Prisma Browser
Configure Network Protection
Table of Contents
Expand All
|
Collapse All
Prisma Browser Docs
Configure Network Protection
Configure Network Protection.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
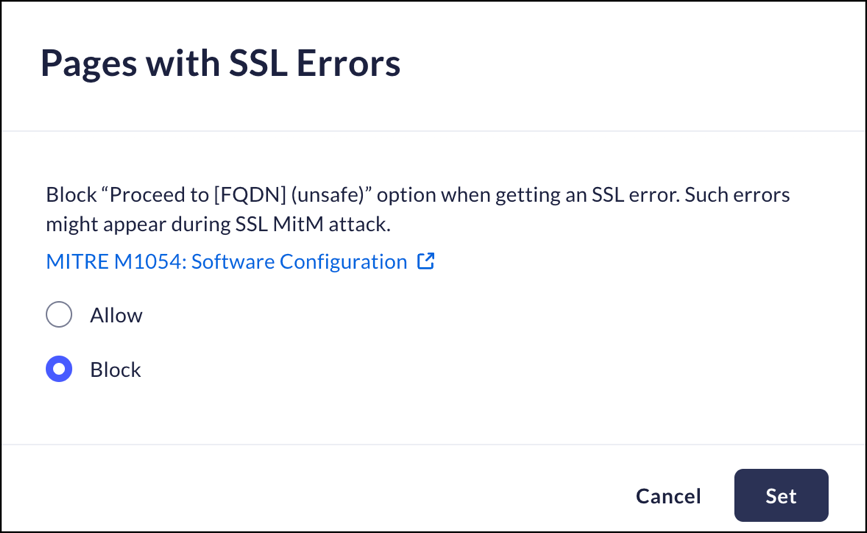
Pages with SSL Errors
Mobile Browser - Full support
This feature manages how the Prisma Browser will react when it
encounters a page with an SSL error. In general, most browsers ask for
permission to "Proceed to [FQDN] (unsafe)".
Since SSL errors can occur during an SSL MitM attack, you can use this
control to block the "Proceed..." functionality.
- From Strata Cloud Manager, select ConfigurationPrisma Browser PolicyControlsBrowser SecuritySelect Pages with SSL Errors.Select one of the following options:
- Allow - Allow users to bypass the blocking page when an SSL issue is identified.
- Block – The Prisma Browser will block the "Proceed..." option when an SSL issue is identified.
Click Set.![]()
DNS-Over-HTTPS
Mobile Browser - No supportThis feature manages the DNS resolution over the HTTPS protocol. It is used for encrypting requests.This assists in preventing MitM attacks.- From Strata Cloud Manager, select ConfigurationPrisma Browser PolicyControlsBrowser SecuritySelect DNS-Over-HTTPS.Select one of the following options:
- Enable - Enter the following information:Upon DNS over HTTPS resolve failure:
- Fail-open: Resolve using plain DNS.
- Fail-close: Do not resolve.
- Enter the DNS-over-HTTPS resolver's URL.
- Disable – Prisma Browser will not enable DNS over HTTPS resolution.
Click Set.![]()
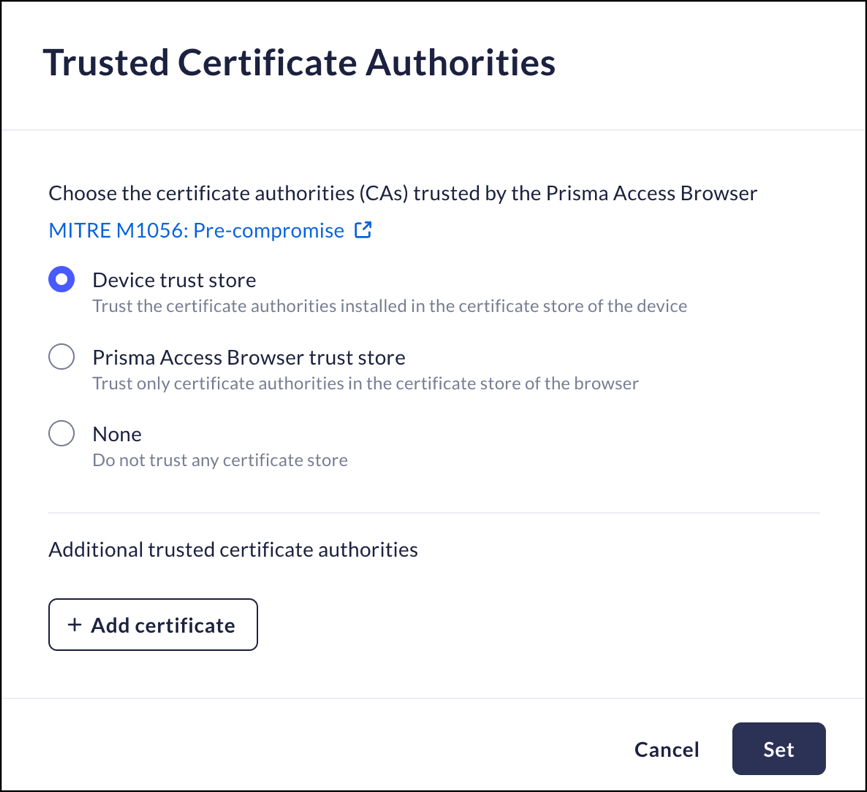
Trusted Certificate Authorities
Mobile Browser - Partial supportThis feature manages how the Prisma Browser manages certificates.- From Strata Cloud Manager, select ConfigurationPrisma Browser PolicyControlsBrowser SecuritySelect Trusted Certificate Authorities.Select the certificate authorities that are to be trusted by the Prisma Browser (this limits the trust to certificates that are already trusted):
- Device trust store - Trust the certificate authorities installed in the device's certificate store.
