Prisma SD-WAN
Validate the AWS Transit Gateway Integration CloudBlade
Table of Contents
Expand All
|
Collapse All
Prisma SD-WAN Docs
-
-
- Prisma SD-WAN Controller
-
- CloudBlade Integrations
- CloudBlades Integration with Prisma Access
-
-
-
-
- 6.5
- 6.4
- 6.3
- 6.1
- 5.6
- Prisma SD-WAN Controller
- Prisma SD-WAN On-Premises Controller
- Prisma SD-WAN CloudBlades
- Prisma Access CloudBlade Cloud Managed
- Prisma Access CloudBlade Panorama Managed
Validate the AWS Transit Gateway Integration CloudBlade
Lets see how to validate the AWS transit gateway integration cloudblade in Prisma SD-WAN.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
The Prisma SD-WAN AWS Transit Gateway Integration CloudBlade
automatically provisions a pair of vIONs in an AWS Connect VPC. The AWS route tables
for the Data Center IONs are updated to establish a GRE tunnel between the AWS DC
vIONs and the Transit Gateway Connect peers. BGP core peering will be established
over the GRE tunnel.
The AWS transit gateway ASN number should not match with the Prisma SD-WAN
default ASN value of 64512.
The following steps can be used to validate if the CloudBlade is working as
intended:
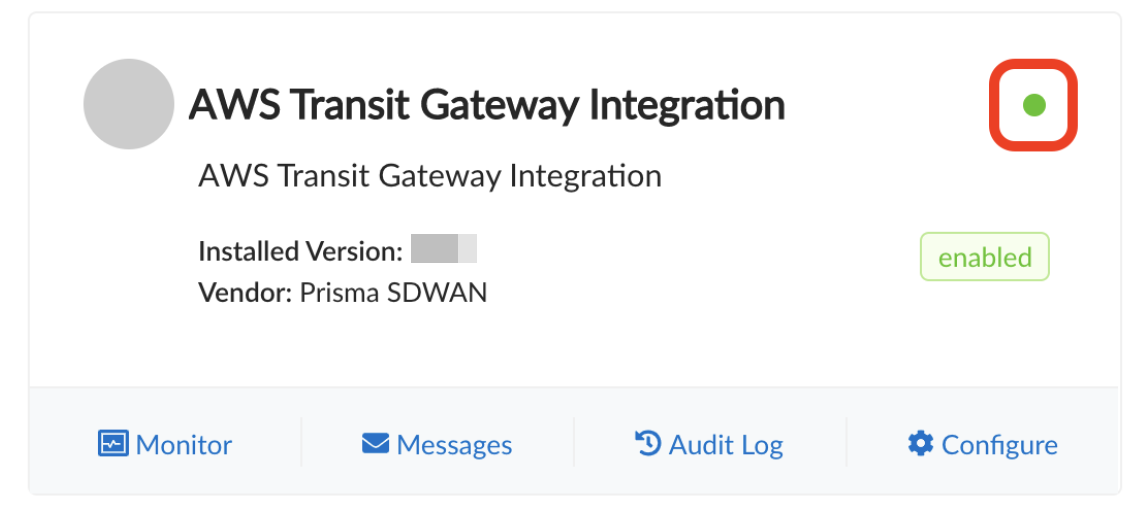
- Check the status indicator on the CloudBlade window.Once enabled and deployed correctly, the status indicator should turn green.
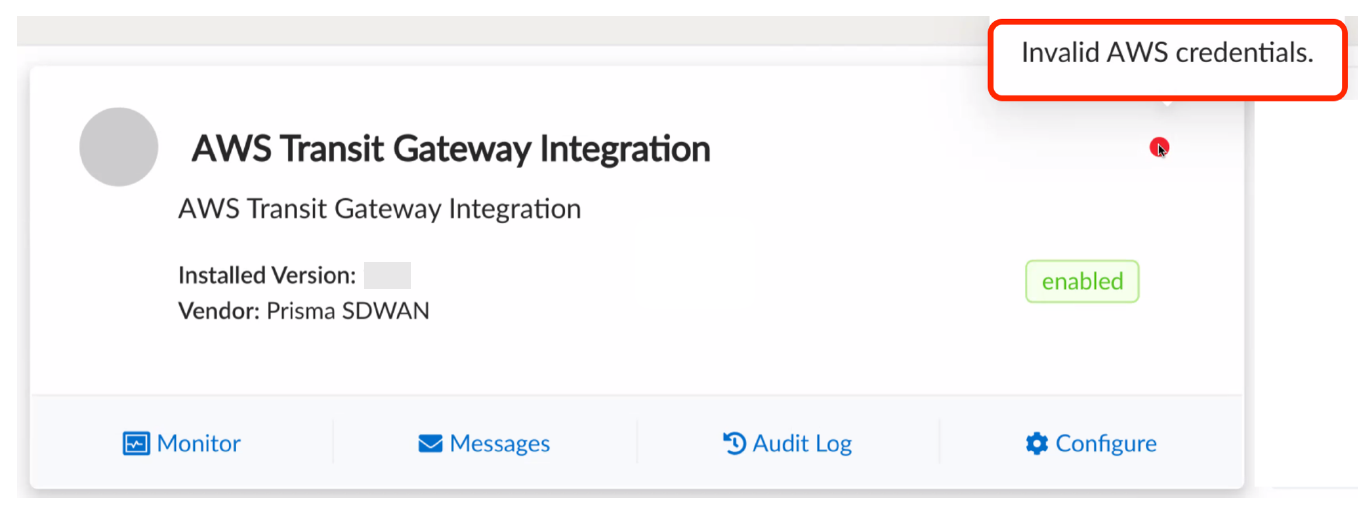
![]() If the access credentials are invalid, the status indicator will throw an Invalid AWS credentials error message.
