Configure Azure as an IdP in the Cloud Identity Engine
Table of Contents
Expand all | Collapse all
-
- Cloud Identity Engine Attributes
- Collect Custom Attributes with the Cloud Identity Engine
- View Directory Data
- Cloud Identity Engine User Context
- Create a Cloud Dynamic User Group
- Configure Third-Party Device-ID
- Configure an IP Tag Cloud Connection
- View Mappings and Tags
- Configure Dynamic Privilege Access in the Cloud Identity Engine
- Send Cortex XDR Risk Signals to Okta
- Configure SSF Okta Receiver as a Risk Connection
- Configure the Secrets Vault
-
- Set Up Password Authentication
-
- Configure Azure as an IdP in the Cloud Identity Engine
- Configure Okta as an IdP in the Cloud Identity Engine
- Configure PingOne as an IdP in the Cloud Identity Engine
- Configure PingFederate as an IdP in the Cloud Identity Engine
- Configure Google as an IdP in the Cloud Identity Engine
- Configure a SAML 2.0-Compliant IdP in the Cloud Identity Engine
- Set Up a Client Certificate
- Configure an OIDC Authentication Type
- Set Up an Authentication Profile
- Configure Cloud Identity Engine Authentication on the Firewall or Panorama
- Configure the Cloud Identity Engine as a Mapping Source on the Firewall or Panorama
- Configure Dynamic Privilege Access in the Cloud Identity Engine
- Get Help
Configure Azure as an IdP in the Cloud Identity Engine
Learn how to configure Azure as an identity provider
in the Cloud Identity Engine to use as an authentication type for
user authentication.
- Download the Cloud Identity Engine integration in the Azure Portal.
- If you have not already done so, activate the Cloud Identity Engine app.Log in to the Azure Portal and select Azure Active Directory.Make sure you complete all the necessary steps in the Azure portal.
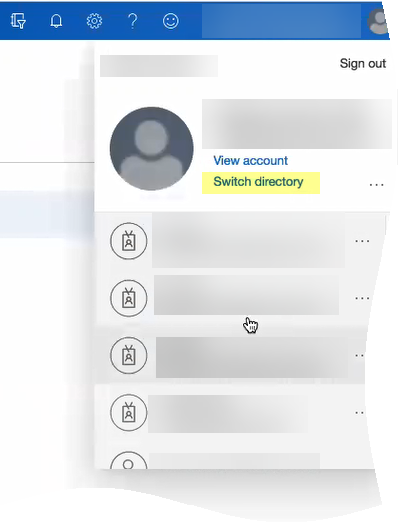
![]() If you have more than one directory, Switch directory to select the directory you want to use with the Cloud Identity Engine.
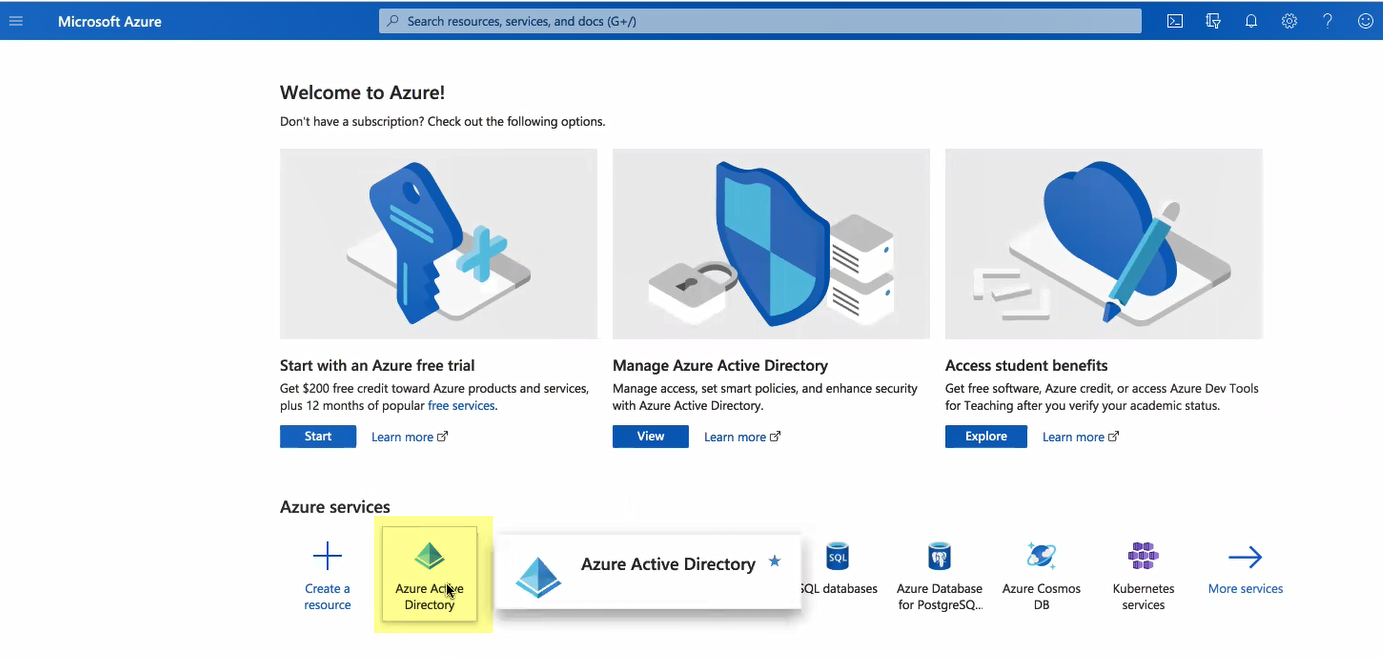
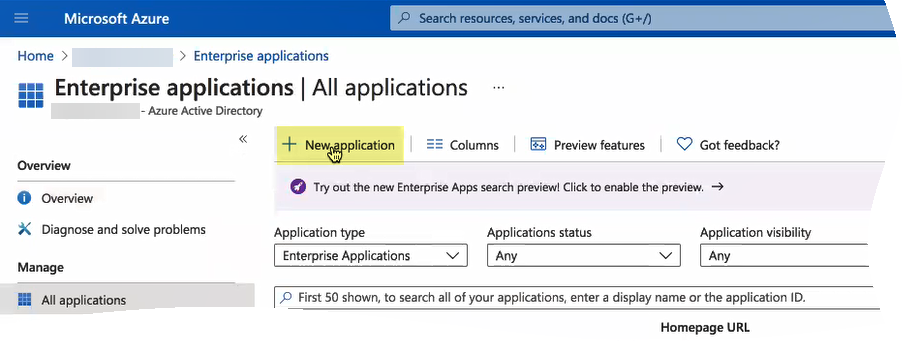
If you have more than one directory, Switch directory to select the directory you want to use with the Cloud Identity Engine.![]() Select Enterprise applications and click New application.
Select Enterprise applications and click New application.![]() Add from the gallery then enter Palo Alto Networks Cloud Identity Engine - Cloud Authentication Service and download the Azure AD single-sign on integration.After the application loads, select Users and groups, then Add user/group to Assign them to this application.Select the users and groups you want to use the Azure IdP in the Cloud Identity Engine for authentication.Be sure to assign the account you're using so you can test the configuration when it's complete. You may need to refresh the page after adding accounts to successfully complete the test.Select Single sign-on then select SAML.Upload Metadata File by browsing to the metadata file that you downloaded from the Cloud Identity Engine app and click Add.After the metadata uploads, Save your configuration.