- Prisma Access Browser trust store - Trust only certificate authorities that are trusted by Palo Alto Networks, and ignores certificates installed in the Device trust store.
- None - Do not trust certificates in any trust store.Prisma Browser for Mobile rules using this control must use one of the Trust Stores. The None option is ignored.
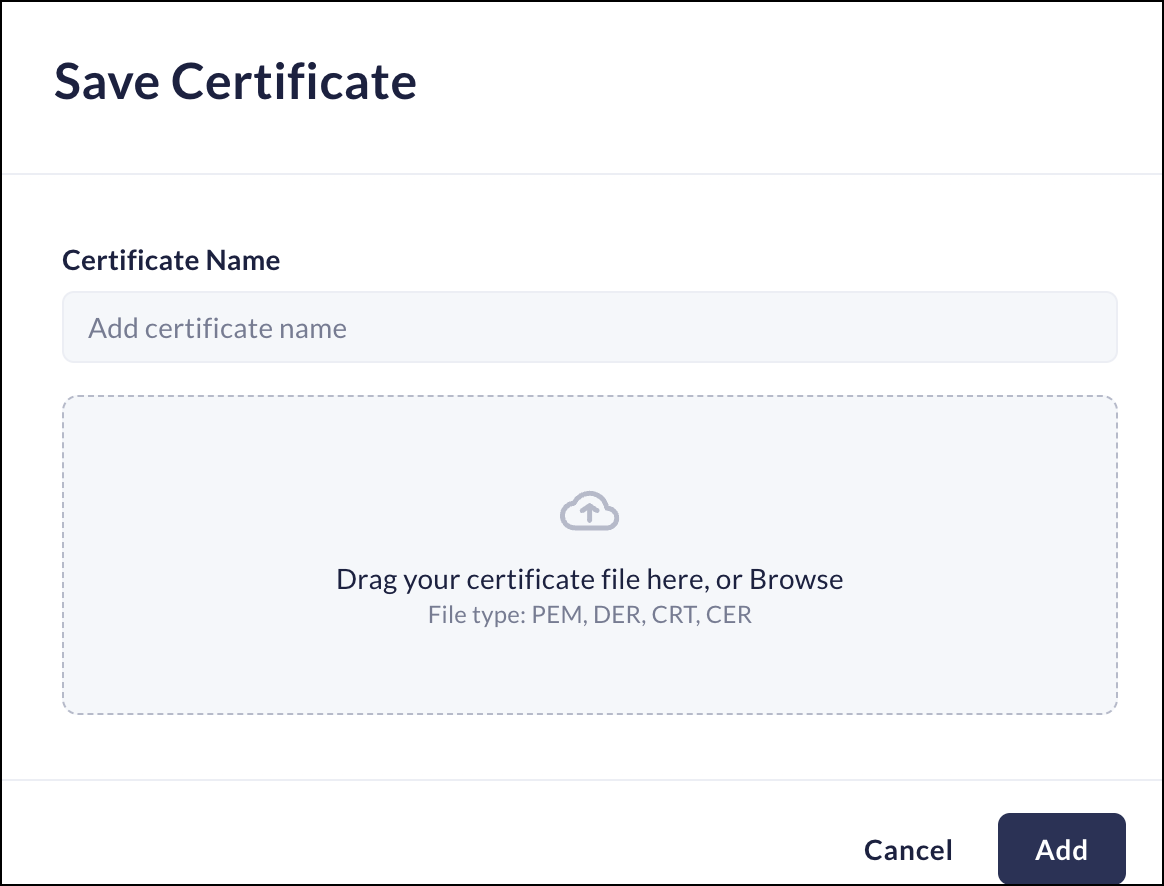
Additional trusted certificate authorities- Add customer-provided certificates not already trusted by the Prisma Browser.- Enter a name for the certificate.
