Prisma AIRS
Deploy Security Lifecycle Review (SLR) for AWS
Table of Contents
Expand All
|
Collapse All
Prisma AIRS Docs
Deploy Security Lifecycle Review (SLR) for AWS
Learn about how to deploy Security Lifecycle Review (SLR) in your cloud environment
using the deployment workflow for Strata Cloud Manager.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
This section helps you deploy Security Lifecycle Review (SLR) in your cloud environment
using the deployment workflow in Strata Cloud Manager.
SLR Deployment Types
The SLR deployment Terraform offers two flexible options for AI traffic monitoring, which
uses AWS infrastructure to meet diverse organizational needs. You can enable SLR in the
following two deployment types:
GWLB-Based Centralized Deployment
- The SLR deployment Terraform deploys SLR in traffic mirroring mode in a centralized security VPC behind AWS Gateway Load Balancer (GWLB) with multiple endpoints.
- Amazon VPC traffic mirroring captures and sends the mirrored traffic from application ENIs to Amazon GWLB, and GWLB sends it to SLR for traffic inspection and analysis.
- Efficient for monitoring multiple applications across different VPCs simultaneously.
- Scales well for large-scale, organization-wide implementations.
- It uses AWS Traffic Mirroring capabilities across supported instance types.
Per Application VPC Deployment
- The SLR deployment Terraform deploys a standalone SLR per VPC in traffic mirroring mode within the application VPC.
- Amazon VPC traffic mirroring captures and sends the mirrored traffic from application ENIs directly to SLR.
- Efficient for monitoring multiple applications in the same VPC.
- Suitable for smaller-scale or isolated deployments.
Prerequisites