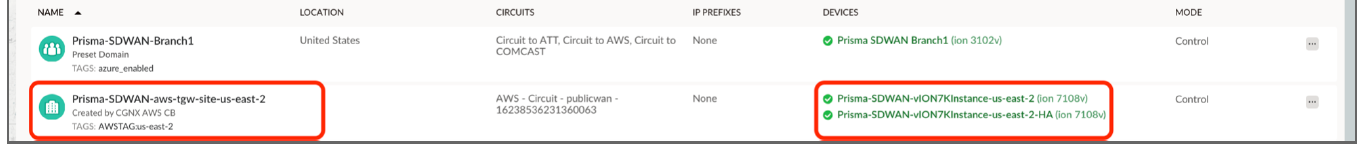
If the access credentials are invalid, the status indicator will throw an Invalid AWS credentials error message.![]() Check if the Prisma SD-WAN data center site has been created in the AWS cloud and if the vION HA pair has been assigned to this site.
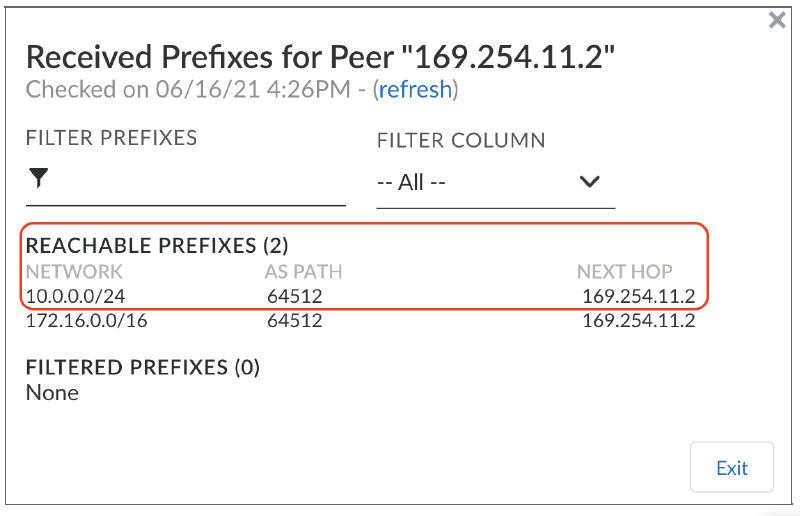
Check if the Prisma SD-WAN data center site has been created in the AWS cloud and if the vION HA pair has been assigned to this site.![]() Go to the Active ION’s Interfaces configuration window and check if the GRE VPN has been created.
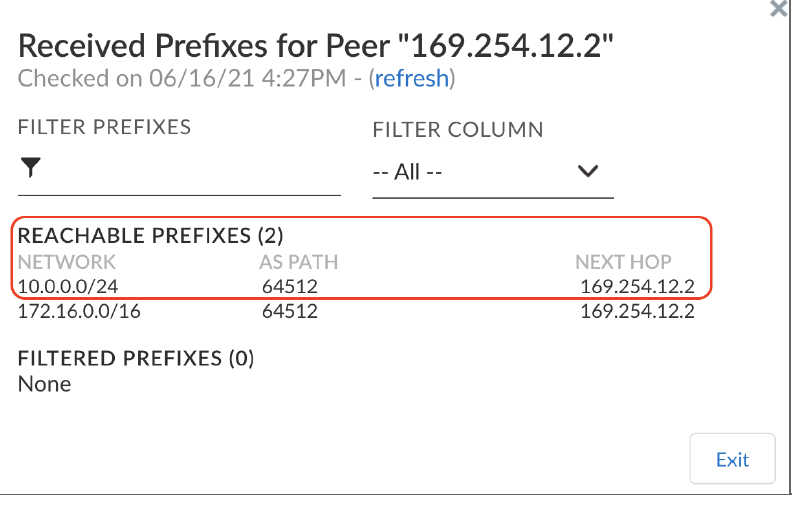
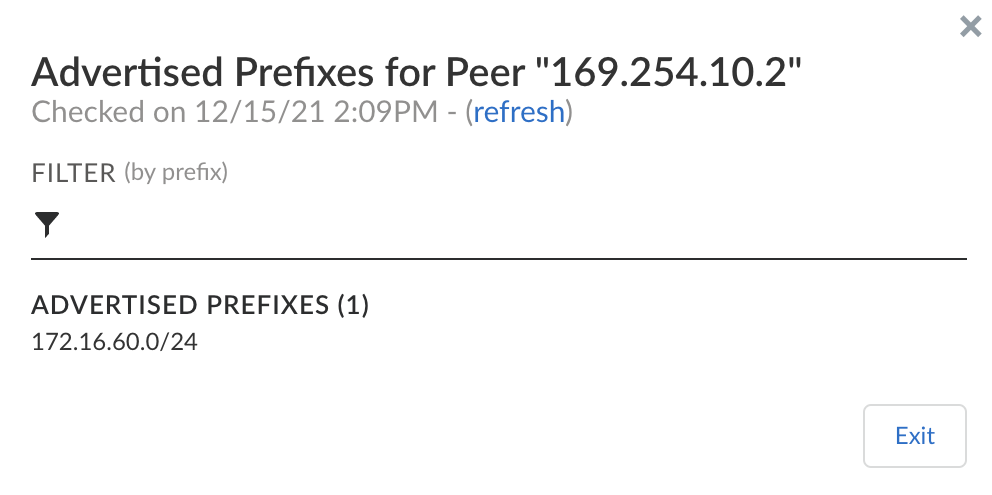
Go to the Active ION’s Interfaces configuration window and check if the GRE VPN has been created.- Click on the interface to check the IP address configuration.Go to the 2nd ION’s interface configuration window and check the GRE tunnel interface configuration.Check if the core BGP peering between each vION and the Transit Gateway Connect peer is UP.Check if both the vIONs have learned the prefixes from the Application VPC behind the AWS Transit Gateway and the active ION has learned and advertised the routes.