(Optional) Edit your User Attributes & Claims to Add a new claim or Edit an existing claim.If you attempt to test the configuration on the Azure Admin Console, a 404 error displays because the test is triggered by the IdP and the Cloud Identity Engine supports authentication requests initiated by the service provider.Configure Azure AD for the Cloud Identity Engine.
Add from the gallery then enter Palo Alto Networks Cloud Identity Engine - Cloud Authentication Service and download the Azure AD single-sign on integration.After the application loads, select Users and groups, then Add user/group to Assign them to this application.Select the users and groups you want to use the Azure IdP in the Cloud Identity Engine for authentication.Be sure to assign the account you're using so you can test the configuration when it's complete. You may need to refresh the page after adding accounts to successfully complete the test.Select Single sign-on then select SAML.Upload Metadata File by browsing to the metadata file that you downloaded from the Cloud Identity Engine app and click Add.After the metadata uploads, Save your configuration.(Optional) Edit your User Attributes & Claims to Add a new claim or Edit an existing claim.If you attempt to test the configuration on the Azure Admin Console, a 404 error displays because the test is triggered by the IdP and the Cloud Identity Engine supports authentication requests initiated by the service provider.Configure Azure AD for the Cloud Identity Engine.- Select Single sign-on then select SAML.Edit the Basic SAML Configuration settings.Upload metadata file and select the metadata file you downloaded from the Cloud Identity Engine in the first step.Enter your regional endpoint as the Sign-on URL using the following format: https://<RegionUrl>.paloaltonetworks.com/sp/acs (where <RegionUrl> is your regional endpoint). For more information on regional endpoints, see Configure Cloud Identity Engine Authentication on the Firewall or Panorama.Copy the App Federation Metadata Url and save it to a secure location.At this point in the process, you may see the option to Test sign-in. If you try to test the single sign-on configuration now, the test won't be successful. You can test your configuration to verify it's correct in step 9.Add and assign users who you want to require to use Azure AD for authentication.
