- Home
- Prisma Access Agent
- Prisma Access Agent Administration
- Configure the Prisma Access Agent
- Set Up Prisma Access Agent User Authentication
- Set Up SAML Authentication With Cloud Identity Engine
- Prisma Access Agent Embedded Browser for SAML Authentication
- Configure Prisma Access Agent to Use the Default System Browser for SAML Authentication
Prisma Access Agent
Configure Prisma Access Agent to Use the Default System Browser for SAML Authentication
Table of Contents
Configure Prisma Access Agent to Use the Default System Browser for SAML Authentication
Learn how to configure the Prisma Access Agent to use the default system browser for
SAML authentication.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
If you configure the Prisma Access Agent to authenticate users via SAML
authentication, the agent will by default use the Prisma Access Agent embedded browser for SAML
authentication. If you don’t want to use the embedded browser for SAML
authentication, you can configure the agent to use the endpoint's default system
browser, such as Chrome, Firefox, or Safari (on macOS systems).
With the default system browser, end users can connect to the Prisma Access Agent or
other SAML-enabled applications without having to reenter their credentials for a
seamless single sign-on (SSO) experience. End users benefit from using the default
system browser for SAML authentication because they can use the same login for
Prisma Access Agent with their saved user credentials on the default system
browser.
In addition, on any browser that supports the Web Authentication (WebAuthn) API, you
can use Universal 2nd Factor (U2F) security tokens such as YubiKeys for multi-factor
authentication (MFA) to identify providers (IdPs) such as Azure or Okta.
If you use the default system browser for SAML
authentication, the browser tab remains open upon successful authentication. If the
user does not close the browser tab each time after authentication, multiple browser
tabs can remain open.
You can configure the default system browser through predeployment using the configuration file
(config.json), user-specific configurations on Strata Cloud
Manager, or local overrides using the pacli command.
- Configure the Prisma Access Agent to use the default system browser using one of the following methods.
- Use preconfiguration by installing the agent with the configuration file
(config.json) that defines the intended browser
type. To enable the system browser for SAML authentication, include the
following key in
config.json:
"use_external_browser_for_auth": true
The default is to use the embedded browser for SAML authentication. - (Strata Cloud Manager Managed Prisma Access only) Configure the Prisma Access Agent
settings. The settings are applied per user or user group and take
precedence over the config.json settings.
- Navigate to the Prisma Access Agent tab.
- Log in to Strata Cloud Manager as the administrator.
- Select ConfigurationNGFW and Prisma AccessConfiguration ScopeAccess AgentSetupPrisma Access Agent.
- Configure user authentication settings if needed for the user or user group for which you want to enable the default system browser.
- Add an agent setting or edit an existing agent setting.
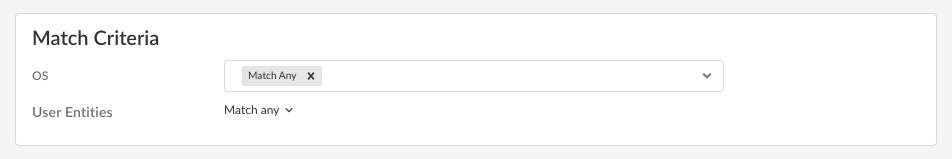
- Select the criteria (OS or
User Entities) that match the user or
user group for which you want to enable the default system
browser.
![]()
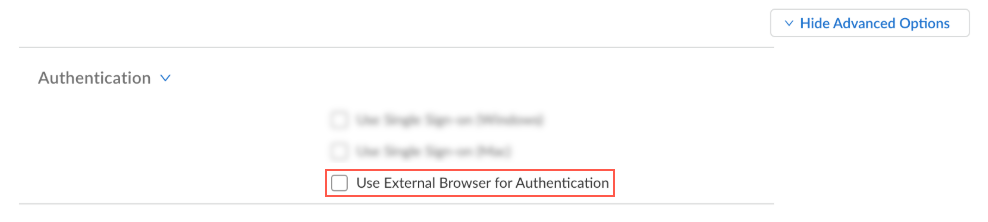
- Enable the option to use the default system browser for
authentication. Select Show Advanced OptionsAuthentication and enable Use External Browser for Authentication. The default is unchecked (use the embedded browser).
![]()
- Configure other agent settings if needed and Save the settings.
- Push the configuration by selecting Push ConfigPush.
- Navigate to the Prisma Access Agent tab.
- Configure browser type settings using the pacli
command. To set the system browser for SAML authentication, use the
following command on the endpoint:
pacli browser system
The pacli setting takes the highest precedence on browser selection. The default is to use the embedded browser for SAML authentication (pacli browser internal).
You can use any of these methods, but the last setting overrides all other settings. Performing a configuration push on Strata Cloud Manager overrides the PACli command as well.(Optional) To verify and troubleshoot the browser configuration.- Check the current browser setting by running the following command on the endpoint:
pacli browser
Check the agent logs for browser-related activities. Browser-related logs are written to the following files on the endpoint.On Windows:%ProgramData%\Palo Alto Networks\Prisma Access Agent\Logs\PABrowser.logOn macOS:~/Library/Logs/PaloAltoNetworks/Prisma Access Agent/PABrowser.log
- Use preconfiguration by installing the agent with the configuration file
(config.json) that defines the intended browser
type. To enable the system browser for SAML authentication, include the
following key in
config.json: