Prisma Access Agent
Configure Windows Hello for Business Authentication for Prisma Access Agent
Table of Contents
Configure Windows Hello for Business Authentication for Prisma Access Agent
Configure your environment to use Windows Hello for Business authentication with
Prisma Access Agent.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
To enable Windows Hello for Business authentication with Prisma Access Agent, you
need to properly configure both your Microsoft Entra ID environment and Cloud
Identity Engine. This procedure guides you through the necessary steps to set up
this integration.
Once configured, Prisma Access Agent will automatically detect the availability of
Primary Refresh Tokens on your users' devices and leverage Windows Hello for
Business authentication methods. Users will be able to authenticate using their
configured personal identification number (PIN) or biometric methods without
additional web-based authentication steps.
Single sign-on with Windows Hello for Business is supported with either the Prisma Access Agent embedded
browser or the default system browser for SAML
authentication. You can configure the agent settings to suppress the embedded browser so that it won't appear.
- Configure Microsft Entra ID and Windows Hello for Business.
- Connect your Windows systems to Microsoft Entra ID.This enables Entra to manage authentication policy rules for your devices. Consult Microsoft's documentation for detailed procedures on joining devices to Microsoft Entra.Configure Windows Hello for Business policy rules in Microsoft Entra ID.Set up policy rules that enforce PIN requirements, biometric authentication methods (facial recognition, fingerprint), and other security settings according to your organization's requirements.Preconfigure end-user devices with Windows Hello for Business.Ensure your users have registered their biometric data or created PINs according to your organization's policy rules. This step is crucial for enabling Primary Refresh Token generation on user devices.Configure Cloud Identity Engine.
- Configure Entra ID as an identity provider (IdP) in Cloud Identity Engine. Create a Security Assertion Markup Language (SAML) 2.0 authentication type for Azure type and configure the SAML settings to integrate with your Azure AD environment.
- Set up an authentication profile and associate the profile with the Azure authentication type you created.
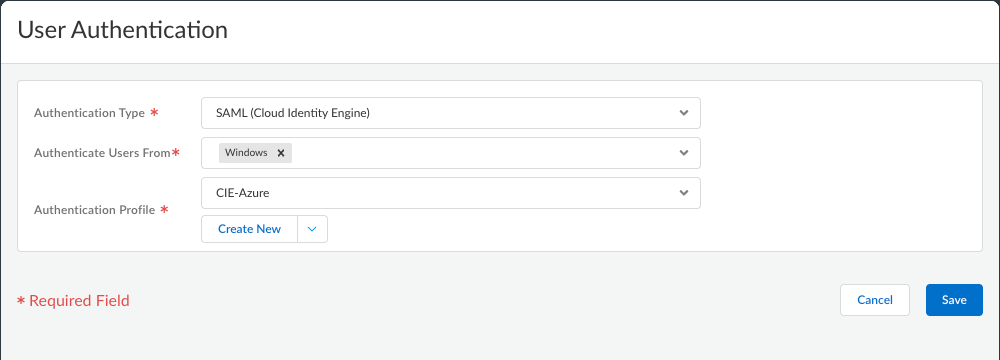
Check the user authentication and app configuration for Prisma Access Agent.- Set up user authentication for Prisma Access Agent using SAML with Cloud Identity Engine.
- In the User Authentication section, make sure the configured
authentication type is SAML.For example, on Strata Cloud Manager Managed Prisma Access:
![]()
- In the App Configuration section, make sure the Connect method is set to Always On.
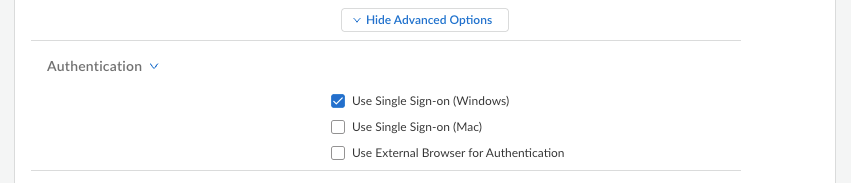
- (Optional) To prevent the Prisma
Acesss Agent embedded browser from appearing during single sign-on,
select Show Advanced OptionsAuthentication and enable Use Single Sign-on
(Windows).
![]()
- Go to ConfigurationConfigure NGFW and Prisma Access and make sure the authentication profile mapped in the SAML user authentication is mapped to the Azure AD or Entra ID as the IdP.
If you made any changes, save and push the configuration.Your Entra ID-joined users can now log in to their Windows devices with their PIN or biometric method and see that Prisma Access Agent is in the connected state.