- Drag or Browse a certificate in .pem, .der, .crt, or .cer formats.
![]()
Click Set.![]()
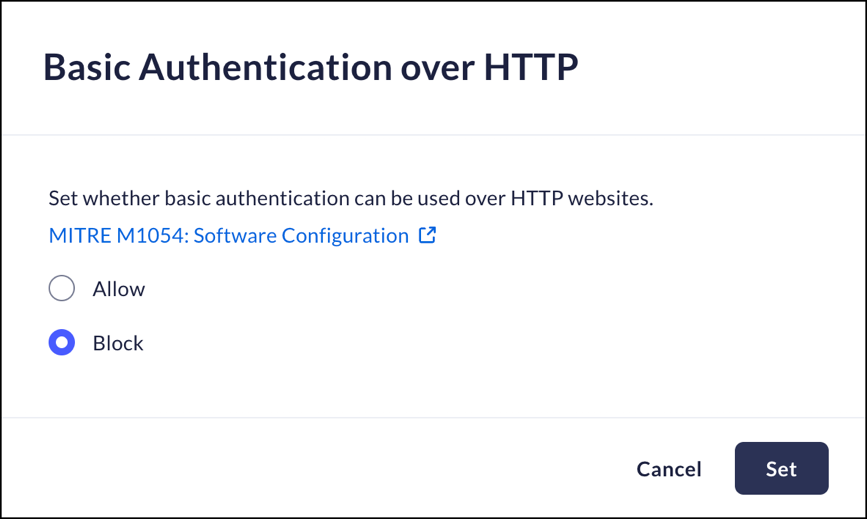
Basic Authentication over HTTP
Mobile Browser - Full supportThis feature controls whether the Prisma Browser can use Basic Authentication over HTTP websites.Since Basic Authentication sends authentication tokens in clear text, sending them over HTTP can be visible to attackers as part of a MitM attack.- From Strata Cloud Manager, select ConfigurationPrisma Browser PolicyControlsBrowser SecuritySelect Basic Authentication over HTTP.Select one of the following options:
- Allow - allow Prisma Browser to use Basic Authentication over HTTP websites.
- Block – block Prisma Browser from using Basic Authentication over HTTP websites.
Click Set.![]()
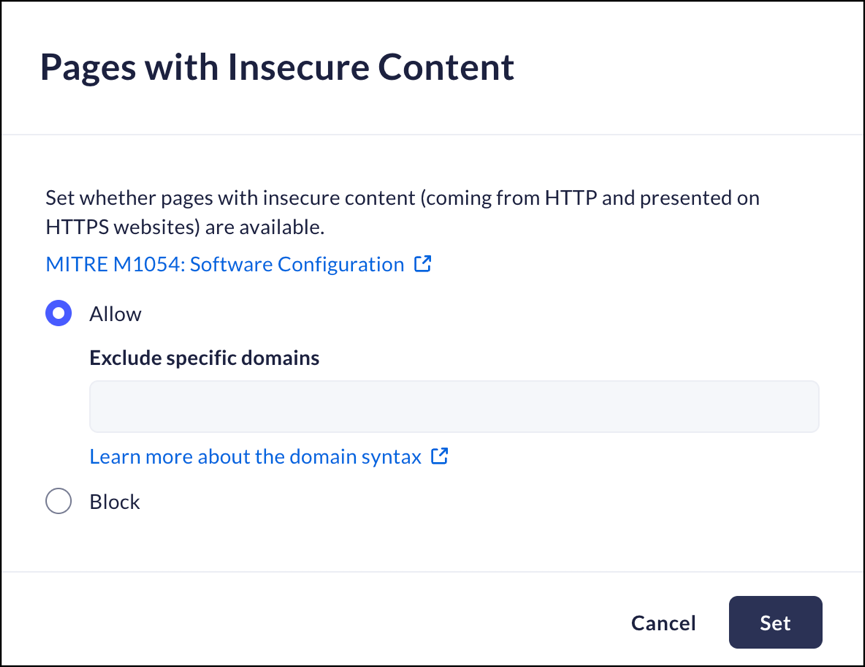
Pages with Insecure Content
Mobile Browser - No supportThis feature controls whether users can load insecure content (data located on HTTP servers) to secure websites (located on HTTPS servers).You can choose to exclude specific domains from this feature when there are specific applications that need an exception to the rule.- From Strata Cloud Manager, select ConfigurationPrisma Browser PolicyControlsBrowser SecuritySelect Pages with Insecure Content.Select one of the following options:
- Allow- Prisma Browser will allow insecure content.
