Prisma Browser
IP Based Enforcement
Table of Contents
Expand All
|
Collapse All
Prisma Browser Docs
IP Based Enforcement
Ensure that access to SSO-enabled applications is only possible from the Prisma Browser.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
IP-based enforcement ensures that access to SSO-enabled applications is
only possible from the Prisma Browser. Authentication traffic to your IdP flows
through a special proxy with a set of known egress IP addresses.
The Prisma Browser uses the Authentication Proxy for
the SSO login pages only. It does not use the proxy for any other traffic.
The Prisma Access Gateway acts as a forward proxy with a set of predictable
IP addresses. You then need to configure the browser to route the IdP authentication
traffic through the Prisma Browser gateway.
You then need to create and establish a conditional access rule in the IdP,
making a requirement to only use the Prisma Browser Gateway for authentication.
This means that any attempt to authenticate via a different browser will fail.
To begin the process, perform the following actions:
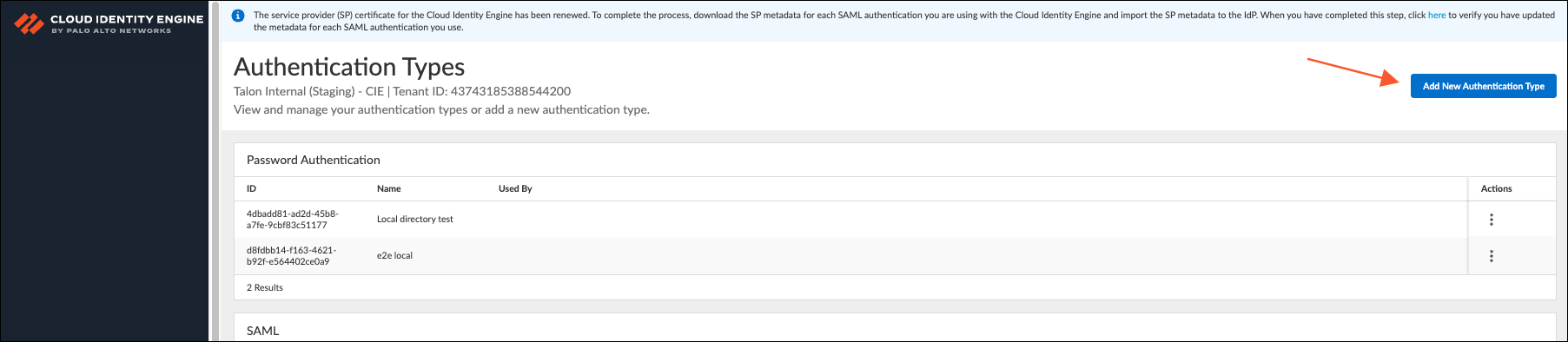
- Open the Strata Cloud Manager.Open the Cloud Identity Engine.Select Authentication TypesClick Add New Authentication Type.
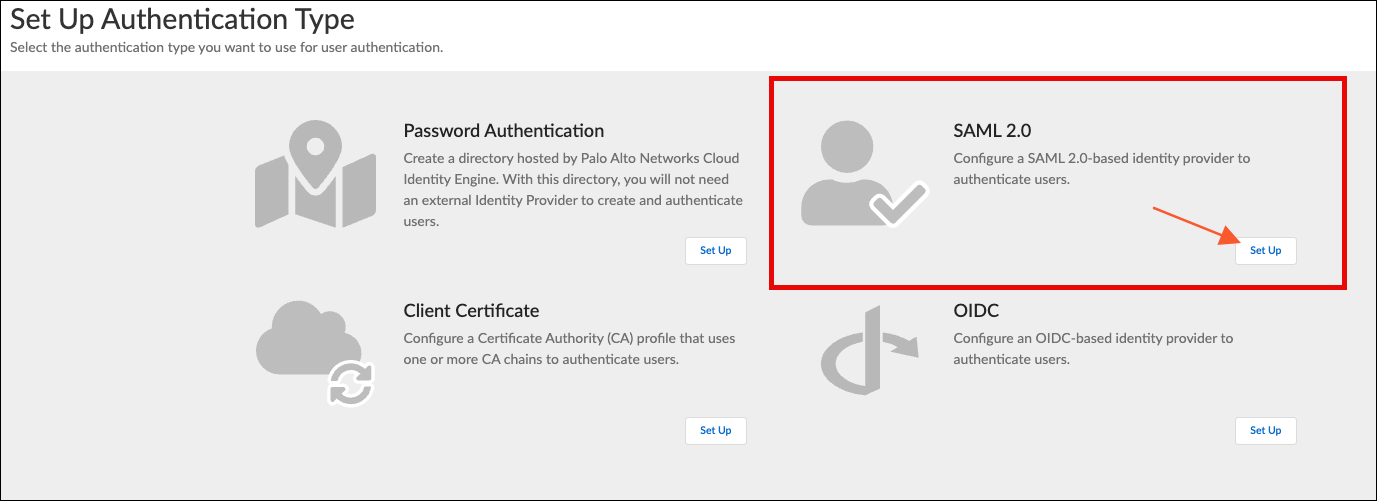
![]() Under SAML 2.0, click Set Up.
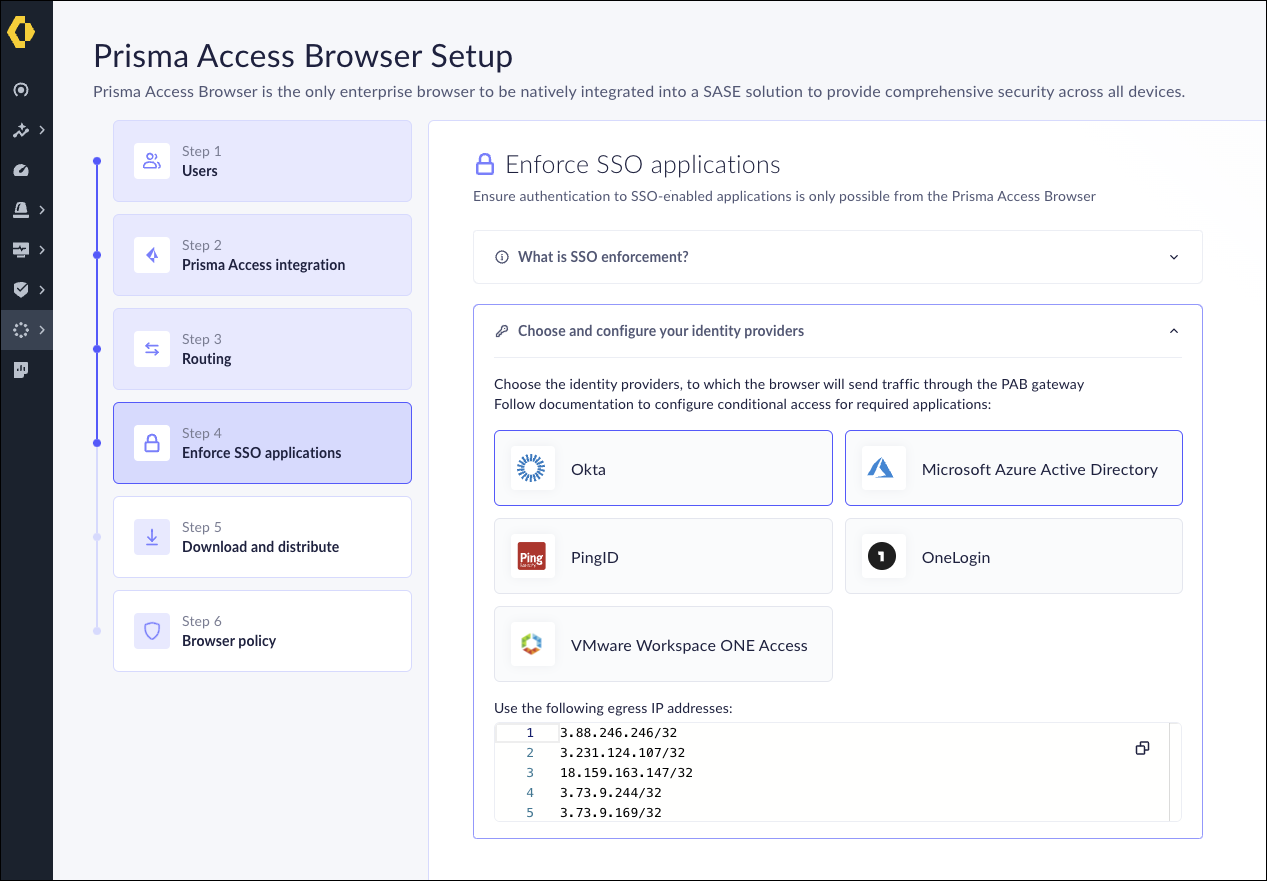
Under SAML 2.0, click Set Up.![]() Set up your IdP. To properly configure the IdP, refer to Cloud Identity Engine Getting Started.In the Prisma Browser Setup page, click step 4: Enforce SSO Applications.
