Create Best Practice Security Profiles for the Internet Gateway
Table of Contents
Expand all | Collapse all
-
- What Is a Best Practice Internet Gateway Security Policy?
- Why Do I Need a Best Practice Internet Gateway Security Policy?
- How Do I Deploy a Best Practice Internet Gateway Security Policy?
- Create User Groups for Access to Allowed Applications
- Decrypt Traffic for Full Visibility and Threat Inspection
-
- Transition Vulnerability Protection Profiles Safely to Best Practices
- Transition Anti-Spyware Profiles Safely to Best Practices
- Transition Antivirus Profiles Safely to Best Practices
- Transition WildFire Profiles Safely to Best Practices
- Transition URL Filtering Profiles Safely to Best Practices
- Transition File Blocking Profiles Safely to Best Practices
- Create Best Practice Security Profiles for the Internet Gateway
- Monitor and Fine-Tune the Policy Rulebase
- Remove the Temporary Rules
- Maintain the Rulebase
Create Best Practice Security Profiles for the Internet Gateway
Most malware sneaks onto the network in legitimate applications or services. To safely
enable applications, you must scan all allowed traffic for threats. Attach Security
profiles to all Security policy rules that allow traffic so that you can detect
threats—both known and unknown—in your network traffic. The following best practice
recommendations focus on the tightest security. Attach a URL Filtering profile to all
rules that allow internet-bound traffic and attach the other profiles to all allow
rules.
More than 90 percent of web traffic is encrypted. Enable decryption to gain visibility into traffic,
use Security profiles to inspect the payload, and prevent malicious events.
Consider adding your best practice security profiles to a default security profile group. When you
name a security profile group default, the firewall
automatically attaches it to every new Security policy rule you create and ensures
that the firewall inspects the traffic for malicious activity.
Also consider creating purpose-built Security profile groups for different types of
traffic. Security profile groups make applying all the necessary profiles to
Security policy rules easy and ensure that no critical profile is
forgotten.
- Best Practice Internet Gateway File Blocking Profile
- Best Practice Internet Gateway Antivirus Profile
- Best Practice Internet Gateway Vulnerability Protection Profile
- Best Practice Internet Gateway Anti-Spyware Profile
- Best Practice Internet Gateway URL Filtering Profile
- Best Practice Internet Gateway WildFire Analysis Profile
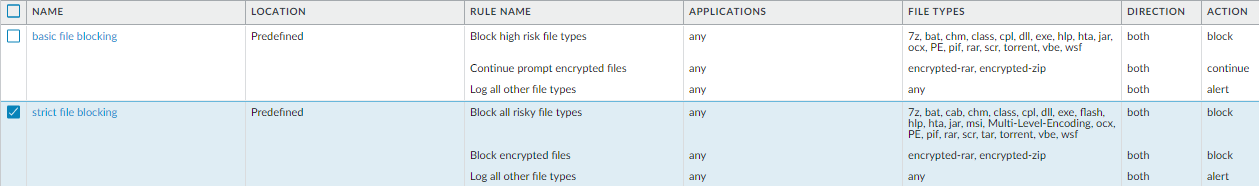
Best Practice Internet Gateway File Blocking Profile
Use these File Blocking settings as a best practice at your internet
gateway.
Use the predefined strict file blocking profile to block file
types commonly included in malware attack campaigns that have no real use case for
upload and download. Blocking these file types reduces the attack surface. The
predefined strict profile blocks batch files, DLLs, Java class files, help files,
Windows shortcuts (.lnk), BitTorrent files, .rar files, .tar files, encrypted-rar
and encrypted-zip files, multilevel encoded files (files encoded or compressed up to
four times), .hta files, and Windows Portable Executable (PE) files, which include
.exe, .cpl, .dll, .ocx, .sys, .scr, .drv, .efi, .fon, and .pif files. The predefined
strict profile alerts on all other file types for visibility into other file
transfers so that you can determine if you need to make policy changes.