- Select Azure Active Directory then select UsersAll users.Create a New user and enter a Name, User name.Select Show password, copy the password to a secure location, and Create the user.In the Palo Alto Networks Cloud Identity Engine - Cloud Authentication Service integration in the Azure Portal, select Users and groups.Add user then select Users and groups.Add Azure as an authentication type in the Cloud Identity Engine app.
- In the Cloud Identity Engine app, select AuthenticationAuthentication Types then click Add New Authentication Type.
![]() Set Up a SAML 2.0 authentication type.
Set Up a SAML 2.0 authentication type.![]() Select the Metadata Type you want to use.
Select the Metadata Type you want to use.- To use the client credential flow, the auth code flow, or SCIM, select Single service provider metadata.
- To Configure Dynamic Privilege Access in the Cloud Identity Engine, select Dynamic service provider metadata.
![]() Copy the Entity ID and Assertion Consumer Service URL and save them in a secure location.
Copy the Entity ID and Assertion Consumer Service URL and save them in a secure location.![]() Download SP Certificate and Download SP Metadata and save them in a secure location.
Download SP Certificate and Download SP Metadata and save them in a secure location.![]() Enter a unique and descriptive Profile Name.
Enter a unique and descriptive Profile Name.![]() Select Azure as your Identity Provider Vendor.
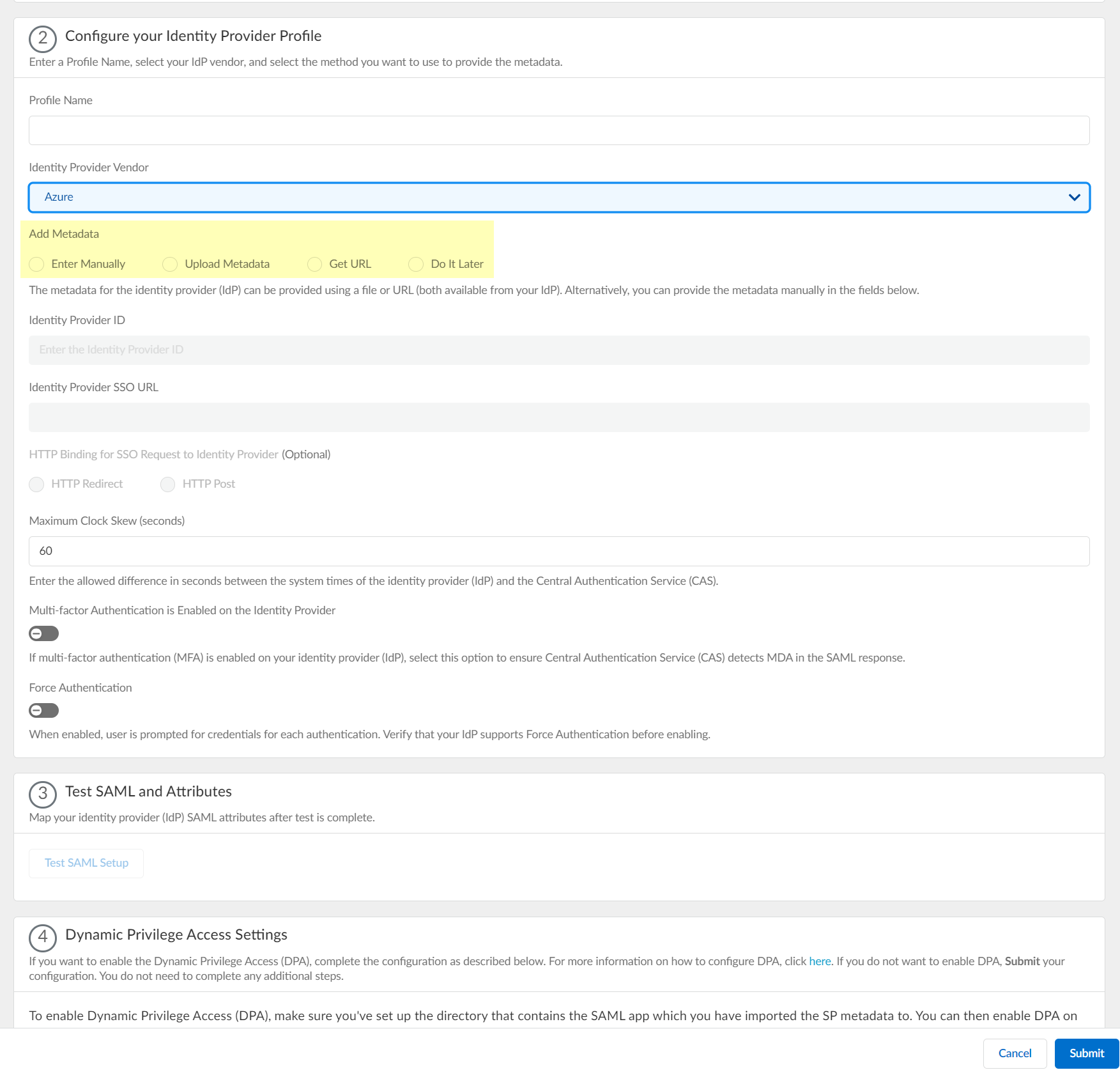
Select Azure as your Identity Provider Vendor.![]() Select the method you want to use to Add Metadata.
