Prisma Access
Configure General Global Settings for Prisma Access Agents
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Configure General Global Settings for Prisma Access Agents
Configure general global agent settings such as the antitamper password and
authentication override.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
You can customize the global agent settings that apply to Prisma
Access Agents across all endpoints.
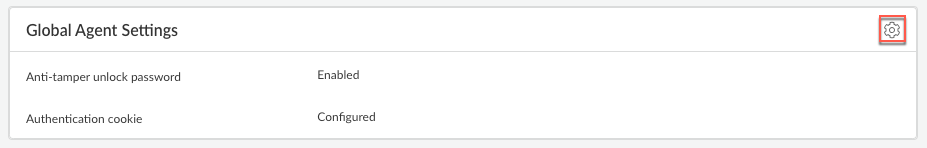
- From Strata Cloud Manager, select ConfigurationNGFW and Prisma AccessConfiguration ScopeAccess AgentSetupPrisma Access Agent.Edit the Global Agent Settings by selecting the gear icon.
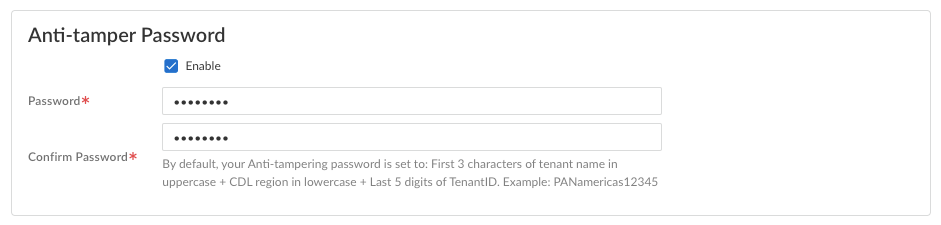
![]() Select General.Configure an anti-tamper unlock password.You can safeguard the Prisma Access Agent by enabling the anti-tamper feature, which prevents any unauthorized user from tampering with the Prisma Access Agent. The anti-tamper feature can protect the following Prisma Access Agent resources on your endpoints:
Select General.Configure an anti-tamper unlock password.You can safeguard the Prisma Access Agent by enabling the anti-tamper feature, which prevents any unauthorized user from tampering with the Prisma Access Agent. The anti-tamper feature can protect the following Prisma Access Agent resources on your endpoints:- Prisma Access Agent folders and files—Unauthorized users cannot delete or rename any Prisma Access Agent-related files and folders.
- Prisma Access Agent services and host information profile (HIP) processes—Unauthorized users cannot stop any Prisma Access Agent-related services and HIP processes. The HIP processes collect information about the host that the Prisma Access Agent is running on and submits the host information to Prisma Access for inspection. If a user tries to stop a process, they must supply the anti-tamper unlock password.
- Prisma Access Agent Registry keys (on Windows) or .plist file (on macOS)—Unauthorized users cannot delete or update the Windows Registry keys or .plist file for the Prisma Access Agent.
- The PACli command-line interface—Unauthorized users cannot disable the Prisma Access Agent or the anti-tamper feature using the PACli command-line interface. Administrators and authorized users who need to perform certain actions for troubleshooting at the command line must provide the anti-tamper unlock (supervisor) password when prompted.
To unlock the anti-tamper feature to troubleshoot the Prisma Access Agent, you need to set up an anti-tamper unlock password (also known as the supervisor password).- Enable the anti-tamper unlock password.If you don't enable the anti-tamper password, no password is assigned, and a user can enter any password (including an empty password) when prompted at the Prisma Access Agent command line.If you disable the anti-tamper password after enabling it, users can run certain PACli commands on the agent, such as the pacli disable, pacli hip status, pacli protect disable, and pacli switchto GlobalProtect commands, without providing the supervisor password. They only need to press Enter when prompted for the password.Enter the Password, and then Confirm Password by reentering the password. The password must have a minimum of eight alphanumeric characters.
