Prisma Access
CloudHSM Support on Prisma Access
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
CloudHSM Support on Prisma Access
Integrate your AWS CloudHSM infrastructure with Prisma Access to store and manage
your keys in an HSM within the AWS cloud.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Prisma® Access supports Amazon Web Services™ (AWS) CloudHSM hardware security
module (HSM) integration, enhancing your ability to secure cryptographic keys and
operations. With AWS CloudHSM support, you can integrate your AWS CloudHSM
infrastructure with Prisma Access, enabling you to store and manage private keys you
need for the digital certificate signing operations required for SSL decryption within
the AWS cloud. You can deploy the AWS CloudHSM solution in multiple AWS cloud regions
data center locations for high availability and performance, and integrate with PA
mobile users, remote networks, and explicit proxy services for SSL decryption. You need
to own and manage the AWS CloudHSM cluster and HSM instances, and create a secure
channel between service connection and HSM cluster for TLS connection between the Prisma
Access security processing nodes (SPNs) and HSM cluster for signing requests.
The SSL decryption functionality on Prisma Access mandates that you bring your own public
key infrastructure (PKI) to the platform or create a new self-signed PKI within Prisma
Access. This feature requires an issuing certificate authority (CA) or forward trust
certificate (consisting of public and private keys) to generate new certificates for
visited sites and domains. Prisma Access requires that all cryptographic secrets,
including the TLS certificate private keys needed for SSL decryption, are stored inside
the configuration file that resides on the Prisma Access service infrastructure and on
each SPN that is part of the tenant. Some Prisma Access customers prefer not to provide
the TLS private keys on PA infrastructure or reside on PA SPNs for SSL decryption
operations (security and compliance requirements).
Integration with AWS CloudHSM solutions securely stores the private key of the issuing CA
certificate. Your users might choose not to input TLS private keys in the configuration
but prefer integrating with their CloudHSM solution to access private keys essential for
digital certificate signing operations for SSL decryption. They might deploy HSM
solutions in clusters of two or more appliances across multiple cloud regions for
enhanced availability and performance.
To understand how AWS CloudHSM integrates with Palo Alto Networks Prisma Access, you
should be familiar with these terms:
- Hardware Security Module (HSM) — A physical computing device that generates, stores, and protects cryptographic keys within a tamper-resistant environment. HSMs safeguard sensitive data by securing the keys used for encryption, decryption, and digital signatures.
- Security Processing Node (SPN) — A component within the Prisma Access™ infrastructure responsible for applying security policies, including SSL decryption. SPNs act as clients to the AWS CloudHSM, performing cryptographic operations by sending requests to the HSM rather than retrieving private keys.
- Availability Zone (AZ) — A distinct, isolated location within an AWS region. Each availability zone is engineered to be independent of others, providing high availability and redundancy for services deployed across multiple availability zones, such as an AWS CloudHSM cluster.
Before You Configure CloudHSM on Prisma Access
Before you configure CloudHSM support on Prisma Access, you need to:
Configure CloudHSM Support in Panorama
To configure CloudHSM support in Prisma Access Panorama, complete the following
steps.
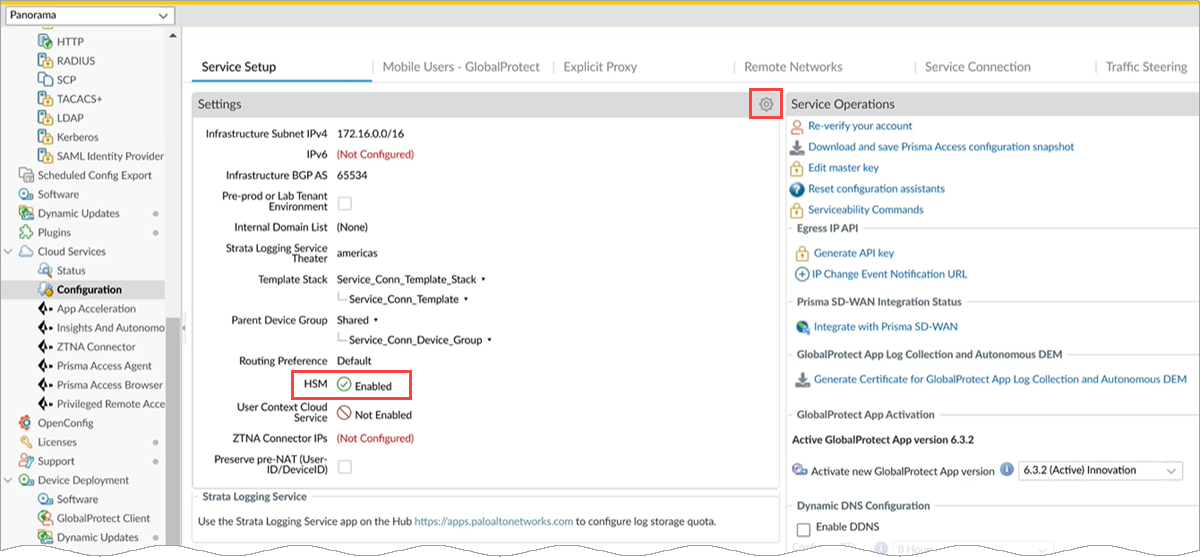
- Go to PanoramaCloud ServicesConfigurationService Setup.HSM Enabled appears when you load the Cloud Services plugin.