- Exclude specific domains - list domains that will receive an exception to the rule.
- Block – Prisma Browser will not allow insecure content.
- Exclude specific domains - list domains that will receive an exception to the rule.
Click Set.![]()
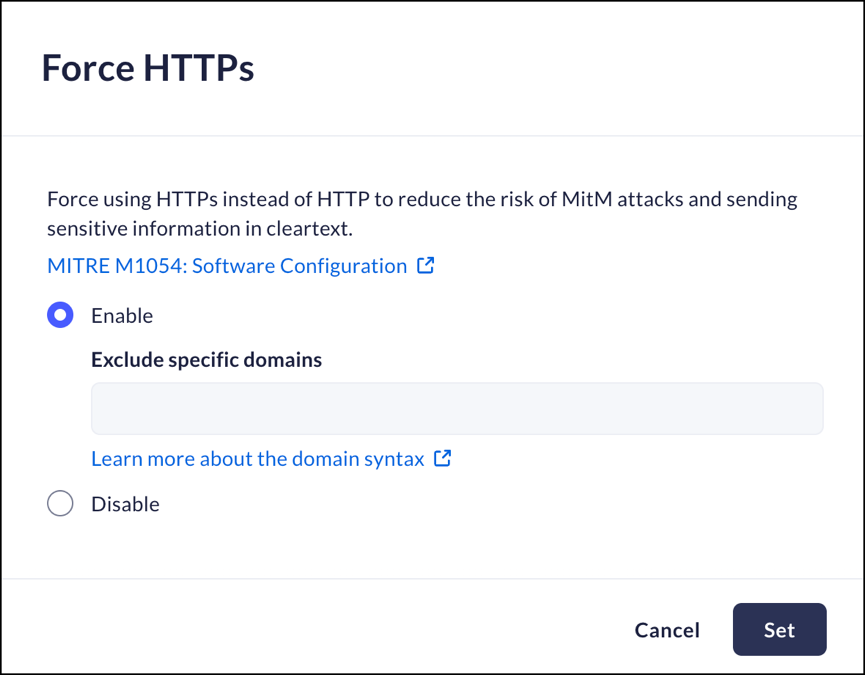
Force HTTPS
Mobile Browser - Partial supportYou can force the use of the HTTPS protocol, minimizing the risk of MitM attacks.You will be able to force HTTPS for all domains, force HTTPS but exclude certain domains, or disable forced HTTPS and work without any restrictions.- From Strata Cloud Manager, select ConfigurationPrisma Browser PolicyControlsBrowser SecuritySelect Force HTTPS.Select one of the following options:
- Enable- Prisma Browser will require use of the HTTPS protocol.You can enter specific domains that will be excluded from this requirement in the Exclude specific Domains field.Exclude specific domains is not available for the for Prisma Browser for Mobile.
- Disable – Prisma Browser will not require use of the HTTPS protocol.
Click Set.![]()
Post-Quantum Key Support
Mobile Browser - No supportThis feature manages the ability to enable or disable the use of post-quantum key agreement protocols within TLS (Transport Layer Security). Post-quantum cryptography refers to algorithms designed to be secure against quantum computer attacks, which could potentially break traditional cryptographic methods. While enabling this feature enhances security by preparing for future quantum threats, it may cause compatibility issues with existing network security products that do not yet support or recognize post-quantum algorithms. Disabling it may help avoid these conflicts, but it reduces future-proofing against emerging quantum-based vulnerabilities.- From Strata Cloud Manager, select ConfigurationPrisma Browser PolicyControlsBrowser SecuritySelect Post-Quantum Key Security.Select one of the following options:
- Enable - Permits the use of Post Quantum Key Security.Disable - Disables the use of Post Quantum Key Security.Not set - The feature is not enabled. This is the default setting.Click Set.
