Prisma Browser
Cloud Storage Integrations
Table of Contents
Expand All
|
Collapse All
Prisma Browser Docs
Cloud Storage Integrations
Describes how to integrate Microsoft One drive and Google Drive
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Refer to the cloud providers for their specific requirements.
|
The Save to Cloud capability enables you to block direct file downloads to
user endpoints and instead redirect downloads to organization-managed cloud storage,
such as Microsoft OneDrive or Google Drive. This approach not only aligns with data
protection policy rules but also improves user productivity by offering smooth
access to files across devices.
Select between Cloud Storage and Encrypted Downloads
This section provides the guidance for selecting the appropriate method - cloud
storage or encrypted downloads - for securely distributing and accessing files,
based on specific operational and security requirements,
Cloud storage and encrypted downloads both support secure file distribution, but
each serves different use cases. The appropriate choice depends on many
different factors.
RECOMMENDED USE CASES
Use Cloud Storage when:
- Frequent Access Is Required — Multiple users or devices need regular access to the files.
- Real-time Collaboration Is Needed — Multiple users must view, edit, or comment on files simultaneously.
- Version Control Is Required — You need to track changes and maintain a history of file versions.
- Centralized Access Control Is Important — You can manage permissions and user access directly within the cloud environment.
- Mobile or Remote Access Is Necessary — Users require access from multiple locations or devices, including mobile endpoints.
Use Encrypted Downloads when:
- One-Time or Limited Access Is Sufficient — Files are intended for single-use or short-term local access.
- High Security is a Priority — Files contain sensitive information that must be stored locally with encryption. The files can only be downloaded using the browser.
- Offline Access Is Required — Users need to access files in environments without reliable internet connectivity.
- Collaboration Isn’t Needed — Files don’t require editing or sharing across users or devices.
- Regulatory Compliance Requires Local Storage — Certain policy rules or legal frameworks mandate storage outside of cloud platforms.
Encrypted downloads allow you to determine
where the files will exist locally, and can only be opened using the Prisma Browser. Save to Cloud allow you to move the files to any
location and is not encrypted.
You need
to configure the Cloud Storage Integrations before you select the cloud
storage providers.
The following cloud providers can be configured:
Cloud Provider - Microsoft OneDrive
This document contains the directions for integrating Microsoft OneDrive as the cloud
provider
Microsoft OneDrive Prerequisites
These are the prerequisites for configuring Microsoft OneDrive as your cloud
provider:
- Global Administrator access in Azure Active Directory (AD)
End users require a valid Microsoft 365 license:
- Microsoft 365 Business Basic /Standard / Premium
- Microsoft 365 Apps for Business
- Microsoft 365 E3 / E5
Configure Microsoft OneDrive as the Cloud Provider
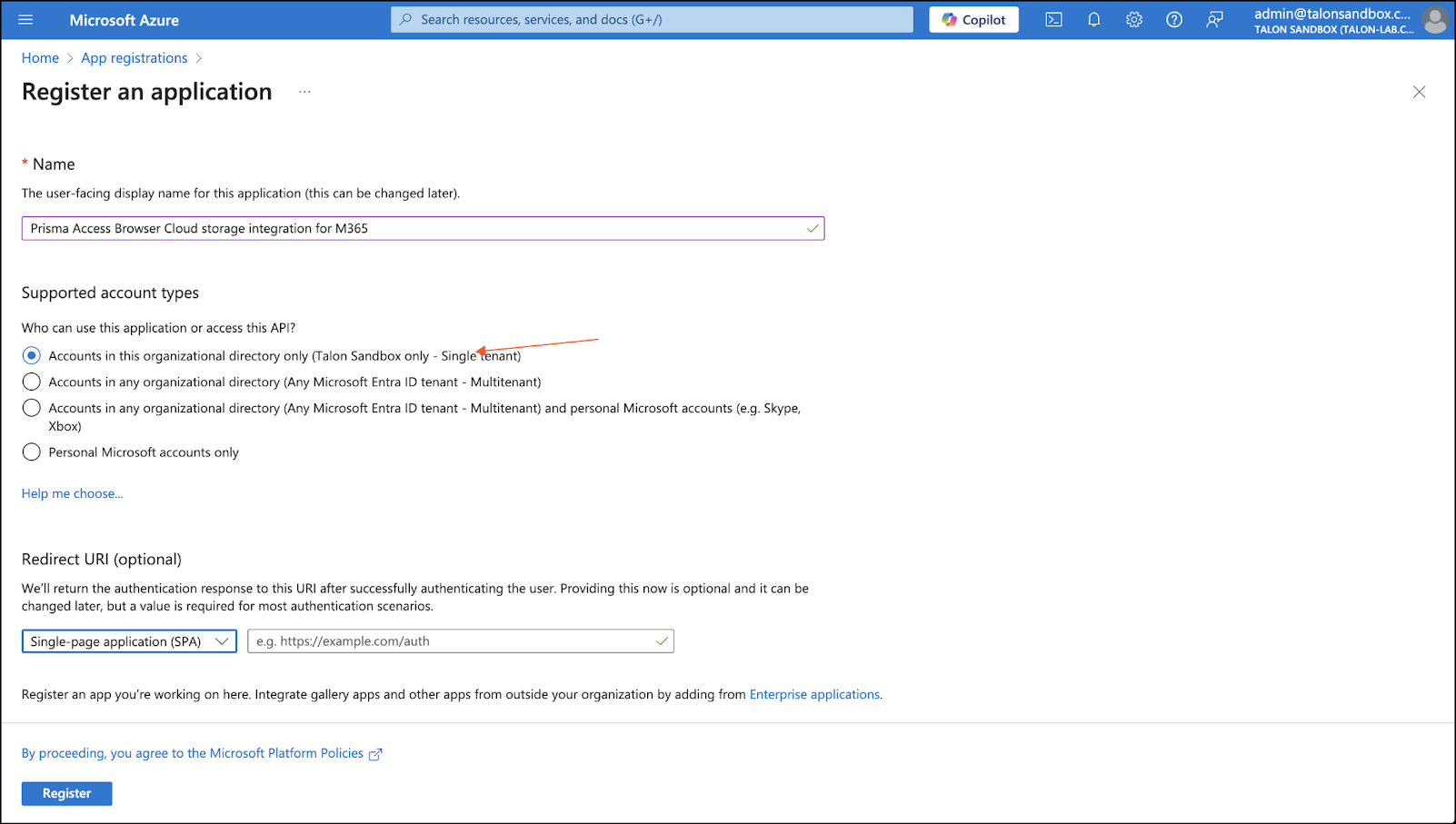
- Register a new app in Azure.