![]()
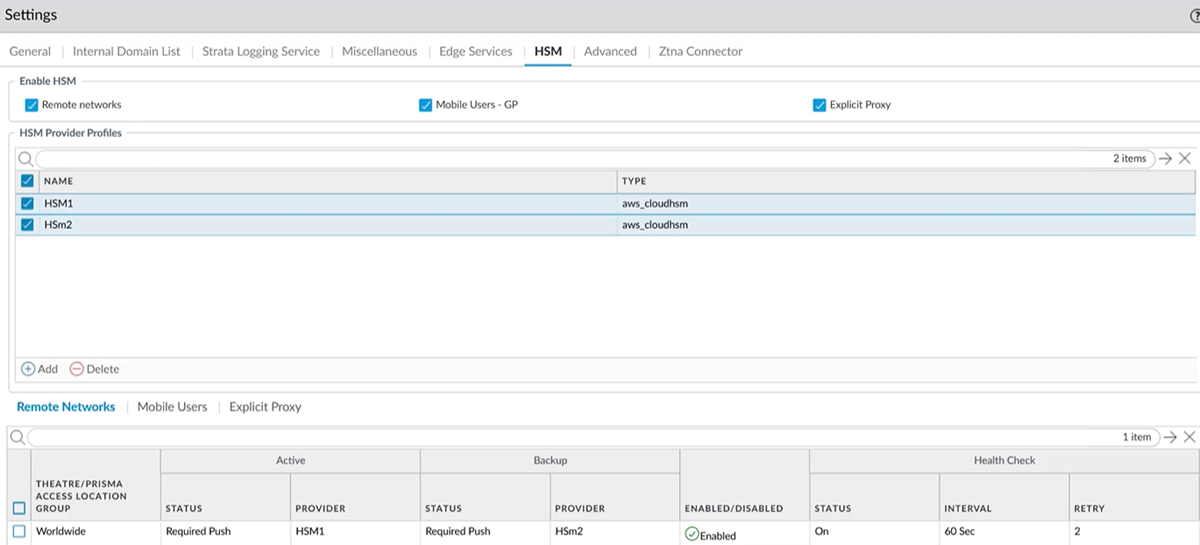
- Select the gear icon, and choose the HSM tab on the Settings page.
- Click the check boxes for Remote Networks,
Mobile Users - GP (GlobalProtect),
Explicit Proxy, or any combination, to configure
global provider profiles on these services.
