Deploy Administrative Access Best Practices
Table of Contents
10.1
Expand all | Collapse all
Deploy Administrative Access Best Practices
Best deployment practices for securing administrative
access and traffic to management networks and interfaces.
Deploying administrative access best practices
consists of seven tasks:
The
two most critical best practices concepts to keep in mind as you
deploy or update management access are:
- Always apply the principle of least privilege access, which means:
- Enable management access only for the people and services that must have access to manage the device.
- Limit access for each administrator and service to only the areas of the device and the privileges required to perform the necessary management functions. Use role-based access control (RBAC) to define access privileges for each administrator.
- Isolate the management network and isolate the device’s management interface so that only management traffic, administrators, and administrative services can access the management network.
- Inspect all traffic destined for the management port.
- Apply Security policy rules that not only specify the IP addresses of administrators and devices allowed access, but that also specify the applications allowed, the source and destination zones allowed, and the users allowed. Granular Security policy enables you to allow the right access to the right people and services on the right devices.
- Apply appropriate threat prevention profiles to the traffic in Security policy.
- Log the traffic and forward the logs to the appropriate administrators and long-term storage.
Select the Management Interface
On PAN-OS firewalls, you can use either the
dedicated Management (MGT) port or a dedicated in-band dataplane
(DP) port as the management interface. On Panorama, you can only
use the dedicated MGT port as the management interface. Regardless
of which port you use as the management interface, use an architecture
that enables you to inspect and control inbound traffic to the management
interface with Security policy.
If you are deploying
a firewall for the first time, you must perform the initial configuration using
the MGT port.
You cannot apply Security policy rules
directly to traffic that ingresses the dedicated MGT port. However,
you can route incoming traffic for the MGT port through a DP port
to decrypt and inspect the traffic. You can use a variety of methods
to route incoming MGT port traffic for inspection, such as:
- Looping back through a local DP port on the same device (MP to DP connection).
- Connecting to a DP port on another firewall.
- Leveraging upstream routing/switching infrastructure to provide the appropriate isolation and the appropriate inspection by firewalls.
When
you use a DP port to inspect traffic destined for the MGT port,
do not enable management protocols on the DP port. Enable management
protocols only on the MGT port. Understand the external services
and service routes for which you will need to set up access
PAN-OS
allows you to configure access to management-related functions such
as the web interface or SSH on DP ports, but that is different than
isolating and inspecting physical MGT port traffic on a DP interface.
To ensure the highest level of security, limit administrative access
traffic such as web UI, API, and CLI to the dedicated management
interface unless site requirements prevent it.
If you
can’t route traffic destined for the MGT port through a DP port
interface on another firewall for inspection, configure a dedicated
DP port to be the management interface so that you can use Security
policy to inspect the inbound management traffic. If you use the
DP port as the management interface, isolate it as described in
this section. Using a DP port as the isolated management interface
trades consuming a production port for safeguarding management traffic.
If
you choose to route inbound management traffic to the MGT port without
prior inspection, understand the risks of not inspecting the traffic,
which include unauthorized access to device management, potential
malicious activity, and unblocked threats. The best practice is
always to inspect inbound management traffic because it controls
and configures your device.
- Management networks that include more than one firewall (and Panorama)—Use the MGT port as the management interface.Route incoming management traffic through an isolated DP interface on a different firewall first and use Security policy to inspect the traffic before forwarding it to the MGT port. This method enables you to inspect and control traffic without consuming a dedicated DP port.To use a DP port on a different firewall to inspect MGT port traffic before forwarding that traffic to the managed firewall:
- Configure a dedicated subinterface and a dedicated VLAN to isolate the traffic on the inspecting firewall’s DP port. Allow only management traffic on that subinterface and in that VLAN. Using a dedicated management subinterface with a dedicated management VLAN enables you to use the rest of the port’s bandwidth for production traffic while still isolating the management network traffic.
- Configure Security policy rules (see Scan All Traffic Destined for the Management Interface) that restrict access to the management interface based not only on IP addresses, but also on users (User-ID), applications (App-ID), and zones, and attach a best practice Vulnerability Protection profile.
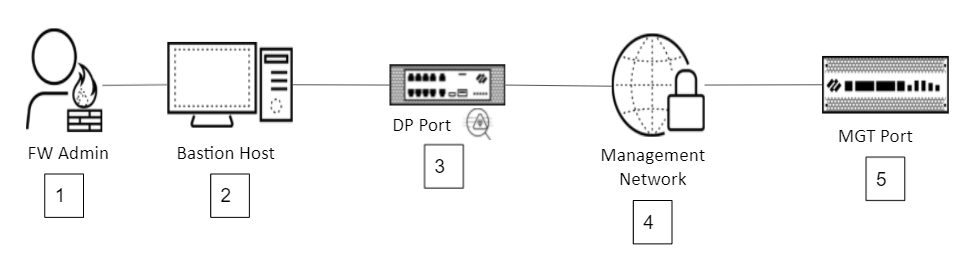
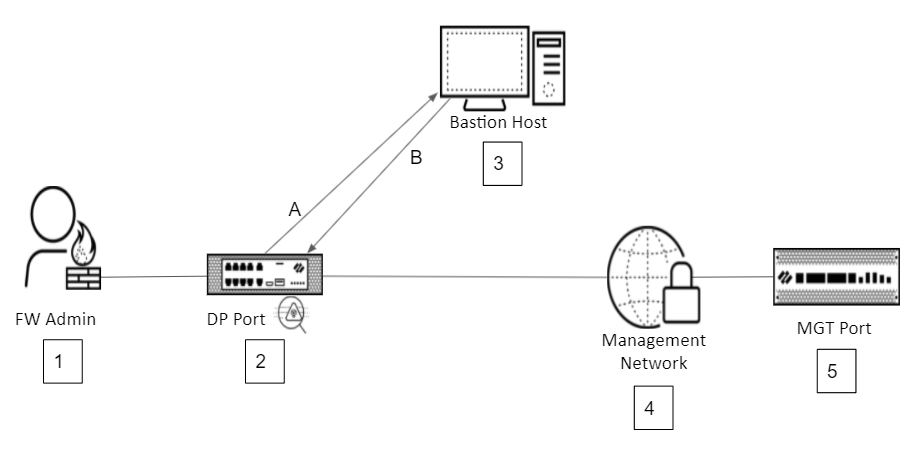
A number of network architectures enable inspecting traffic destined for the management port, many of which depend on company-specific needs. The following topology diagrams show two common high-level architecture examples of using a DP port on one firewall to inspect traffic destined for the MGT port of a firewall in the management network. Both architectures have these common components:- A firewall administrator attempting to access a device. Administrators who are external to the network access the network using a VPN.
- A bastion host that authenticates the administrator to prevent unauthorized access to the management network and management devices.
- A firewall with a dedicated subinterface and a dedicated VLAN on a DP port to isolate the management traffic. The firewall inspects management traffic before the traffic enters the management network. No management protocols are enabled on the DP port.
- An isolated management network, protected by the bastion host and the inspecting firewall.
- A device that the administrator manages using the MGT port.
After each diagram is a description of its packet flow.Management Isolation Topology 1![]() Packet Flow
Packet Flow- The firewall administrator (1) uses a VPN connection to attempt to log in and manage a firewall (5)
- The bastion host (2) authenticates the administrator’s credentials.
- If authentication succeeds, the bastion host (2) creates a new session and forwards the traffic to the inspecting firewall (3), which protects the management network. The firewall decrypts and inspects the traffic.
- If Security policy on the inspecting firewall (3) allows the administrator to access the firewall (5) in the management network, the inspecting firewall (3) forwards the traffic to the management network (4) and is restricted to connecting only to the device (5) that the administrator needs to manage. Security policy rules determine which devices the administrator can access, from where, using which applications, and even when, and how to inspect the traffic. Role-based access profiles control the privilege level the administrator has on each device.
- All subsequent traffic between the administrator (1) and the managed device (5) is inspected (3) for threats.
Management Isolation Topology 2![]() Packet Flow
Packet Flow- The firewall administrator (1) uses a VPN connection to attempt to log in and manage a firewall (5)
- The administrator’s traffic reaches the inspecting firewall (2) that protects the management network. The firewall decrypts and inspects the traffic, and then forwards it (A) to the bastion host (3).
- The bastion host (3) authenticates the administrator’s credentials.
- If authentication succeeds, the bastion host (3) creates a new session and forwards it (B) back to the inspecting firewall (2), where the traffic is inspected again.
- If Security policy on the inspecting firewall (2) allows the administrator to access the firewall (5) in the management network, the inspecting firewall (2) forwards the traffic to the management network (4) and is restricted to connecting only to the device (5) that the administrator needs to manage. Security policy rules determine which devices the administrator can access, from where, using which applications, and even when, and how to inspect the traffic. Role-based access profiles control the privilege level the administrator has on each device.
- All subsequent traffic between the administrator (1) and the managed device (5) is inspected (2) for threats.
- Management networks in which you cannot use another firewall’s DP port to inspect inbound MGT port traffic—Dedicate one of the firewall’s DP ports as the management interface so that you can apply Security policy to inspect and control management traffic (do not use the MGT port as the management interface). Do not allow any traffic on the DP port other than management traffic.The tradeoff is best security against not being able to use one DP port as a production port. If you can’t dedicate a firewall DP port to management traffic and must use the out-of-band MGT port, understand the risks and follow the rest of the best practices in this document to isolate the management network and restrict administrator and service access to only those that require access to manage the device.When you can’t use a DP port interface on a different firewall to inspect the traffic, dedicate a firewall DP port to management traffic or you won’t be able to apply Security policy or Threat profiles to inbound management traffic. That means you can’t inspect traffic, apply Vulnerability Protection profiles, or use Security policy to restrict MGT port access in a granular manner. You can use a loopback interface or another method to route the traffic from the MGT port to a DP port on the same firewall, but you still need to dedicate the DP port to the management traffic to isolate it on the device.
Manage Administrator Access
Controlling administrators and services that
manage a device boils down to applying the principle of least privilege
access. Understand which administrators and services need which
level of access—ask yourself, does an administrator need to configure
anything or is read-only access sufficient? Which areas does each administrator
manage?
The principle of least privilege access along with
ensuring proper authentication and activity monitoring is especially
important for Panorama access because Panorama controls multiple
firewalls.
- Replace the default admin account.The first time that you log into a firewall or Panorama, it forces you to change the default admin account password. The most secure action is to replace the default account with a new local account because the username “admin” is well known. Configure one local account to ensure that you can access the device if the network or the authentication server goes down and make it the only local account on the device. When you specify the new local account’s login and password, make them as secure as possible.
- If this is your first login to the device, perform the mandatory change to the default admin account password. (See Step 5 of Perform Initial Configuration).
- Create a new local superuser account with a strong password. In,DeviceAdministratorsAddan administrator, create a strong password based on the recommendations of National Institute of Standards and Technology (NIST) or local regional standards bodies, and applicable compliance regulations. Set theAdministrator TypeasDynamicandSuperuser.
- Log out of the firewall or Panorama and then log back in with the new, more secure local admin account that you just configured.
- Delete the default admin account so that your new local superuser account is the only local account on the device. In, select the default admin account and thenDeviceAdministratorsDeletethe account.
- Store the new local login and password credentials in the safest storage your enterprise has available in case emergency access is required.If for business reasons you must have more than one local account on the firewall, follow the best practices for password construction and usage later in this section. However, multiple local admin accounts are not a security best practice because each local account increases the risk of credential compromise resulting in unauthorized access.
- For all management access other than the default local administrator account, including API access, Configure a Firewall Administrator Account, use an external authentication system (see Configure Local or External Authentication for Firewall Administrators) with a password manager that generates passwords automatically and configure Multi-Factor Authentication (MFA) to prevent the unauthorized use of stolen credentials. The mandatory local superuser account is the only local account that you should have on the device (to use in case of emergency).NIST Special Publication 800-63B Digital Identity Guidelines describes standard best practices for digital authentication management in the U.S. Other regions may have local entities that provide standard best practices.If you cannot implement the best practice of using an external authentication system and must configure local administrators, Configure Certificate-Based Administrator Authentication to the Web Interface and Configure SSH Key-Based Administrator Authentication to the CLI to increase security. Always use MFA to protect against compromised credentials.
- Enable MFA for all management access with external authentication and authorization using RADIUS or SAML and corporate credentials (use your existing authentication system if you have one). If available, use privileged account management (PIM) and/or privileged identity management (PIM) solutions to secure credentials externally.If you have a strong authentication system using smart cards, Configure Certificate-Based Administrator Authentication to the Web Interface and Configure SSH Key-Based Administrator Authentication to the CLI. If your system can’t use MFA, import the certificate from the SAML provider to ensure secure access. If you manage certificates through a cloud provider, use client certificates to provide secure login access. Use client certificates for on-premise access to help protect servers against DoS attacks.
- Ensure that the password manager follows industry recommendations for constructing strong passwords, such as those published by NIST in NIST Special Publication 800-63B Digital Identity Guidelines and Easy Ways to Build a Better P@$5w0rd, and follow compliance regulations. Some regions may have local entities that require compliance regulations.
- Follow industry password usage best practices such as those published by NIST (or local standards authorities and compliance regulations).
- Change the master key on the device to prevent the default master key from being compromised and used to decode passwords. Take the following actions when you change the master key:
- Back up your configuration before you change the master key.
- In HA firewall configurations (standalone or Panorama-managed), disable Config Sync on both firewalls before you change the master key, and then configure the same master key on both devices before you re-enable Config Sync.
- On Panorama, WildFire and Log Collector devices must use the same master key as Panorama.
- Resetting the master key results in down time, so do it during a normal maintenance period.
- As with the local admin account, store the master key in the safest storage your enterprise has. You need the current master key to reset the master key (periodically reset the master key because eventually it runs out of unique encryptions). If you lose the master key, the only way to reset it is to reset the system to the factory default.If you lose the master key and factory reset the device and the default master key was changed before the reset, your backed up configuration won’t work on the device after the reset because the master key is different.
- Securing API access is similar to securing administrator access. The main difference is that after you configure administrator accounts and role-based access control (RBAC, see Step 4), you generate an API key, which contains an API’s authentication details, and use the key for subsequent API access instead of submitting the username and password credentials every time.Using API keys is a best practice because it enables you to Configure API Key Lifetime to enforce regular key rotation and harden your security posture. When you enable API key lifetimes on firewalls or Panorama, ensure that the systems and scripts which access those devices update their API keys at the end of the configured lifetime to prevent disrupting access.
- For SNMP access, if your infrastructure supports it, use SNMPv3 instead of SNMPv2c. SNMPv3 has many security improvements that are best practices to implement. SNMPv3:
- Enables granular, per-manager and per-agent access to MIB objects, so you can restrict access to the areas that the manager or agent needs to access. (SNMPv2c gives access to all MIBs to all managers and agents.)
- Enables granular, per-manager and per-agent authentication requirements.
- Provides encryption instead of transmitting data in cleartext and has stronger hashing algorithms.
Create the appropriate SNMP accounts and configure the firewall or Panorama to communicate with the SNMP Manager to Monitor Statistics Using SNMP.You can route SNMP traffic through the MGT port or through a DP port (must be a layer 3 Ethernet interface). If you use the MGT port, first send inbound traffic through a DP port on the same firewall or on another firewall so that you can control and inspect the incoming traffic using Security policy rules. Create a dedicated subinterface and a dedicated VLAN on the DP port to isolate the SNMP traffic.If the SNMP Manager is outside of the management network, route SNMP traffic through the bastion host or a similarly hardened server at the edge of the management network.If you use SNMP to manage routers or switches that are behind the firewall, configure the appropriate Security policy rule to allow the traffic.
- Limit access to users and services that manage the firewall.Only allow access for people and services that need to manage the device.
- Assign anAdmin Role Profile() to each administrator or group or department of administrators who have the same role and to each service or group of services that require the same access. Configure each profile sot that it limits access to only the areas of the device that each administrator, group of administrators, service, or group of services manages. Create individual, unique accounts for each administrator and for each service (for example, Terraform, Ansible, Tufin, etc.).DeviceAdmin Roles
- Configure administrative access only for people and services that need to manage the device.
- Configure a unique firewall administrator account for each administrator and for each service so that you can control and identify them individually. Administrative Role Types describes the access roles you can assign to administrators. Don’t use the same account for more than one administrator or for more than one service. API access for services works similarly to access for human administrators, including using role-based access.Apply the appropriateAdmin Role Profileto each individual account.
- Configure Admin Role Profiles and apply them to individual administrator and service accounts to control access privileges granularly. Profiles determine what the administrator(s) or service(s) can do and how they can do it (CLI, API, UI). Configure each profile to limit administrative privileges to only the areas of the device that an administrative group, department, individual, or service needs to manage. Do not over-provision administrators or services; allow only the required access privileges. Reference: Web Interface Administrator Access describes the web access privileges that you can assign or deny to administrators on the firewall and on Panorama.
- In Panorama, Configure Access Domains to control administrative access to specific Device Groups, templates, Log Collector Groups, etc.
- Add a Commit Description when you commit changes so that others can understand the reason for the change or addition.
- Configure a login timeout (Idle Timeout) to prevent administrators from leaving idle sessions open too long, specify a number ofFailed Attemptsto prevent brute force attempts to log in, and specify aLockout Timeto prevent further immediate access attempts after reaching theFailed Attemptslimit.
- Configure global timeout settings for the device inor configure more granular settings forDeviceSetupManagementAuthentication SettingsFailed AttemptsandLockout Timein.DeviceAuthentication Profile
- Check NIST Special Publication 800-63B Digital Identity Guidelines or local regional standards bodies or applicable compliance regulations for recommended settings.
If you allow API access, Configure API Key Lifetime based on what makes sense for your deployment to enforce regular key rotation—don’t over-provision the key lifetime. - Configure Administrator Activity Tracking and send the logs to an external server for auditing and monitoring.
- Configure System logs and use Log Forwarding to send them to an external server for auditing and monitoring. Use a method that notifies administrators of events so that they can take action in a timely manner.
- Use the Administrator Login Activity Indicators to Detect Account Misuse such as a high number of failed login attempts.
- Enforce audit comments in policy rules so that you can understand why an administrator created or modified a rule.
Isolate the Management Network
To help prevent unauthorized access to devices,
allow only management traffic, device administrators, and management
services on your dedicated management network.
Enable access to the management interface
only from within your dedicated management network. Do not enable
access to your management interface from the internet or from other
zones inside your enterprise security boundary.
- Use a bastion host (or a similarly hardened host dedicated only to management network access) with screen recording and the strongest authentication and access control to provide secure external access to your dedicated management network. Figure 1 and Figure 2 show example topologies with a bastion host.
- Only allow external connections to the firewall management interface from the bastion host so that all incoming management traffic is authenticated, regardless of whether that traffic originates in the internet or in a non-management zone in your internal network. This makes the secure bastion host the only authentication gateway to the management network. It also makes the bastion host’s IP address(es) and the secure management network the only IP addresses that need to access the management interface. Only allow access to device management ports from the management network zone—do not enable direct access from the internet or from any other zones.For example, external administrators and services can use a VPN to authenticate to and access the management network through the bastion host. After logging in to the bastion host, with the proper permissions, the administrator or service can then log in to the firewall or Panorama.Bastion hosts authenticate external traffic to the management network. However, not all inbound traffic comes through the bastion host. For example, internal management network traffic (originating in the management zone) does not authenticate through the bastion host. User-ID, EDLs, and some other types of traffic usually reach the firewall using a service route or from within the dedicated management network.
- For Panorama, ensure that all managed firewalls are in the dedicated management network(s). Expose the Panorama MGT port only to the management network(s).
- Ensure that administrators and services that require management access are allowed to access the bastion host so that you don’t accidentally cut off access for essential services.
- If you can’t use a bastion host as a single point of access to the management network, create a dedicated management network and allow management access only from hosts in that IP network. Include only the administrators and services that manage devices and the management interfaces of the devices in the management network. Do not allow access for anyone or any service that does not manage devices in the network. Require MFA for all management access. (For restricting permitted IP addresses on the firewall or Panorama management interface, see Step 2 in Restrict Access to the Management Interface.)
- Enable access to the management network only from the management zone (including the bastion host). Do not allow direct access to the management network from the internet or other zones.
- Require strict user authentication to access the management network.
- Authenticate multiple times. Authenticate at the bastion host and authenticate again at the firewall.
- Always require MFA to prevent attacks based on stolen credentials.
- If you need remote access to device management, use a VPN tunnel and authenticate through the bastion host and again through the firewall.
- If you don’t have a bastion host, use Authentication policy with MFA.
Regardless of where access originates, follow the same process: allow least privilege access through the bastion host (or equivalent hardened server dedicated to management network access), authenticate, and require MFA.
Restrict Access to the Management Interface
Although the most critical concept for safeguarding
the management interface is not to allow direct access from outside
of your dedicated management network, there are also many other
actions to take to secure the management interface.
- Allow direct inbound management interface access only from within the dedicated management network.Route internet access via VPN through a bastion host (or similarly hardened server that enables screen recording) for authentication to protect the management interface and network. If you can’t use a bastion host, allow access to the management interface only from within the management network. Do not allow direct access to the management interface from outside of the management network and never expose the management interface directly to the internet.
- Configure management interface settings to restrict the available services and to restrict the allowed IP addresses.
- If you use the MGT port as the management interface (mandatory on Panorama), configureManagement Interface Settings() to restrict the services and IP addresses available on the management interface.DeviceSetupInterfacesManagement
- Enable HTTPS and SSH, and if you want to test connectivity to the device or use monitoring and scanning tools, enable ping. Do not allow cleartext protocols (HTTP, Telnet).When enabling services, follow the principle of least privilege access—allow only the services you need to manage the device.
- Specify thePermitted IP Addresses. Ideally, the only allowed IP addresses are the bastion host’s IP addresses and required IP addresses within the management network. If you don’t have a bastion host or similarly hardened server to act as the border guard for your management network, allow only IP addresses in the management network to access the management port.Because you must use the MGT port as the Panorama management interface, you may need to specify IP addresses to allow the necessary services to access the device. You also may need to open Ports Used for Panorama to allow necessary services. Allow only the IP addresses and open only the ports for required services and follow the principle of least privilege access.
- Route incoming MGT port traffic to a DP interface on another firewall or on the same firewall (as described in Select the Management Interface with the examples Figure 1 and Figure 2) so that you can apply Security policy to the traffic. Do not configure management protocols on the DP interface you use to inspect the traffic destined for the MGT port. Configure the same type of Security policy rule for inbound traffic as described in Step 3 in Scan All Traffic Destined for the Management Interface.
- For SNMP access, follow the recommendations here.
- If you use a firewall DP port as the management interface, configure an Interface Management Profile () to restrict the services and IP addresses available on the management interface.NetworkNetwork ProfileInterface Mgmt
- Enable only the services that you require to manage the device (principle of least privilege access). For example, enable HTTPS for web UI access and SSH for CLI access. If you want to test connectivity to the device or use monitoring and scanning tools, enable ping. If you use the management port for SNMP, enable SNMP, etc. Do not allow cleartext protocols (HTTP, Telnet).Panorama may require allowing certain ports to support services.For firewalls that Panorama manages, if you require administrators to context switch on Panorama for web UI (HTTPS) access, then only enable SSH access on the firewall and enable both HTTPS and SSH access on Panorama.
- Specify thePermitted IP Addresses. Ideally, the only allowed IP addresses are the bastion host’s IP addresses and required IP addresses within the management network. If you don’t have a bastion host or similarly hardened server to act as the border guard for your management network, allow only IP addresses in the management network to access the management port.
- Create a Security policy rule for inbound traffic to the management interface (see Step 3 in Scan All Traffic Destined for the Management Interface).
- Treat and inspect external access the same way you treat and inspect internal access.
- Traffic from VPNs and external services should access the management interface through the bastion host or equivalent so that the traffic is treated and inspected the same way as internal traffic. Never expose the management interface directly to the internet.
- If you don’t have a bastion host, route access through the dedicated management network, authenticate with MFA, and inspect the traffic. Don’t allow a VPN or anything else that originates outside of the dedicated management network to access the management interface directly.
- If you have Panorama devices that manage firewalls in different networks, treat the traffic similarly to other external traffic—inspect the traffic and limit connectivity following the principle of least privilege access (Ports Used for Management Functions describes the ports and protocols for management functions).
- Allow access using only the most secure version of Transport Layer Security (TLS) encryption and most secure encryption settings.
- If you use the MGT port as the management interface, Configure an SSL/TLS Service Profile () that uses strong encryption to restrict access to the web interface and protect against weak protocols. Set theDeviceCertificate ManagementSSL/TLS Service ProfileMin VersiontoTLSv1.2and theMax VersiontoMax. Setting TLSv1.2 as theMin Versionautomatically blocks the weak 3DES and RC4 encryption algorithms and MD5 authentication algorithm.Depending on applicable compliance regulations, you may want to block other authentication, encryption, and key exchange algorithms, which you can do in the CLI using the configuration commandset shared ssl-tls-service-profile <profile-name> protocol-settings.
- Configure an SSH Service Profile (andDeviceCertificate ManagementSSH Service ProfileAdda management server profile) to restrict SSH access to the CLI to only the encryption cipher, authentication, and key exchange algorithms that meet your compliance regulations. If you don’t configure this profile, all algorithms are allowed, including weak encryption algorithms that you should block.
- As described in Step 5 of Manage Administrator Access, prevent brute force attacks on administrator logins and prevent leaving idle sessions open too long.
- Treat external services such as DNS, NTP, authentication, and Palo Alto Networks Services the same way that you treat other external traffic destined for the MGT port: run the traffic through a firewall DP port to inspect it before it reaches the MGT port.By default, the firewall uses the dedicated MTG port to access services that are outside of the management network. If you can’t access the required services through the management network and inspect them, Configure Service Routes () that use a DP port instead of the MGT port so that you can inspect the traffic. When you configure services routes:DeviceSetupServicesService Route Configuration
- Follow the principle of least privilege access and allow only the services you need.
- Create a dedicated subinterface and a dedicated VLAN on the DP interface to isolate the services traffic.
- Customize service routes by specifying a source interface and source address on the firewall or Panorama that does not have management access enabled.
- Apply Security policy to the traffic (see Scan All Traffic Destined for the Management Interface).Use App-ID in Security policy to ensure that only the required service applications are allowed. There are App-IDs for many common services (such as DNS) that you can use to lock down access and prevent unnecessary applications from accessing the device.Some services, such as SNMP, cannot use service routes. For these services, the same advice applies: before the traffic reaches the MGT port, run the traffic through a firewall DP port on a dedicated subinterface and a dedicated VLAN to isolate the traffic, and apply Security policy to control and inspect the traffic.
Replace the Certificate for Inbound Traffic Management
Replace the default certificate
for inbound management traffic that the firewall automatically
generates on the first boot up with a new certificate issued specifically
for your enterprise. Use a certificate signed by your enterprise
CA (if you have an enterprise PKI) for best security.
Keep Content and Software Updates Current
Ensure that content and software updates are
current so that the device receives the latest security patches
and threat updates.
- Subscribe to content update emails, security advisories, and software updates on the Customer Support Portal.
- Read the latest Release Notes before you upgrade PAN-OS.
- Follow Best Practices for Applications and Threats Content Updates when updating to the latest content release version.
Scan All Traffic
Destined for the Management Interface
Apply Security policy rules that scan all
inbound traffic to the management interface. To scan the inbound
traffic on the management interface, you must
run traffic destined for the MGT port through a firewall DP port
for inspection first or you must use a DP port as the management
interface, as described in Select the Management Interface. You cannot
apply Security policy directly to traffic on the MGT port, you must
run the traffic through a DP port.
- Create Security policy rules to allow access to the web and CLI interfaces.
- If you use a bastion host as the only gateway to your management network, configure a rule to allow traffic from the bastion host to the managed device. Configure rules to allow traffic from necessary users and services within the management network (restricted to only the necessary applications, etc.).
- If you do not use a bastion host, create the required rules to allow access only from the management zone, using only the necessary applications and allowing only the necessary users or services. All management traffic should come from within the management zone. Inspect traffic entering the network from a VPN or other secure tunnel before it enters the management zone.
- Create a best practice Vulnerability Protection profile by cloning the preconfigured strict Vulnerability profile and then modifying it so that it only scans the signatures from the requesting server.
- After you clone and modify the best practice Vulnerability Protection profile, delete the profile rules that haveclientas theHost Typebecause you only need to scan the inbound traffic.
- Attach the Vulnerability Protection profile to every Security policy rule that controls inbound access to the management interface.
- Tighten each Security policy rule to allow only the necessary users, services, and applications.
- Allow only the IP addresses you specified in the Interface Management Profile.
- Specify the management network zone(s) as both the source and destination zones (both the bastion host and the device’s management port are in the management network zone(s)).
- Allow only the applications and services that you need to manage the device (use App-ID).
- Specify user groups and/or individual users (you must implement User-ID).
- Include the modified best practice Vulnerability Protection profile (Step 2).
- Log traffic that matches the rule (this is enabled by default) and forwards logs to external log storage to be available for analysis (you must Configure Log Forwarding).
- If temporary access is required, for example for a contractor, configure a non-recurring schedule () to specify when that access is allowed and when it stops. Attach the schedule to the Security policy rule that allows the temporary access.ObjectsSchedules
- Decrypt inbound traffic to the management interface so the firewall can inspect it. If you use the MGT port as the management interface, you must first route the traffic through the DP port of a firewall to decrypt and inspect the traffic (see Select the Management Interface).
- Apply an SSL Inbound Inspection Decryption profile to the traffic.
- Follow Decryption Best Practices to eliminate weak ciphers and algorithms based on applicable compliance regulations.Do not decrypt management or service route traffic from the firewall to Panorama.Do not configure SSL Forward Proxy decryption to decrypt outbound management traffic from the firewall or Panorama.