- Sign in to the Azure Portal.Go to Azure Active Directory → App registrations → + New registration.Enter a descriptive name (for example, Prisma Browser Cloud Storage for M365)Choose Single tenant (Accounts in this organizational directory only).Under Redirect URI, select Single-page application (SPA) and use this URI: https://gdhaibkimkeghllnpodfpoamchapggea.chromiumapp.org/Click Register.
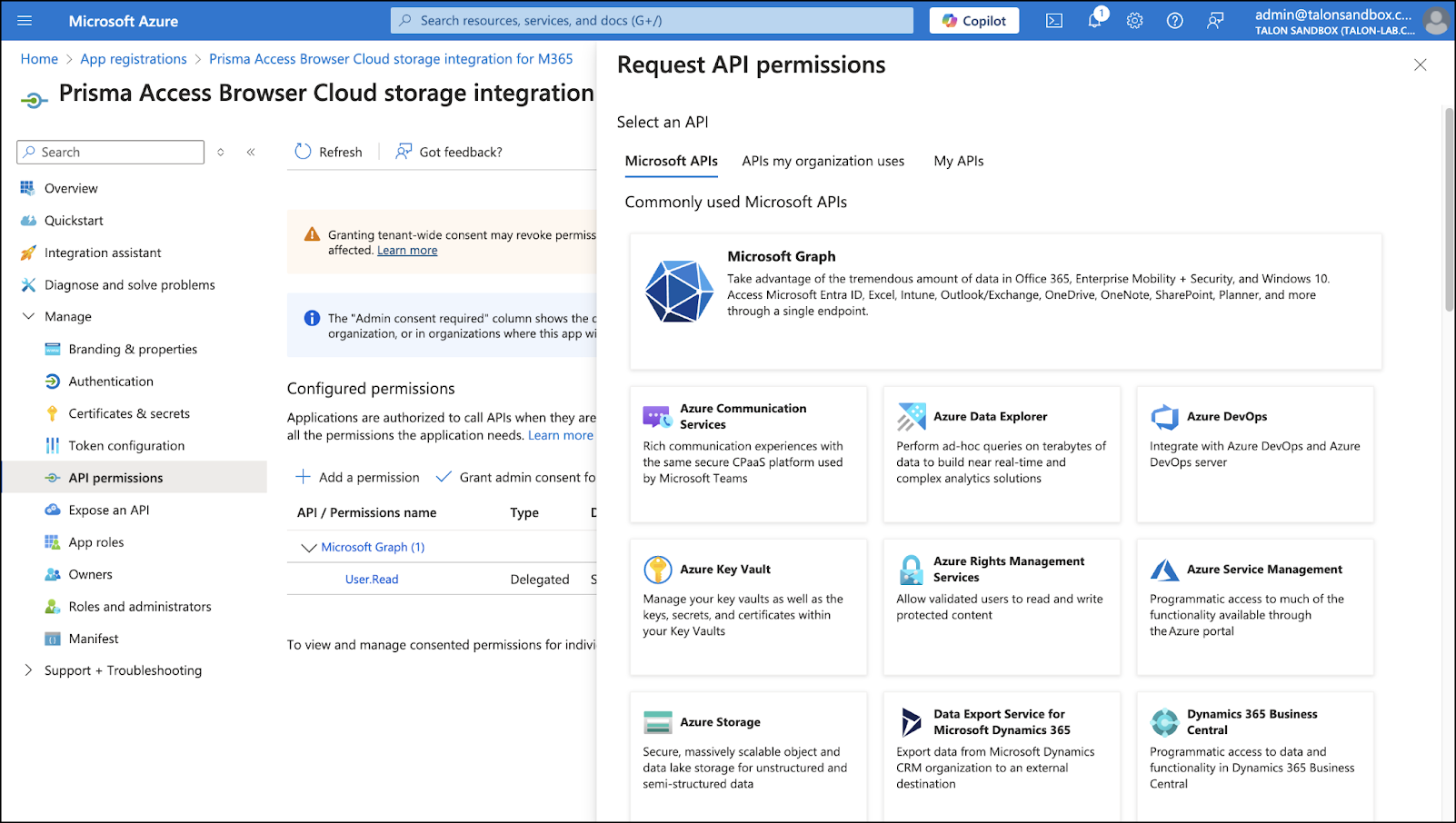
![]() Add Permissions to the New App.