![]()
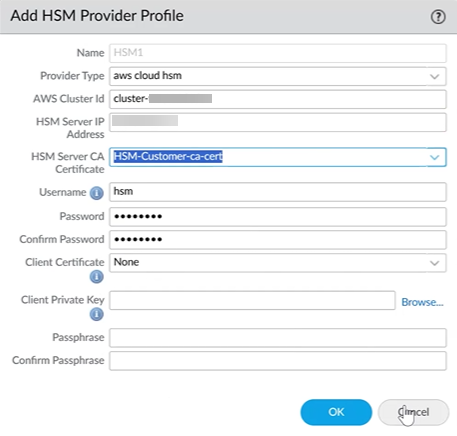
- Click the Add icon to create HSM Provider
Profiles, which are used for the services (remote
networks,mobile users - GP, or Explicit Proxy) you selected:
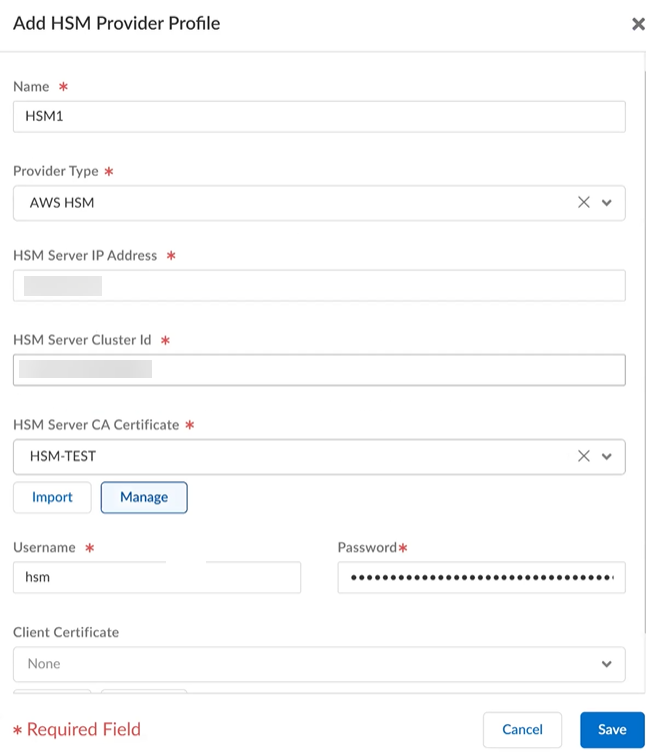
- Name—Give the provider profile a unique name.
- Provider Type—Select aws cloud hsm from the drop-down.
- AWS Cluster ID—Your cluster ID from AWS, which could consist of multiple servers.
- HSM Server IP Address—An HSM server IP address from your AWS cluster.
- HSM Server CA Certificate—Your HSM server CA certificate, which you downloaded from AWS.
- Username—Enter the crypto user credentials from AWS
- Password—Enter your crypto user credentials password, and confirm your password.
- Client Certificate (Optional)—Certificate to authenticate with the HSM cluster. It must be signed by the HSM server CA.
- Client Private Key (Optional)—Passphrase encrypted private key.
- Passphrase (Optional)—Enter the passphrase for your client private key, and confirm your passphrase.
![]()
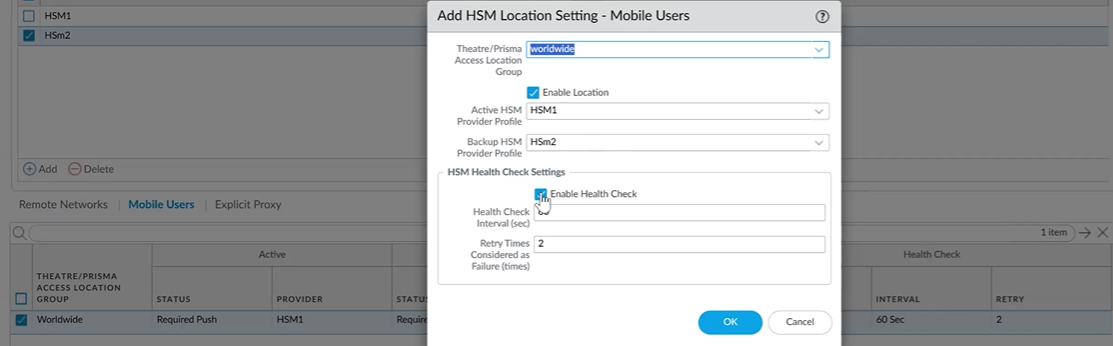
- Configure the HSM Location Setting for each service. The system pushes your configurations to the firewalls provisioned in these location settings, or regions.Click the check box in the Theatre/Prisma Access Location Group column for the service you want to configure. Theatres and Prisma Access Locations you can use are Worldwide; North America & South America; Africa, Europe & Middle East, and Asia, Australia & Japan.
- Active HSM Provider Profile—Select your active HSM provider profile from the drop-down.
- Backup HSM Provider Profile—Select your backup HSM provider profile from the drop-down.
- HSM Health Check Settings—Enable health check by clicking the check box.
![]()
- After you select a Theatre/Prisma Access Location Group, you have the option to Test Network Connectivity for that region. The connectivity test runs on all firewalls you have onboarded based on the region.
Set Up Decryption Policy
All signing requests occur from the CloudHSM server, not locally. To do this, you
need to set up a decryption policy with an CloudHSM private key. The private key
resides in the CloudHSM server and is used for all signing requests from new
customers.