Select the method you want to use to Add Metadata.![]()
- If you want to enter the information manually, copy the identity
provider ID and SSO URL, download the certificate, then enter the
information in the Cloud Identity Engine IdP profile.
- Copy the necessary information from the Azure Portal and enter
it in the IdP profile on the Cloud Identity Engine app as
indicated in the following table:
Copy or Download from Azure Portal Enter in Cloud Identity Engine IdP Profile Copy the Azure AD Identifier. Enter it as the Identity Provider ID. Download the Certificate (Base64). Click Browse files to select the Identity Provider Certificate you downloaded from the Azure Portal. Copy the Login URL. Enter the URL as the Identity Provider SSO URL. ![]()
- (Optional) Select the HTTP Binding for SSO Request to
Identity Provider (Optional) method you want to
use for the SAML binding that allows the firewall and IdP to
exchange request and response messages:
- HTTP Redirect—Transmit SAML messages through URL parameters.
- HTTP Post—Transmit SAML messages using base64-encoded HTML.
![]()
- Copy the necessary information from the Azure Portal and enter
it in the IdP profile on the Cloud Identity Engine app as
indicated in the following table:
- If you want to upload a metadata file, download the metadata file from
your IdP management system.
- In the Azure Portal, Download the Federation Metadata XML and Save it to a secure location.
- In the Cloud Identity Engine app, click Browse files to select the metadata file, then Open the metadata file.
![]()
- If you want to use a URL to retrieve the metadata, copy the
App Federation Metadata Url, then paste it in
the profile as the Identity Provider Metadata URL
and click Get URL to obtain the
metadata.Palo Alto Networks recommends using this method to configure Azure as an IdP.
![]()
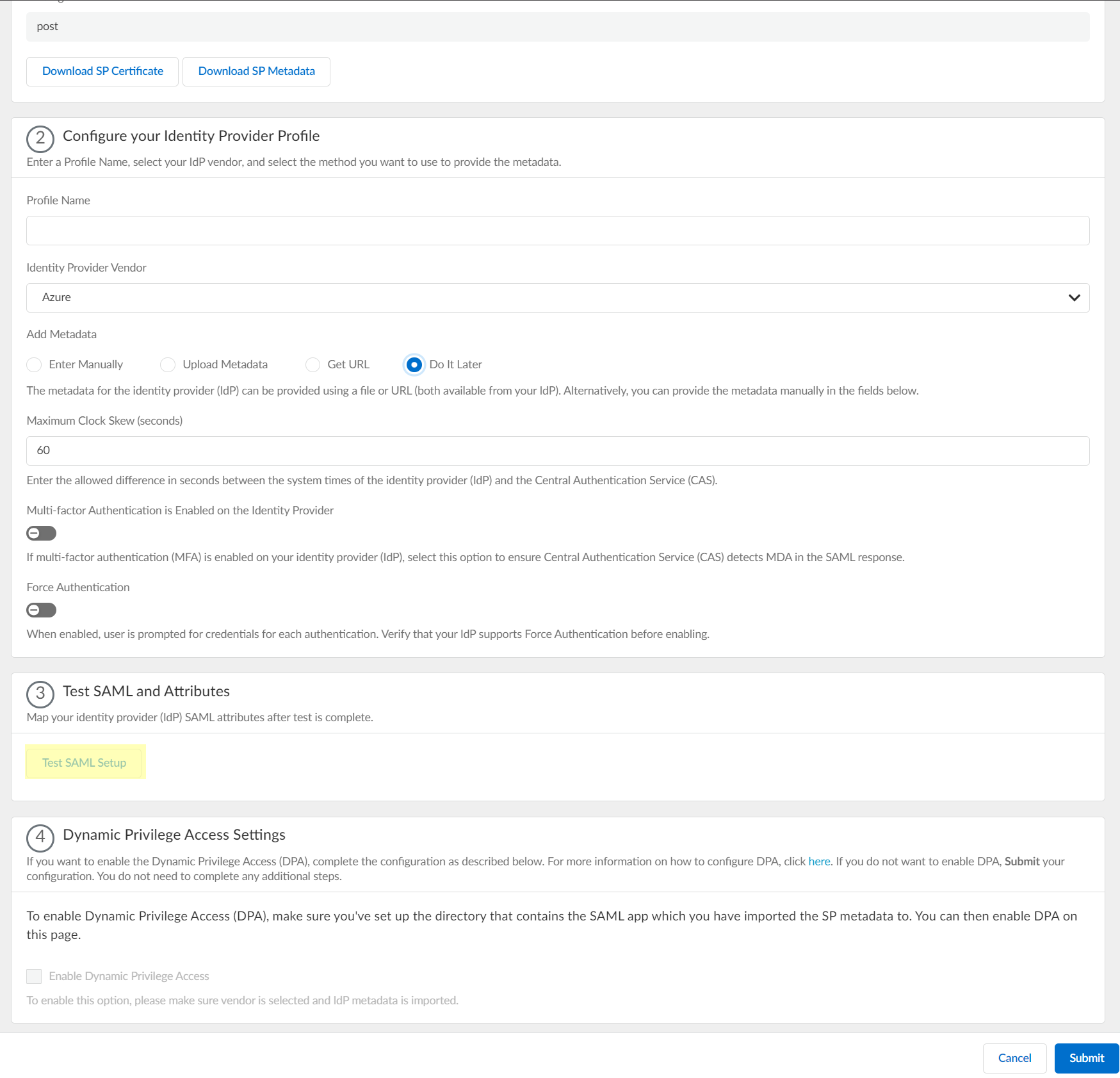
- If you don't want to
enter the configuration information now, you can Do it
later. This option allows you to submit the profile
without including configuration information. However, you must edit the
profile to include the configuration information to use the
authentication type in an authentication profile.
![]()