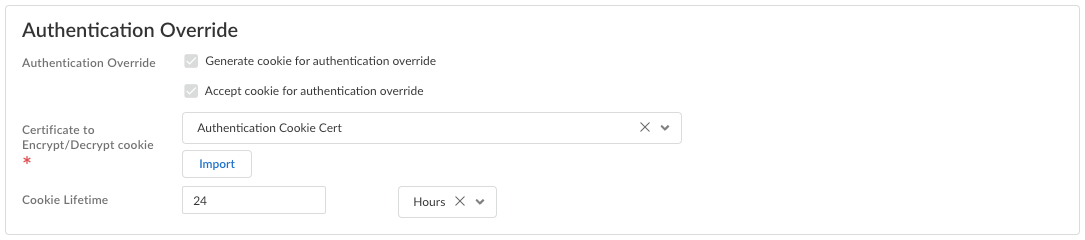
![]() As a best practice, set up the anti-tamper unlock password the first time you configure Prisma Access Agent.Configure Authentication Override settings to allow Prisma Access to generate and accept secure, encrypted cookies for user authentication. Authentication override allows the user to provide login credentials only once during the specified Cookie Lifetime.
As a best practice, set up the anti-tamper unlock password the first time you configure Prisma Access Agent.Configure Authentication Override settings to allow Prisma Access to generate and accept secure, encrypted cookies for user authentication. Authentication override allows the user to provide login credentials only once during the specified Cookie Lifetime.![]()
- Generate cookie for authentication override—Enables Prisma Access to generate encrypted endpoint-specific cookies and issue authentication cookies to the endpoint.
- Accept cookie for authentication override—Enables Prisma Access to authenticate users with a valid, encrypted cookie. When the app presents a valid cookie, Prisma Access verifies that the cookie was encrypted by Prisma Access originally, decrypts the cookie, and then authenticates the user.
- Certificate to Encrypt/Decrypt Cookie—Select an RSA certificate to use to encrypt and decrypt the cookie.
- Cookie Lifetime—Specifies the hours, days, or weeks for which the cookie is valid (default is 24 hours). The range for hours is 1-72; the range for weeks is 1-52; and the range for days is 1-365. After the cookie expires, the user must reenter their login credentials. Prisma Access then encrypts a new cookie to send to the agent. This value can be the same as or different from the cookie lifetime that you configure.
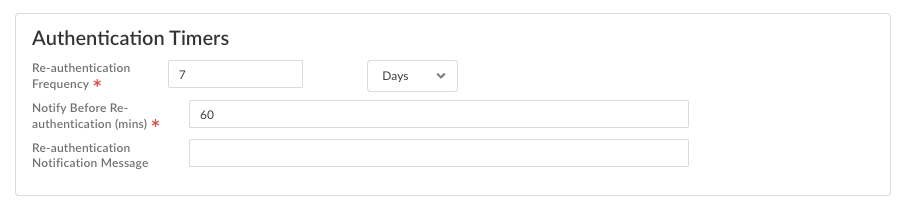
Configure authentication timers that enable you to control when and how frequently users must re-authenticate when accessing resources through the agent.- Re-authentication Frequency—Define the frequency that determines how often users must provide their credentials. This frequency applies globally across your deployment and directly controls the user refresh token lifetime. You can enter a value 10 hours and 30 days. (Default: 7 days)
- Notify Before Re-authentication—Specify a notification timer that alert users before their authentication expires. You specify how many minutes in advance users receive warnings, with a range of 5 to 120 minutes. (Default: 60 minutes)
- Re-authentication Notification Message—Customize the notification message that displays to users. If you leave the re-authentication notification message empty, the agent displays a default message. You can enter custom text with a maximum of 127 characters.
![]() Block Login for Quarantined Devices to prevent Prisma Access Agent users from logging in from quarantined devices.If a user attempts to log in from a quarantined device when this setting is enabled, the Prisma Access Agent notifies the user that the device is quarantined and the user cannot log in from that device. If this setting is not enabled, the user receives the notification but is able to log in from that device.The Block Login for Quarantined Devices setting applies to both Prisma Access Agent and GlobalProtect. Any changes you make will be reflected and used for GlobalProtect, and vice versa.Save your settings.
Block Login for Quarantined Devices to prevent Prisma Access Agent users from logging in from quarantined devices.If a user attempts to log in from a quarantined device when this setting is enabled, the Prisma Access Agent notifies the user that the device is quarantined and the user cannot log in from that device. If this setting is not enabled, the user receives the notification but is able to log in from that device.The Block Login for Quarantined Devices setting applies to both Prisma Access Agent and GlobalProtect. Any changes you make will be reflected and used for GlobalProtect, and vice versa.Save your settings.