Set up your IdP. To properly configure the IdP, refer to Cloud Identity Engine Getting Started.In the Prisma Browser Setup page, click step 4: Enforce SSO Applications.![]() Choose the appropriate IdP. All Prisma Browserauthentication traffic to those identity provider tunnels through the Prisma Browser gateway. The options are:
Choose the appropriate IdP. All Prisma Browserauthentication traffic to those identity provider tunnels through the Prisma Browser gateway. The options are:- Okta
- PingID
- VMware ONE Workspace Access
- Microsoft Azure Active Directory
- OneLogin
To integrate the Prisma Access Browser and Okta with the device Posture provider, see here.Configure Okta IP-Based Enforcement
Follow these steps to limit access to all or specific apps to the Prisma Browser when you use Okta. - Configure the Prisma Browser Application Enforcement IP Addresses
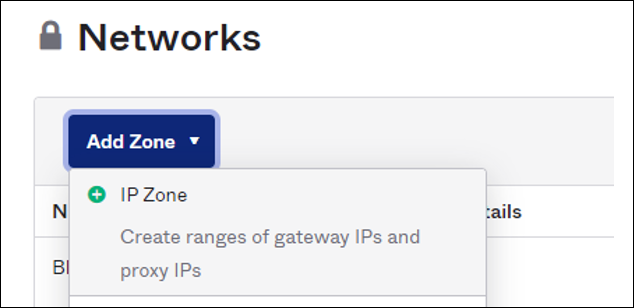
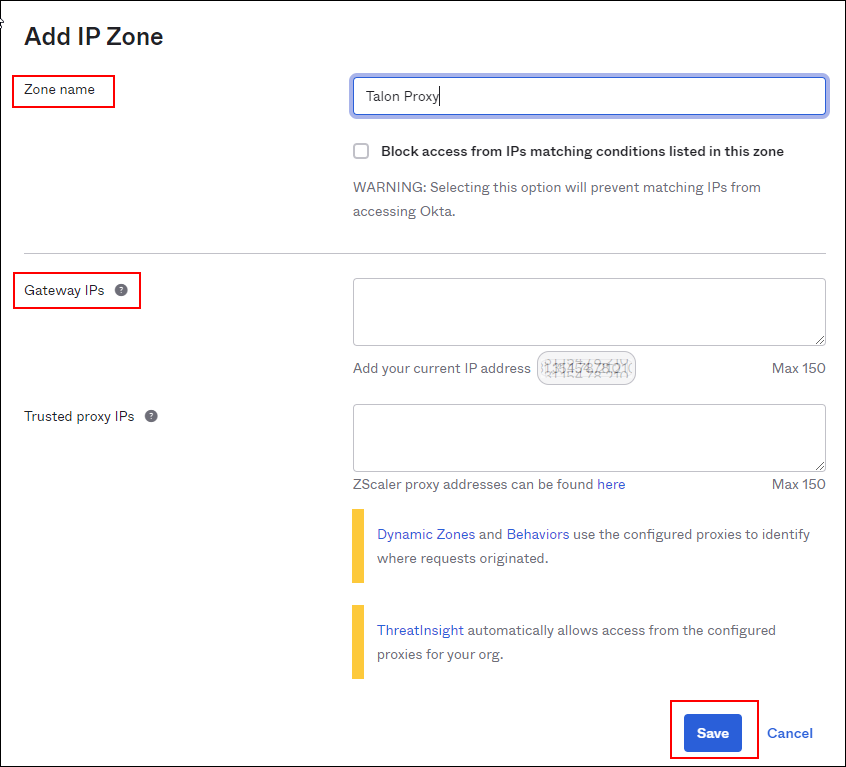
- Configure the Application Enforcement IP Addresses. In the Okta app go to Security > Networks > Add zone > IP zone.
![]() Set the name of the zone to the Prisma Access Authentication Proxy.In the Gateway IPfield, paste the egress IP Addresses.Click Save.
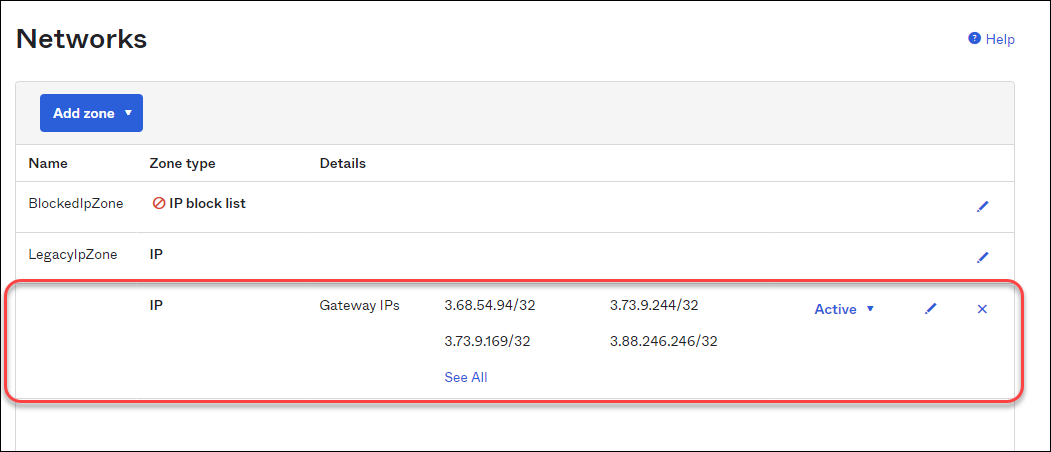
Set the name of the zone to the Prisma Access Authentication Proxy.In the Gateway IPfield, paste the egress IP Addresses.Click Save.![]() Confirm that the new zone appears in the list.
Confirm that the new zone appears in the list.![]() Select Applications and User Groups to Adhere to the Policy
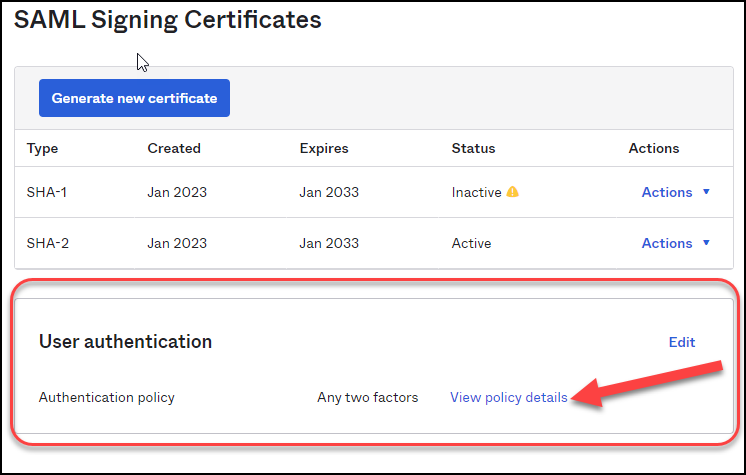
Select Applications and User Groups to Adhere to the Policy- You need to create a new conditional access; Choose Applications -> Applications and click on the app that you want to restrict.Go to the Sign On tab, scroll down to the User Authentication and click View policy details.
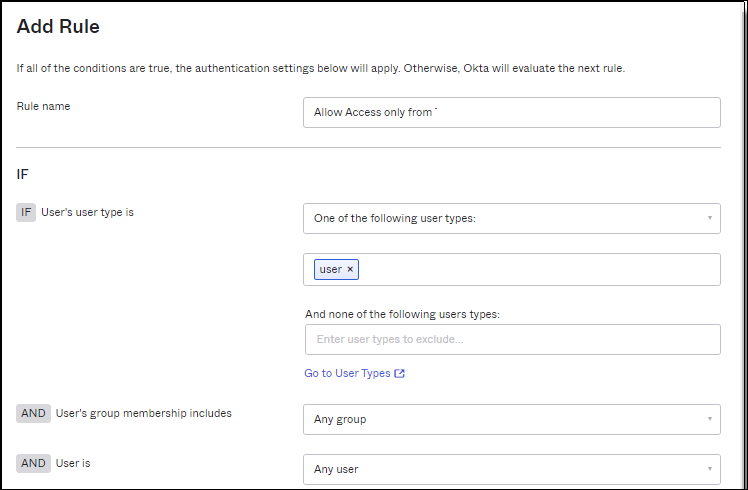
![]() Click Add rule and enter the following information:
Click Add rule and enter the following information:- Name: Allow access only from the Prisma Browser.
- Users: Select the users or user groups to enforce:
- User's group membership includes - make sure that you configure this setting for groups.
- User is - Allows you to apply rules to some specific
users, but not to other specific users.
![]()
- Device Platform is - Make sure you select both Windows and macOS.
- User IP is Select Not in any of the following zones, and select Prisma Access Authentication Proxy.