Add Permissions to the New App.- Open the new app → App permissions → + Add a permission.Choose Microsoft Graph.Add the following Application permissions:
- Application.Read.All
- DelegatedPermissionGrant.Read.All
Click +Add a permission → Microsoft Graph → Delegated permissions.Add the following permission:- Files.ReadWrite.All
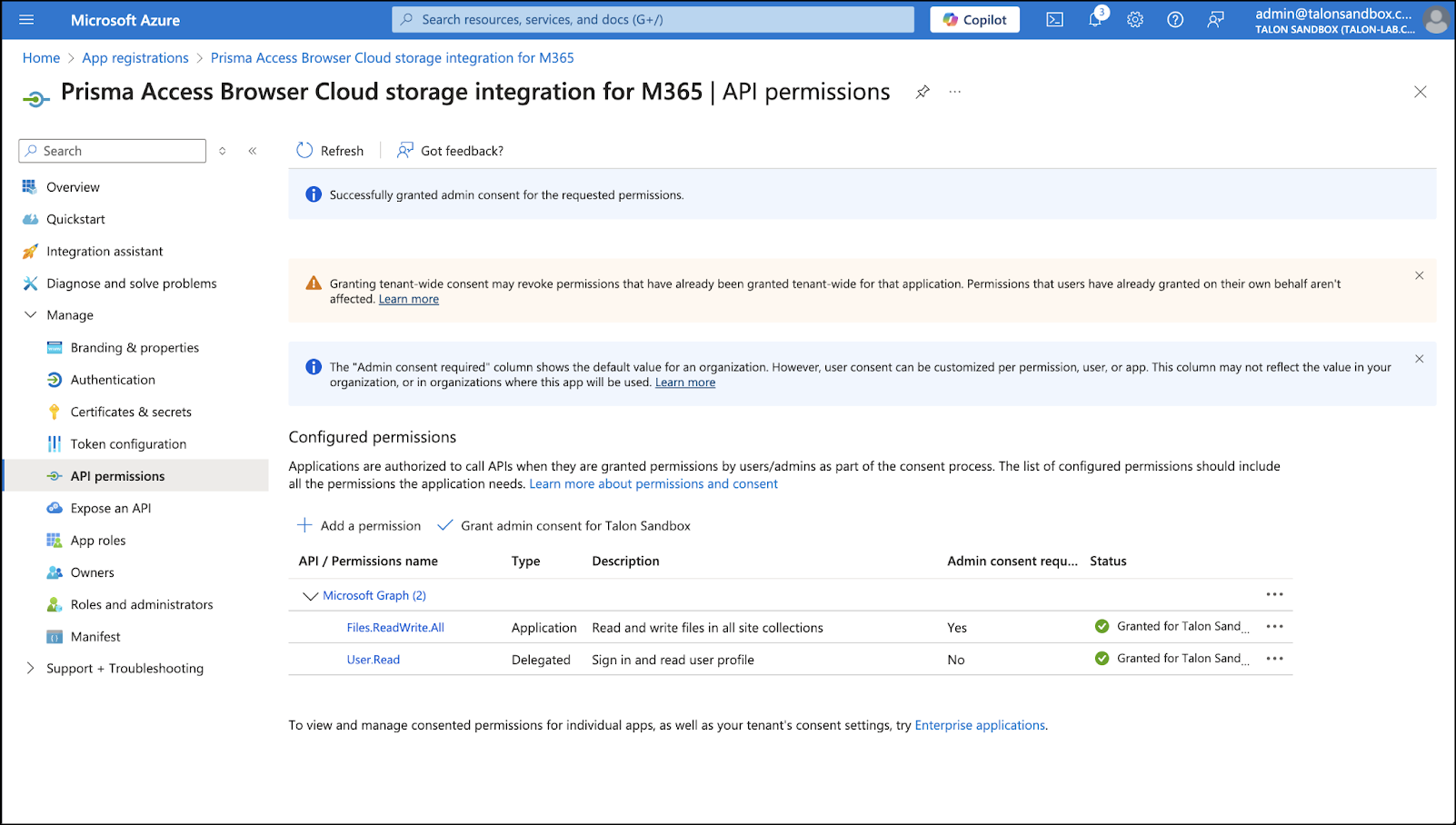
Click Grant admin consent for <your tenant name> Click Yes in the consent confirmation pop-up.User.Read permission (delegated) is added by default by the application. DO NOT REMOVE THIS PERMISSION.![]()
![]() WHY ARE THESE PERMISSIONS NEEDED?Prisma Browser requires specific permissions. These are the minimum necessary to ensure proper connection and to manage file downloads to your organization's cloud storage. This least-privilege approach minimizes security risks by only requesting access essential for its operation.
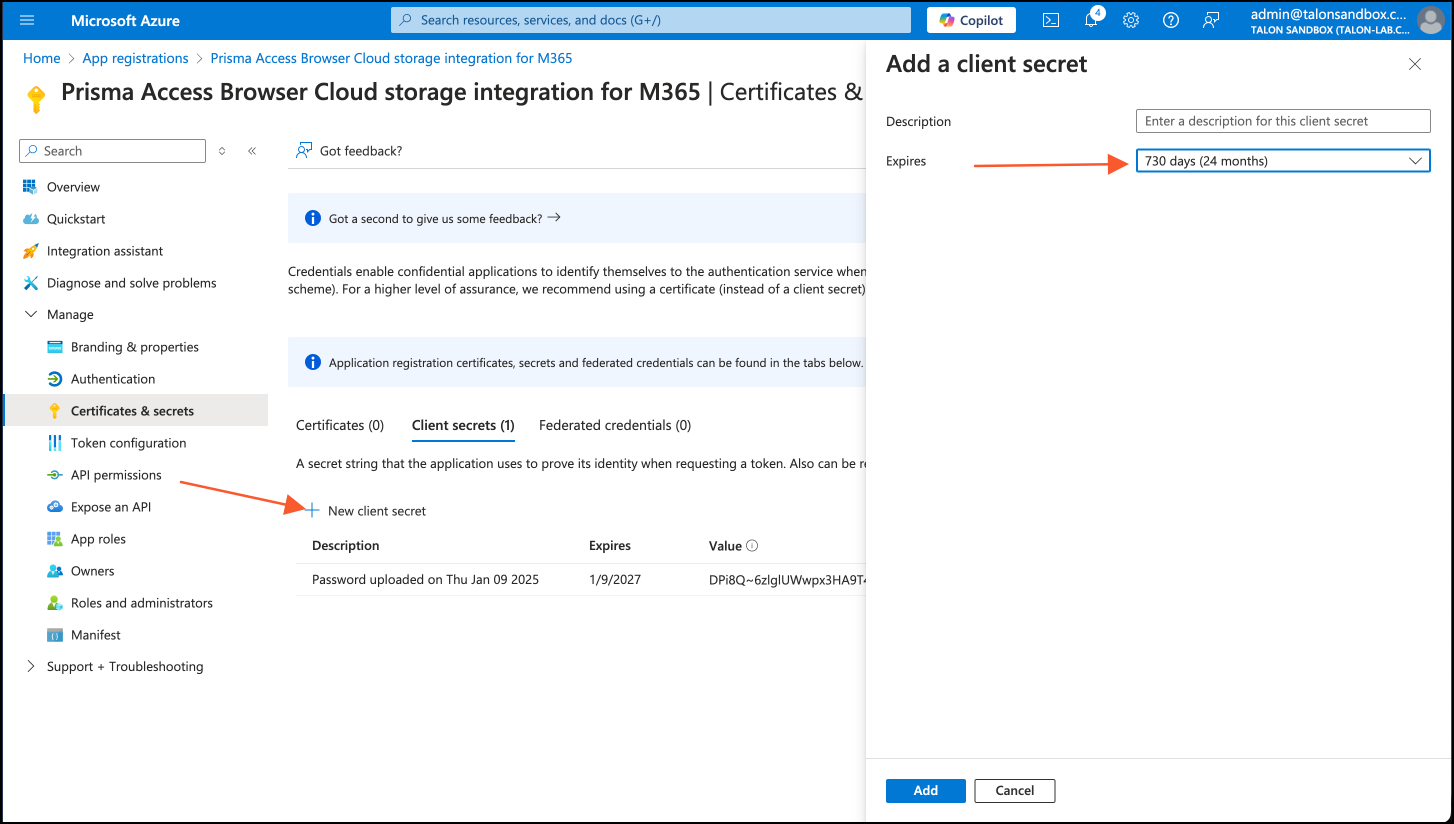
WHY ARE THESE PERMISSIONS NEEDED?Prisma Browser requires specific permissions. These are the minimum necessary to ensure proper connection and to manage file downloads to your organization's cloud storage. This least-privilege approach minimizes security risks by only requesting access essential for its operation.Permission Type Permission Name Reason Delegated User.Read Confirms that the user connected to the browser is the same user that is connected to Microsoft. Delegated Files.ReadWrite.All Saving files to the user's OneDrive on their behalf. Application Application.Read.All DelegatedPermissionGrant.Read.All Verifies the integration configured by the Microsoft admin. Admins always consent to application permissions. In contrast, end users consent to delegated permissions. Granting admin consent for delegated permissions is required. It prevents users from mistakenly denying permissions, which would block them from downloading and saving files to OneDrive when a Security policy is triggered.Verifying the onboarding status of the integration is critical. Improper configuration will prevent Prisma Browser from saving files to OneDrive. This will block end users from downloading and saving files when their download action matches a policy rule.Generate Client Secret.- Go to Certificates & Secrets → New client secret.In the Add a client secret tab, do the following:
- Enter a description for the secret, for example - Microsoft secret 01. (this field is optional.
