Prisma Access
Set Up Syslog Forwarding to Microsoft Sentinel
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Set Up Syslog Forwarding to Microsoft Sentinel
Learn how to set up syslog forwarding to Microsoft Sentinel.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
If you need to fulfill your organization's legal compliance
requirements, you can easily forward firewall logs stored in Strata Logging Service (formerly Cortex Data Lake) to external destinations
through Prisma Access. For example, you can forward logs using syslog to a SIEM for
long term storage, SOC, or internal audit obligations.
You can forward logs to Microsoft Sentinel.
Before you begin, ensure to set up a Sentinel log analytics workspace.
Create a self-signed certificate or use a public certificate for the
Syslog receiver.
- Log in to your Microsoft Azure account.Create and deploy a data connector for Strata Logging Service.
- Search for Sentinel in your Azure account.Select Microsoft Sentinel(your workspace)Content hub.Search and select Palo Alto Networks Cortex Data Lake and install it.
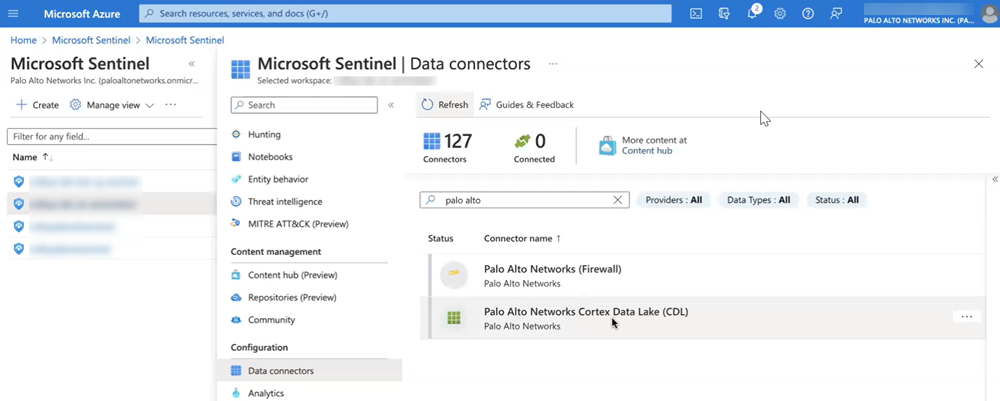
![]() Go to Data connectors and refresh the section to view the Palo Alto Networks Cortex Data Lake (CDL) data connector.
Go to Data connectors and refresh the section to view the Palo Alto Networks Cortex Data Lake (CDL) data connector.![]() Configure Linux Syslog agent according to the instructions you see in Microsoft Sentinel.
Configure Linux Syslog agent according to the instructions you see in Microsoft Sentinel.- Select the Strata Logging Service data connector.Select Open connector page.Configure the Linux agent according to the instructions.
![]() It takes some time to view if the connection is successful. You can view the number of data connectors deployed in Sentinel, which is 1 in this scenario.From Prisma Access, open the Strata Logging Service app associated with your tenant.Go to Prisma AccessTenants and ServicesStrata Logging Service.Select Log Forwarding.Add a Syslog forwarding profile.Configure the Syslog forwarding Profile.
It takes some time to view if the connection is successful. You can view the number of data connectors deployed in Sentinel, which is 1 in this scenario.From Prisma Access, open the Strata Logging Service app associated with your tenant.Go to Prisma AccessTenants and ServicesStrata Logging Service.Select Log Forwarding.Add a Syslog forwarding profile.Configure the Syslog forwarding Profile.- Enter the required values and information.Enter the Syslog server IPv4 address or FQDN.Ensure that the value entered here matches the Subject Alternative Name (SAN) of the certificate installed on your syslog server.Enter the port on which the syslog server is receiving and the facility.Upload a self-signed certificate or a publicly signed certificate.
![]() Test Connection to ensure that Strata Logging Service can communicate with the receiver.Click Next, and select the CEF format to forward logs.Select only the CEF format.Select the logs you want to forward, by adding appropriate filters.
Test Connection to ensure that Strata Logging Service can communicate with the receiver.Click Next, and select the CEF format to forward logs.Select only the CEF format.Select the logs you want to forward, by adding appropriate filters.![]() Save the changes.The status of the Syslog profile takes some time to change from Provisioning to Running.(Optional) Verify if the logs are forwarded to Microsoft Sentinel.
Save the changes.The status of the Syslog profile takes some time to change from Provisioning to Running.(Optional) Verify if the logs are forwarded to Microsoft Sentinel.- Log in to Microsoft Sentinel.Go to Logs and run an appropriate query.The forwarded logs appear.
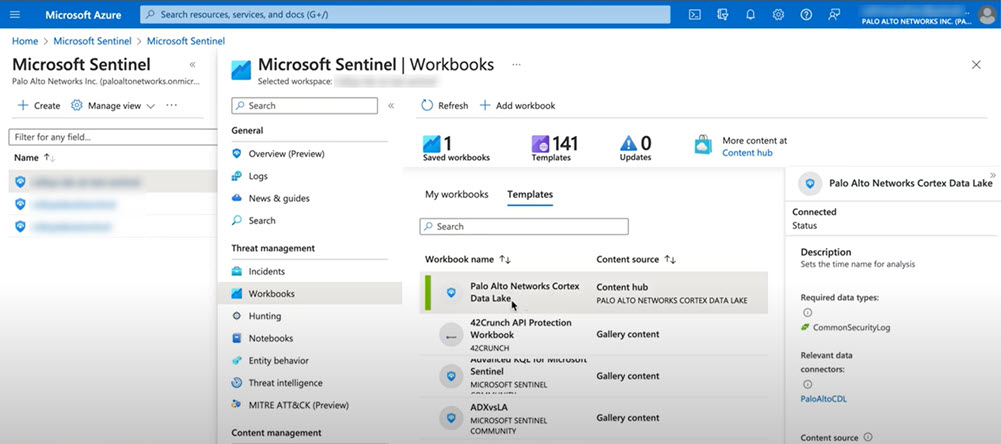
![]() (Optional) Add a workbook in your workspace to visualize and monitor the data.
(Optional) Add a workbook in your workspace to visualize and monitor the data.- Go to WorkbooksTemplates.Search for the Palo Alto Networks Cortex Data Lake workbook with Content hub as the content source.
![]() View template to view the populated data.(Optional) Save the template to edit it.
View template to view the populated data.(Optional) Save the template to edit it.![]()