![]()
![]()
![]()
Setup Application Path Policy Rules
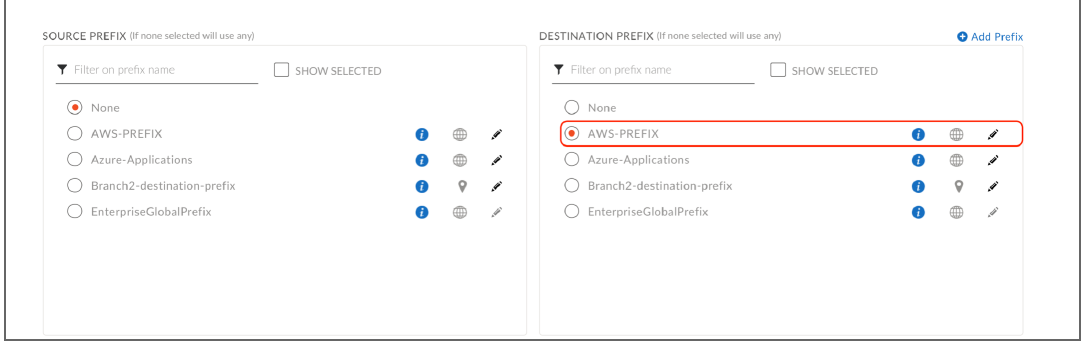
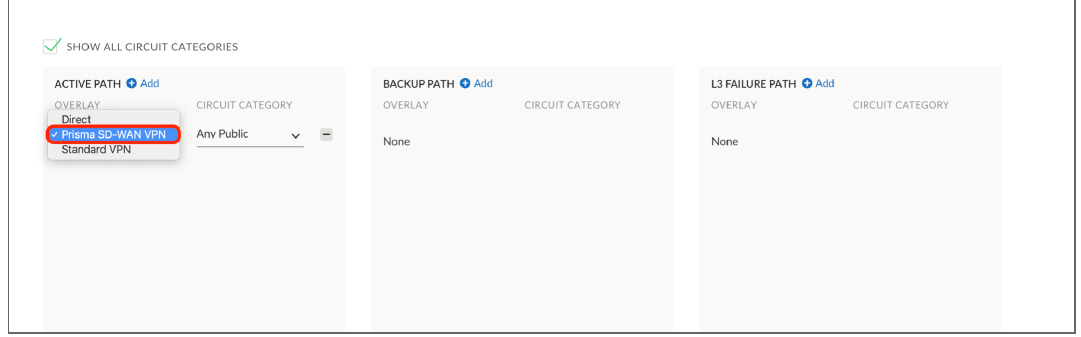
Once the CloudBlade configures the appropriate entities within Prisma SD-WAN, the administrator can configure path policies to allow the ION devices to make intelligent per-app path selections.The Prisma SD-WAN Secure Application Fabric (AppFabric) enables granular controls for virtually an unlimited number of policy permutations down to the sub-application level. Below is an example of configuring a path policy rule to use the Prisma SD-WAN VPN to the AWS DC ION.In Strata Cloud Manager, go ConfigurationPrisma SD-WANPoliciesPaths and choose a policy set of interest. Within the policy set, click the Add Rule and define the following: name, network contexts, destination, prefixes or apps of interest (or a combination of both apps and prefixes), active and backup paths, and service and DC groups.In this example, we will use a destination prefix-based rule since we have already defined a path prefix that matches the IP address of the service running in the AWS Application VPC.![]()
![]()