In some cases, the need to support critical applications might prevent you from
blocking all of the strict profile’s file types. Follow the Transition File Blocking Profiles Safely to Best Practices advice to help determine
whether you need to make exceptions in different areas of the network. Review
the data filtering logs (MonitorLogsData Filtering) to identify file types and talk with business stakeholders about
the file types their applications require. Based on this information, clone the
strict profile and modify it as needed to allow only the other file type(s) that
you need to support the critical applications. You can also use the
Direction setting to restrict files types from
flowing in both directions or block files in one direction but not in the other
direction.
You might also require a few protocols often used for malicious purposes for
activities such as Windows updates. The strict file blocking
profile blocks .exe., .dll, .pe, and .cab files. To make exceptions to allow
protocols for a specific activity such as Windows updates:
- Create a specific Security policy rule that allows only the required users and business applications that use the protocols you want to block for other traffic.
- Clone your strict File Blocking profile, modify it to allow the required protocols, and then attach it to the rule.
- Place the rule above a Security policy rule with a File Blocking profile that blocks the protocols for all other traffic.
This method enables you to use potentially malicious file types in a safe way that
enables business applications while blocking malicious traffic. Fine-tune the
profiles and rulebase to allow any required exceptions.
Why Do I Need This Profile?
Attackers can deliver malicious
files in many ways:
- Attachments or links in corporate or personal email.
- Links or IMs in social media and other sources.
- Exploit Kits.
- File sharing applications (such as FTP, Google Drive, or Dropbox).
- USB drives.
Attaching a strict file blocking profile prevents these types of attacks and
reduces your attack surface.
If you choose not to block all PE files, send all unknown files to WildFire for
analysis. Set the Action to continue to prevent drive-by
downloads, which is when an end user downloads content that installs malicious
files, such as Java applets or executables, without the user's knowledge.
Drive-by downloads can occur when users visit web sites, view email messages, or
click pop-up windows meant to deceive them. Educate users that if they are
prompted to continue with a file transfer they didn’t knowingly initiate, they
might be subject to a malicious download. In addition, use file blocking with
URL filtering to limit the categories in which users can transfer files to
reduce the attack surface if you must allow file types that might carry
threats.
Best Practice Internet Gateway Antivirus Profile
Use these Antivirus security profiles settings as a best practice at your
internet gateway.
To ensure availability for business-critical applications, follow the Transition Antivirus Profiles Safely to Best Practices advice as you move from your
current state to a best practices profile. The goal is to transition to profile as
shown here and attach it to all Security policy rules that allow traffic. The
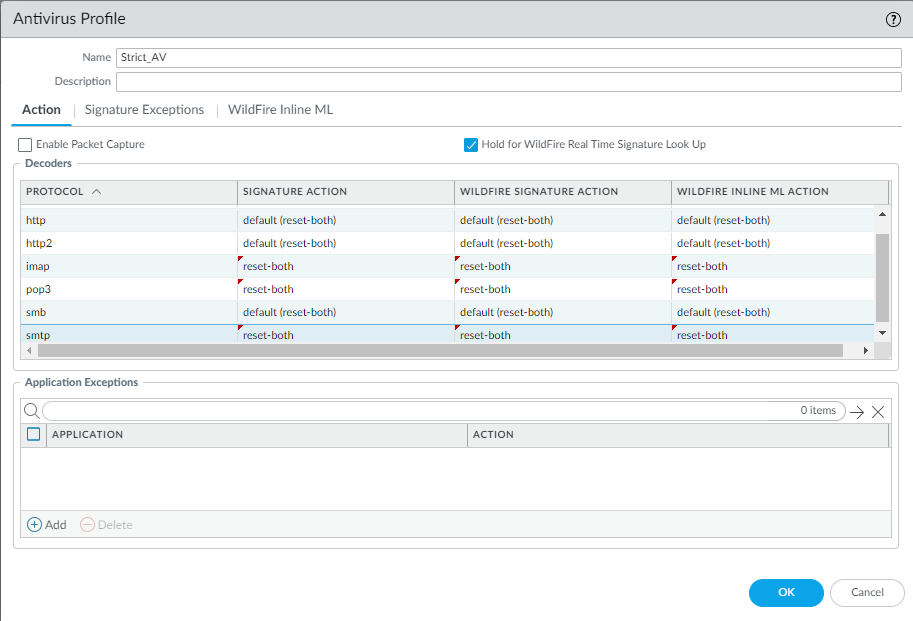
Antivirus profile protocol decoders detect and prevent viruses and malware from
being transferred over seven protocols: FTP, HTTP, HTTP2, IMAP, POP3, SMB, and SMTP.