- In the Expires field, select 730 days (24 months).
Click Add.Copy the value of the new client secret. You will need it for the next step when you connect the cloud storage to the Prisma Browser. We recommend that you save it in a safe place.![]() Connect to the Prisma Browser.
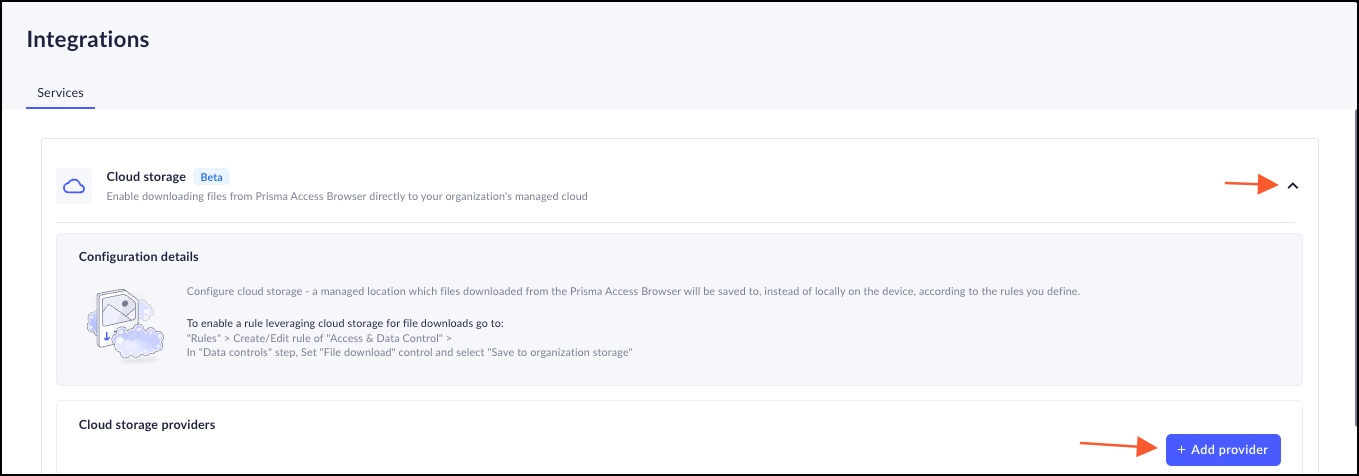
Connect to the Prisma Browser.- Go to the Prisma Browser admin console and select Integrations.Select Cloud Storage.Click on either +add provider or Connect your first provider.
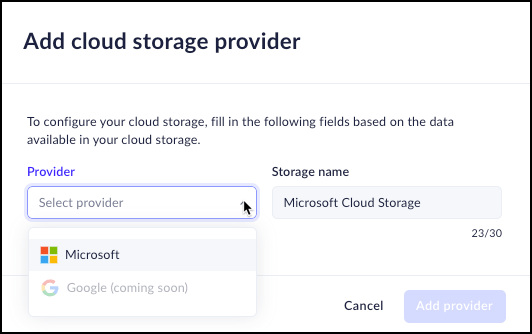
![]() Select the provider - Microsoft.Insert a descriptive Storage name for the connection, for example - Microsoft Cloud Storage.
Select the provider - Microsoft.Insert a descriptive Storage name for the connection, for example - Microsoft Cloud Storage.![]() Paste the Client secret that you generated in the previous step.Enter the Application (client) ID and the Directory (tenant) ID from the Application Overview in the Azure Portal.Click Test provider connection to verify the connection with Azure.Once the test is successful, click Add Provider.Create the Save to Cloud Rule
Paste the Client secret that you generated in the previous step.Enter the Application (client) ID and the Directory (tenant) ID from the Application Overview in the Azure Portal.Click Test provider connection to verify the connection with Azure.Once the test is successful, click Add Provider.Create the Save to Cloud Rule- Open the Access & Data Control rules and create a new rule.At the Data Control step, select File Download.Select Save to organization storage and choose the provider that you configured in the previous step.Add any additional details, and click Set.
Known Limitations and Requirements
To successfully use Save to Cloud, users must meet the following conditions:- Microsoft 365 Licensing: The policy must apply only to users who hold a valid Microsoft 365 license that includes access to OneDrive and the Office suite.
- Email Consistency: The email address used to sign into the browser must match the Microsoft account associated with the user’s OneDrive. This prevents accidental data leakage or cross-account DLP violations.
- Microsoft Sign-In Required: Users must be signed into their Microsoft account. If not already authenticated, they will be prompted to log in, with the browser providing a username hint to streamline the process.
HTML sites will be compressed using zip format and saved in a folder. The Prisma Browser does not support unzipping files. As a result, this is not recommended.
Cloud Provider - Google Drive
This document contains the directions for integrating Google Drive as the cloud providerGoogle Drive Prerequisites
These are the prerequisites for configuring Google Drive as your cloud provider:- Super Admin role in the Google Workspace Admin Console.
- Role on a Google Cloud Platform (GCP) project. You need one of the following
toles:
- Service Account Creator (roles/iam.serviceAccountCreator)
- Service Account Key Admin (roles/iam.serviceAccountKeyAdmin)
- Service Usage Admin (roles/serviceusage.serviceUsageAdmin)
- Project Editor role (roles/editor)
End users require a valid Google Workspace License. The supported SKUs include:- Google Workspace Business Starter
- Google Workspace Business Standard
- Google Workspace Business Plus
- Google Workspace Enterprise Standard
- Google Workspace Enterprise Plus
Configure Google Drive as the Cloud Provider
This document outlines the steps required to onboard Google Drive as a cloud Storage Provider for use with Prisma Browser’s Save to Cloud feature. This process involves configuring access through Google Cloud Platform (GCP) and delegating domain-wide authority in the Google Workspace Admin Console.- Enable the Google Drive API in GCP.
- Open a browser tab and navigate to the Google Cloud Console.Select or create a project that will be used for the integration.In the left side menu, go to APIs & Services → Enabled APIs and Services.Click Enable APIs & Services.
![]() Select Google Drive API and click Enable on the details page.
Select Google Drive API and click Enable on the details page.![]() The Service Account allows the browser to upload files by generating a one-time token per upload, eliminating the need for the user to log in each time.Create a Service Account.
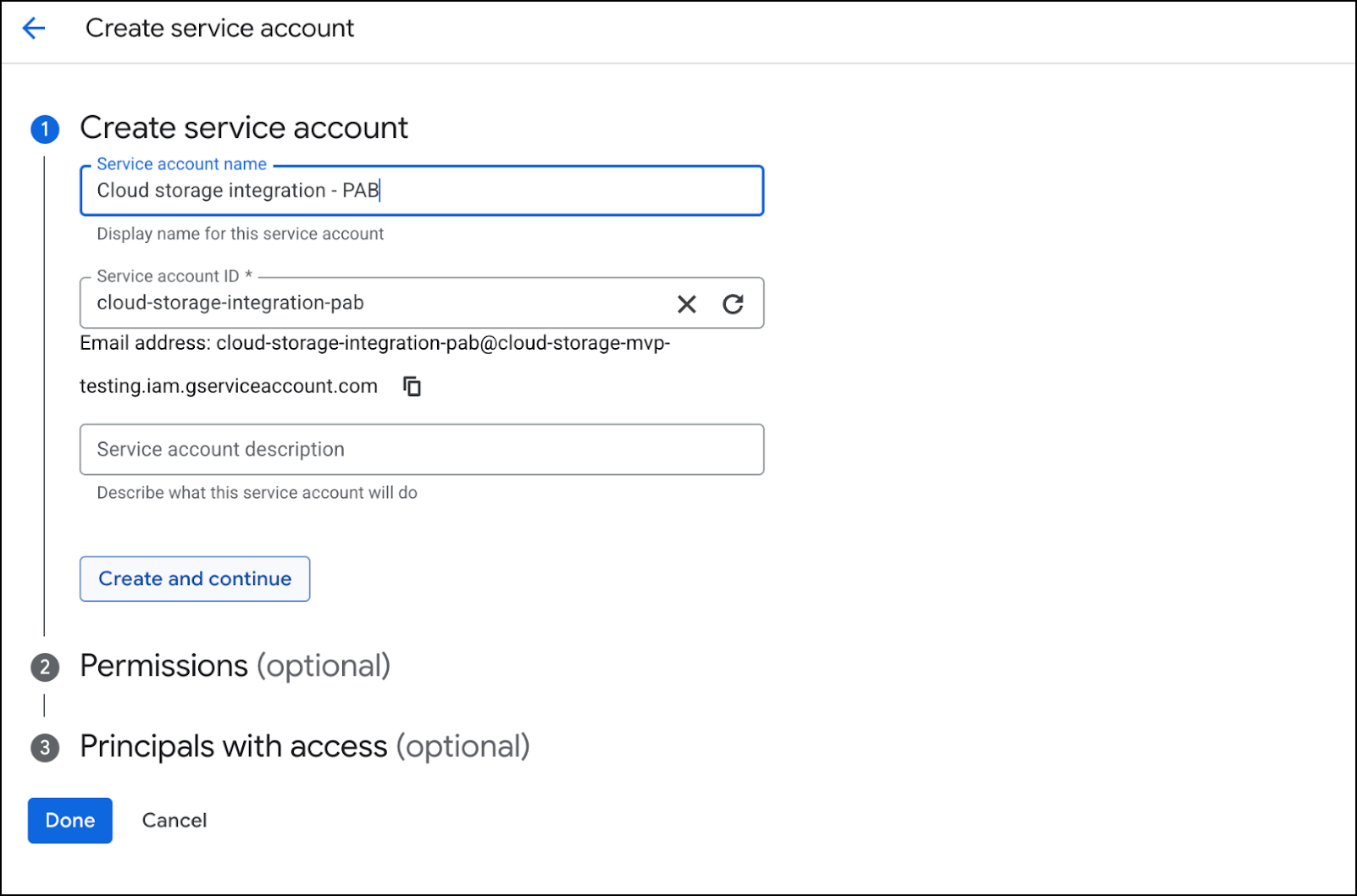
The Service Account allows the browser to upload files by generating a one-time token per upload, eliminating the need for the user to log in each time.Create a Service Account.- In the Google Cloud Console, go to the project you selected in the previous step.Navigate to IAM & Admin and select Service Accounts.Click + Create service account.
- Enter a Service account name. This name will be displayed in the Google Cloud Console.
- Click Create and continue to generate the Service account ID. You can edit it, if needed.
- Optionally, enter a Service Account description.
- Click Done.