- Go to Device GroupsPoliciesDecryptionPre Rules and select a Device Group from the drop-down.
- Find the Private Key in HSM—Under PanoramaCertificate ManagementCertificatesDevice Certificates, set Location to vsys1, and
find the HSM-Intermediate-CA-Cert under
HSM2-CA-cert in the table. Under the Key column, you see that this certificate is Configured to save on HSM. This is the device certificate used for decryption.
Configure CloudHSM Support in Strata Cloud Manager
To configure CloudHSM support in Strata Cloud Manager, complete the following steps.
- Go to ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessPrisma Access InfrastructurePrisma Access SetupHSM Settings and select the gear icon to open the HSM
Settings page.
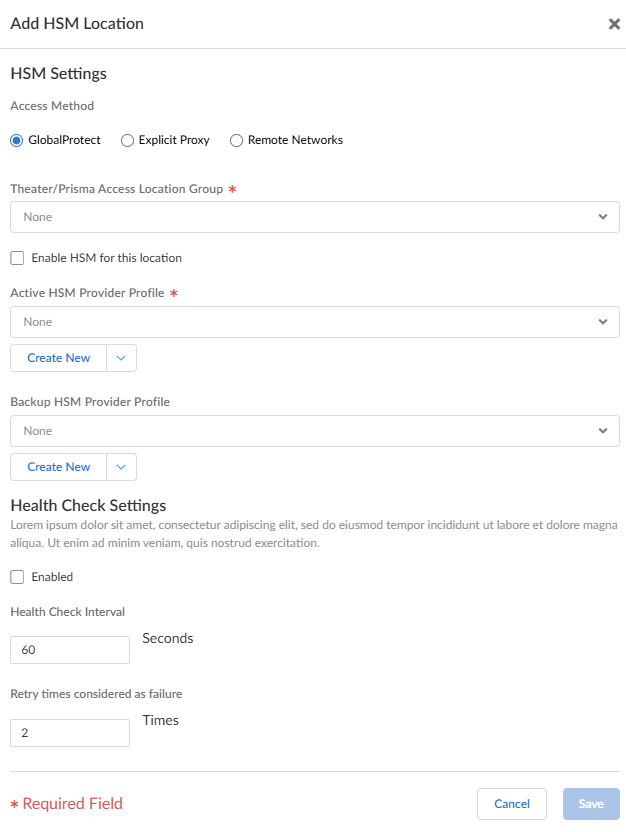
- HSM Locations—Add and configure
HSM Locations for Remote
Networks, Mobile Users - GP,
and Explicit Proxy, or select an existing HSM
location from the table.
- Select a Theatre/Prisma Access Location Group from the drop-down for the service you want to configure. Theatres and Prisma Access Locations you can use are Worldwide; North America & South America; Africa, Europe & Middle East, and Asia, Australia & Japan.
- Click the Enable HSM for this location check box.
- Select an Active HSM Provider Profile from the drop-down, or click Create New to add a new provider profile.
- Health Check Settings—Enable health check by clicking the check box. Enter Health Check Interval in number of seconds, and how many Retry times considered as failure.
- Save your configuration.
![]()
- HSM Provider Profiles—Add an HSM Provider
Profile using your data from AWS. You can have multiple HSM provider profiles.
![]()
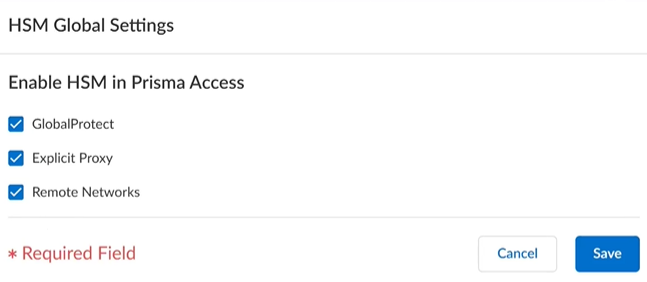
- HSM Global Settings—Select the check boxes
next to the services for which you want to enable HSM in
Prisma Access globally.
![]()
- HSM Locations—Add and configure
HSM Locations for Remote
Networks, Mobile Users - GP,
and Explicit Proxy, or select an existing HSM
location from the table.
- Go to ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessObjectsCertificate Management.
- In the Custom Certificates table, select the certificates you want to import.