SaaS Security
Onboard a Microsoft Entra ID App to SSPM
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
Onboard a Microsoft Entra ID App to SSPM
Connect a Microsoft Entra ID instance to SSPM to detect posture risks.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Data Security license:
|
For SSPM to detect posture risks in your Microsoft Entra ID instance, you must
onboard your Microsoft Entra ID instance to SSPM. Through the onboarding process,
SSPM connects to the Microsoft Graph API and, through the API, scans your Microsoft
Entra ID instance at regular intervals.
SSPM gets access to your Microsoft Entra ID instance through a service principal,
which represents a Microsoft Entra application that you create. You will configure
this application's permissions to enable SSPM to access only the API scopes that
SSPM requires to complete its scans. When you register this application, Microsoft
Entra creates the associated service principle that SSPM will use to connect to the
API.
The supported Microsoft account plans for SSPM scans are the following plans:
- Microsoft Business Premium
- Microsoft Entra ID P1
To access your Microsoft Entra ID instance, SSPM requires the following information,
which you will specify during the onboarding process.
| Item | Description |
|---|---|
| Tenant ID | A globally unique identifier (GUID) for your Microsoft Entra tenant. |
| Client ID | SSPM will access the Microsoft Graph API through a Microsoft Entra service principal that represents an application that you create. Microsoft Entra generates the client ID to uniquely identify the application and its associated service principal. |
| Client Secret | SSPM will access the Microsoft Graph API through a Microsoft Entra service principal that represents an application that you create. Microsoft Entra generates the client secret, which SSPM uses to authenticate to the service principal. |
To onboard your Microsoft Entra ID instance, you complete the following actions:
- Log in to the administrator account that you will use to create your Microsoft Entra application and its associated service principal.Required Permissions: The administrator must be able to grant access to the API scopes required by SSPM. In SSPM, the Microsoft Entra onboarding screen lists the scopes that SSPM requires. These scopes are also listed later in these instructions.
- Open a web browser to the Microsoft Entra admin center.Log in to the administrator account.Create and register your Microsoft Entra application.
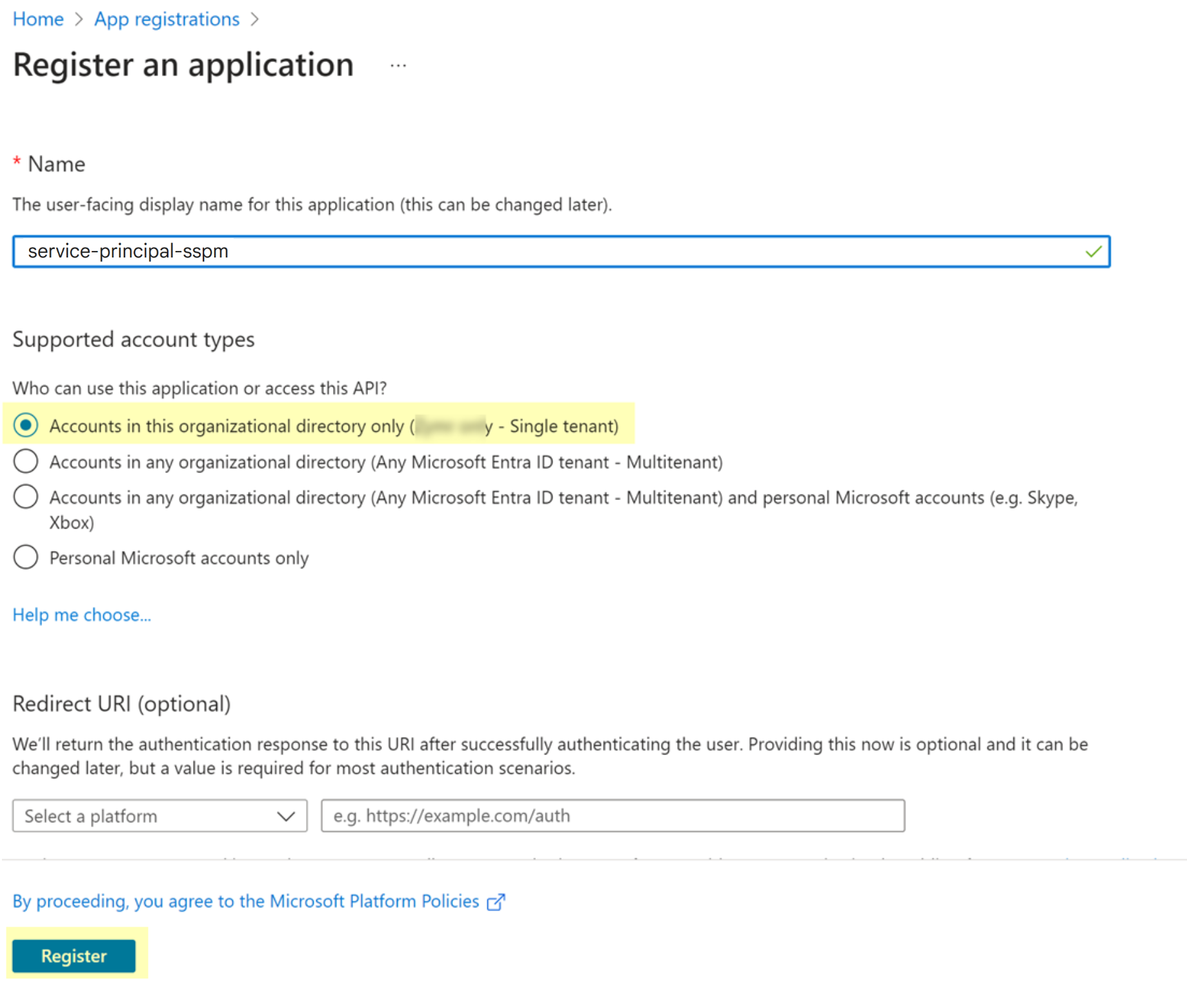
- From the left navigation pane in the Microsoft Entra admin center, select App registrations.On the App registrations page, select the action to create a New application.On the Register an Application page, complete the following actions:
- Specify a name for the application.
- Select Accounts in this organizational directory only.
- Register.Microsoft Entra registers your application and displays the details page for your application. Registering the application automatically creates its associated service principal.
![]()
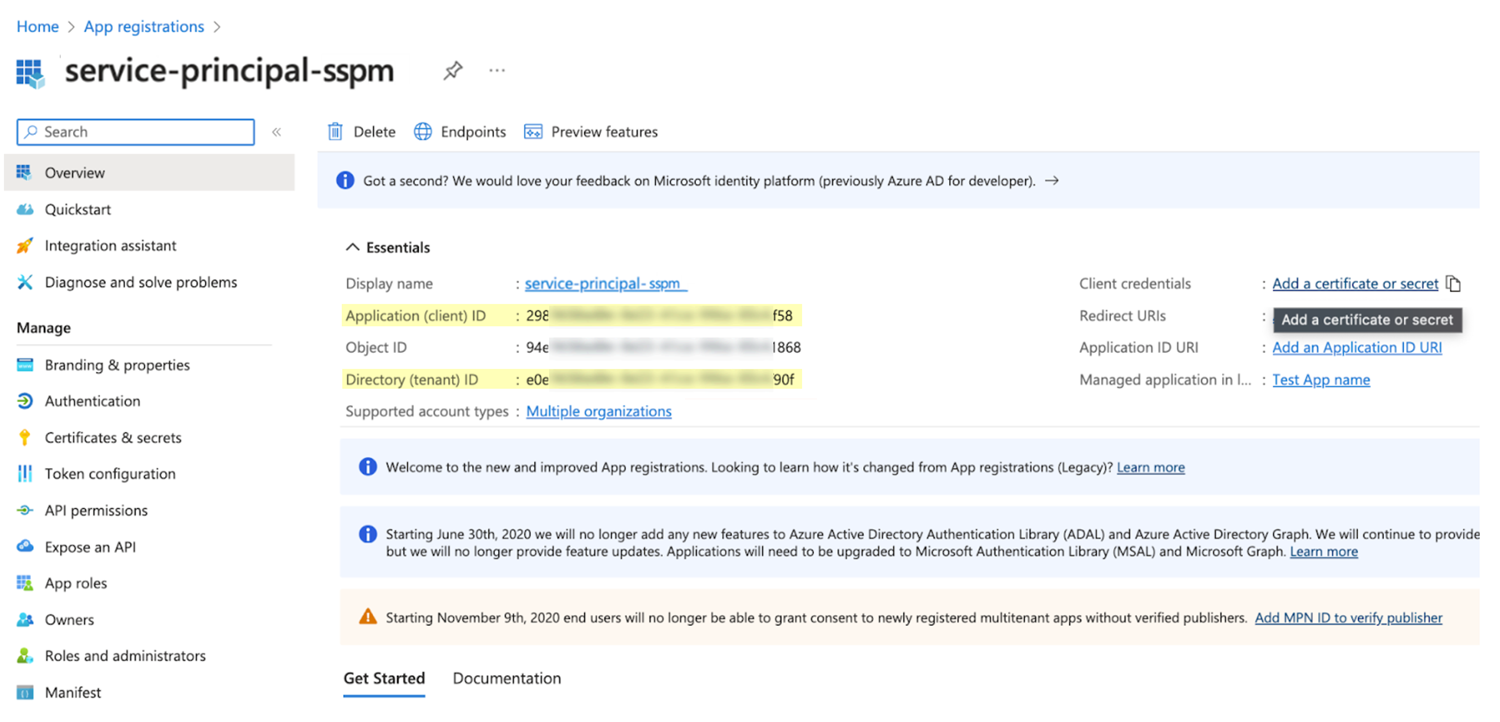
Copy the tenant ID and application credentials (client ID and client secret) for your application.- Copy the tenant ID and client ID.
- From the details page for your application, select Overview.
- From the overview page, copy the client ID from the Application (client) ID field and paste it into a text file.
- From the overview page, copy the tenant ID from the Directory (tenant) ID field and paste it into a text file.
Don’t continue to the next step unless you have copied the client ID and tenant ID. You will also provide this information to SSPM during the onboarding process.![]() Create and copy the client secret.
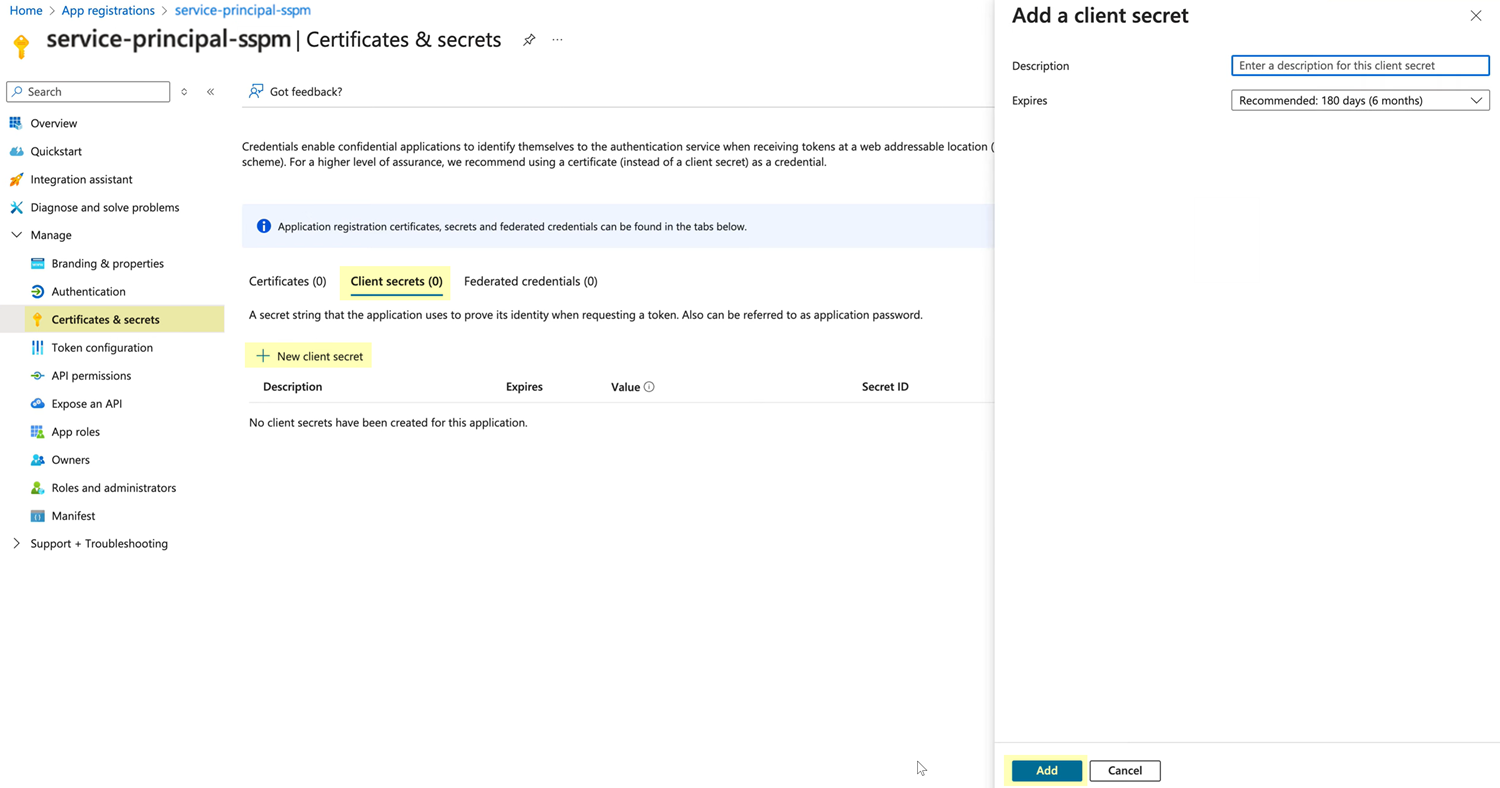
Create and copy the client secret.- From the details page for your application, select Certificates & secretsClient secrets.