![]()
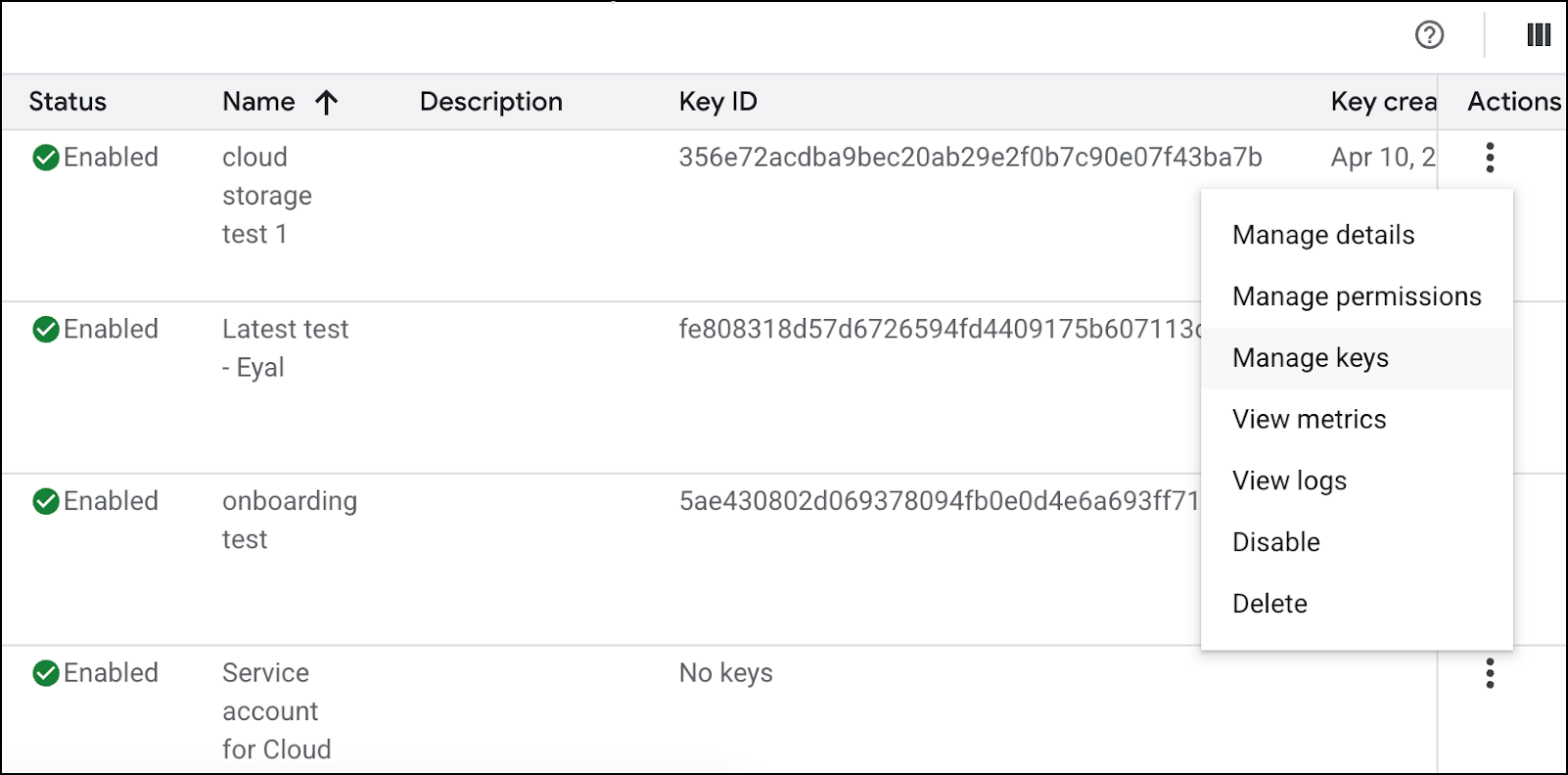
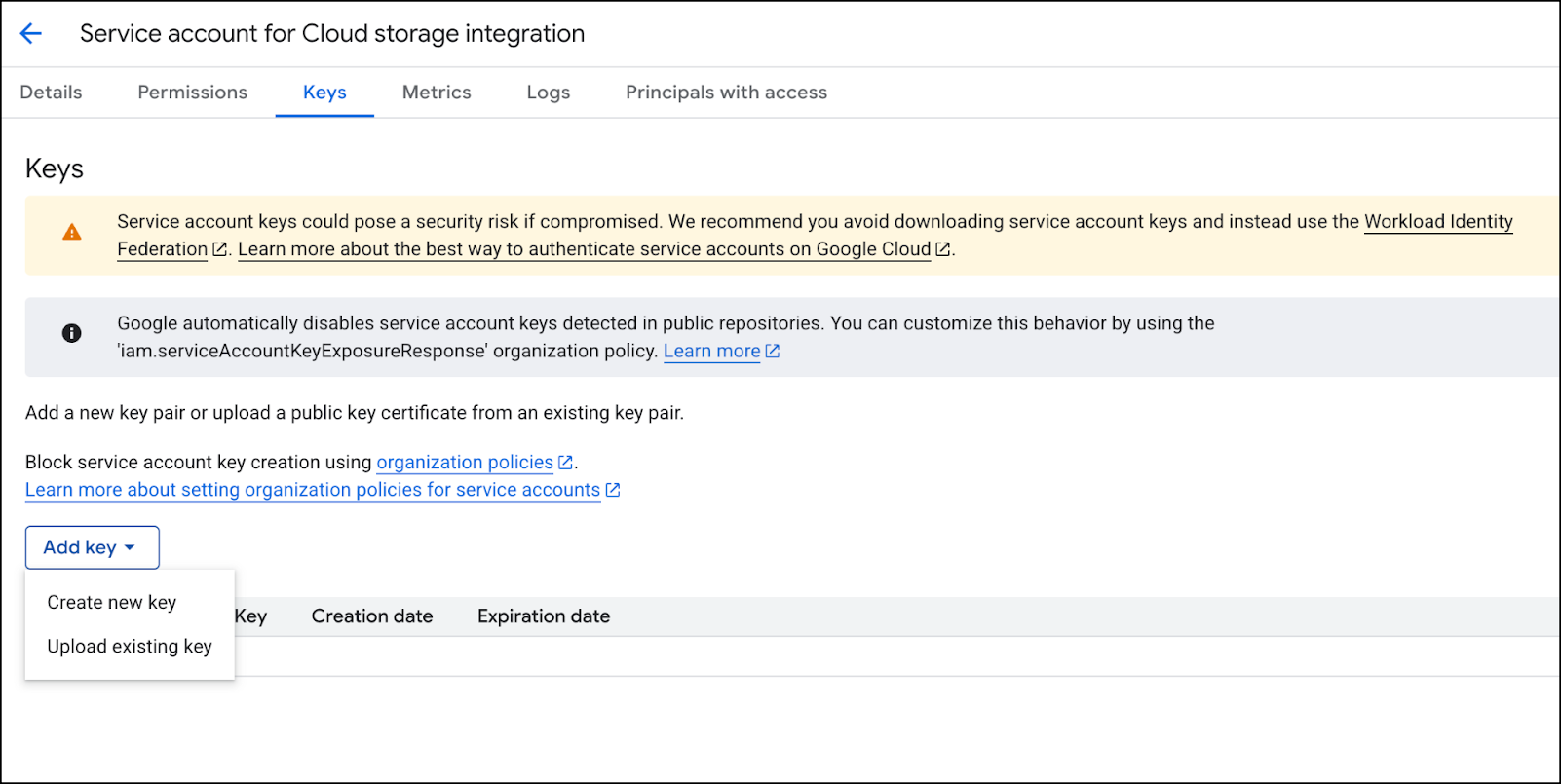
Continue through the steps until the service account is created.Generate a Private Key (JSON)- Locate your newly-created service account in the list.Click the More (⋮) icon under the Actions field, and select Manage Keys.