- Access is - Select Denied.
- Click Save.
Enable IdP Enforcement in the Prisma Access Console- In the Strata Cloud Manager, navigate to Workflows → Prisma Access Setup → Prisma BrowserConfiguration → Prisma Browser → Onboarding .In the Onboard Users section, Locate Prisma Browser and click View.In the Prisma Browser Setup page, click Step 4: Enforce SSO Applications.Select the appropriate IdP. In this case, click Okta.From this point on, users will only be able to access the SSO applications via the Prisma Browser
Configure Microsoft Azure Active Directory IP-Based Enforcement
Follow these steps to limit access to all or specific apps to the Prisma Browser when you use Microsoft Azure Active Directory. The Prisma Browser uses the Authentication Proxy for the SSO login pages only. It does not use the proxy for any other traffic.You need Microsoft P2 Premium licenses at a minimum, including Microsoft 365 business to enable this enforcement.Configure the Prisma Browser Application Enforcement IP Addresses
- Create a new Named Location from the Azure Active Directory Admin Center.
- Search for the Named Locations from the Admin Center. If available, select the New and improved Named Location.
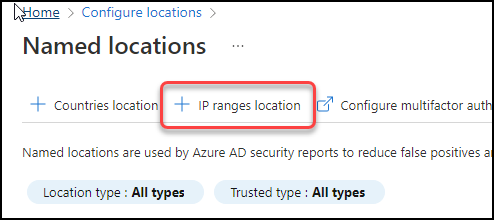
![]() Click IP range location.
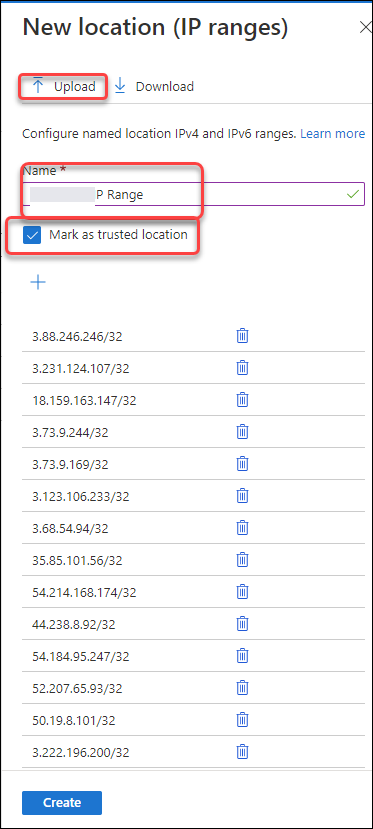
Click IP range location.![]() In the New Location <IP> Ranges section, enter the name of the Prisma Browser IP Range.Paste the egress IP Addresses into a text file.Upload the file.
In the New Location <IP> Ranges section, enter the name of the Prisma Browser IP Range.Paste the egress IP Addresses into a text file.Upload the file.![]() Click Create.Confirm that the new Named Location appears on the list.
Click Create.Confirm that the new Named Location appears on the list.![]() Select Applications and User Groups to Adhere to Policy
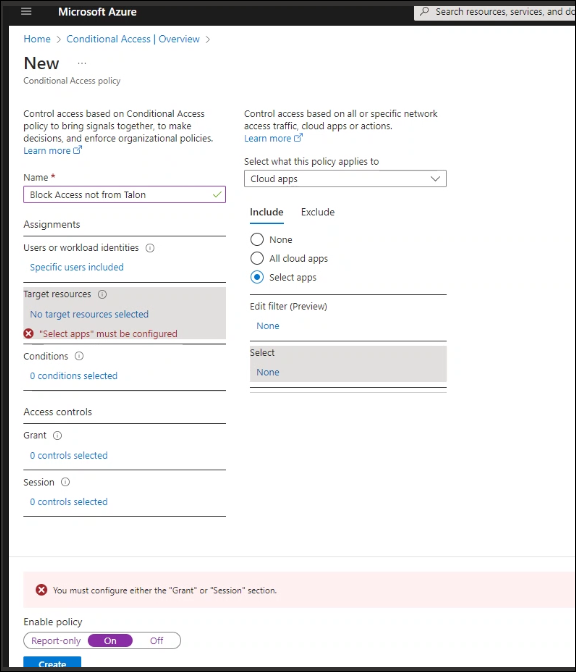
Select Applications and User Groups to Adhere to Policy- Navigate to the Azure Conditional Access Portal.Select New Policy → Create New Policy , and enter the following information:
- Name - Enter a name. For example, Block access not from Prisma Browser.
- Assignments - Assign the policy to users or groups. Be sure to include all users who need to connect to applications using the Prisma Browser only.
- Target Resources - Make sure that the Control access includes cloud apps.
- Conditions - Apply any needed conditions. Include at least one local condition.
- Grant - Select Block access.
- Cloud apps or actions - Select Cloud apps, then include selected applications.
The Prisma Browser can't be a required application for enforcement.If you select All apps, be sure to exclude the Prisma Browser.- Enable policy - Set this to On.
Click Create.![]() Enable IdP Enforcement in the Prisma Access Console
Enable IdP Enforcement in the Prisma Access Console- In the Strata Cloud Manager, navigate to Workflows → Prisma Access Setup → Prisma BrowserConfiguration → Prisma Browser → Onboarding .In the Onboard Users section, Locate Prisma Browser and click View.In the Prisma Browser Setup page, click Step 4: Enforce SSO Applications.Select the appropriate IdP. In this case, click Microsoft Azure Active Directory.From this point on, users will only be able to access the SSO applications via the Prisma Browser
Configure OneLogin IP-Based Enforcement
Follow these steps to limit access to all or specific apps to the Prisma Browser when you use OneLogin. - Configure the Prisma Browser Application Enforcement IP Addresses
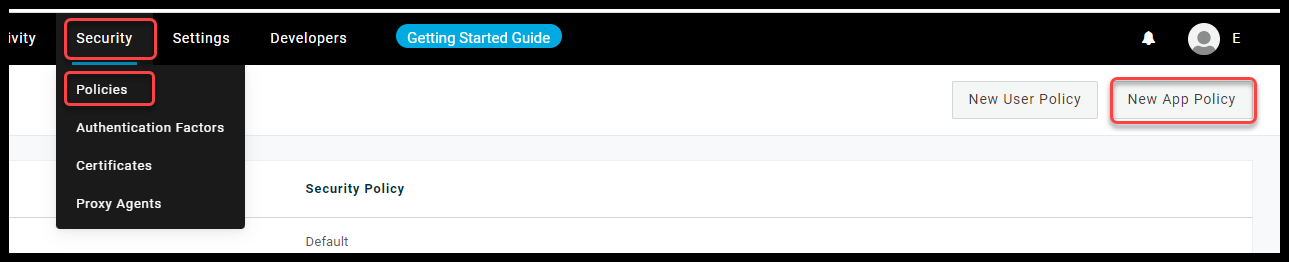
- In the OneLogin toolbar go to Security -> Policy .Click New App Policy.
![]() Enter a name to identify the policy. For example, Enforce Access from the Prisma Browser only.In the IP Address Whitelist, copy and paste the egress IP Addresses.Click Save.Click Select Applications and User Groups to Adhere to Policy
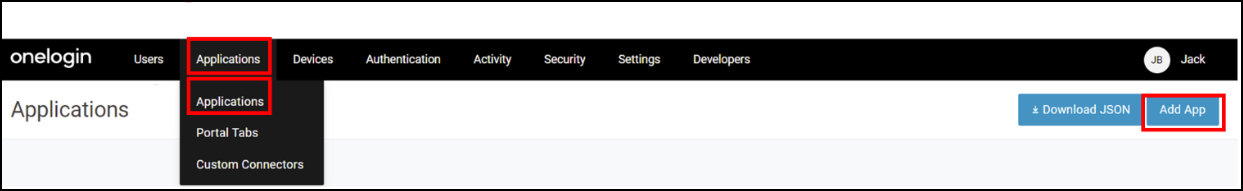
Enter a name to identify the policy. For example, Enforce Access from the Prisma Browser only.In the IP Address Whitelist, copy and paste the egress IP Addresses.Click Save.Click Select Applications and User Groups to Adhere to Policy- On the OneLogin toolbar go to Application → Applications.Click Add App.