Set WildFire Signature and WildFire Inline ML actions for all seven protocols (the
Antivirus profile also enforces actions based on WildFire signatures) and if you
haven't already done it, enable real-time signature lookup as shown in Transition Antivirus Profiles Safely to Best Practices.
Configure the cloned Antivirus profile to reset both the client and the server for
all seven protocol decoders and WildFire actions, and then attach the profile to the
Security policy allow rules.
If you treat internal applications differently than external applications, you
might need an Antivirus profile for internet-facing traffic and a different
Antivirus profile for internal traffic.
Enable real-time signature lookup globally and in the Antivirus profile to hold files
until the firewall receives the latest real-time antivirus signature from the
cloud:
- Enable globally: DeviceSetupContent-IDContent-ID SettingsRealtime Signature Lookup, enable Hold for WildFire Real Time Signature Look Up and set the Action on Real Time Siganture Timeout to Reset Both. You must enable real-time signature lookup globally to enable it in Antivirus profiles.
- Enable Hold for WildFire Real Time Signature Lookup in the Antivirus profile. Holding files to ensure that WildFire gets the latest antivirus signatures protects you from zero-day malware and outdated antivirus signatures that you might be exposed to if you forward files without holding them for the latest signatures.
Why do I need this profile?
By attaching Antivirus profiles to
all Security rules, you block known malicious files (malware, ransomware bots,
and viruses) as they come into the network. Common ways for users to receive
malicious files include email attachments, links to download malicious files,
and silent compromise facilitated by Exploit Kits that exploit a vulnerability
and then automatically download malicious payloads to the end user’s
device.
Best Practice Internet Gateway Vulnerability Protection Profile
Use these Vulnerability Protection security profile settings as a best practice
at your internet gateway.
Attach a Vulnerability Protection profile to all
allowed traffic to protect against buffer overflows, illegal code execution, and
other attempts to exploit client- and server-side vulnerabilities. To ensure
availability for business-critical applications, follow the Transition Vulnerability Protection Profiles Safely to Best Practices advice as you move from your
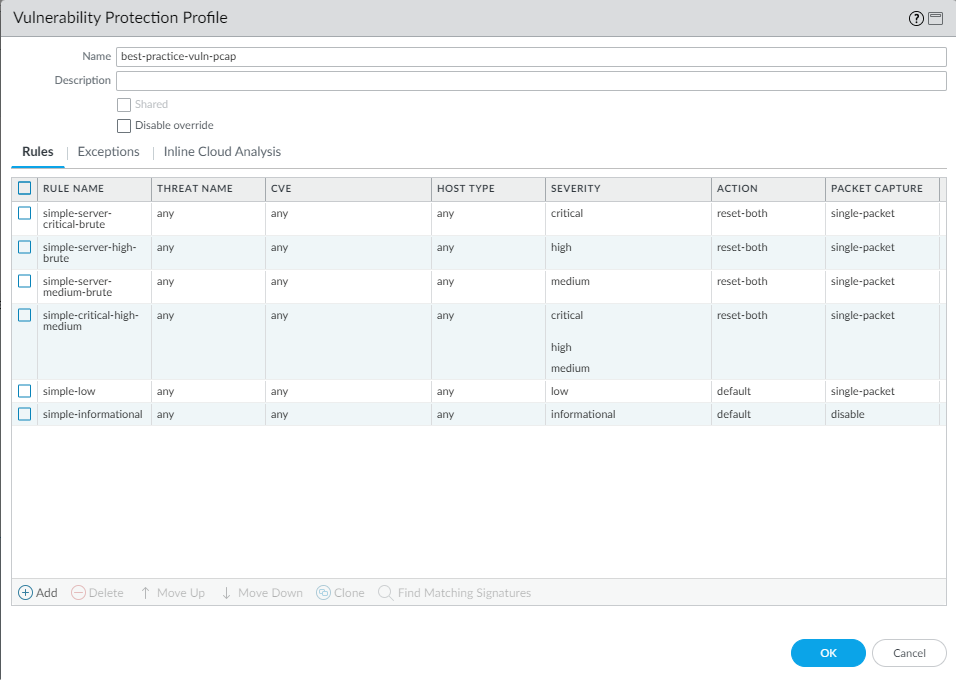
current state to the best practice profile. Clone the predefined strict
Vulnerability Protection profile and edit it to create the best practice
profile:
- Change the Action in the three brute force rules to reset-both and Packet Capture to single-packet to transition from alerting on brute-force attack events to blocking them.
- Consolidate critical, high, and medium severity events for servers and clients into one rule. Set the Action to reset-both and set Packet Capture to single-packet. This simplifies the profile and works because the profile uses the same action and the same packet capture settings for these severities.For profiles that control internal (east-west) traffic, blocking medium severity events might impact business applications. If blocking impacts business applications, create a separate rule in the profile for medium severity events with the Action set to alert. Apply the profile only to internal traffic.
- To simplify the profile, consolidate low severity events for servers and clients into one rule. Set the Action to default and set Packet Capture to single-packet.
- Consolidate informational events for servers and clients into one rule. Set the Action to default and set Packet Capture to disable.PCAPs for informational events generate a relatively high volume of traffic that usually isn't useful compared captures about potential threats.
- Apply extended PCAP instead of single PCAP to high-value traffic to which you apply the alert Action. Apply PCAP using the same logic you use to decide what traffic to log and take PCAPs of the traffic you log. Apply single PCAP to traffic you block. The default number of packets that extended PCAP records and sends to the management plane is five packets, which is the recommended value. In most cases, capturing five packets provides enough information to analyze a threat. If too much PCAP traffic goes to the management plane, then capturing more than five packets might result in dropping PCAPs.
If you want more granularity for fine-tuning the profile, create separate rules
with the Action and Packet Capture
settings as described. For example, create a rule for critical, high, and medium
severities for servers and another similar rule for clients, or create separate
rules for each severity for clients and for servers to achieve the level of
granularity and control you want.
Packet captures consume management plane resources. Check system resources (for
example, DashboardSystem Resources) to understand usage before and after you implement packet
capture to ensure that your system has sufficient resources to take the packet
captures you want.
Enable packet capture (PCAP) for each rule so you
can track down the source of potential attacks. Download content updates automatically and install
them as soon as possible so that the signature set is always up to date.