![]() Click ADD KEY → Create new key.
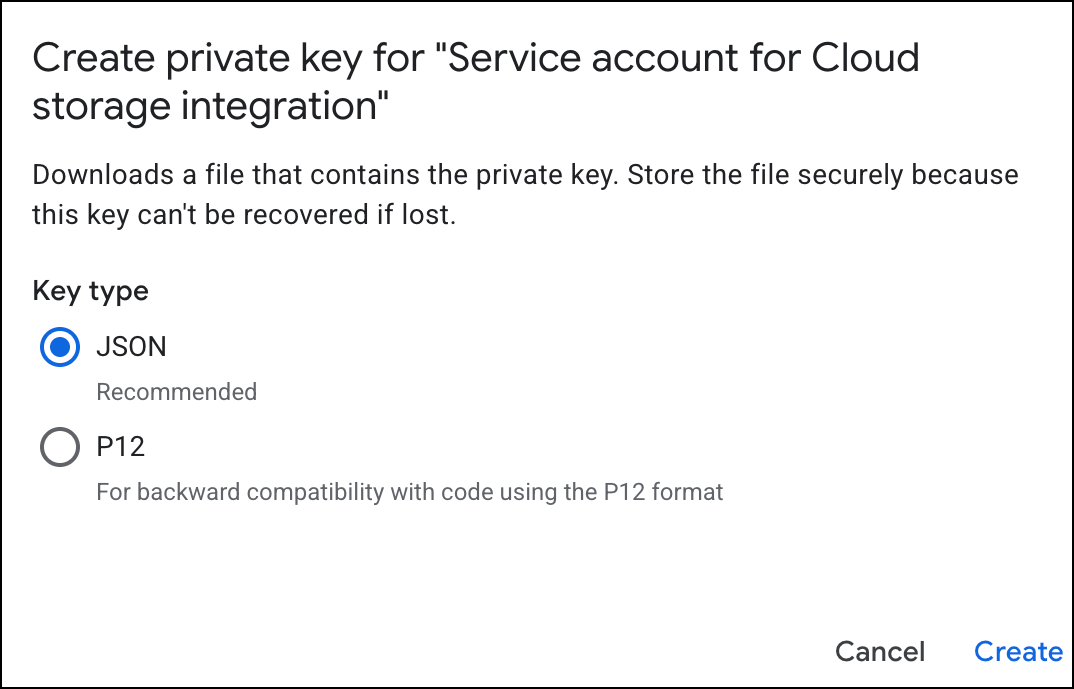
Click ADD KEY → Create new key.![]() Choose JSON as the key type and click Create.
Choose JSON as the key type and click Create.![]() The system downloads a private key file to your computer. Store this file securely; it authenticates the service account.Retrieve the Client ID
The system downloads a private key file to your computer. Store this file securely; it authenticates the service account.Retrieve the Client ID- Go back to the Service Accounts page in the Cloud Console.Click the name of your service account to open its details.Under the Details tab, locate the Client ID and copy it. You will use this in the next step.
![]() Delegate Domain-Wide Authority in Google Workspace.
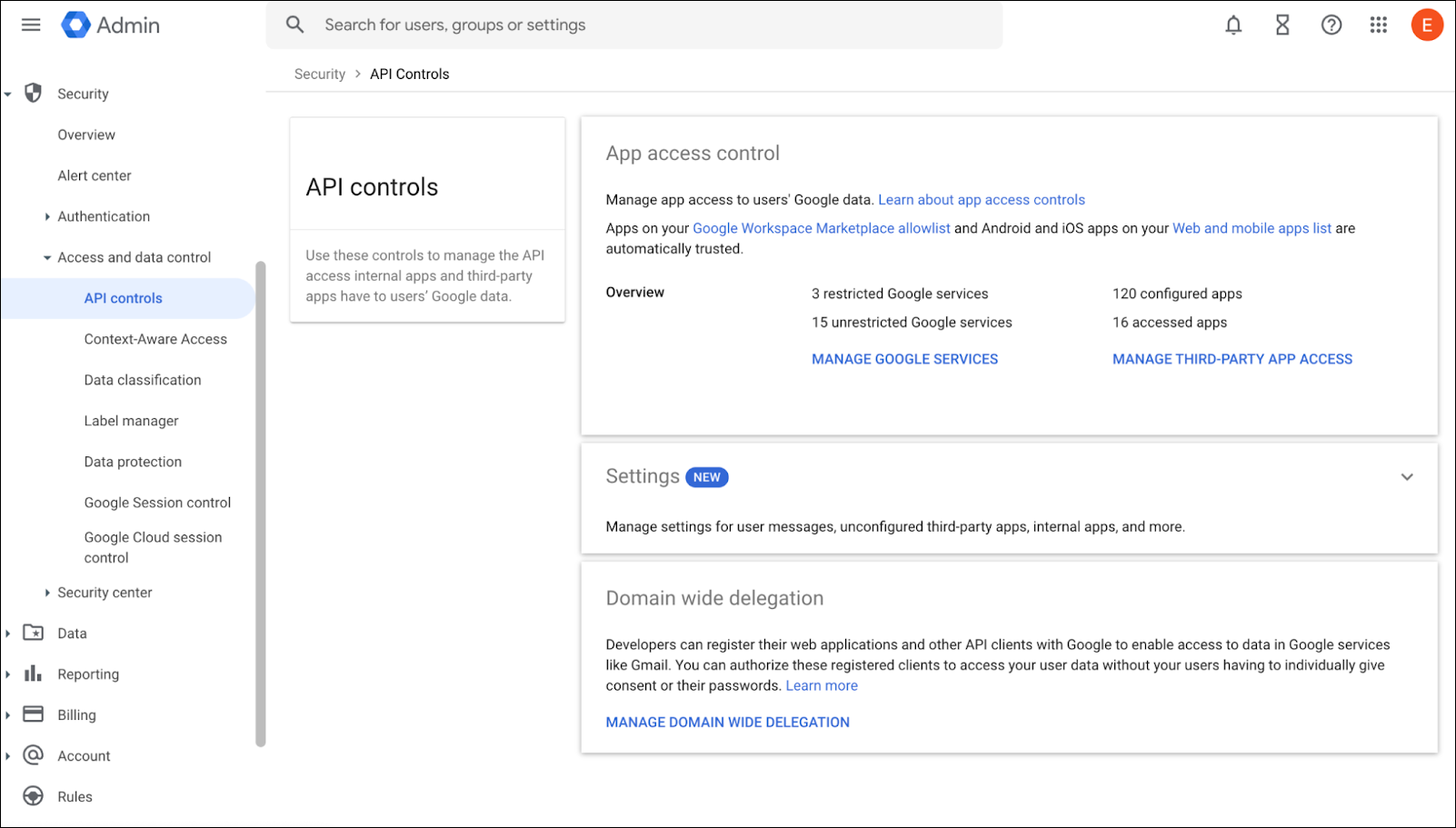
Delegate Domain-Wide Authority in Google Workspace.- Open a browser and navigate to theGoogle Admin Console.Sign in using a Super Admin account.From the left-hand menu, go to Security → API Controls.Scroll to the Domain-wide delegation section and click Manage Domain Wide Delegation.
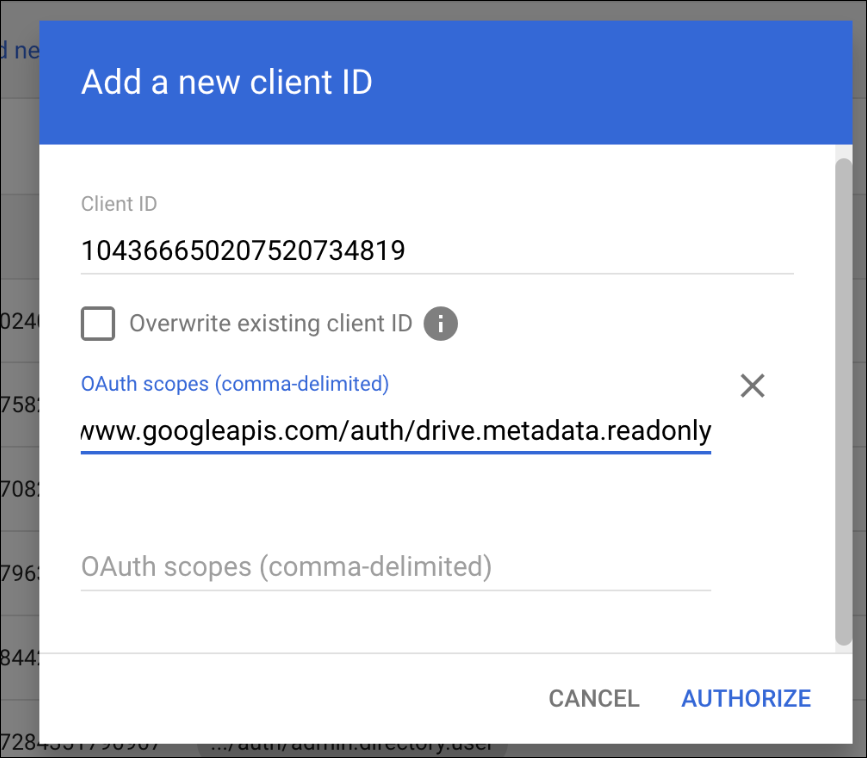
![]() Click Add new to add a new Client ID.In the Client ID field, paste the ID you copied from your service account.In the OAuth Scopes field (comma-delimited), enter the following scopes:
Click Add new to add a new Client ID.In the Client ID field, paste the ID you copied from your service account.In the OAuth Scopes field (comma-delimited), enter the following scopes:- https://www.googleapis.com/auth/drive.file
- https://www.googleapis.com/auth/drive.metadata.readonly
These scopes allow the service account to access and manage Google Drive files on behalf of users within the domain.![]() Click Authorize to complete the delegation process.Why are the Scopes required?These scopes adhere to the principle of least privilege, ensuring the application only has the permissions required to perform its core functions — securing connections and managing file downloads effectively to the organizational cloud.These scopes allow the service account to access and manage Drive files on behalf of users within the domain.
Click Authorize to complete the delegation process.Why are the Scopes required?These scopes adhere to the principle of least privilege, ensuring the application only has the permissions required to perform its core functions — securing connections and managing file downloads effectively to the organizational cloud.These scopes allow the service account to access and manage Drive files on behalf of users within the domain.drive.metadata.readonly Used to list folders in the user's drive drive.file Used to upload files to the user's drive By using domain-wide delegation, Prisma Browser can upload files to an end-user's Google Drive without any user interaction. This process leverages the user's browser sign-in context, eliminating the need for them to be actively signed into Google.For security, Prisma Browser uses a short-lived access token to upload files to Google Drive. This token is created only when a file download triggers a matching cloud storage rule and is strictly scoped to the signed-in user, which prevents extensive access.Create the integration with the Prisma Browser Console.- Go to the Prisma Browser admin console and select Integrations.Select Cloud Storage.Click on either +add provider or Connect your first provider.
![]() Select Google.Insert a descriptive name for connection; for example, your Google tenant name.Upload the JSON file.Enter an email to verify permissions.
Select Google.Insert a descriptive name for connection; for example, your Google tenant name.Upload the JSON file.Enter an email to verify permissions.- This step secures your organization’s data and enhances user productivity by integrating with your managed cloud storage services. Instead of allowing direct file downloads to user devices, our 'Save to Cloud' feature automatically redirects them to your organization’s cloud storage.This method ensures that you can enforce your data protection policies and give users seamless access to their files across all their devices, which supports better collaboration and a smoother workflow.
- To ensure that you have configured the permissions correctly, you must use the email of an active, licensed user in your organization. The system uses this email solely for a permissions check; it will not send emails or upload any files to the account.
Click Test provider connection to verify the connection with Google.Once the test is successful, click Add Provider.Known Limitation
HTML sites will be compressed using zip format and saved in a folder. The Prisma Browser does not support unzipping files. As a result, this is not recommended.