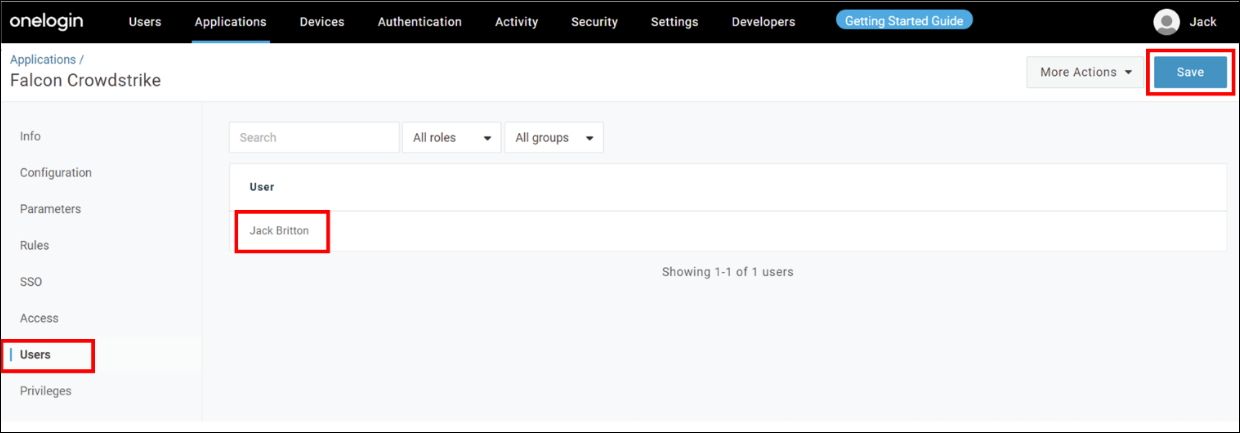
![]() In the Found Applications field. search for the application that you need to add.Click Save.Select Access.In the drop down before the Policy Title, select Enforce Access from the Prisma Browser only.Repeat steps b-f for each application that you want to add enforcement access.The Prisma Browser can't be a required application for enforcement.Select Users.Select the Users or Groups that must adhere to the Enforce Access from the Prisma Browser only policy.
In the Found Applications field. search for the application that you need to add.Click Save.Select Access.In the drop down before the Policy Title, select Enforce Access from the Prisma Browser only.Repeat steps b-f for each application that you want to add enforcement access.The Prisma Browser can't be a required application for enforcement.Select Users.Select the Users or Groups that must adhere to the Enforce Access from the Prisma Browser only policy.![]() Enable IdP Enforcement in the Prisma Access Console
Enable IdP Enforcement in the Prisma Access Console- In the Strata Cloud Manager, navigate to Workflows → Prisma Access Setup → Prisma BrowserConfiguration → Prisma Browser → Onboarding .In the Onboard Users section, Locate Prisma Browser and click View.In the Prisma Browser Setup page, click Step 4: Enforce SSO Applications.Select the appropriate IdP. In this case, click v .From this point on, users will only be able to access the SSO applications via the Prisma Browser
Configure PingOne IP Based Enforcement
Follow these steps to limit access to all or specific apps to the Prisma Browser when you use PingOne. - Configure the Prisma Browser Application Enforcement. In the PingOne Admin Console, perform the following steps:
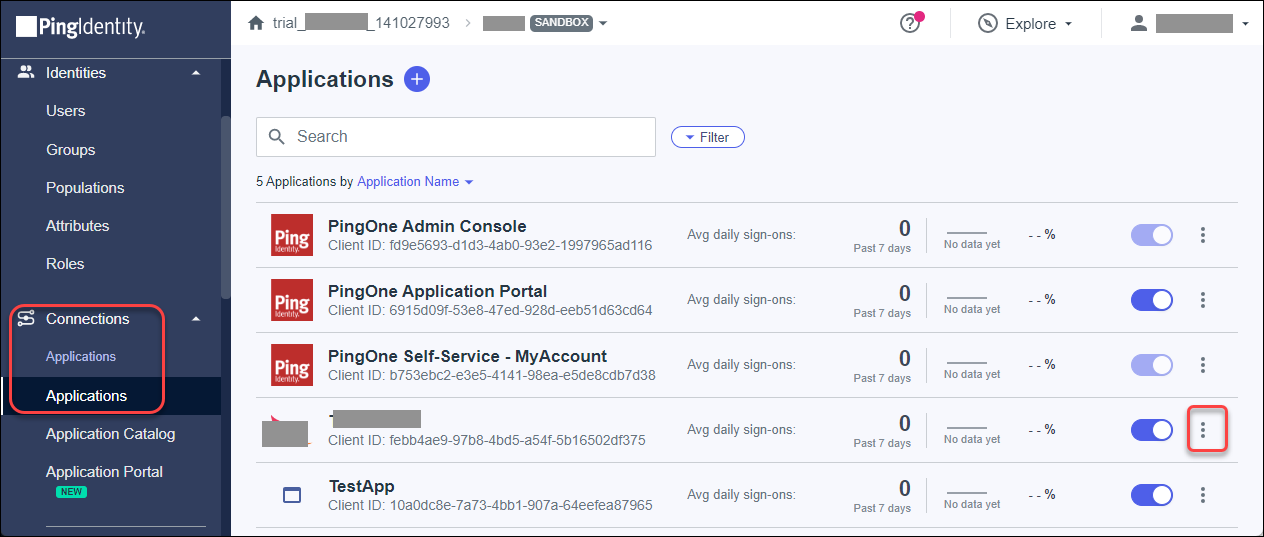
- Select Connection → Application, select the Prisma Browser application, and click the vertical ellipse.
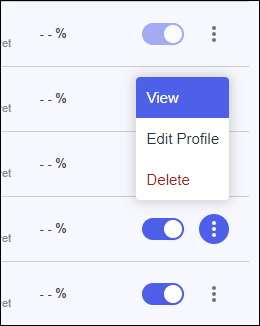
![]() Click View.
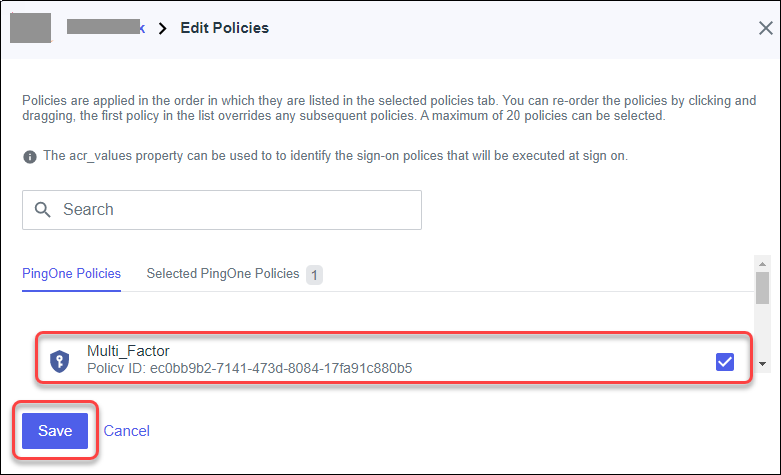
Click View.![]() Select the Policy Rules tab and click the pencil icon.Click Add Policy Rules.In the Edit Policies window, select Multi_Factor, and click Save.
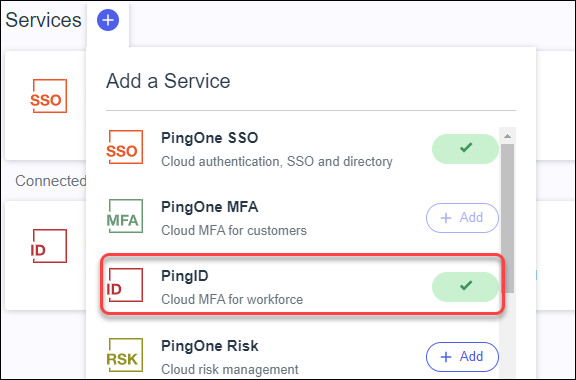
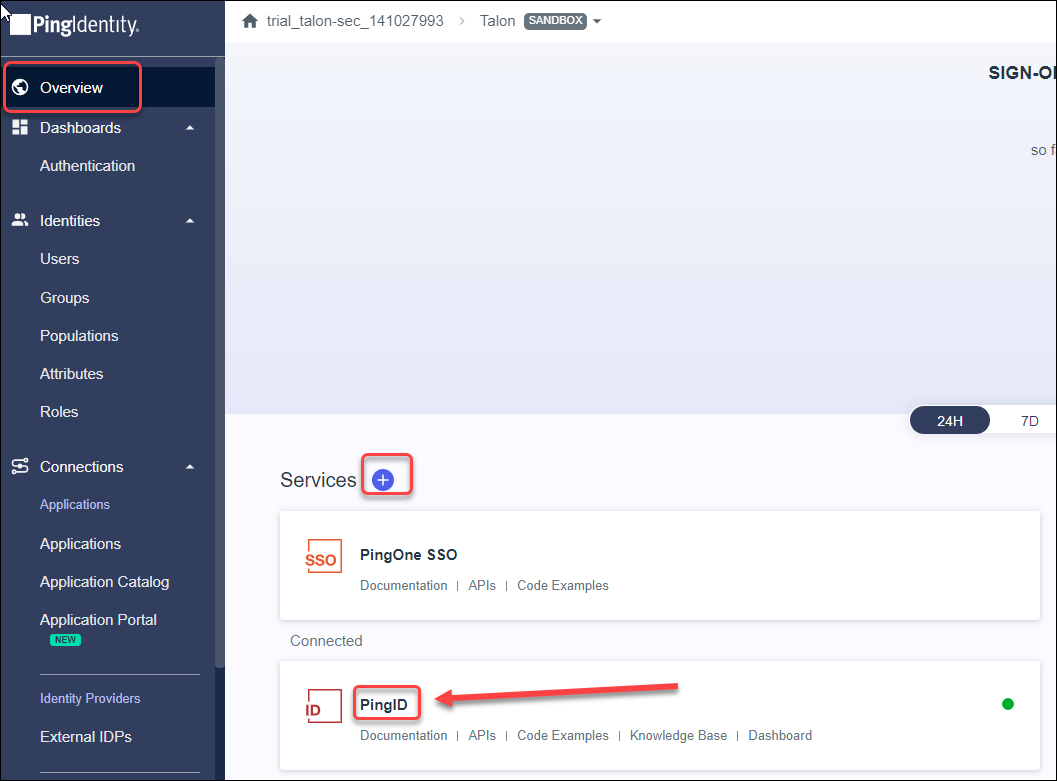
Select the Policy Rules tab and click the pencil icon.Click Add Policy Rules.In the Edit Policies window, select Multi_Factor, and click Save.![]() Select Overview and click PingID.
