Prisma Access Agent
Configure IPv6 Sinkhole for Prisma Access Agent
Table of Contents
Configure IPv6 Sinkhole for Prisma Access Agent
Learn how to configure the IPv6 sinkhole feature for Prisma Access Agent to enhance
security by tunneling and blocking IPv6 traffic.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
In a dual-stack endpoint that can process both IPv4 and IPv6 traffic, the Prisma
Access Agent sends mobile user IPv4 traffic through the tunnel to Prisma Access for
protection.
To reduce the attack surface for IPv6-based threats, you can configure Prisma Access
Agent to sinkhole IPv6 traffic. Because endpoints can automatically fall back to an
IPv4 address, sinkholing IPv6 traffic enables a secure and uninterrupted user
experience for mobile user traffic to the internet.
You can configure Prisma Access Agent so that it sinkholes all mobile user IPv6
traffic by tunneling and blocking IPv6 traffic. When you enable this functionality,
Prisma Access Agent assigns an IPv6 address to the connecting endpoint in addition
to an IPv4 address; then, it routes the IPv6 traffic to Prisma Access and discards
it using a built-in security policy.
While certain edge cases like IPv6 localhost, LAN, link-local, and DHCPv6 are not
routed to the gateway, the IPv6 sinkhole feature significantly enhances your ability
to manage and secure IPv6 traffic within your Prisma Access environment.
Prisma Access Agent for Linux does not support IPv6 sinkholing. In order to
reduce the attack surface from IPv6-based threats, users must disable IPv6 before installing the
agent.
To sinkhole all mobile user IPv6 traffic in Prisma Access Agent deployments, complete
the following steps:
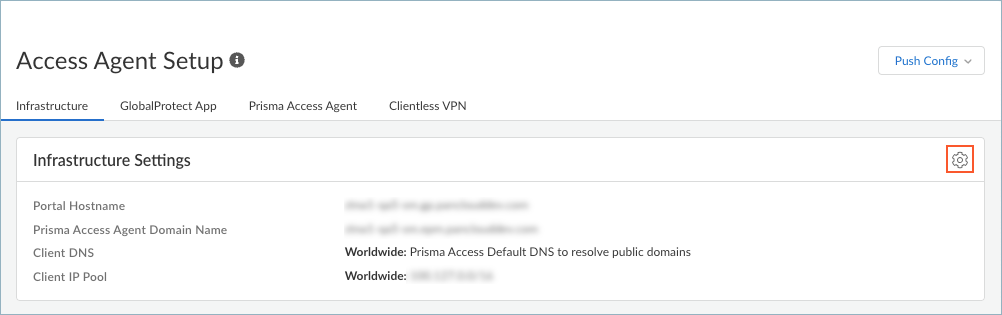
- In Strata Cloud Manager, select ConfigurationNGFW and Prisma AccessConfiguration ScopeAccess AgentSetupInfrastructure.Edit the infrastructure settings.
![]() If you're on a coexistence tenant (with the GlobalProtect™ app), select Filter ByPrisma Access Agent to show only the settings that are related to Prisma Access Agent.
If you're on a coexistence tenant (with the GlobalProtect™ app), select Filter ByPrisma Access Agent to show only the settings that are related to Prisma Access Agent.![]() Select Force IPv6 Sinkhole.Default: DeselectedPrisma Access uses fc00:0:0:0:0:0:0:0/64 as the sinkhole address.
Select Force IPv6 Sinkhole.Default: DeselectedPrisma Access uses fc00:0:0:0:0:0:0:0/64 as the sinkhole address.![]() Save your infrastructure settings and push the configuration.Verify that IPv6 traffic has been sinkholed by running the following PACli command on an endpoint:
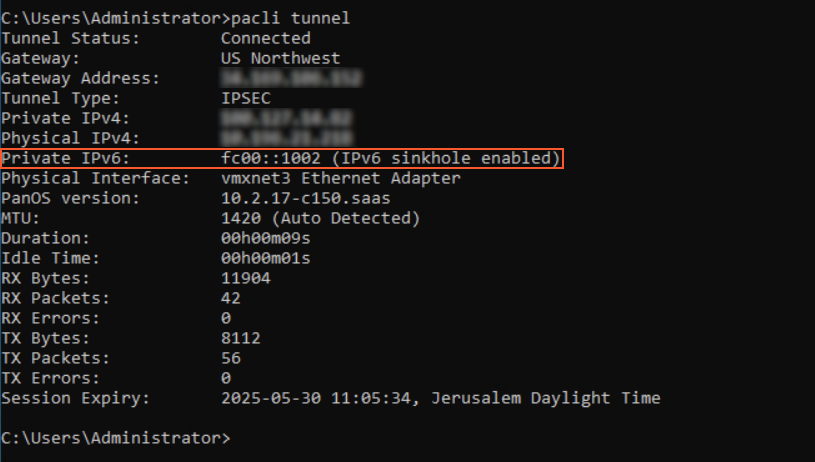
Save your infrastructure settings and push the configuration.Verify that IPv6 traffic has been sinkholed by running the following PACli command on an endpoint:pacli tunnel
For example, on the Windows agent, the output will look similar to the following:![]()