Advanced URL Filtering
Configure URL Filtering (Strata Cloud Manager)
Table of Contents
Configure URL Filtering (Strata Cloud Manager)
If you’re using Panorama to manage Prisma Access:
Toggle over to the PAN-OS & Panorama tab and follow the guidance there.
If you’re using Strata Cloud Manager, continue here.
URL filtering is called URL Access Management in Strata Cloud Manager
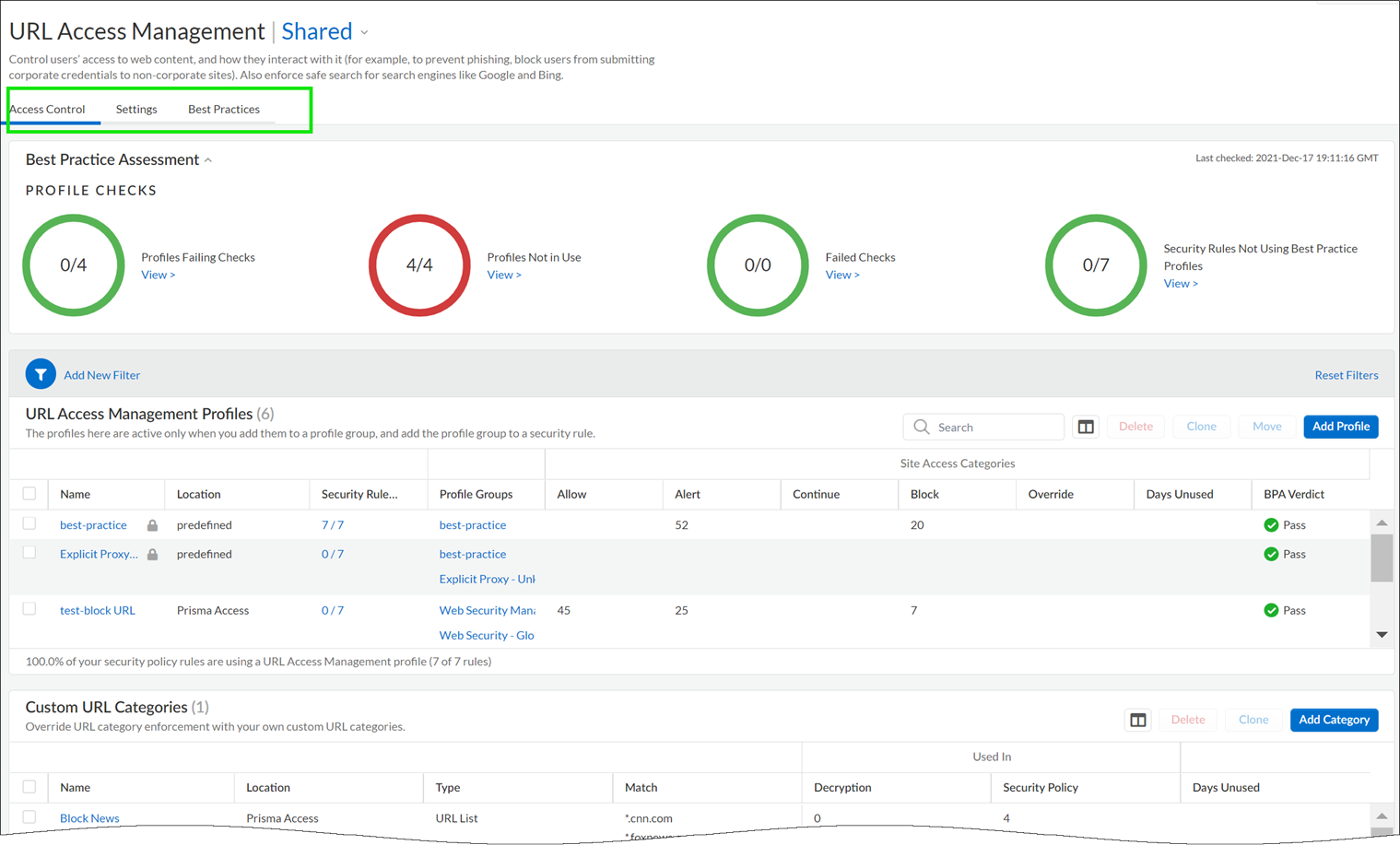
- Check that your Prisma Access subscription covers Advanced URL Filtering.Explore the URL Access Management Dashboard.Go to ConfigurationNGFW and Prisma AccessSecurity ServicesURL Access Management.Move between the Access Control, Settings, and Best Practices tabs to explore the available URL filtering features.
![]() Review and customize General URL Filtering Settings.On the dashboard, go to Settings to see the default URL Filtering settings that apply across your Prisma Access environment, including:
Review and customize General URL Filtering Settings.On the dashboard, go to Settings to see the default URL Filtering settings that apply across your Prisma Access environment, including:- URL Filtering timeout and lookup settings
- URL Filtering overrides for certain admins
- URL Filtering response pages
Automatically append end tokens to URLs in a custom URL category or external dynamic list(PAN-OS 10.1 and earlier) If you add URLs to custom URL categories or external dynamic lists (EDLs) of URL list type and don't append a trailing slash (/), you may block or allow more URLs than intended. For example, entering example.com instead of example.com/ expands matching URLs to example.com.website.info or example.com.br. Prisma Access can automatically append a trailing slash to URLs in custom URL categories or EDLs so that, if you enter example.com, Prisma Access treats it as it would treat example.com/ and only considers that domain and its subdirectories matches. Go to SettingsGeneral Settings and enable the Append End Token to Entries option.(PAN-OS 10.2 and later)Prisma Access automatically adds a trailing slash to domain entries.You can customize these settings for each deployment type (mobile users, remote networks, or service connections).Create a URL Access Management profile.On the URL Access Management dashboard, Add Profile and continue to specify web access settings:- Access Control displays the URL categories and lists for which you can define web access and usage policy. By default, the Site Access and User Credential Submission permissions for all categories are set to Allow.
- For each URL category, configure User Credential Detection so that users can submit credentials only to sites in specified URL categories.
- Enable Safe Search Enforcement to enforce strict safe search filtering.
- Enable Log Container Page Only to log only those URLs that match the content type that is specified.
- Enabling HTTP Header Logging provides visibility into the attributes in the HTTP request sent to a server.
- Use the Advanced URL Inline Categorization to enable and configure real-time web page analysis and manage URL exceptions.
- Enable local Inline Categorization—Enables real-time analysis of URL traffic using machine learning models, to detect and prevent malicious phishing variants and JavaScript exploits from entering your network.
- Enable cloud Inline Categorization—Enables real-time analysis of URLs by forwarding suspicious web page contents to the cloud for supplemental analysis, using machine learning based detectors that complement the analysis engines used by local inline ML.
- You can define URL Exceptions for specific web sites to exclude from inline machine learning actions.
Note that:- Best practice checks are built-in to the profile to give you a live evaluation of your configuration.
- After you’ve finished enabling a profile, you can examine profile usage to see if any security policy rules are referencing the profile.
![]() Apply the URL Access Management profile to a Security policy rule.A URL Access Management profile is only active when it’s included in a profile group that a Security policy rule references.Follow the steps to activate a URL Access Management profile (and any Security profile). Be sure to Push Config
Apply the URL Access Management profile to a Security policy rule.A URL Access Management profile is only active when it’s included in a profile group that a Security policy rule references.Follow the steps to activate a URL Access Management profile (and any Security profile). Be sure to Push Config