Advanced Threat Prevention Powered by Precision AI®
View Threat Logs
Table of Contents
View Threat Logs
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Threat categories classify different types of threat signatures
to help you understand and draw connections between events threat
signatures detect. Threat categories are subsets of the more broad
threat signature types: spyware, vulnerability, and antivirus. Threat
log entries display the Threat Category for
each recorded event.
You can browse, search, and view Advanced Threat
Prevention logs that are automatically generated when a threat is
detected. Typically, this includes any qualifying threat signature
match that a Threat Prevention feature, including Inline ML, analyzes
unless it is specifically configured with a log severity level of
none. Log entries provide numerous details about the event, including
the threat level and, if applicable, the nature of threat.
View Threat Logs (Cloud Management)
- Use the credentials associated with your Palo Alto Networks support account and log in to the Strata Cloud Manager on the hub.For more information on using Activity dashboards, refer to the Log Viewer.Filter threat logs based on the Threat Category or Subtype in Prisma Access.
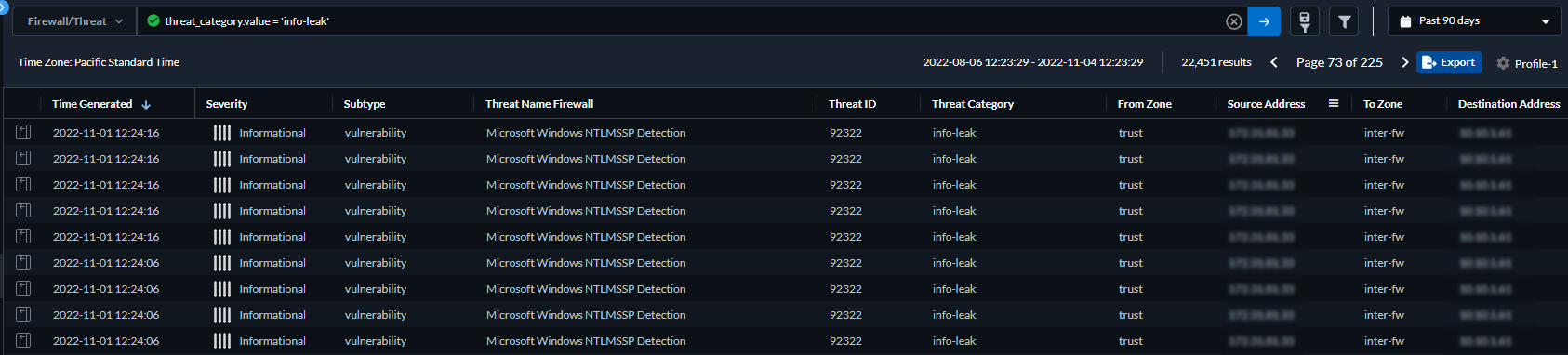
- Select Log Viewer.Change the log type to be searched to Threat.Create a search filter using one the threat signature subtypes used by the Antivirus, Anti-spyware, or Vulnerability Protection profiles (antivirus, spyware, and vulnerability, respectively) or based on the threat category using the query builder. For example, you can use sub_type.value = 'spyware' to view logs for threats that have been determined to be spyware. To search for other subtypes, replace spyware in the above example with another supported subtype (vulnerability or spyware). You can also search based on a specific Threat Category, such as an info-leak vulnerability by using the following query threat_category.value = 'info-leak'. For a list of valid categories you can use, refer to Threat Signature Categories. Adjust the search criteria as necessary for your search, including additional query parameters (such as the severity level and action) along with a date range.
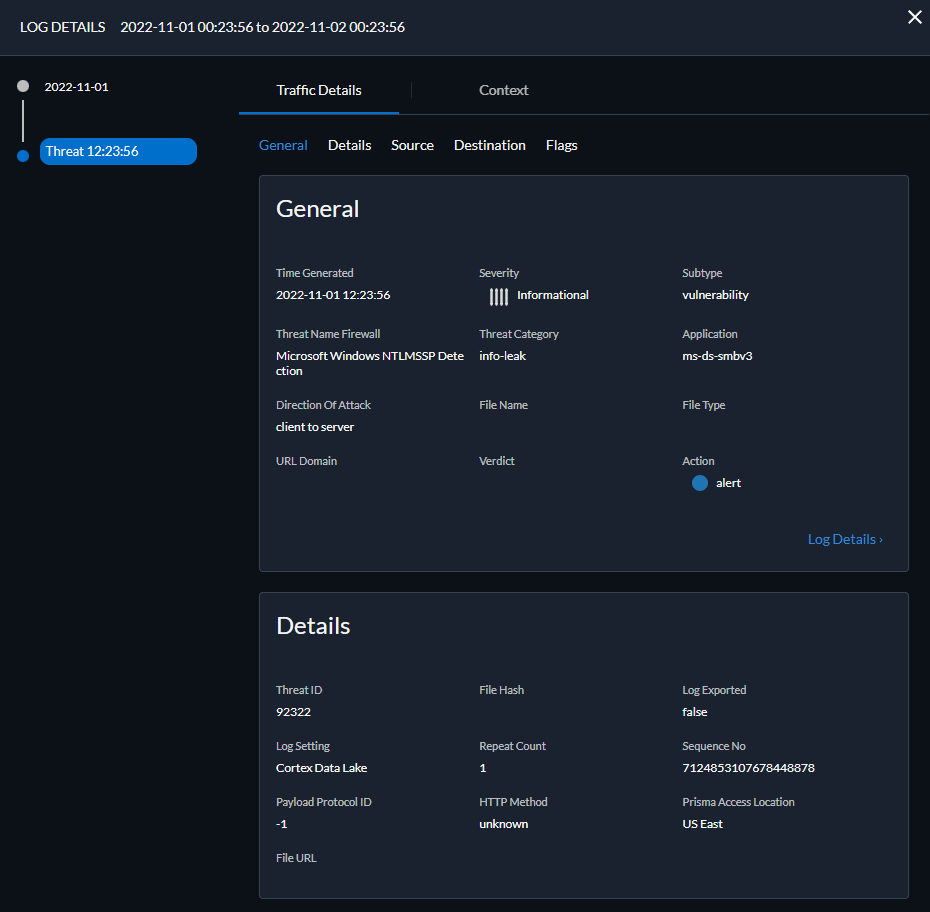
![]() Run the query after you have finished assembling your filters.Select a log entry from the results to view the log details.
Run the query after you have finished assembling your filters.Select a log entry from the results to view the log details.![]() The threat Category is displayed in the Details pane of the detailed log view. Other relevant details about the threat are displayed in their corresponding windows.Filter Threat logs by threat [categories] that have been detected using inline cloud analysis (spyware).HTTP-based C2 traffic that was originally categorized with the threat name Inline Cloud Analyzed HTTP Command and Control Traffic Detection and is associated with multiple Threat IDs, is now separated into three unique threat names to correspond to the unique Threat IDs and more accurately describe the detections made by Advanced Threat Prevention: Evasive HTTP C2 Traffic Detection (Threat ID: 89950), Evasive Cobalt Strike C2 Traffic Detection (Threat ID: 89955, 89956, and 89957), and Evasive Empire C2 Traffic Detection (Threat ID: 89958).HTTP-based C2 traffic logs generated prior to December 11, 2023 will continue to be categorized with the threat name Inline Cloud Analyzed HTTP Command and Control Traffic Detection.
The threat Category is displayed in the Details pane of the detailed log view. Other relevant details about the threat are displayed in their corresponding windows.Filter Threat logs by threat [categories] that have been detected using inline cloud analysis (spyware).HTTP-based C2 traffic that was originally categorized with the threat name Inline Cloud Analyzed HTTP Command and Control Traffic Detection and is associated with multiple Threat IDs, is now separated into three unique threat names to correspond to the unique Threat IDs and more accurately describe the detections made by Advanced Threat Prevention: Evasive HTTP C2 Traffic Detection (Threat ID: 89950), Evasive Cobalt Strike C2 Traffic Detection (Threat ID: 89955, 89956, and 89957), and Evasive Empire C2 Traffic Detection (Threat ID: 89958).HTTP-based C2 traffic logs generated prior to December 11, 2023 will continue to be categorized with the threat name Inline Cloud Analyzed HTTP Command and Control Traffic Detection.- Select Log Viewer.Change the log type to be searched to Threat.Create a search filter using a threat category used exclusively by Inline Cloud Analysis (spyware): threat_category.value = 'inline-cloud-c2'. You can further constrain the search by cross-referencing a Threat-ID value that corresponds to a specific C2 type. For example, threat_category.value = 'inline-cloud-c2' AND Threat ID = 89958, whereby 89958 indicates the Threat ID of evasive empire C2 traffic.Select a log entry to view the details of a detected C2 threat.The threat Category is displayed under the General pane of the log details. C2 threats that have been detected using inline cloud analysis have a threat category of inline-cloud-c2. You can cross-reference the Threat ID value in the Details pane to determine the specific type of C2 that has been detected.Filter Threat logs by threat [categories] that have been detected using inline cloud analysis (vulnerability).
- Select Log Viewer.Change the log type to be searched to Threat.Create a search filter using a threat category used exclusively by Inline Cloud Analysis (vulnerability): threat_category.value = 'inline-cloud-exploit'.Select a log entry to view the details of the detected command injection and SQL injection vulnerabilities. Inline exploit (SQL injection) threats have an ID of 99950 while inline exploit (command injection) threats have an ID of 99951.
View Threat Logs (NGFW (Managed by PAN-OS or Panorama))
- Filter Threat logs by threat category.
- Select MonitorLogsThreat.Add the Threat Category column so you can view the Threat Category for each log entry:
![]() To filter based on Threat Category:
To filter based on Threat Category:- Use the log query builder to add a filter with the Attribute Threat Category and in the Value field, enter a Threat Category.
- Select the Threat Category of any log entry to add that category to the filter:
![]() Filter Threat logs by threat signature type.
Filter Threat logs by threat signature type.- Select MonitorLogsThreat.Add the Type column, if it is not present, so you can view the threat signature category for each log entry:To filter based on the signature type:
- Use the log query builder to add a filter with the Attribute of the threat signature category and in the Value field, enter a threat signature type. You can select from vulnerability, virus, and spyware, which corresponds to the signatures handled by your Vulnerability Protection, Antivirus, and Anti-Spyware security profiles.
- Select the Type of any log entry to add that threat signature type to the filter. You can also manually build your query using the filter and threat signature type.
Filter Threat logs by threat [categories] that have been detected using inline cloud analysis (spyware).HTTP-based C2 traffic that was originally categorized with the threat name Inline Cloud Analyzed HTTP Command and Control Traffic Detection and is associated with multiple Threat IDs, is now separated into multiple unique threat names to correspond to the unique Threat IDs and more accurately describe the detections made by Advanced Threat Prevention:- Evasive HTTP C2 Traffic Detection (Threat ID: 89950)
- Evasive Cobalt Strike C2 Traffic Detection (Threat ID: 89955, 89956, and 89957)
- Evasive Empire C2 Traffic Detection (Threat ID: 89958)
- Evasive Sliver C2 Traffic Detection (Threat ID: 89961)
If you do not install the update content or are reviewing HTTP-based C2 traffic logs generated prior to December 11, 2023 (the release date of the content update), all HTTP-based C2 traffic will continue to be categorized with the threat name Inline Cloud Analyzed HTTP Command and Control Traffic Detection.- Select MonitorLogsThreat. You can filter the logs based on certain characteristics of the threat. Consider the following examples:
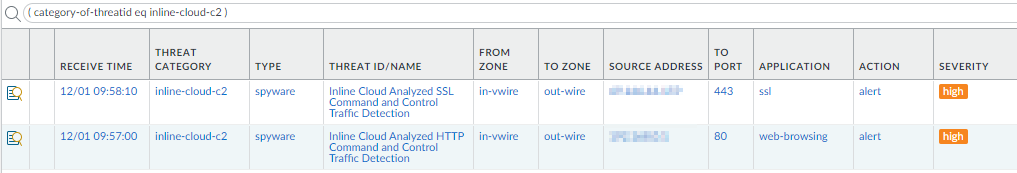
- Filter using ( category-of-threatid eq inline-cloud-c2 ) to view logs for C2 threats that have been analyzed using the inline cloud analysis mechanism of Advanced Threat Prevention.
- You can further constrain the search by cross-referencing a Threat-ID value that corresponds to a specific C2 type. For example, ( category-of-threatid eq inline-cloud-c2 ) and (name-of-threatid eq 89958), whereby 89958 indicates the Threat ID of evasive empire C2 traffic.
- Filter using (local_deep_learning eq yes) to view logs for threats that have been analyzed using the Local Deep Analysis mechanism of Advanced Threat Prevention.
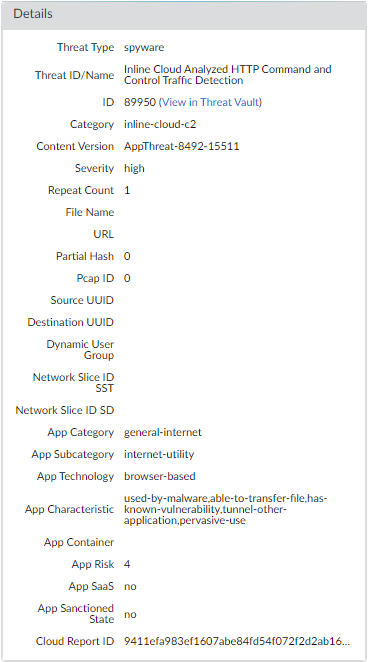
![]() Select a log entry to view the details of a detected C2 threat.The threat Category is displayed under the Details pane of the detailed log view. C2 threats that have been detected using inline cloud analysis have a threat category of inline-cloud-c2. You can cross-reference the Threat ID value to determine the specific type of C2 that has been detected.
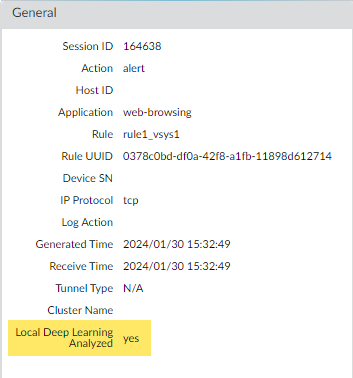
Select a log entry to view the details of a detected C2 threat.The threat Category is displayed under the Details pane of the detailed log view. C2 threats that have been detected using inline cloud analysis have a threat category of inline-cloud-c2. You can cross-reference the Threat ID value to determine the specific type of C2 that has been detected.![]() If the threat was analyzed using Local Deep Learning, the Local Deep Learning Analyzed field indicates yes.
If the threat was analyzed using Local Deep Learning, the Local Deep Learning Analyzed field indicates yes.![]() Monitor activity on the firewall for vulnerability exploits that have been detected using inline cloud analysis (vulnerability).
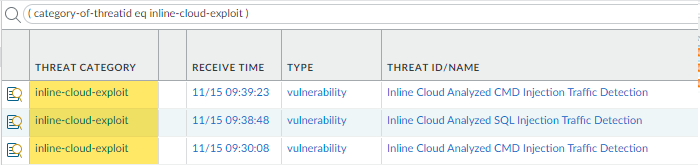
Monitor activity on the firewall for vulnerability exploits that have been detected using inline cloud analysis (vulnerability).- Select MonitorLogsThreat and filter by ( category-of-threatid eq inline-cloud-exploit ) to view logs that have been analyzed using the inline cloud analysis mechanism of Advanced Threat Prevention. Inline exploit (SQL injection) threats have an ID of 99950 while inline exploit (command injection) threats have an ID of 99951.
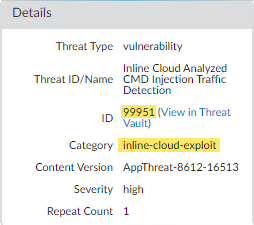
![]() Select a log entry to view the details of a vulnerability exploit.The threat Category is displayed under the Details pane of the detailed log view. Vulnerability exploits that have been detected using inline cloud analysis have a threat category of inline-cloud-exploit.
Select a log entry to view the details of a vulnerability exploit.The threat Category is displayed under the Details pane of the detailed log view. Vulnerability exploits that have been detected using inline cloud analysis have a threat category of inline-cloud-exploit.![]() Monitor activity on the firewall for DNS relay threats that have been detected using inline cloud analysis.Other Advanced Threat Prevention Inline Cloud Analysis engines provide supplemental detection of DNS relay threats, such as the MLC2 detection service. In these cases, the relevant detection service(s) are listed in the Advanced Threat Prevention Report.
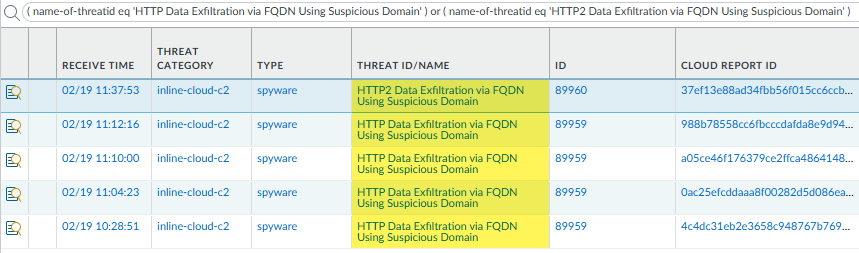
Monitor activity on the firewall for DNS relay threats that have been detected using inline cloud analysis.Other Advanced Threat Prevention Inline Cloud Analysis engines provide supplemental detection of DNS relay threats, such as the MLC2 detection service. In these cases, the relevant detection service(s) are listed in the Advanced Threat Prevention Report.- Select MonitorLogsThreat and filter by ( name-of-threatid eq 'HTTP Data Exfiltration via FQDN Using Suspicious Domain' ) or ( name-of-threatid eq 'HTTP2 Data Exfiltration via FQDN Using Suspicious Domain' ) to view logs that have been analyzed using the inline cloud analysis mechanism of Advanced Threat Prevention. HTTP-based DNS relay threats have an ID of 89959 while HTTP2-based DNS relay threats have an ID of 89960.
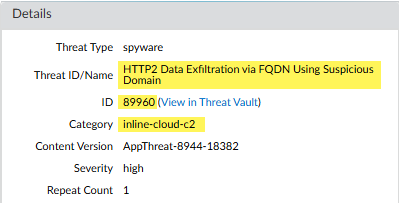
![]() Select a log entry to view the details of a DNS relay threat.The specific Threat ID/Name and ID associated with the threat are displayed under the Details pane of the detailed log view. DNS relay threats that have been detected using inline cloud analysis have a threat category of inline-cloud-c2.
Select a log entry to view the details of a DNS relay threat.The specific Threat ID/Name and ID associated with the threat are displayed under the Details pane of the detailed log view. DNS relay threats that have been detected using inline cloud analysis have a threat category of inline-cloud-c2.![]() Filter ACC activity by threat category.
Filter ACC activity by threat category.- Select ACC and add Threat Category as a global filter:
![]() Select the Threat Category to filter all ACC tabs.
Select the Threat Category to filter all ACC tabs.![]()