Select Overview and click PingID.- Click on the Services + and add the PingID
service.
![]()
- Click on PingID and continue the process.
![]()
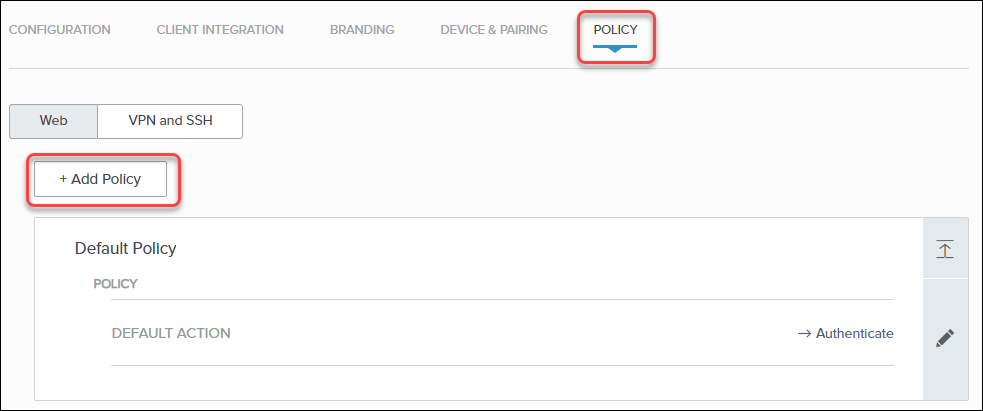
- Select the Policy tab and click Add Policy.
![]()
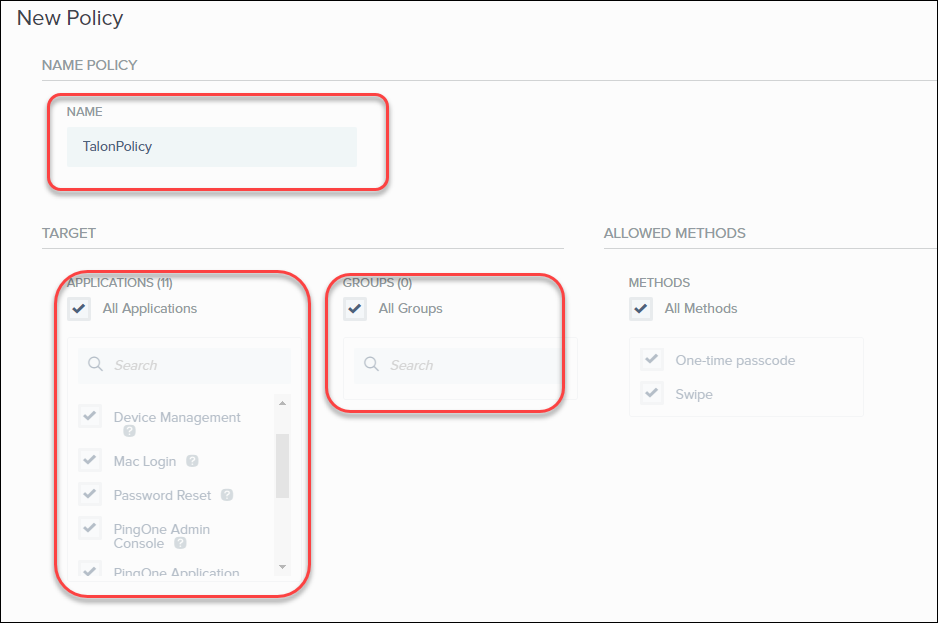
In the New Policy page, enter the following information:- In the Name field, enter an identifying name.
- In the Application section, select the applications that you want to apply conditional access enforcement.
- In the Groups section, select All Groups.
![]()
- If an application does not appear on the list:
- Make sure that the application has multi-factor authentication enabled.
- Under PingFederate Applications, click Add Application to add the application to the list.
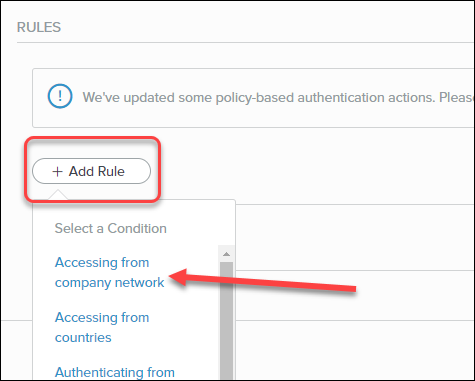
In the Rules section, click Add Rule.- For Select a Condition, choose Accessing from a
company network.
![]()
- For Action select Approve.
- For the IP addresses, manually copy and paste the egress IP addresses as comma-separated-values.
- In the Default Action section, choose Deny.
- Click Save.
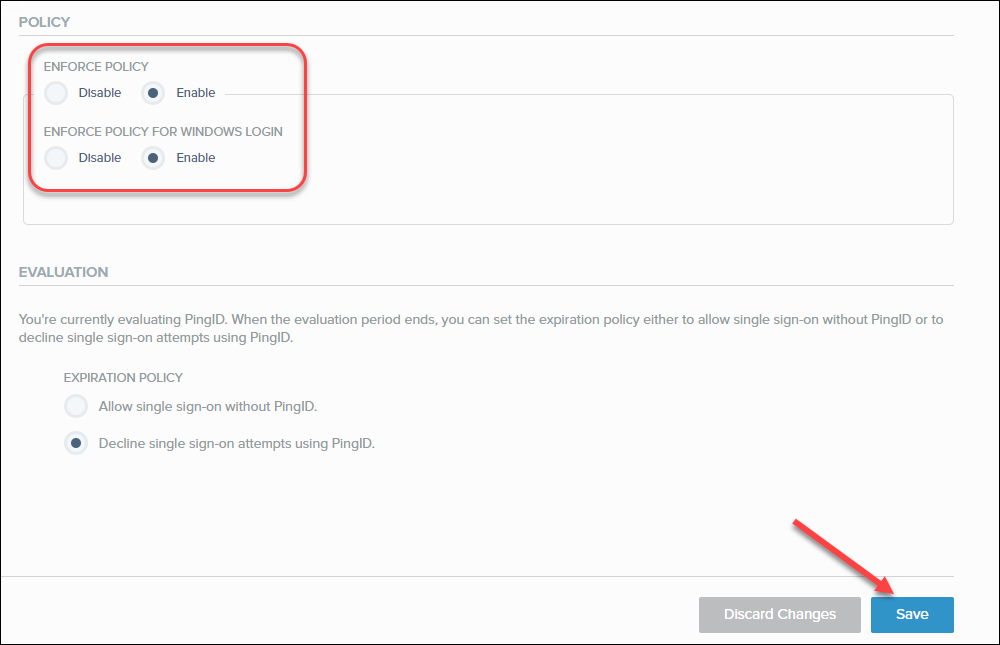
Click the Configuration tab and scroll down to the Policy section.- Enable Enforce Policy.
- Enable Policy for Windows Login.
- Click Save.
