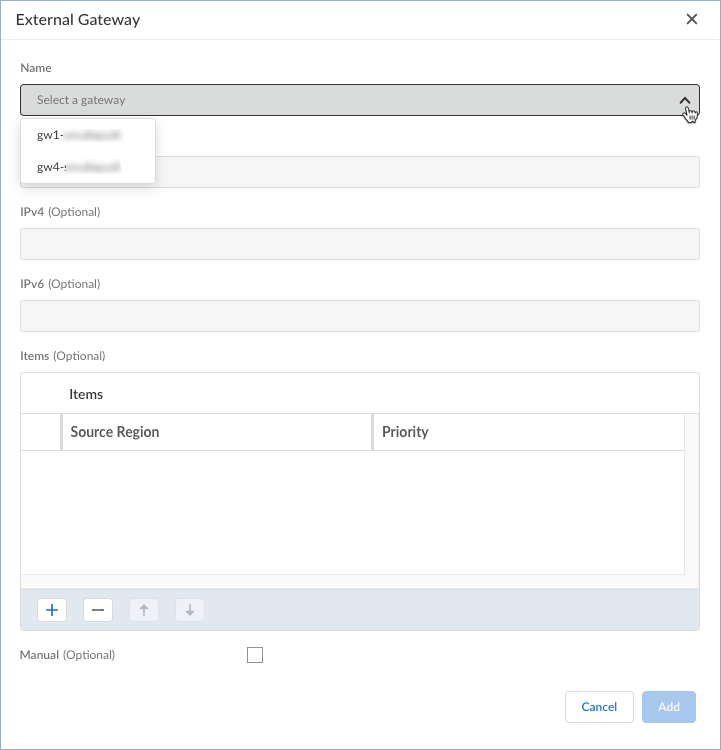
- Select a gateway. The gateways on the list are the same gateways that you added in the Infrastructure settings.
![]() You can’t enter the FQDN or IPv4 settings here, since the gateway is managed on the Infrastructure tab.(Optional) Click the + sign to add one or more Source Regions for the gateway, or select Any to make the gateway available to all regions. When users connect, the Prisma Access Agent recognizes the region, and only allows users to connect to gateways that are configured for that region. For gateway selection, the source region is considered first, then gateway priority.(Optional) Set the Priority of the gateway by clicking the field and selecting one of the following values:
You can’t enter the FQDN or IPv4 settings here, since the gateway is managed on the Infrastructure tab.(Optional) Click the + sign to add one or more Source Regions for the gateway, or select Any to make the gateway available to all regions. When users connect, the Prisma Access Agent recognizes the region, and only allows users to connect to gateways that are configured for that region. For gateway selection, the source region is considered first, then gateway priority.(Optional) Set the Priority of the gateway by clicking the field and selecting one of the following values:- If you have only one external gateway, leave the value as Highest (the default).
- If you have multiple external gateways, you can modify the priority values (ranging from Highest to Lowest) to indicate a preference for the specific user group to which this configuration applies. For example, if you prefer that the user group connects to a local gateway, you would set the priority higher than that of more geographically distant gateways. The priority value is then used to weight the agent’s gateway selection algorithm.
- If you don't want apps to automatically establish connections with the gateway, select Manual only. This setting is useful in testing environments.
(Optional) Select Manual to identify the external gateway as a manual gateway.A manual external gateway resides outside of the corporate network and provides security enforcement, tunnel access, or both for your remote users. The difference between the autodiscovery external gateway and the manual external gateway is that the Prisma Access Agent only connects to a manual external gateway when the user initiates a connection. You can also configure different authentication requirements for manual external gateways.Add the gateway settings.Add an internal gateway. Follow the steps for adding an external gateway. The steps are similar.![]()
- From Strata Cloud Manager: