Prisma Access Browser
Configure Prisma Access Browser Browser Security Controls
Table of Contents
Expand All
|
Collapse All
Prisma Access Browser Docs
Configure Prisma Access Browser Browser Security Controls
Configure browser security controls for Prisma Access Secure Enterprise Browser (Prisma Access Browser).
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
You can configure the controls in the following ways:
- When you're creating a new browser security rule, you can set the controls in the Browser Security controls page.
- You can edit an existing rule.
- You can create a policy profile and attach it to a rule.
- You can select it from Strata Cloud Manager ManageConfigurationPrisma Access Browser PolicyProfilesBrowser Security.
The following topics only display one way.
Browser Security – Browser Session
Browser Lock
Mobile Browser - Partial support
The Prisma Access Browser includes a lock screen feature enabling
you to apply an extra layer of security to your browser. If the Browser Lock
is enabled, users will need to enter a PIN code or a Passkey to unlock the
browser upon first use, or after a configurable idle time has elapsed. This
feature is especially useful for Unmanaged devices. For Unmanaged devices,
you are not able to configure a device lock. This feature allows you to
protect the enterprise data by configuring a lock on the browser.
This PIN code is browser-dependent and is not related to the SSO password.
The Prisma Access Mobile Browser relies on
the native device screen lock, and not the lock that is included in the
PrismaPrisma Access Browser tool. The PIN length and Maximum Failed
Attempts will be ignored.
The Authentication method is configured in Browser Security ->
Authentication Factor.
- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Browser Lock.Select one of the following options:
- Enable - enable the Browser lock.
- Select the Idle time - 1 minute to 12
hours (or never). This is the time that must elapse
before the Browser Lock screen appears.Idle time refers to the time tat the device is idle, not the browser; which would be sitting in the background.For mobile browsers, this means that the browser moves to the background. After 1 minute, the OS browser lock tool is used to force a reauthorization of the browser.
- Select the Idle time - 1 minute to 12
hours (or never). This is the time that must elapse
before the Browser Lock screen appears.
- Disable - the Prisma Access Browser will disable malicious file protection.
Click Set.![]()
Flush Browser Data
Mobile Browser - Partial supportThis policy creates temporary browser sessions. This means that browser data will be cleared upon close, or after a configured time period.The Prisma Access Mobile Browser supports flushing data when the browser closes. Configuring periodic flushing on the mobile browser will have no impact.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Flush Browser Data.Select one of the following options:
- Enable - the Prisma Access Browser flush the browser data.
- Select the attributes to clear:
- Browsing history
- Download history
- Cookies and other site data
- Cached images and files
- Passwords and Passkeys
- Autofill
- Site settings.
- Host app data
- Select the trigger for the browser flush action:
- Browser close - the data will be flushed when the browser is closed.
- Time period - the data will be flushed after the configured time elapsed. If this option is selected, you can set the flush time from 1-24 hours.
- Disable – disable the Browser flush feature.
Click Set.i![]()
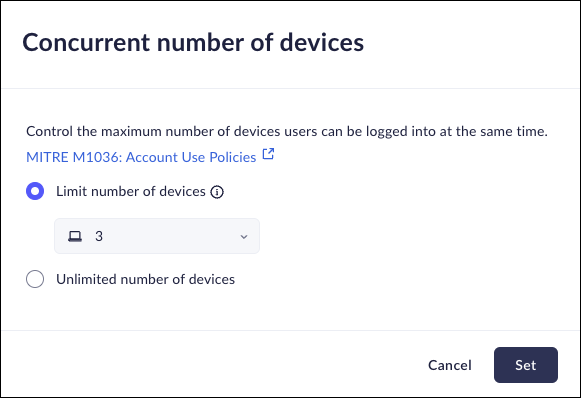
Concurrent Browser Sessions
Mobile Browser - Partial supportThis policy allows you to determine the maximum number of devices that a user can have logged into the browser at one time. This includes both the Prisma Access Browser and the Prisma Access Mobile Browser.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Concurrent number of devices.Select one of the following options:
- Limit number of devices - You will be able to limit the number of browser session concurrently. You can set the maximum to between 1 and 5 concurrent sessions per user.
- Unlimited number of devices – There is no limit to the number of concurrent sessions that users can have.
Click Set.![]()
Browser Security – Browser Hardening
Cast
Mobile Browser - No supportThis feature controls the ability to screencast a tab or the desktop via the Prisma Access Browser.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Cast.Select Allow to permit casting or Block to deny casting.Click Set.Restart the browser to apply this feature.
![]()
Developer Tools
Mobile Browser - No supportThis feature actively controls users' ability to open Developer Tools or manually load browser extensions in "Developer Mode" via "load unpack". It can also assist with preventing users from running unauthorized JavaScript code in the Developer Tools console.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Developer Tools.Select Allow to permit the Developer options, or Block to deny their use.Click Set.Restart the browser to apply this feature.
![]()
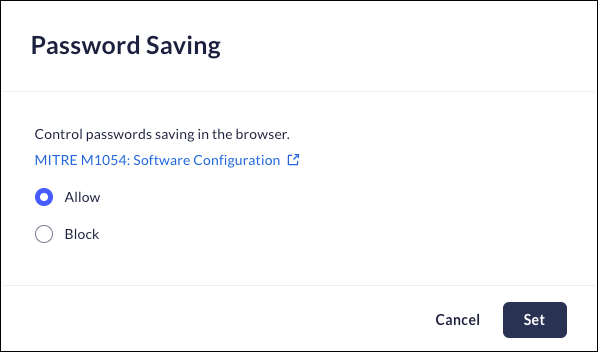
Password Saving
This feature determines whether the browser will be able to save passwords for websites.Mobile Browser - Full support- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Password Saving.Select one of the following options:
- Allow - Users will be able to save passwords in the browser.
- Block - Users will be restricted to save passwords in the browser.
Click Set.![]()
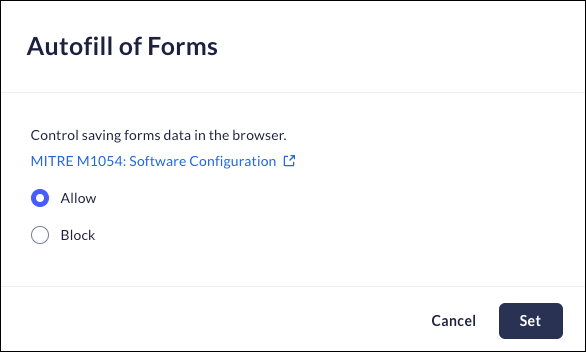
Autofill of Forms
Mobile Browser - No supportThis feature determines whether or not the browser will store information to autofill forms.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Autofill of Forms.Select one of the following options:
- Allow – The browser will save information to autofill forms in the future.
- Block – The browser will not save form information to be filled automatically in the future.
Click Set.![]()
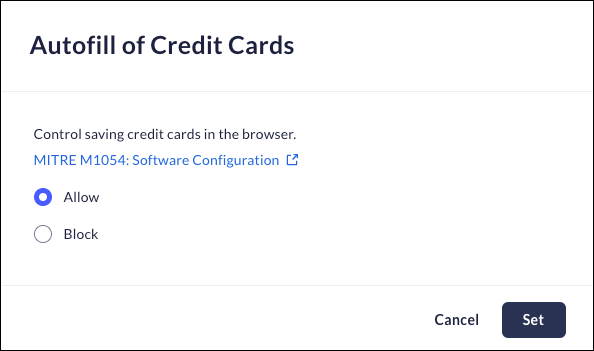
Autofill of Credit Cards
Mobile Browser - No supportThis feature determines whether or not the browser will allow users to store credit card information.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Autofill of Credit Cards.Select one of the following options:
- Allow – Prisma Access Browser will be able to save credit card details.
- Block – Prisma Access Browser will be restricted from saving credit card details for future use.
Click Set.![]()
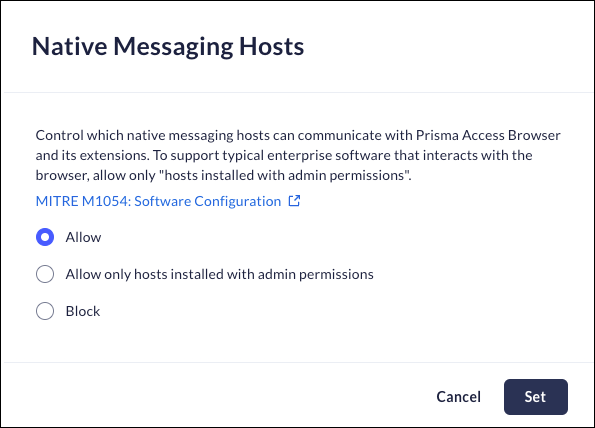
Native Messaging Hosts
Mobile Browser - No supportNative Messaging Hosts allows the software installed on the device to communicate with Prisma Access Browser and its installed extensions, and vice versa. Enterprise software that interacts with the browser typically requires you to select "Allow only hosts installed with admin permissions."- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Native Messaging Hosts.Select one of the following options:
- Allow – the browser will be able to communicate with Native Messaging Hosts.
- Allow only hosts installed with admin permissions
- Block – the browser’s use of Native Messaging Hosts will be restricted.
Click Set.![]()
JavaScript Running from Omnibox
This feature determines whether or not users will be able to run JavaScript code from the browser omnibox (Address Bar). Users may exploit this functionality to manipulate web pages using JavaScript.Mobile Browser - No support- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect JavaScript Running from Onmibox.Select one of the following options:
- Allow – the Prisma Access Browser will allow JavaScript to run from omnibox..
- Block – the Prisma Access Browser will restrict JavaScript from running from omnibox.
Click Set.![]()
Keylogging Protection
Mobile Browser - No supportThis policy allows you to determine if keylogging protection will be enabled. Keylogging tools can monitor and report a user's actions as they interact with the computer. As the name suggests, a keylogger records what the user types, and reports the information back to whoever installed the logger.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Keylogging Protection.Select one of the following options:
- Allow – Keyloggers will be prevented from listening to keystrokes typed on Prisma Access Browsers.
- Block – Keylogging protection is turned off.
Click Set.![]()
Popups
Mobile Browser - Support for iOS only.With this feature, you can control the display of popups in the browser.The popups can be allowed, allowed with exceptions, blocked, or blocked with exceptions.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Popups.Select one of the following options:
- Allow – Popups will be permitted in the browser. You can specifically exclude domains from being allowed. This will block popups from those domains only.
- Block – Popups will be blocked. You can specifically exclude domains from being blocked. This will allow popups from those domains only.
Click Set.![]()
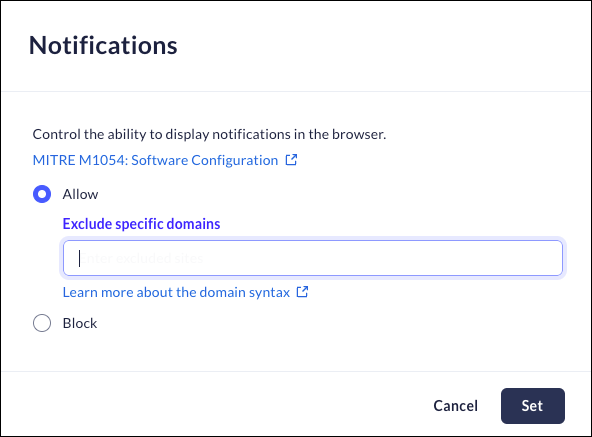
Notifications
Mobile Browser - No supportYou can use this feature to control notifications being displayed within the browser. The notifications can be allowed, allowed with exceptions, blocked, or blocked with exceptions.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Notifications.Select one of the following options:
- Allow - Notifications will be permitted in the browser. You can specifically exclude specific domains. This will block notifications from these domains.
- Block - Notifications will be blocked. You can specifically exclude specific domains from the rule. This will allow popups from those domains only.
Click Set.![]()
Authentication Factor
Mobile Browser - No supportYou can use this feature to configure the settings for the Authentications methods. When you need to enable the Browser Lock or step-up MFA across the different data controls, this control is needed to select the options for the lock.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Authentication Factor.Select one of the following options:
- PIN Code – configure the size of the code (between 4-6 digits) and the number of attempts that can be made before the account will be locked out.
- Passkey – select whether the passkey will be an Internal or External authenticator.
Click Set.![]()
Open Links in External Apps
Mobile Browser - Mobile onlyWhile most of the time we want to keep the Prisma Access Browser as a secure bubble, that all work is done only in the browser. This is not possible for a few reasons. First of all, some applications can't be opened in a browser, such as Zoom, Teams, Slack, among others. Blocking these apps would result in a terrible user experience. Second, most mobile devices are BYOD. Third, Some URLs can only be opened in a native app.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Open Links in External Apps.Select one of the following options:
- Always – External apps will always open in native applications.
- Only for specific apps – Only selected links will open in external apps. The following apps can be selected:
- MS Teams
- MS Outlook
- MS OneDrive Business/ SharePoint Online
- Slack
- Zoom
- Salesforce
- Okta
- Gmail
- Google Calendar
- Google Workspace (Sheets, Docs, Slides)
- Google Drive.
- \Never - External apps will never open in native applications.
- Users decide when to open links in native apps - End users will be able to decide when to open links in Prisma Access Browser and when to use a native app.
Click Save.Browser Security – Network Protection
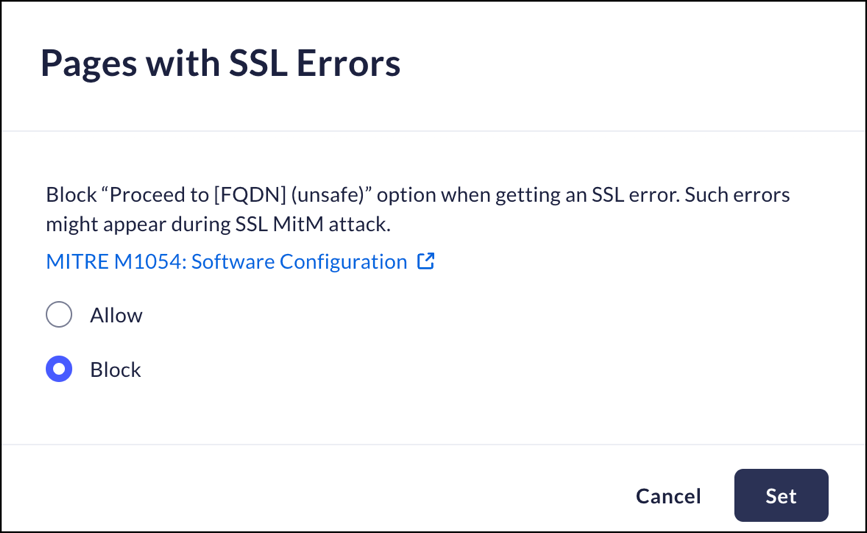
Pages with SSL Errors
Mobile Browser - Full supportThis feature manages how the Prisma Access Browser will react when it encounters a page with an SSL error. In general, most browsers ask for permission to "Proceed to [FQDN] (unsafe)".Since SSL errors can occur during an SSL MitM attack, you can use this control to block the "Proceed..." functionality.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Pages with SSL Errors.Select one of the following options:
- Allow - Allow users to bypass the blocking page when an SSL issue is identified.
- Block – the Prisma Access Browser will block the "Proceed..." option when an SSL issue is identified.
Click Set.![]()
DNS-Over-HTTPS
Mobile Browser - No supportThis feature manages the DNS resolution over the HTTPS protocol. It is used for encrypting requests.This assists in preventing MitM attacks.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect DNS-Over-HTTPS.Select one of the following options:
- Enable - Enter the following information:Upon DNS over HTTPS resolve failure:
- Fail-open: Resolve using plain DNS.
- Fail-close: Do not resolve.
- Enter the DNS-over-HTTPS resolver's URL.
- Disable – Prisma Access Browser will not enable DNS over HTTPS resolution.
Click Set.![]()
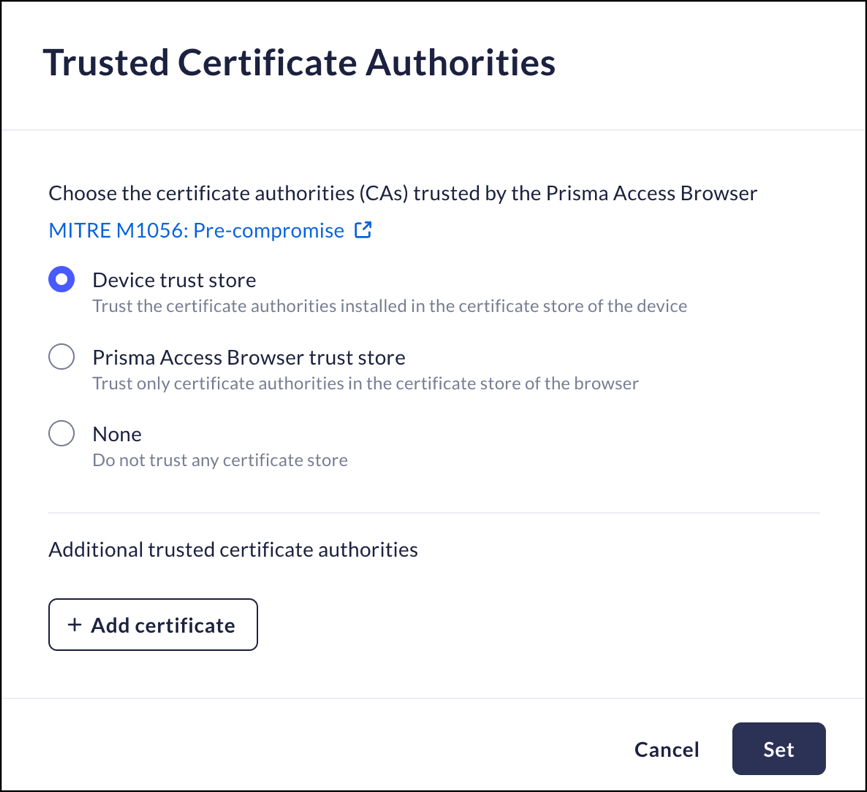
Trusted Certificate Authorities
Mobile Browser - Partial supportThis feature manages how the Prisma Access Browser will react when it encounters a page with an SSL error. In general, most browsers ask for permission to "Proceed to [FQDN] (unsafe)".Since SSL errors can occur during an SSL MitM attack, you can use this control to block the "Proceed..." functionality.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Trusted Certificate Authorities.Select the certificate authorities that are to be trusted by the Prisma Access Browser (this limits the trust to certificates that are already trusted):
- Device trust store - Trust the certificate authorities installed in the device's certificate store.
- Prisma Access Browser trust store - Trust only certificate authorities that are trusted by Palo Alto Networks, and ignores certificates installed in the Device trust store.
- None - Do not trust certificates in any trust store.
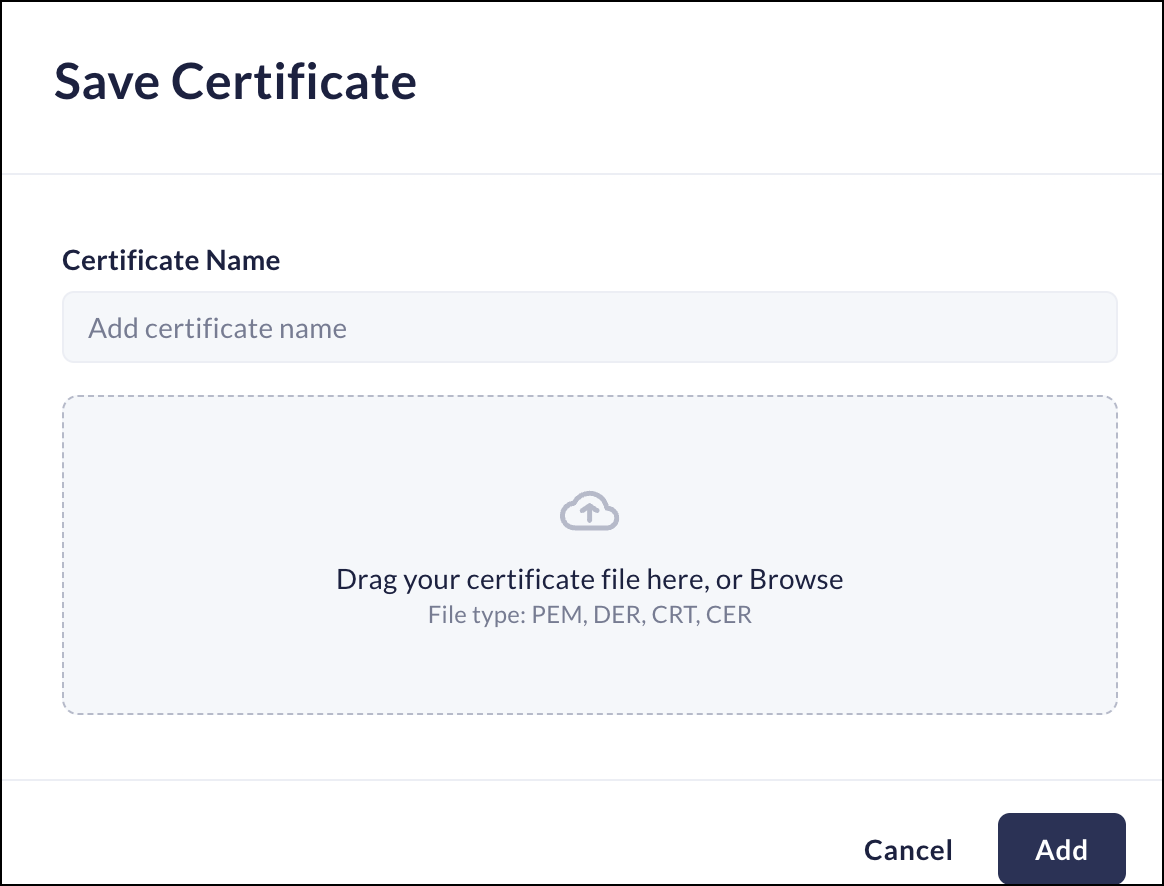
Additional trusted certificate authorities- Add customer-provided certificates not already trusted by the Prisma Access Browser..- Enter a name for the certificate.
- Drag or Browse a certificate in .pem, .der, .crt, or .cer formats.
![]()
Click Set.![]()
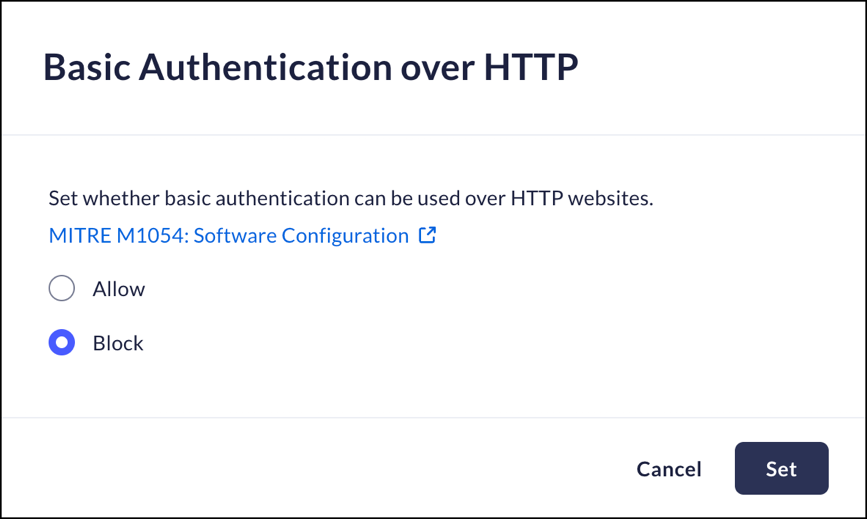
Basic Authentication over HTTP
Mobile Browser - No supportThis feature controls whether the Prisma Access Browser can use Basic Authentication over HTTP websites.Since Basic Authentication sends authentication tokens in clear text, sending them over HTTP can be visible to attackers as part of a MitM attack.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Basic Authentication over HTTP.Select one of the following options:
- Allow - allow Prisma Access Browser to use Basic Authentication over HTTP websites.
- Block – block Prisma Access Browser from using Basic Authentication over HTTP websites.
Click Set.![]()
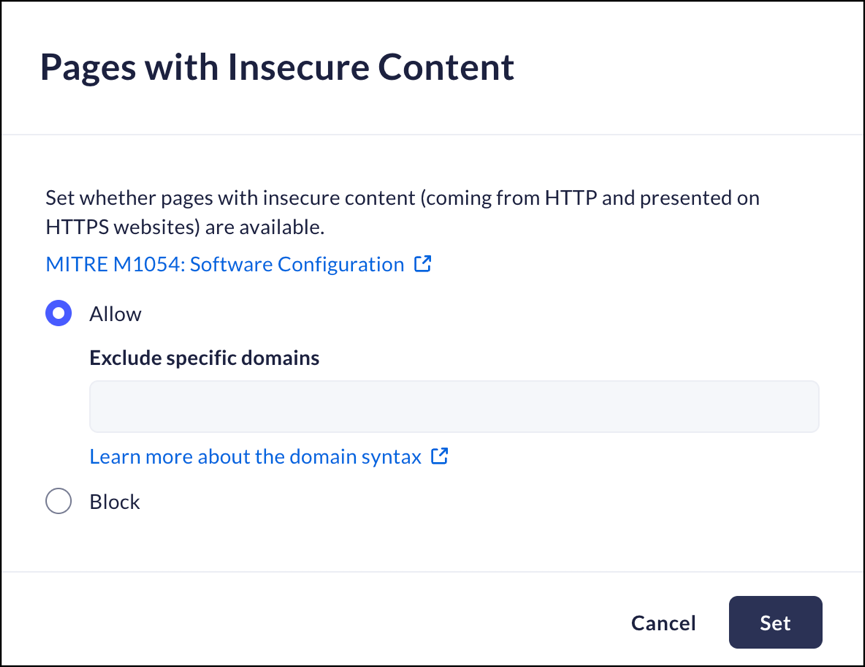
Pages with Insecure Content
Mobile Browser - No supportThis feature controls whether users can load insecure content (data located on HTTP servers) to secure websites (located on HTTPS servers).You can choose to exclude specific domains from this feature when there are specific applications that need an exception to the rule.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Pages with Insecure Content.Select one of the following options:
- Allow- Prisma Access Browser will allow insecure content.
- Exclude specific domains - list domains that will receive an exception to the rule.
- Block – Prisma Access Browser will not allow insecure content.
- Exclude specific domains - list domains that will receive an exception to the rule.
Click Set.![]()
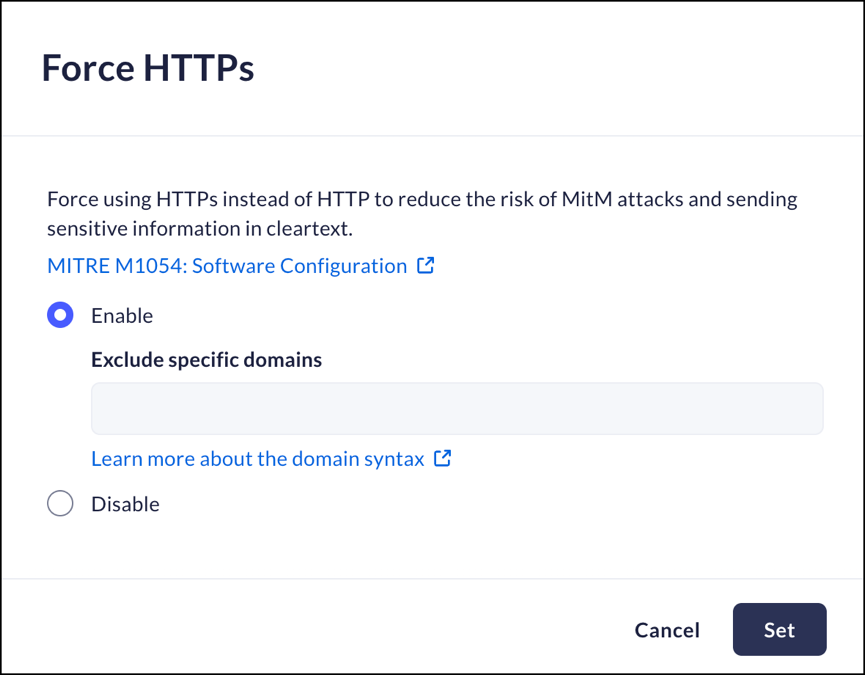
Force HTTPS
Mobile Browser - No supportYou can force the use of the HTTPS protocol, minimizing the risk of MitM attacks.You will be able to force HTTPS for all domains, force HTTPS but exclude certain domains, or disable forced HTTPS and work without any restrictions.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Force HTTPS.Select one of the following options:
- Enable- Prisma Access Browser will require use of the HTTPS protocol. You can select specific domains that will be excluded - meaning that these domains will not require the HTTPS protocol.
- Disable – Prisma Access Browser will not require use of the HTTPS protocol.
Click Set.![]()
Post-Quantum Key Support
Mobile Browser - No supportThis feature manages the ability to enable or disable the use of post-quantum key agreement protocols within TLS (Transport Layer Security). Post-quantum cryptography refers to algorithms designed to be secure against quantum computer attacks, which could potentially break traditional cryptographic methods. While enabling this feature enhances security by preparing for future quantum threats, it may cause compatibility issues with existing network security products that do not yet support or recognize post-quantum algorithms. Disabling it may help avoid these conflicts, but it reduces future-proofing against emerging quantum-based vulnerabilities.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Post-Quantum Key Security.Select Enable to permit the use of Post-Quantum Key Security, or Block to deny the use.Click Set.
![]()
Browser Security – Extensions
Allowed or Blocked Extensions
Mobile Browser - No supportAllowed or Blocked Extensions give you control over which extensions are permitted in the Prisma Access Browser.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Allowed or Blocked Extensions.Select one of the following options:
- Allow all - allow all extensions.
- Block specific extensions - you can select specific extensions to block. The extension must be identified by its ID.
- Allow only specific extensions - you can select specific extensions to permit. The extension must be identified by its ID.
- Block all - block all extensions.
Click Set.![]()
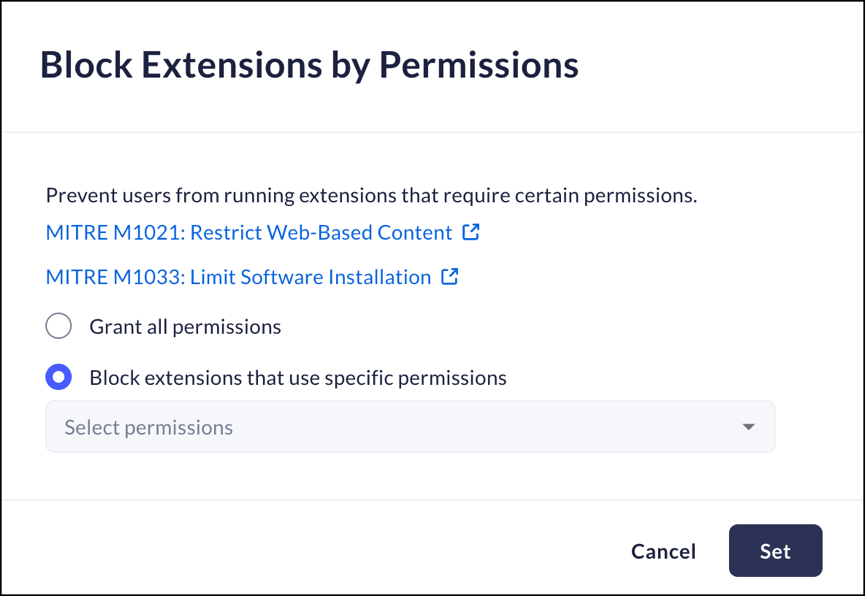
Block Extensions by Permission
Mobile Browser - No supportThis control allows you to block extensions based on their required permissions.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Block Extensions by Permission.Select one of the following options:
- Grant all permissions - permit running extensions without regard to their required permissions.
- Block extensions that use specific permissions - block that requires specific permissions. Permissions that were not selected will be permitted. You can select as many permissions as required.
Click Set.![]()
Hide Sensitive Data from Extensions
Mobile Browser - No supportThis control allows you to hide sensitive data - any data that can compromise user information and be used for illicit logins - from extensions.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Hide Sensitive Data from Extensions.Select one of the following options:
- Enable - enable hiding sensitive data from extensions.
- Disable - do not hide sensitive data from extensions.
Click Set.![]()
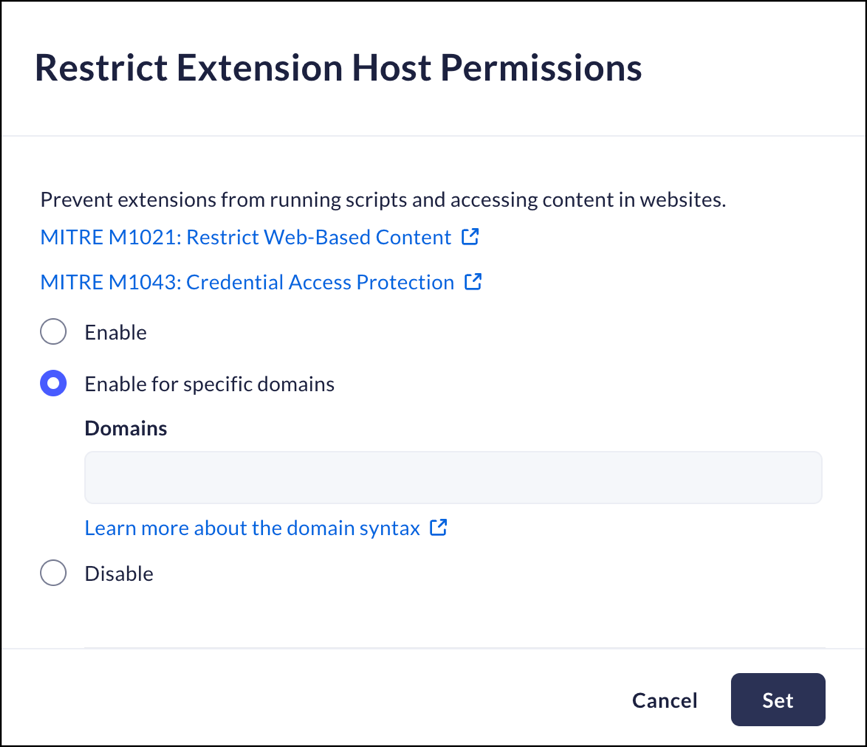
Restrict Extension Host Permissions
Mobile Browser - No supportThis control allows you to hide sensitive data - any data that can compromise user information and be used for illicit logins - from extensions.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Restrict Extension Host Permissions.Select one of the following options:
- Enable - prevent extensions from running scripts and accessing content.
- Enable for specific domains - prevent extensions from running scripts and accessing content from specific domains. Click here to see information regarding domain syntax.
- Disable - do not prevent extensions from running scripts and accessing content.
Click Set.![]()
Browser Security – Internet Explorer Compatibility Mode
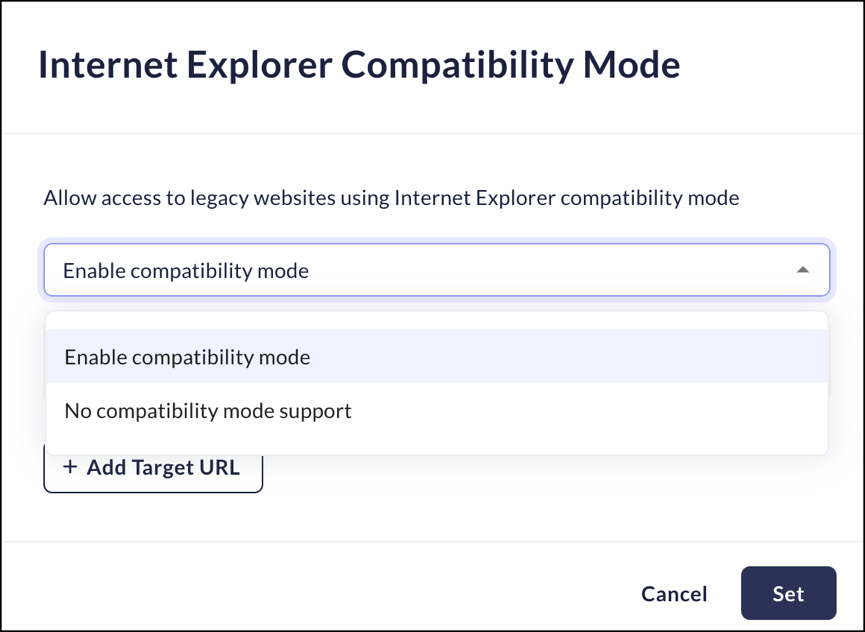
Internet Explorer Compatibility Mode
Mobile Browser - No supportMicrosoft has announced end-of-support dates for different versions of IE. For more information, refer to Microsoft's Lifecycle FAQ.Organizations may require compatibility with Internet Explorer, as they are running internal legacy websites.You can select these particular sites and allow users to access them in the Prisma Access Browser using Internet Explorer Compatibility Mode. This will render the application or site as if it were being accessed via Internet Explorer.The Prisma Access Browser Internet Explorer ~Compatibility Mode is compatible with the Internet Explorer browser version 11.Click here for more information regarding entering URLs.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Internet Explorer Compatibility Mode.Select one of the following options:
- Enable compatibility mode - You need to add the target URLs that need Internet Explorer Compatibility.
- No compatibility mode support - Users will not be able to use sites that require IE Compatibility.
Click Set.![]()
Browser Security – Printers
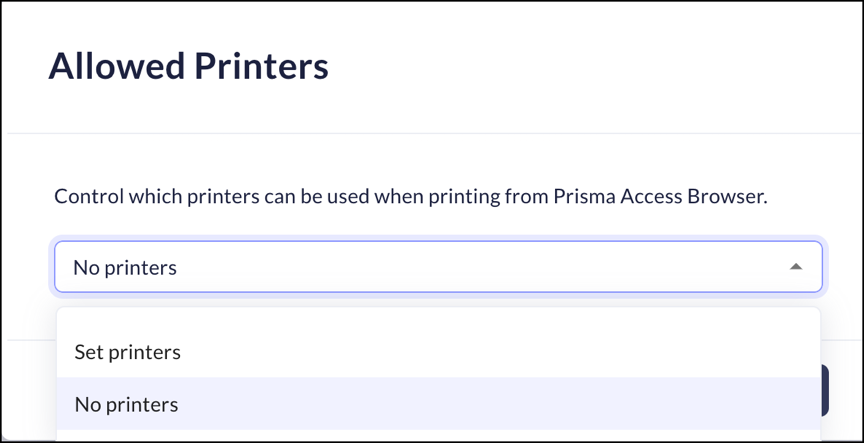
Allowed Printers
Mobile Browser - No supportThe Prisma Access Browser allows you to configure particular printers for users who need to print from the browser. This provides an additional level of security, where end-users will only be able to print to permitted devices, such as printers in the office.This feature does not preclude users from printing from other devices when using applications not managed through the Prisma Access Browser.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Allowed Printers.Select one of the following options:
- No printers – end-users cannot print from the browser.
- Set printers - Click Add Printer to enter the network location of each printer that end users will be able to select when printing is required.
Click Set.![]()
Browser Security – Privacy
Third-party Cookies
Mobile Browser - No supportThe Prisma Access Browser allows you to configure particular printers for users who need to print from the browser. This provides an additional level of security, where end-users will only be able to print to permitted devices, such as printers in the office.This feature does not preclude users from printing from other devices when using applications not managed through the Prisma Access Browser.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Third-party Cookies.Select one of the following options:
- Allow - Third-party elements can set cookies.
- Block - Third-party elements cannot set cookies.
Click Set.![]()
Browser History
Mobile Browser - No supportThe Prisma Access Browser allows you manage the ability to delete the browser history.- From Strata Cloud Manager, select ManageConfigurationPrisma Access Browser PolicyProfilesBrowser SecuritySelect Browser History.Select one of the following options:
- Enable - browser history is saved.
- Disable - browser history is not saved, and tab syncing is disabled. This setting cannot be changed by users.
- Block Deletion - browser history and download history cannot be deleted.
Click Set.