![]()
Enable IdP Enforcement in the Prisma Access Console- In the Strata Cloud Manager, navigate to Workflows → Prisma Access Setup → Prisma BrowserConfiguration → Prisma Browser → Onboarding .In the Onboard Users section, Locate Prisma Browser and click View.In the Prisma Browser Setup page, click Step 4: Enforce SSO Applications.Select the appropriate IdP. In this case, click PingOne.From this point on, users will only be able to access the SSO applications via the Prisma Browser
Configure JumpCloud Based IP Enforcement
Follow these steps to limit access to all or specific apps to the Prisma Browser when you use JumpCloud. - Configure the Prisma Browser Application Enforcement. In the JumpCloud Admin Portal, perform the following steps:
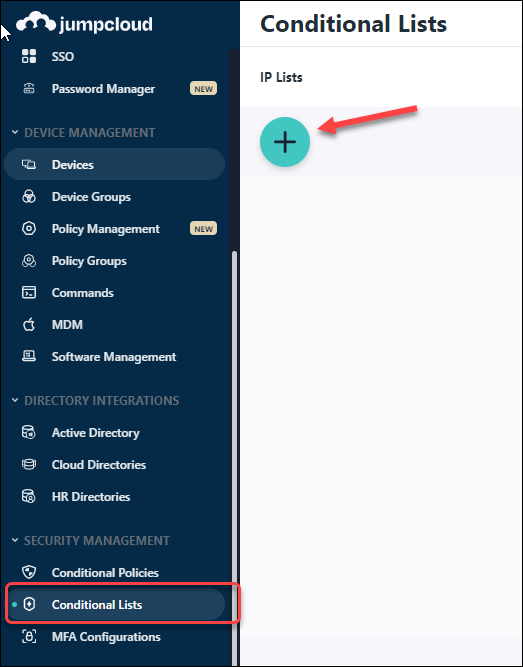
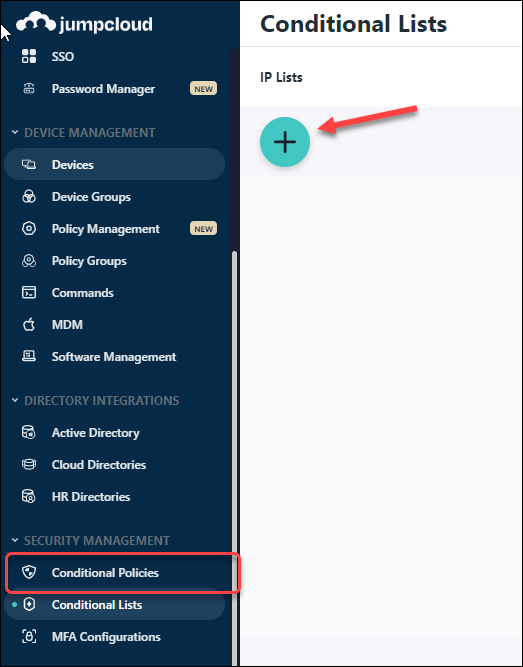
- Select Security Management -> Conditional Lists and click the +.
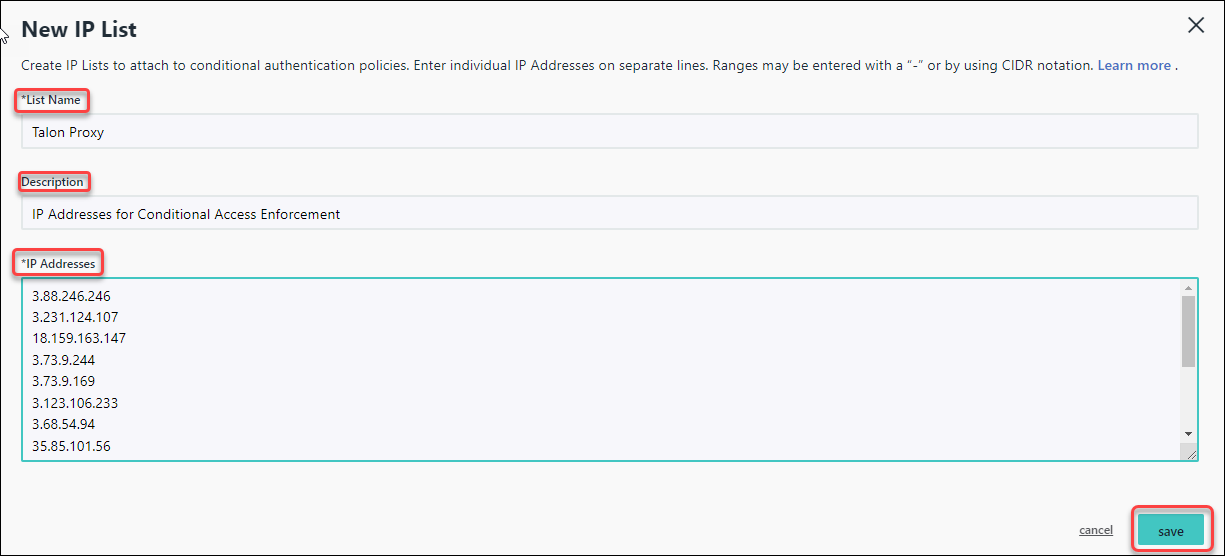
![]() In the New IP List, enter the following information:
In the New IP List, enter the following information:- List Name - Prisma Access Authentication Proxy.
- Description - Enter an optional description for the list.
- IP Addresses - Enter the list of egress IP addresses.
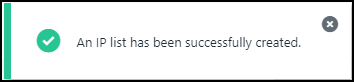
Click Save.![]() A message will display indicating that the list was created.
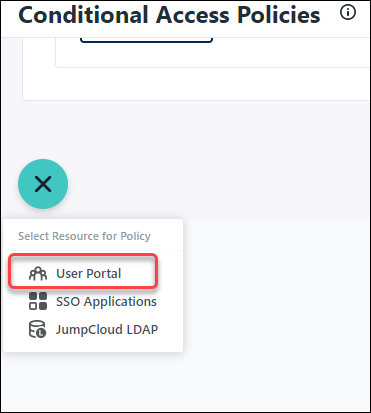
A message will display indicating that the list was created.![]() Select Security Management -> Conditional Policies and click the +.
Select Security Management -> Conditional Policies and click the +.![]() Click User Portal.
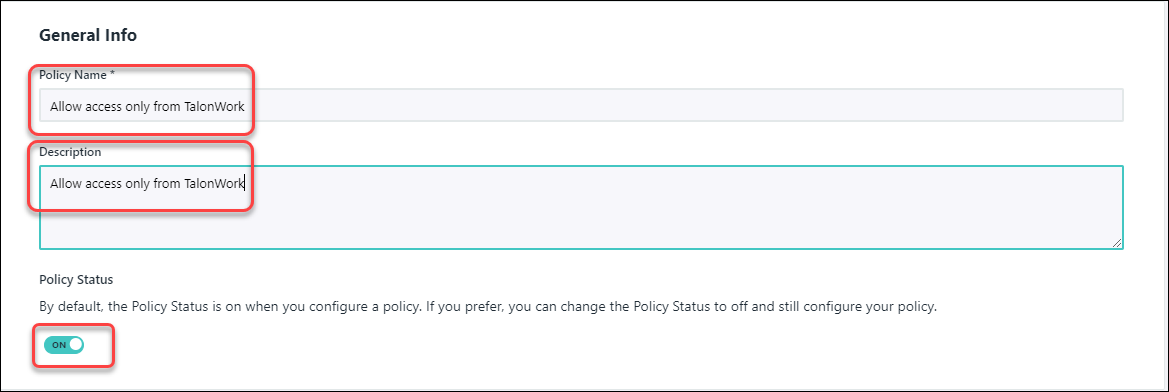
Click User Portal.![]() In the General Info section, enter the following information:
In the General Info section, enter the following information:- Policy Name - Enter a name for the policy, for example - Allow access only from the Prisma Browser.
- Description - Enter an optional description.
- Policy Status - Make sure that this is set to 'On'.
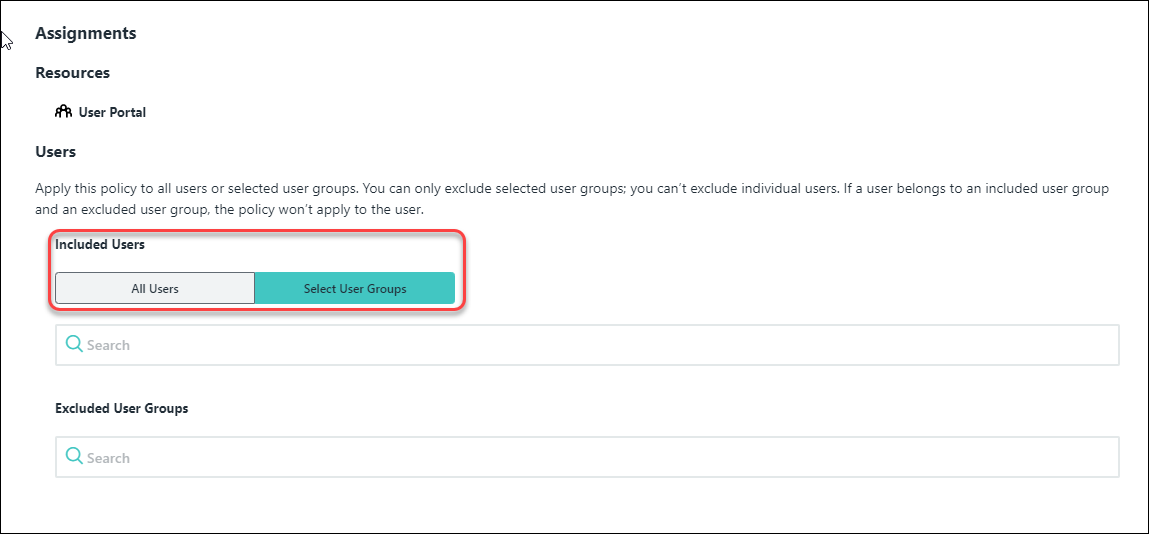
![]() In the Assignments section, click All Users or Select User Groups.
In the Assignments section, click All Users or Select User Groups.![]() Admins can select All Users or individual user groups. Additionally, admins can select groups that are to be excluded from the policy.For example, the policy can be applied to all users, but the admins can be excluded.In the Conditions section, do the following:
Admins can select All Users or individual user groups. Additionally, admins can select groups that are to be excluded from the policy.For example, the policy can be applied to all users, but the admins can be excluded.In the Conditions section, do the following:- Click Add conditions and select IP addresses.
- IP address: Select not on list, and for the list - select Prisma Access Authentication Proxy.
In the Action section, enter the following information:- For Access, select Denied.
- For Authentication, select based on your corporate policy.
![]() Enable IdP Enforcement in the Prisma Access Console
Enable IdP Enforcement in the Prisma Access Console- In the Strata Cloud Manager, navigate to Workflows → Prisma Access Setup → Prisma BrowserConfiguration → Prisma Browser → Onboarding .In the Onboard Users section, Locate Prisma Browser and click View.In the Prisma Browser Setup page, click Step 4: Enforce SSO Applications.Select the appropriate IdP. In this case, click JumpCloud.From this point on, users will only be able to access the SSO applications via the Prisma Browser
Configure VMware Workspace ONE IP Based Enforcement
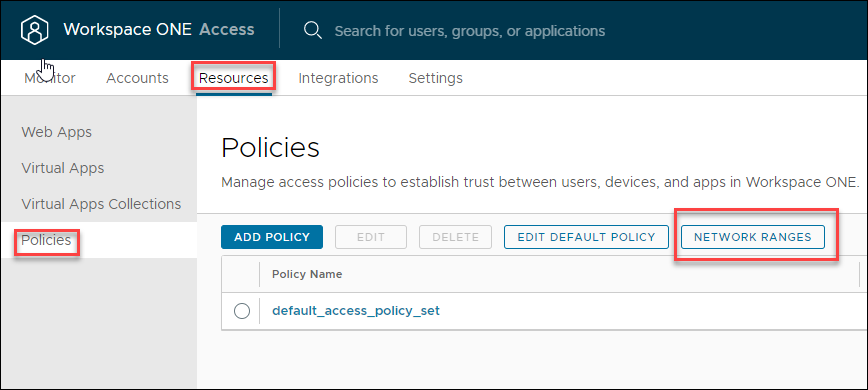
Follow these steps to limit access to all or specific apps to the Prisma Browser when you use VMware Workspace ONE. - Configure the Prisma Browser Application Enforcement. In the Main Access Portal page, perform the following steps:
- On the main Access Portal page, select Resources -> Policies, and click Network Ranges.
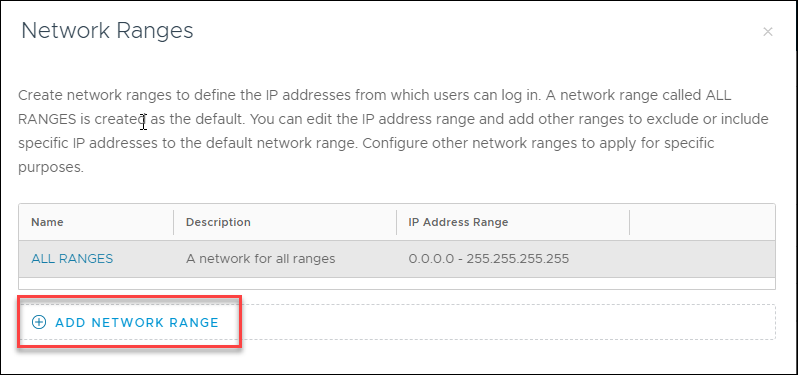
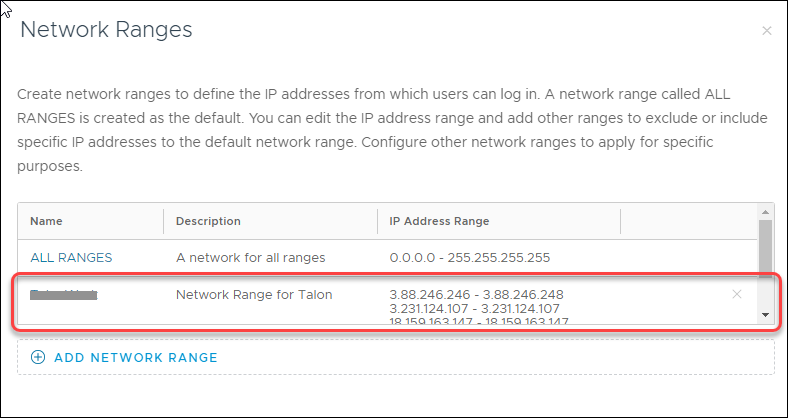
![]() Click Add Network Range.
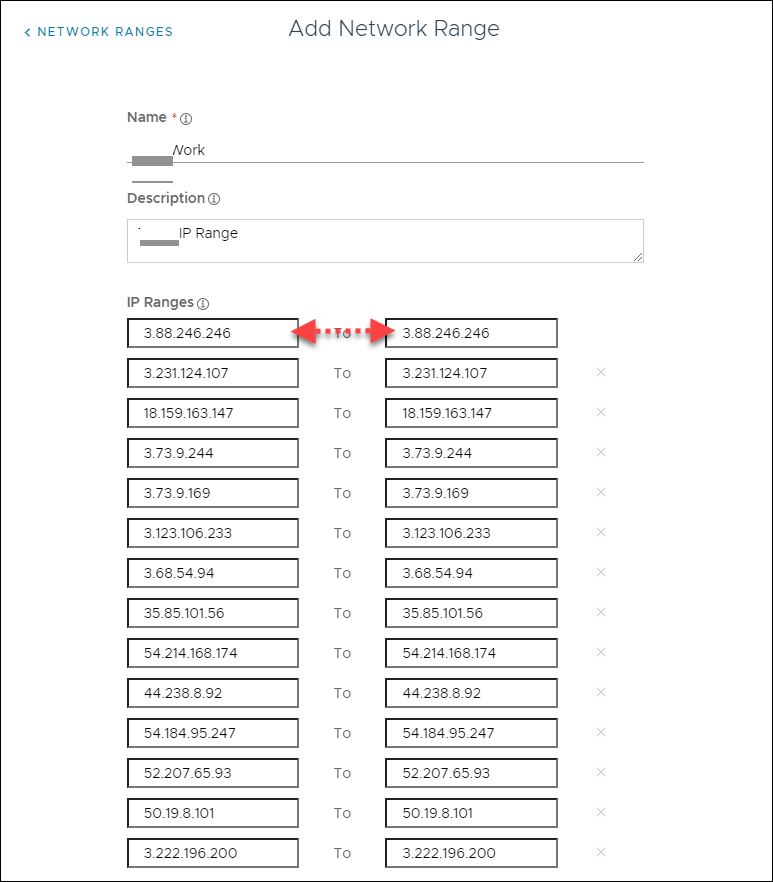
Click Add Network Range.![]() Enter a Name and Description for the Network Range.manualle enter each row of the egress IP addresses.The values must be entered as "from -to" without including the subnet mask.
Enter a Name and Description for the Network Range.manualle enter each row of the egress IP addresses.The values must be entered as "from -to" without including the subnet mask.![]() Click Save. The new Network Range will be added to the list.
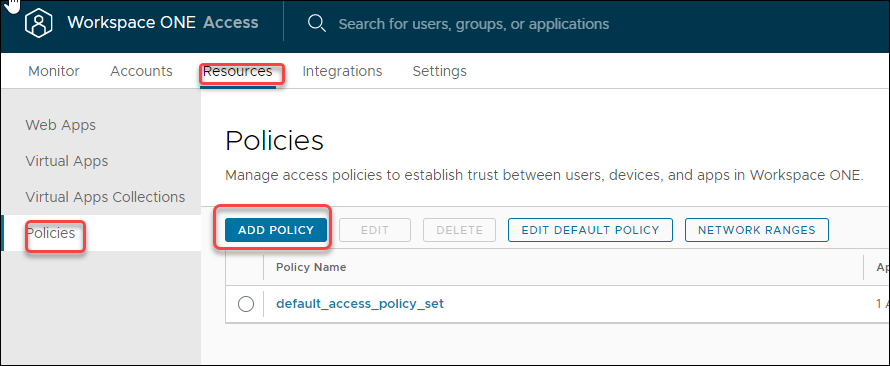
Click Save. The new Network Range will be added to the list.![]() Select Applications and User Group to Adhere to Policy
Select Applications and User Group to Adhere to Policy- On the main Access Portal page, select Resources -> Policies, and click Add Policy.
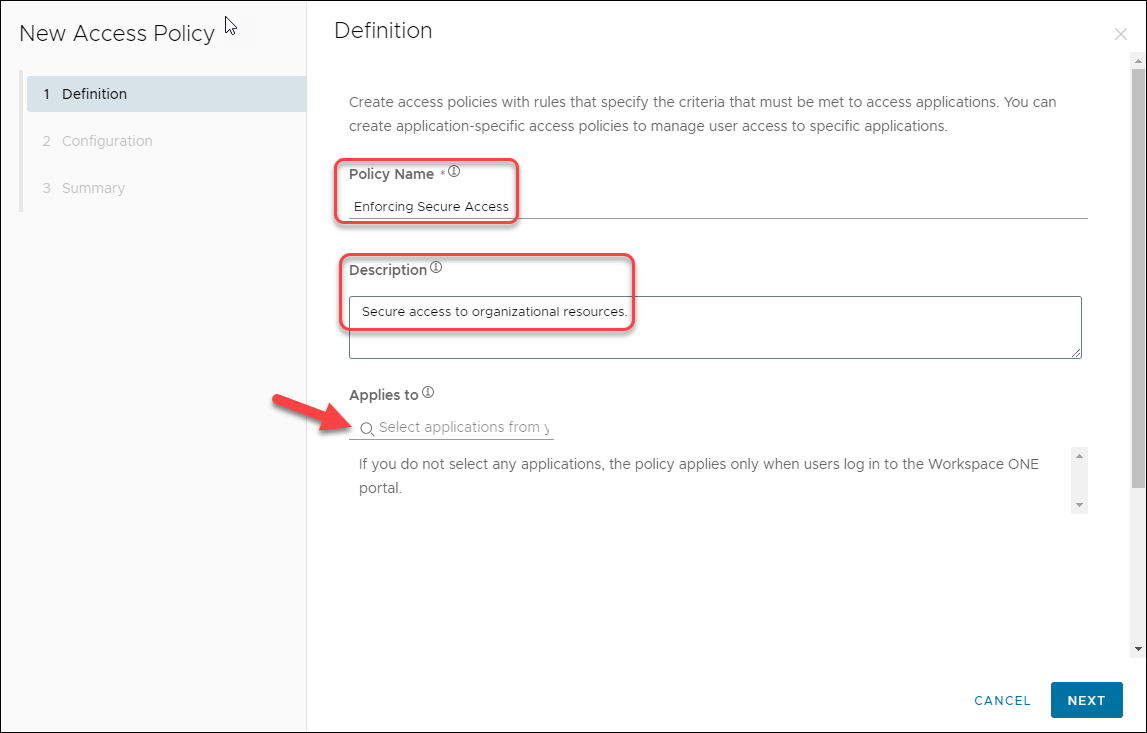
![]() On the Definition page, enter a name and a description for the Policy.Select the relevant application in the Applies to field.
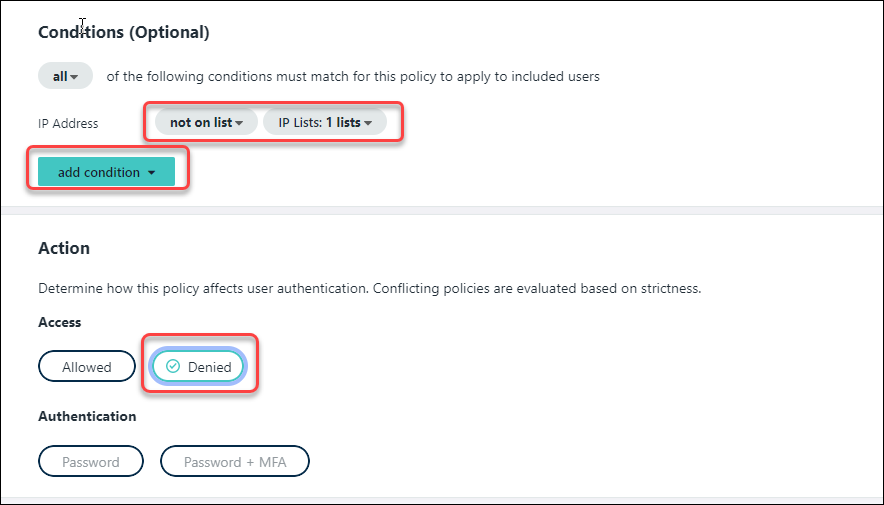
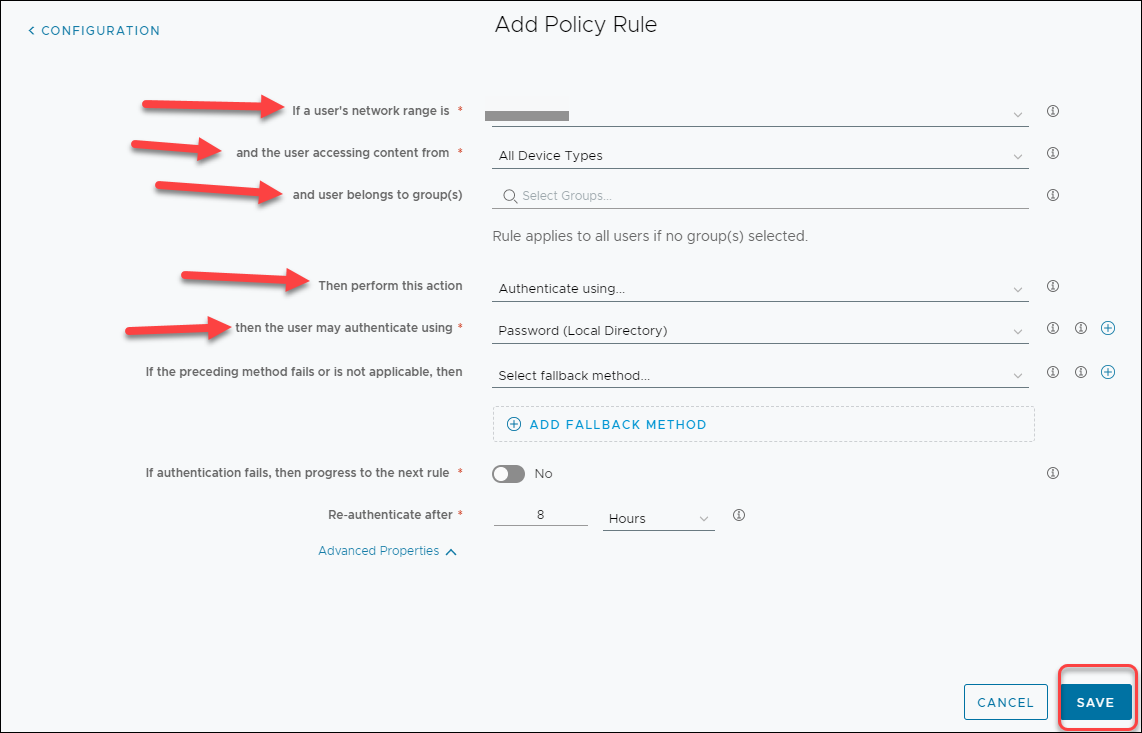
On the Definition page, enter a name and a description for the Policy.Select the relevant application in the Applies to field.![]() The Prisma Browser cannot be a required application for enforcement.Click Next.On the Configuration page, click Add Policy Rule, and provide the following information:
The Prisma Browser cannot be a required application for enforcement.Click Next.On the Configuration page, click Add Policy Rule, and provide the following information:- If a user's network range is - Select the Range Name defined in the previous step.If a user's network range is – Select the Range Name defined in the previous step.
- and the user accessing content from – All Device Types.
- and the user belongs to a group – Select the affected group (optional).
- Then perform this action – Authenticate using…
- then the user may authenticate using – Password (Local Directory)
![]() Click Save. The new policy will be displayed,Click Next and review the New Access Policy Summary.Click Save. The new policy will be added to the policy list.Enable IdP Enforcement in the Prisma Access Console
Click Save. The new policy will be displayed,Click Next and review the New Access Policy Summary.Click Save. The new policy will be added to the policy list.Enable IdP Enforcement in the Prisma Access Console- In the Strata Cloud Manager, navigate to Workflows → Prisma Access Setup → Prisma BrowserConfiguration → Prisma Browser → Onboarding .In the Onboard Users section, Locate Prisma Browser and click View.In the Prisma Browser Setup page, click Step 4: Enforce SSO Applications.Select the appropriate IdP. In this case, click