Prisma Access
Configure the Prisma Access Service Infrastructure (Strata Cloud Manager)
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Configure the Prisma Access Service Infrastructure (Strata Cloud Manager)
Learn how to set up service infrastructure in Prisma Access (Managed by Strata Cloud Manager).
Use the following recommendations and requirements when you add an infrastructure
subnet for Prisma Access:
- Use an RFC 1918-compliant subnet. While the use of non-RFC 1918-compliant (public) IP addresses is supported, we don't recommend it because of possible conflicts with the internet public IP address space.
- Do not specify any subnets that overlap with the 169.254.0.0/16 and 100.64.0.0/10 subnet range because Prisma Access reserves those IP addresses and subnets for its internal use.
- This subnetwork is an extension to your existing network and therefore, cannot overlap with any IP subnets that you use within your corporate network or with the IP address pools that you assign for Prisma Access for users or Prisma Access for networks.
- Because the service infrastructure requires a large number of IP addresses, you must designate a /24 subnetwork (for example, 172.16.55.0/24).
- If you use dynamic routing for your remote networks or service connections, you must also configure an RFC 6996-compliant BGP Private AS number.
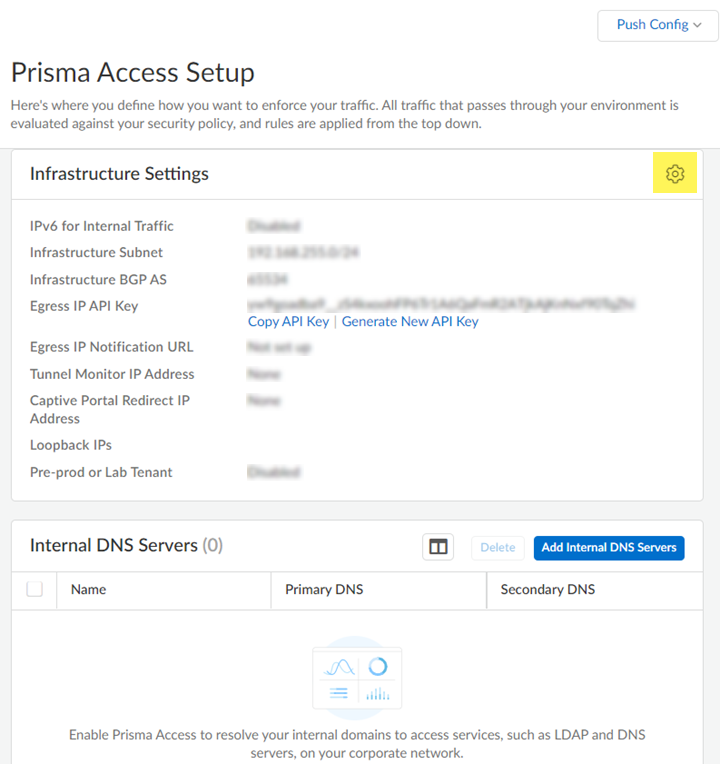
- Launch Prisma Access.Go to ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma Access InfrastructureInfrastructure Settings and click the gear to edit the settings.