- Optional: If you have already onboarded an AWS account in Prisma AIRS AI Runtime: Network intercept.
- Navigate to AI Security AI Runtime AI Runtime Firewall.
- In the top right corner, click on the cloud icon.
- Choose your AWS cloud account and select Download Terraform to add "ec2:DescribeNetworkInterfaces" policy to your `iam.tf` file.
- Copy all files from the newly downloaded folder into your existing AWS discovery Terraform folder.
- Initialize, plan, and deploy the updated onboarding Terraform in your AWS environment.
- Create an elastic network interface (ENI) for your EC2 instance and route your traffic through the GWLB endpoint to enable centralized inspection by the SLR deployment.
- Associate the AIRS-SLR-AWS-default snippet to a folder and attach this folder to the SCM management parameters. Refer Manage: Snippets for details.
Deploy GWLB-Based SLR in AWS
Deploy GWLB-based SLR when you want to monitor multiple applications across different
VPCs simultaneously.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
- Log in to Strata Cloud Manager.Navigate to Insights AI Runtime AI Runtime Firewall.In the top right corner, click on the binocular icon.Select a cloud service provider and select Next.If you have previously created an SLR deployment, select Add New SLR Deployment on the SLR Monitoring deployment screen.
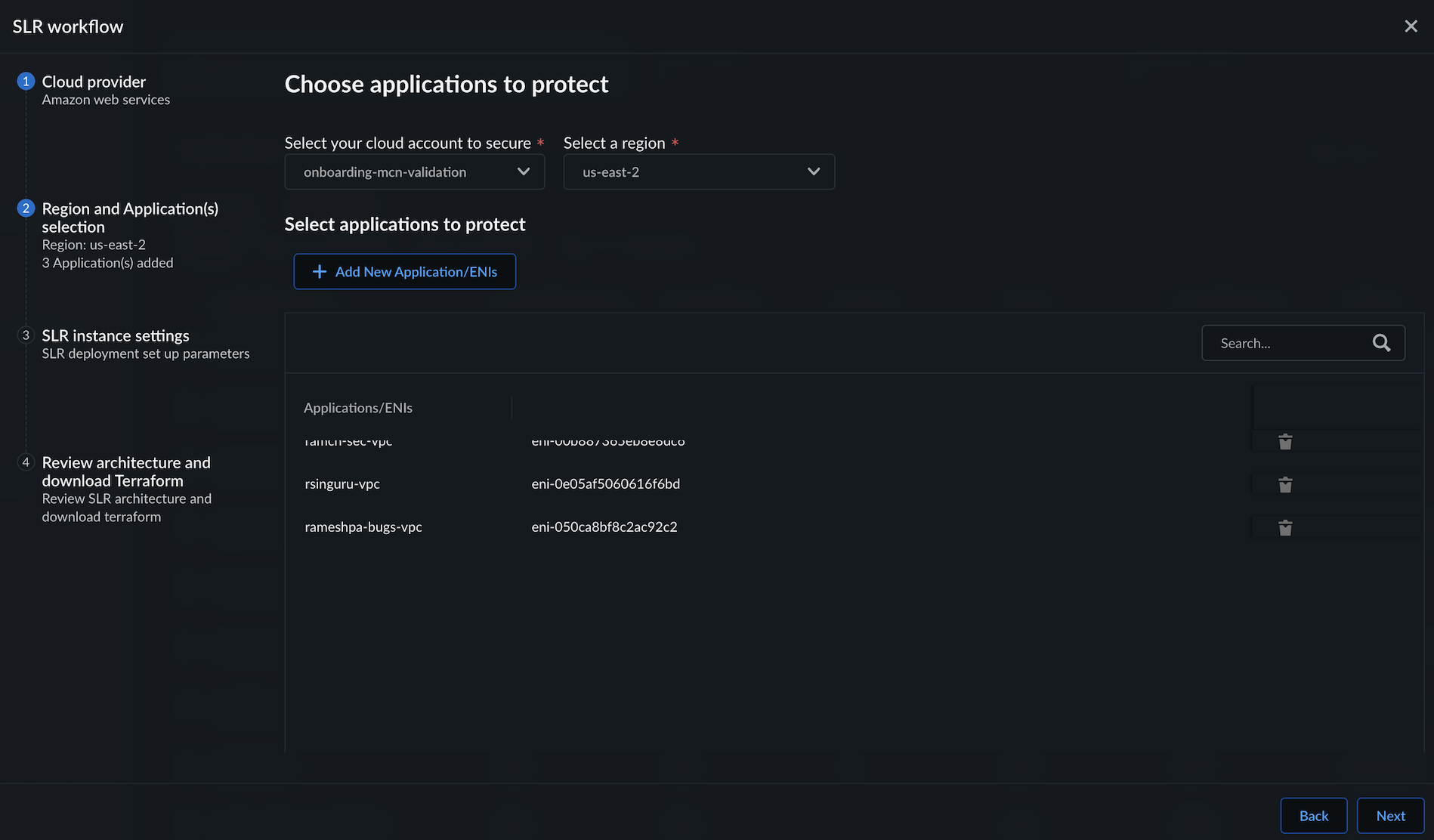
![]() In Regions & Application(s):
In Regions & Application(s):- Select the cloud account you want to secure.Select the Region in which you want to protect the applications.Click Add New Application/ENIs, and select the application’s ENIs.Select Next.
![]() In Deployment Parameters, select Gateway Load Balancer (GWLB) based deployment.
In Deployment Parameters, select Gateway Load Balancer (GWLB) based deployment.- Enter the configurations to create the GWLB endpoints:
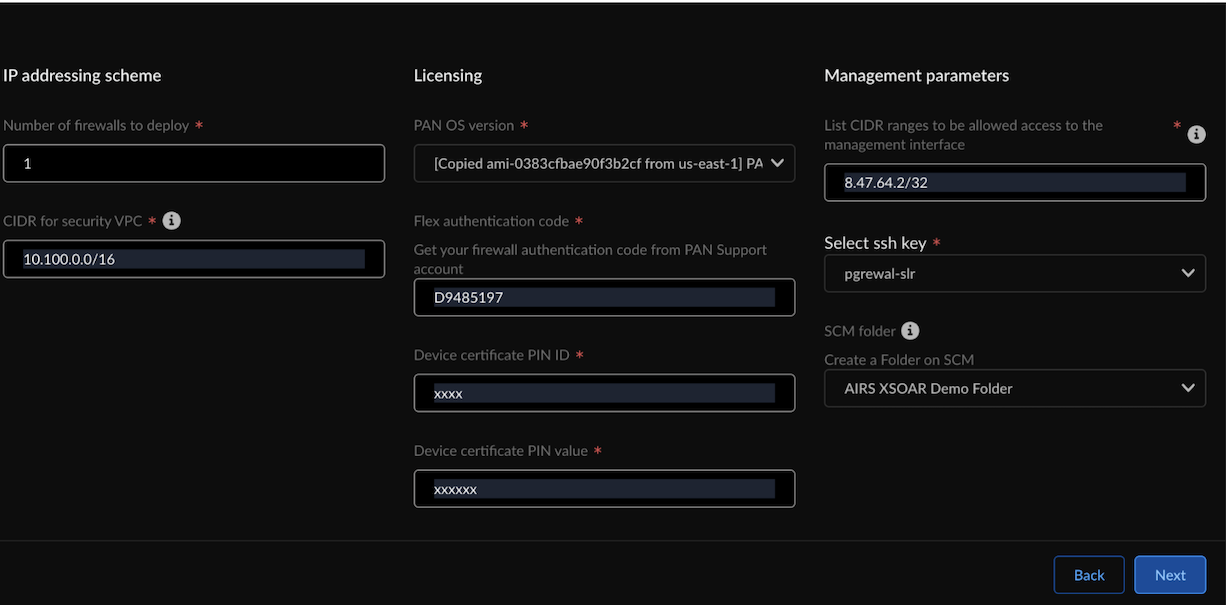
![]() In GWLB Endpoint CIDR: Enter the subnet’s CIDR IP address for each application’s endpoint. Ensure the CIDR is part of the application VPC where you want to monitor traffic.Configure the following:
In GWLB Endpoint CIDR: Enter the subnet’s CIDR IP address for each application’s endpoint. Ensure the CIDR is part of the application VPC where you want to monitor traffic.Configure the following:IP addressing scheme Licensing Management parameters - Number of firewalls to deploy.
- CIDR value for the security VPC. CIDR IP address of the firewall.
- PAN OS version for your image.
- Flex authentication code (Copy AUTH CODE for the deployment profile you created for Prisma AIRS AI Runtime: Network intercept in Customer Support Portal).
- Device Certificate PIN ID.
- Device Certificate PIN value.
- List CIDR ranges to be allowed access to the management interface.
- Enter the SSH key to be used for login (see how to create a key pair for your Amazon EC2 instance).
- Select Manage by SCM and select the
SCM folder to group the Prisma AIRS AI Runtime: Network
intercept. (See, Workflows: Folders
- Strata Cloud Manager).Select the SCM folder with the default configuration snippet - "AIRS-SLR-AWS-default" you created in the prerequisite step from the SLR deployment section.
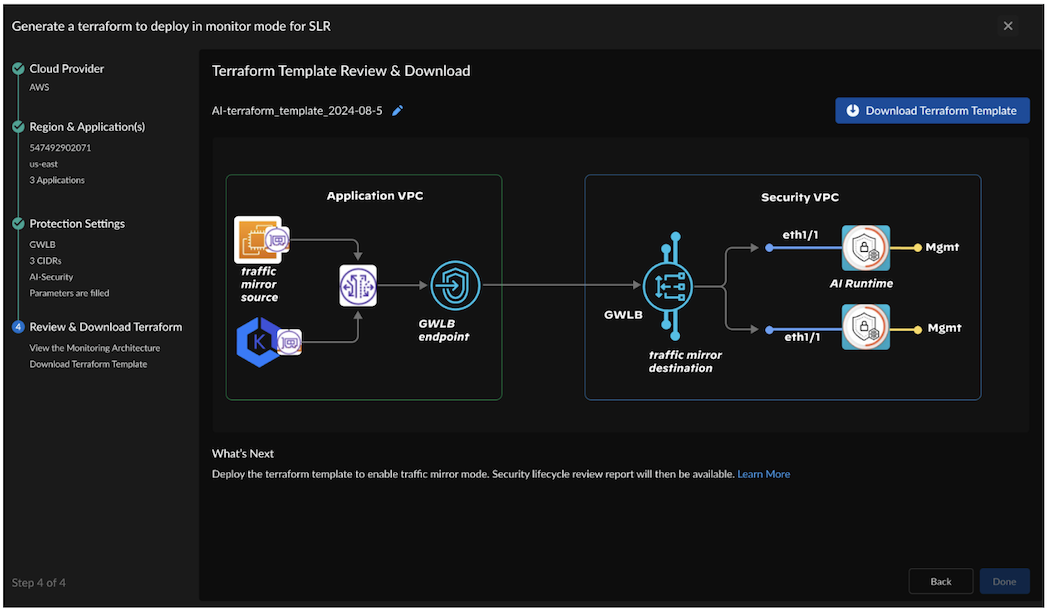
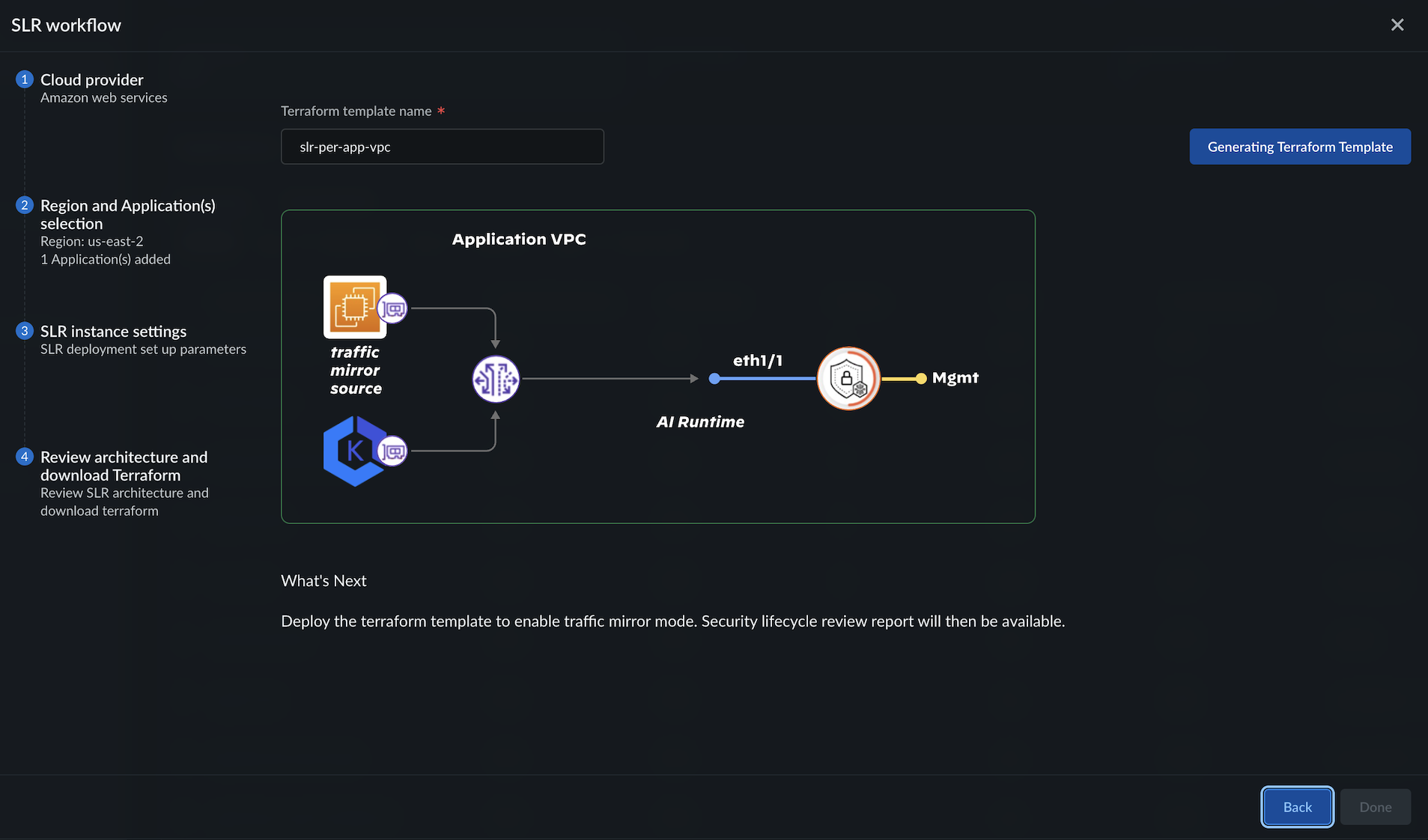
![]() Select Next.Enter a Terraform template name.Review the network architecture for GWLB-based centralized SLR deployment:2 VPC: Application VPC and Security VPC.
Select Next.Enter a Terraform template name.Review the network architecture for GWLB-based centralized SLR deployment:2 VPC: Application VPC and Security VPC.- The GWLB endpoint in the application VPC monitors the mirroring traffic between the application ENIs.
- GWLB in the security VPC collects the mirrored traffic routed from the GWLB endpoint.
- SLR is deployed in the security VPC behind GWLB.
- Interfaces - eth1/1: GWLB transfers the mirrored traffic to the SLR instances through eth1/1.
Click Generate Terraform Template.Click Download Terraform Template and save the zip file. This saves and downloads the SLR deployment Terraform.![]() Click Done.Unzip the downloaded file.Navigate to <unzipped-folder> with 2 directories: `architecture` and `modules`. Deploy the Terraform templates in your cloud environment following the `README.md` file in the `architecture` folder.Initialize and apply the Terraform for the security_project.Deploying Terraform for the security project creates the GWLB endpoints in your selected application VPC. The security Terraform deploys an Auto Scaling Group (ASG) in a security VPC with an SLR, the SLR receives the mirrored traffic from application ENIs.The security_project contains the Terraform plan to deploy an SLR in traffic mirroring mode in a centralized security VPC behind AWS Gateway Load Balancer (GWLB) with multiple endpoints.cd architecture cd security_project terraform init terraform plan terraform applyThe output is similar to the below snippet and displays the SLR public IP address.Output: Apply complete! Resources: 6 added, 0 changed, 1 destroyed. Outputs: App_inspected_dns_name = [] Gwlb_service = { "Security_gwlb" = "com.amazonaws.vpce.us-east-1.vpce-svc-xxxxxxxxxxxxxxxx" }Run the application Terraform to peer the application VPCs. The application Terraform enables packet mirroring at the application workload and exports traffic to SLR.cd ../application_project terraform init terraform plan terraform applyThe output lists the GWLB endpoints and the traffic mirror sessions.Next, View and Manage SLR Reports for threat analysis and risk mitigation.
Click Done.Unzip the downloaded file.Navigate to <unzipped-folder> with 2 directories: `architecture` and `modules`. Deploy the Terraform templates in your cloud environment following the `README.md` file in the `architecture` folder.Initialize and apply the Terraform for the security_project.Deploying Terraform for the security project creates the GWLB endpoints in your selected application VPC. The security Terraform deploys an Auto Scaling Group (ASG) in a security VPC with an SLR, the SLR receives the mirrored traffic from application ENIs.The security_project contains the Terraform plan to deploy an SLR in traffic mirroring mode in a centralized security VPC behind AWS Gateway Load Balancer (GWLB) with multiple endpoints.cd architecture cd security_project terraform init terraform plan terraform applyThe output is similar to the below snippet and displays the SLR public IP address.Output: Apply complete! Resources: 6 added, 0 changed, 1 destroyed. Outputs: App_inspected_dns_name = [] Gwlb_service = { "Security_gwlb" = "com.amazonaws.vpce.us-east-1.vpce-svc-xxxxxxxxxxxxxxxx" }Run the application Terraform to peer the application VPCs. The application Terraform enables packet mirroring at the application workload and exports traffic to SLR.cd ../application_project terraform init terraform plan terraform applyThe output lists the GWLB endpoints and the traffic mirror sessions.Next, View and Manage SLR Reports for threat analysis and risk mitigation.Deploy Per Application VPC-Based SLR in AWS
Deploy Per application VPC-based Security Lifecycle Report (SLR) when you want to monitor multiple applications running in the same VPC.Where Can I Use This? What Do I Need? - Per Application VPC-Based Security Lifecycle Review (SLR) Deployment in AWS
Deploy Per application VPC-based Security Lifecycle Review (SLR) to monitor multiple applications running in the same VPC.- Log in to Strata Cloud Manager.Navigate to Insights Prisma AIRS Prisma AIRS AI Runtime: Network intercept.In the top-right corner, click on the binocular icon.Select a cloud service provider and select Next.If you have previously created an SLR deployment, select Add New SLR Deployment on the SLR Monitoring deployment screen.
![]() In Regions & Application(s):
In Regions & Application(s):- Select your cloud account to secure from the onboarded cloud accounts list.Select a region in which you want to protect the applications.Click Add New Application/ENIs, and select the application ENIs from the available list.Select Next.
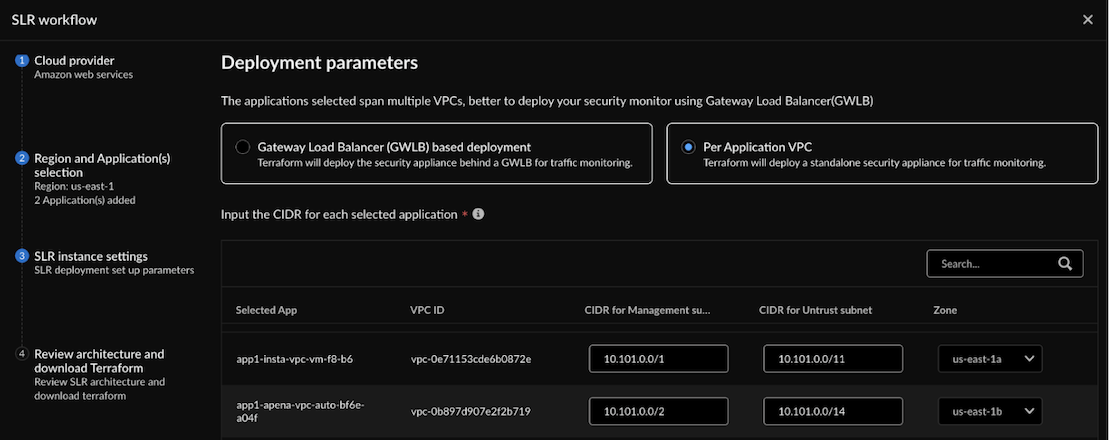
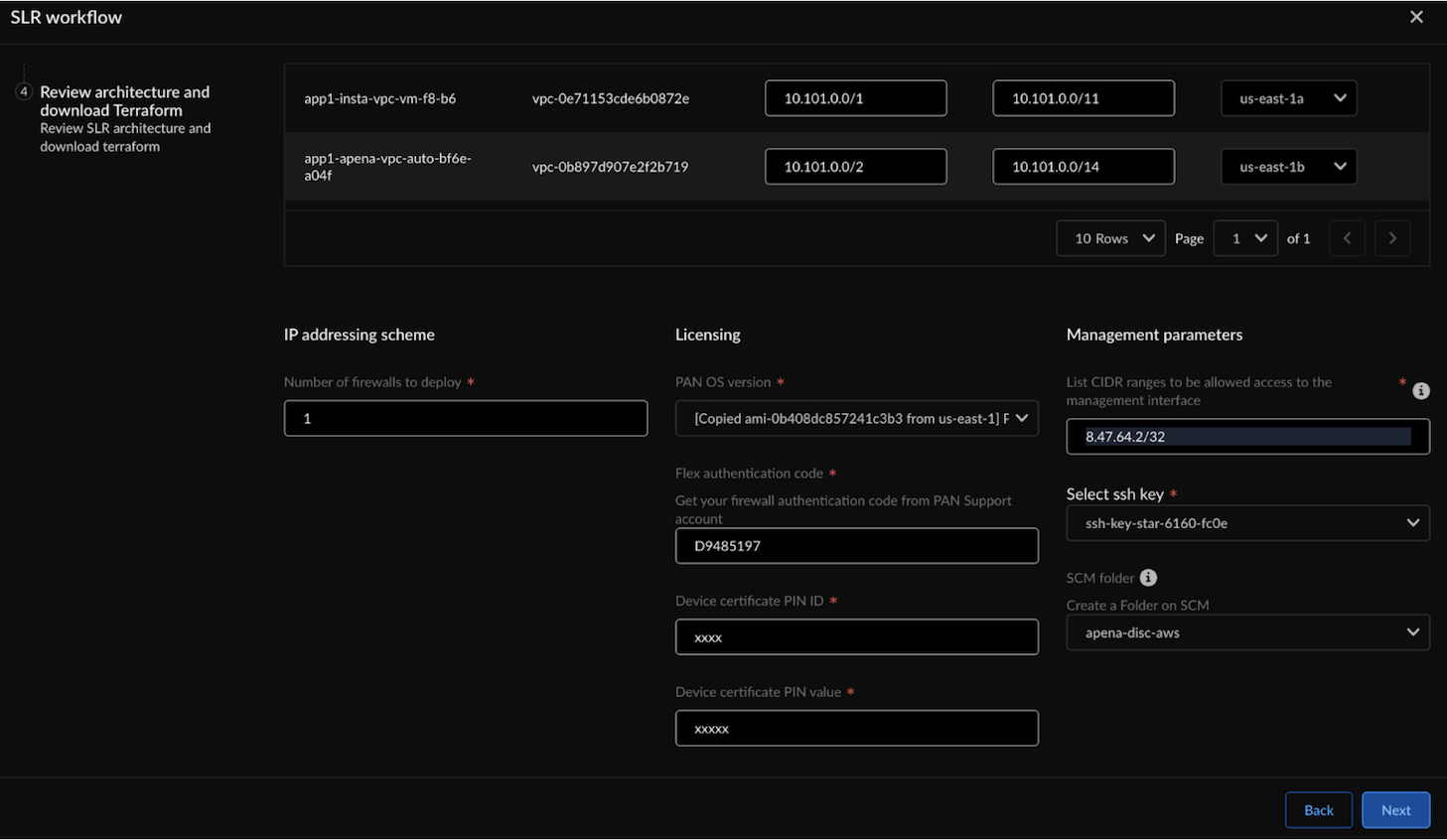
![]() In Deployment Parameters, select Per Application VPC.Input the CIDR for each selected application:
In Deployment Parameters, select Per Application VPC.Input the CIDR for each selected application:- Enter the CIDR IP address for the management port.
- Enter the CIDR IP address for the Untrust VPC subnet.
- In Zone, select the zone where your application resides in the
specified VPC ID (these are the available zones in the region you
selected earlier).You can choose multiple applications within the same VPC.
![]() Configure the following:
Configure the following:![]()
IP addressing scheme Licensing Management parameters - Number of firewalls to deploy
Enter the following values:- PAN OS version for your image.
- Flex authentication code (Copy AUTH CODE for the deployment profile you created for Prisma AIRS AI Runtime: Network intercept in Customer Support Portal).
- Device Certificate PIN ID.
- Device Certificate PIN value.
In Management parameters, enter the following:- List CIDR ranges to be allowed access to the management interface.
- The SSH key to be used for login (see how to create a key pair for your Amazon EC2 instance).
- Manage by SCM and then select the SCM
folder to group the Prisma AIRS AI Runtime: Network
intercept. (See, Workflows: Folders
- Strata Cloud Manager).Select the SCM folder with the default configuration snippet - "AIRS-SLR-AWS-default" you created in the prerequisite step from the SLR deployment section.
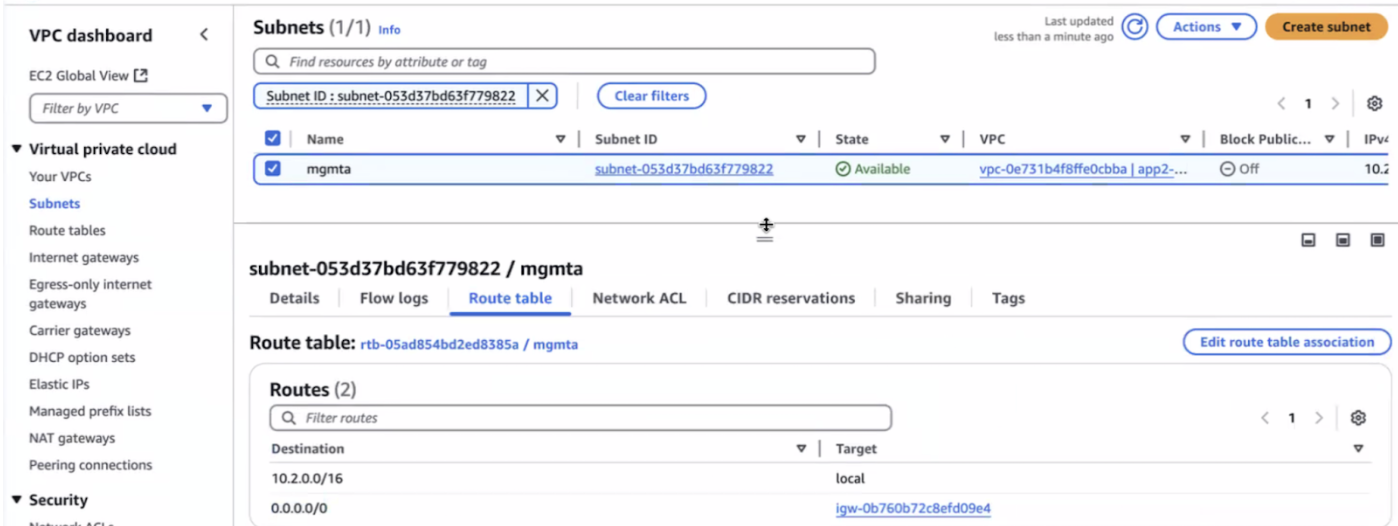
Select Next.Enter a Terraform template name.Click Generate Terraform Template.Click Download Terraform Template and save the zip file.![]() Click Done.Initialize and apply the Terraform for the `security_project` to deploy a standalone SLR per VPC in traffic mirroring mode within the application VPC.The security Terraform for the security project creates the Gateway Load Balancer (GWLB) endpoints in your selected application VPC. It also deploys an Auto Scaling Group (ASG) with an SLR in a security VPC. The SLR receives the mirrored traffic from the application ENIs.cd architecture cd security_project terraform init terraform plan terraform applyTo ensure the Per App SLR management interface can connect to the internet through the Internet Gateway(IGW) to function properly in your security VPC, you must manually add the IGW to its route table.Configure IGW for SLR firewall management subnet:
Click Done.Initialize and apply the Terraform for the `security_project` to deploy a standalone SLR per VPC in traffic mirroring mode within the application VPC.The security Terraform for the security project creates the Gateway Load Balancer (GWLB) endpoints in your selected application VPC. It also deploys an Auto Scaling Group (ASG) with an SLR in a security VPC. The SLR receives the mirrored traffic from the application ENIs.cd architecture cd security_project terraform init terraform plan terraform applyTo ensure the Per App SLR management interface can connect to the internet through the Internet Gateway(IGW) to function properly in your security VPC, you must manually add the IGW to its route table.Configure IGW for SLR firewall management subnet:- Create an Internet Gateway (IGW) in your application VPC if you
have not done so already. For detailed instructions, refer to the AWS documentation: Create and attach an internet gateway.
- Navigate to AWS Console > EC2 > Instances and search for the SLR (AI firewall) instance.
- Go to the Networking tab and click on the Subnet ID associated with the management port of the SLR firewall.
- In the subnet details, select the Route table tab.
- Edit the route table and add a new route:
- Destination: 0.0.0.0/0
- Target: Select the IGW you created earlier
- Save the changes to update the route table.
![]() Navigate to the `application_project` directory, and run the application Terraform to peer the application VPCs.This sets up traffic mirroring sessions to direct traffic to the SLR firewall for monitoring.cd ../application_project terraform init terraform plan terraform applyNext, View and Manage SLR Reports for threat analysis and risk mitigation.
Navigate to the `application_project` directory, and run the application Terraform to peer the application VPCs.This sets up traffic mirroring sessions to direct traffic to the SLR firewall for monitoring.cd ../application_project terraform init terraform plan terraform applyNext, View and Manage SLR Reports for threat analysis and risk mitigation.