![]()
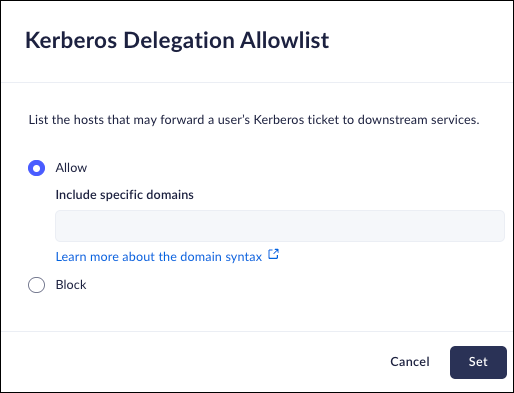
Kerberos Delegation Allowlist
Mobile Browser - No supportList the hosts that may forward a user’s Kerberos ticket to downstream services. When this is enabled, the Kerberos ticket is used in place of your SSO so that back-end services are easier yo use.- From Strata Cloud Manager, select ConfigurationPrisma Browser PolicyControlsBrowser SecuritySelect Kerberos Delegation Allowlist .Select one of the following options:
- Enable - Activates real-time host scanning of the selected hosts. For information on specifying hosts in the correct pattern, refer to this page. of t.Disable - Disables the use of the real-time host scanning.Click Set.
![]()
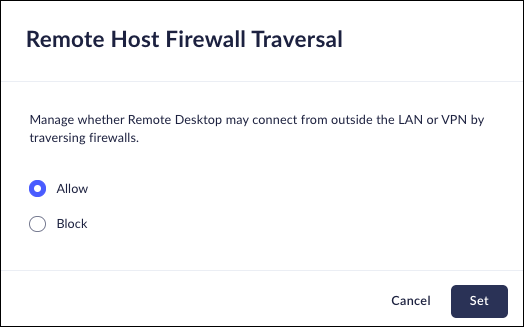
Remote Host Firewall Traversal.
Mobile Browser - No supportThis policy controls whether the Remote Desktop can bypass firewalls. When enabled, users can connect remotely from any network. When disabled, access is limited to the same local network or VPN, enhancing security by restricting remote access.- From Strata Cloud Manager, select ConfigurationPrisma Browser PolicyControlsBrowser SecuritySelect Remote Host Firewall Traversal .Select one of the following options:
- Allow - Allow users to connect remotely from any network.Block - Remote connection is only permitted from the same local network or VPN.Click Set.
![]()
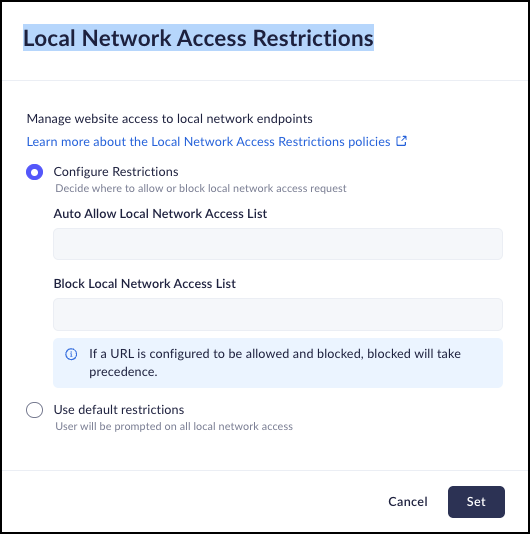
Local Network Access Restrictions
Mobile Browser - No supportThe local network access permission prompt and restrictions feature is targeted to affect browsers versioned 146.xx and above.Local Network Access Restrictions is a security control that allows you to govern how websites interact with devices located on your users local networks. This manages the underlying LocalNetworkAccessRestrictionsEnabled, LocalNetworkAccessAllowedForUrls, LocalNetworkAccessBlockedForUrls policies for Chromium-based browsers.The default value for desktop devices is 'Use default restrictions' meaning, a user will be prompted to manage all local network access.- From Strata Cloud Manager, select ConfigurationPrisma Browser PolicyProfilesBrowser SecuritySelect Local Network Access Restrictions .Select one of the following options:
- Configure Restrictions - Decide where to allow or block local network access requests. You will then need to enter the Auto Allow Local Network Access List or the Block Local Network Access List.If a Local Network is configured to be blocked and allowed, the block takes precedence.Use default restrictions - Users will be prompted for all local network access.Click Set.
![]()