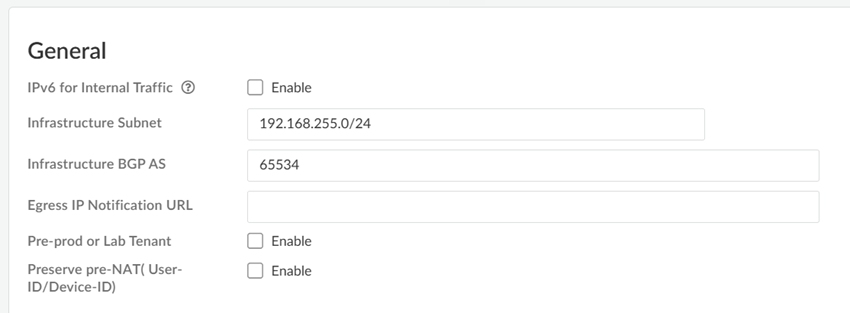
![]() Enter an Infrastructure Subnet that Prisma Access can use to enable communication between your remote network locations, mobile users, and the HQ or data centers that you plan on connecting to Prisma Access over service connections.Use an RFC 1918-compliant subnet for the infrastructure subnet. While the use of non-RFC 1918-compliant (public) IP addresses is supported, we don't recommend it because of possible conflicts with the internet public IP address space.(Optional) If you are configuring IPv6, select IPv6 for Internal Traffic and select an IPv6 subnet.Enter the Infrastructure BGP AS you want to use within the Prisma Access infrastructure.If you want to enable dynamic routing so that Prisma Access can dynamically discover routes to resources in your remote networks and HQ or data center locations, you must use the Border Gateway Protocol (BGP). The Infrastructure BGP AS is the autonomous system (AS) number that identifies the routes through which BGP can send traffic. If you do not supply an AS number, Prisma Access uses the default AS number (65534).If you want to specify your own AS number, you must use an RFC 6996-compliant private AS number. Accepted formats are 4-Byte AS Plain [64512-65534],[4200000000-4294967294] or AS Dot [0.64512-0.65534], [64086.59904-65535.65534] notation.If you enable your users to access applications based on source IP address, you will need to get the list of IP addresses that traffic from Prisma Access uses as the source address so that you can allow them in your application access policies.Copy the Egress IP API Key to enable use of the Prisma Access Egress IP Address API. Also, because the IP addresses that Prisma Access uses change periodically—for example when you add a new location, when Prisma Access needs to scale resources in an existing location, or when there is an infrastructure upgrade—you need to know when the IP addresses change so that you can update your policy rules, or automate these updates by defining a Egress IP Notification URL. See Retrieve the IP Addresses for Prisma Access for more details.(Optional) Enable the tenant as a pre-production or lab tenant.
Enter an Infrastructure Subnet that Prisma Access can use to enable communication between your remote network locations, mobile users, and the HQ or data centers that you plan on connecting to Prisma Access over service connections.Use an RFC 1918-compliant subnet for the infrastructure subnet. While the use of non-RFC 1918-compliant (public) IP addresses is supported, we don't recommend it because of possible conflicts with the internet public IP address space.(Optional) If you are configuring IPv6, select IPv6 for Internal Traffic and select an IPv6 subnet.Enter the Infrastructure BGP AS you want to use within the Prisma Access infrastructure.If you want to enable dynamic routing so that Prisma Access can dynamically discover routes to resources in your remote networks and HQ or data center locations, you must use the Border Gateway Protocol (BGP). The Infrastructure BGP AS is the autonomous system (AS) number that identifies the routes through which BGP can send traffic. If you do not supply an AS number, Prisma Access uses the default AS number (65534).If you want to specify your own AS number, you must use an RFC 6996-compliant private AS number. Accepted formats are 4-Byte AS Plain [64512-65534],[4200000000-4294967294] or AS Dot [0.64512-0.65534], [64086.59904-65535.65534] notation.If you enable your users to access applications based on source IP address, you will need to get the list of IP addresses that traffic from Prisma Access uses as the source address so that you can allow them in your application access policies.Copy the Egress IP API Key to enable use of the Prisma Access Egress IP Address API. Also, because the IP addresses that Prisma Access uses change periodically—for example when you add a new location, when Prisma Access needs to scale resources in an existing location, or when there is an infrastructure upgrade—you need to know when the IP addresses change so that you can update your policy rules, or automate these updates by defining a Egress IP Notification URL. See Retrieve the IP Addresses for Prisma Access for more details.(Optional) Enable the tenant as a pre-production or lab tenant.- Enable the tenant as Pre-prod or Lab Tenant.
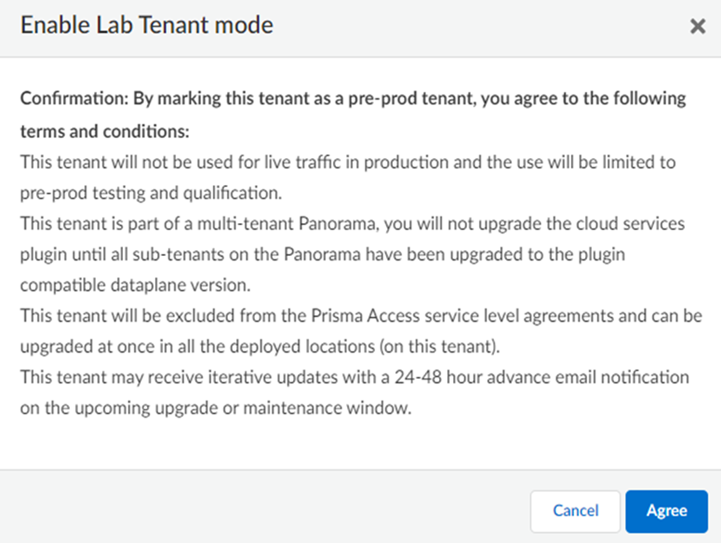
![]() Agree to confirm.
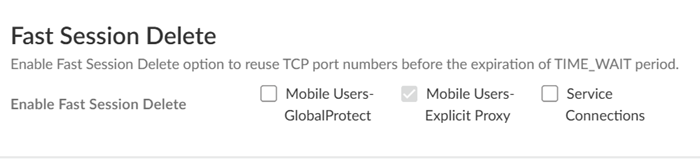
Agree to confirm.![]() When you enable a tenant as a pre-production or lab tenant, you can schedule upgrades for this tenant alone before upgrading other production tenants. The tenant receives notifications 24 to 48 hours before an upcoming upgrade. When you disable the tenant from pre-production or lab tenant, it is considered as a production tenant.(Optional) Select Preserve Pre-NAT to preserve user and device-ID mapping for service connections with a next-generation firewall that use Source NAT.(ZTNA Connector Deployments Only) Set up the ZTNA Connnector Application IP Blocks and Connector IP Blocks.(Optional) To enable Fast-Session delete for Remote Networks, Service Connections, or Mobile Users —GlobalProtect deployments, select the check boxes for Mobile Users—GlobalProtect or Service Connections.Fast-Session Delete allows Prisma Access to reuse TCP port numbers before the TCP TIME_WAIT period expires, and can be useful for SSL decrypted sessions that may be short-lived.For Mobile Users—Explicit Proxy deployments, Fast-Session delete is a key part of its functionality and you cannot disable it.
When you enable a tenant as a pre-production or lab tenant, you can schedule upgrades for this tenant alone before upgrading other production tenants. The tenant receives notifications 24 to 48 hours before an upcoming upgrade. When you disable the tenant from pre-production or lab tenant, it is considered as a production tenant.(Optional) Select Preserve Pre-NAT to preserve user and device-ID mapping for service connections with a next-generation firewall that use Source NAT.(ZTNA Connector Deployments Only) Set up the ZTNA Connnector Application IP Blocks and Connector IP Blocks.(Optional) To enable Fast-Session delete for Remote Networks, Service Connections, or Mobile Users —GlobalProtect deployments, select the check boxes for Mobile Users—GlobalProtect or Service Connections.Fast-Session Delete allows Prisma Access to reuse TCP port numbers before the TCP TIME_WAIT period expires, and can be useful for SSL decrypted sessions that may be short-lived.For Mobile Users—Explicit Proxy deployments, Fast-Session delete is a key part of its functionality and you cannot disable it.![]() Save your changes when complete to return to the main infrastructure page.To enable Prisma Access to resolve your internal domains, Add Internal DNS Servers.If you plan on configuring service connections to enable access to resources in your corporate network and you also need Prisma Access to resolve your internal domains, you must define the list of internal domains. DNS queries for domains in the internal domain list are sent to your local DNS servers to ensure that resources are available to Prisma Access remote network users and mobile users.
Save your changes when complete to return to the main infrastructure page.To enable Prisma Access to resolve your internal domains, Add Internal DNS Servers.If you plan on configuring service connections to enable access to resources in your corporate network and you also need Prisma Access to resolve your internal domains, you must define the list of internal domains. DNS queries for domains in the internal domain list are sent to your local DNS servers to ensure that resources are available to Prisma Access remote network users and mobile users.- Enter the Primary DNS server and Secondary DNS server that Prisma Access should use to resolve the internal domain names.Add the internal Domain Names that you want Prisma Access to resolve.You can use a wildcard (*) in front of the domains in the domain list, for example *.acme.local or *.acme.com.Push Config to save your service infrastructure settings to Prisma Access.