- Select New client secret.
- In the Add a client secret flyout dialog, specify an expiration
date for the client secret and Add the
client secret.
![]()
- Copy the Value of the new client secret
and paste it into a text file.Don’t continue to the next step unless you have copied the client secret. You will need to provide this information to SSPM during the onboarding process.
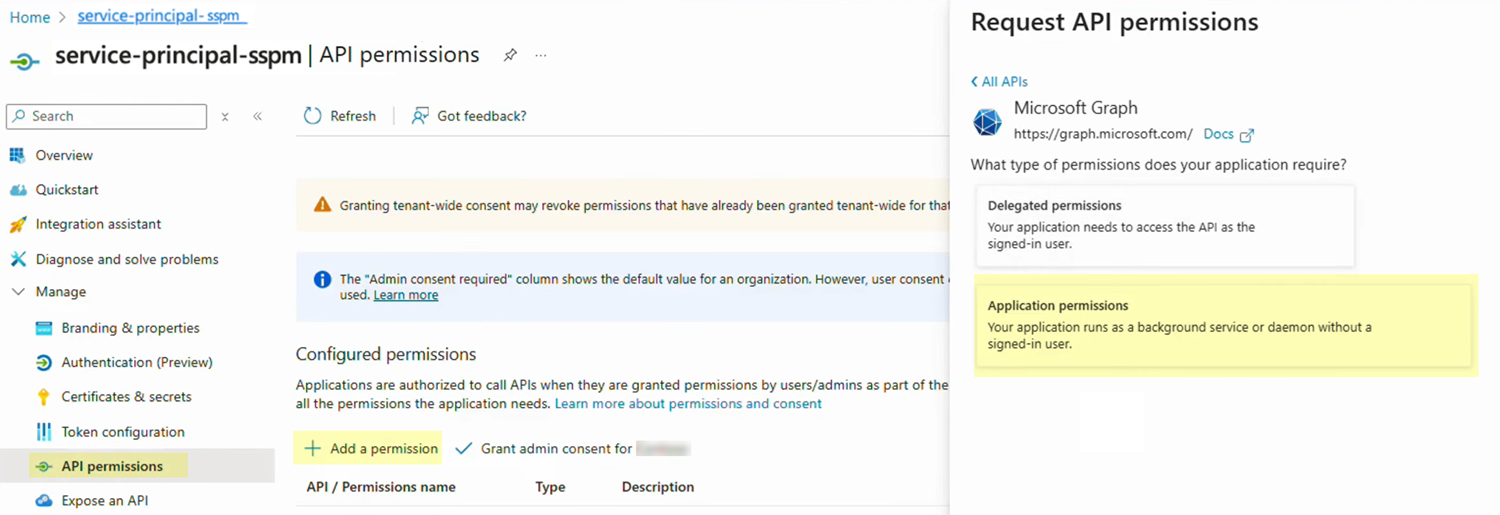
Configure API permissions for your application.Configure your application to enable access only to the Microsoft Graph API scopes that SSPM requires.- From the details page for your application, select API permissions.On the API permissions page, select the action to Add a permission.In the Request API permissions flyout dialog, select the Microsoft Graph API.The Microsoft Graph page prompts you to select the type of permissions your application requires.Select Application permissions.
![]() The Microsoft Graph page prompts you to select the type of permissions your application requires.Select the following API scopes and Add permissions.
The Microsoft Graph page prompts you to select the type of permissions your application requires.Select the following API scopes and Add permissions.- AuthenticationContext.Read.All
- IdentityProvider.Read.All
- Policy.Read.All
- RoleManagement.Read.Directory
On the API permissions page, verify that all the scopes were added as application permissions.On the API permissions page, select Grant admin consent for your organization.Connect SSPM to your Microsoft Entra ID instance.In SSPM, complete the following steps to enable SSPM to connect to your Microsoft Entra ID instance.- Log in to Strata Cloud Manager.Select ConfigurationSaaS SecurityPosture SecurityApplicationsAdd Application and click the Microsoft Entra ID tile.On the Posture Security tab, Add New instance.Select the option for Service Principal.Enter the application credentials (client ID and client secret) and your tenant ID.Connect.