Specify the Maximum Clock Skew (seconds), which is the allowed difference in seconds between the system times of the IdP and the firewall at the moment when the firewall validates IdP messages (default is 60; range is 1–900). If the difference exceeds this value, authentication fails.![]() Select Multi-factor Authentication is Enabled on the Identity Provider if your Azure configuration uses multi-factor authentication (MFA).
Select Multi-factor Authentication is Enabled on the Identity Provider if your Azure configuration uses multi-factor authentication (MFA).![]() To require users to log in using their credentials to reconnect to GlobalProtect, enable Force Authentication.
To require users to log in using their credentials to reconnect to GlobalProtect, enable Force Authentication.![]() Click Test SAML setup to verify the profile configuration.This step is necessary to confirm that your firewall and IdP can communicate.If you do not provide the vendor information, the SAML test passes so that you can still submit the configuration.
Click Test SAML setup to verify the profile configuration.This step is necessary to confirm that your firewall and IdP can communicate.If you do not provide the vendor information, the SAML test passes so that you can still submit the configuration.![]() Select the SAML attributes you want the firewall to use for authentication and Submit the IdP profile.
Select the SAML attributes you want the firewall to use for authentication and Submit the IdP profile.- In the Azure Portal, Edit the User Attributes & Claims.
- (Optional) In the Cloud Identity Engine app, enter the Username Attribute, Usergroup Attribute, Access Domain, User Domain, and Admin Role.
- Submitthe profile.
![]() If you want to Enable Dynamic Privilege Access, ensure completion of the prerequisites before enabling this option, then Submit your changes to confirm the configuration.For more information, refer to Configure Dynamic Privilege Access in the Cloud Identity Engine.
If you want to Enable Dynamic Privilege Access, ensure completion of the prerequisites before enabling this option, then Submit your changes to confirm the configuration.For more information, refer to Configure Dynamic Privilege Access in the Cloud Identity Engine.![]()