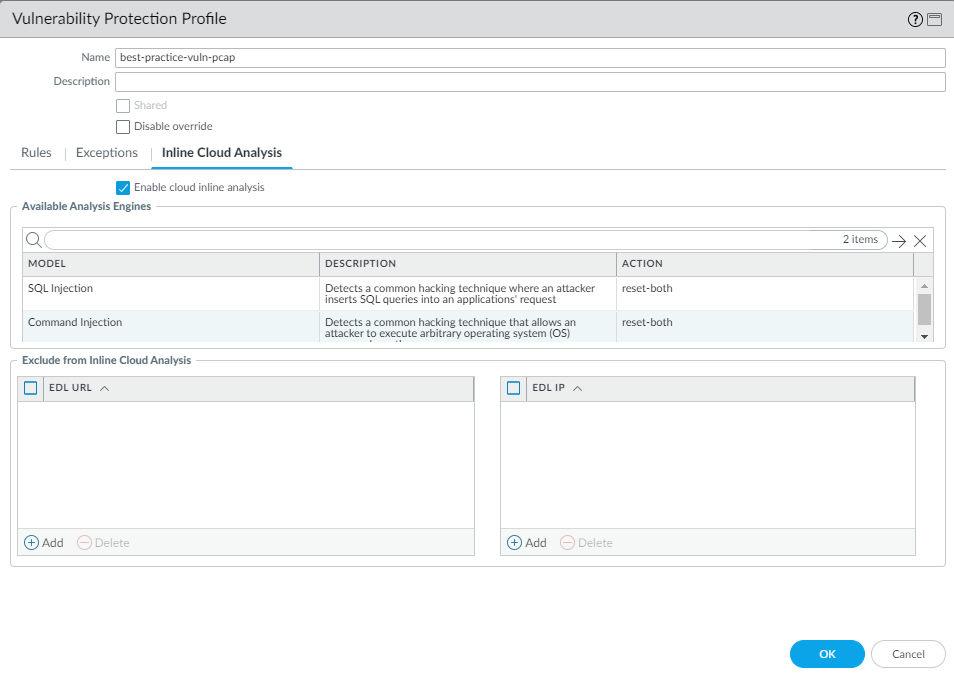
For Inline Cloud Analysis, set the
Action to reset-both to block
common hacking techniques.
Why do I need this profile?
Without strict vulnerability
protection, attackers can leverage client- and server-side vulnerabilities to
compromise end-users. For example, an attacker could leverage a vulnerability to
install malicious code on client systems or use an Exploit Kit to automatically
deliver malicious payloads to end users. Vulnerability Protection profiles
prevent an attacker from using vulnerabilities on internal hosts to move
laterally within your network.
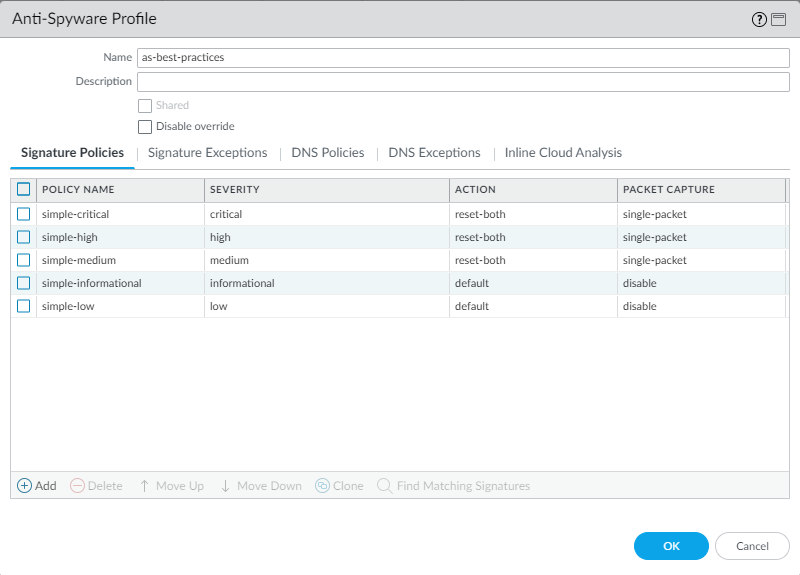
Best Practice Internet Gateway Anti-Spyware Profile
Use these Anti-Spyware security profile settings as a best practice at your
internet gateway.
Attach an Anti-Spyware profile to all allowed
traffic to detect command-and-control traffic (C2) initiated from malicious code
running on a server or endpoint and prevent compromised systems from establishing an
outbound connection from your network. Clone the predefined strict Anti-Spyware
profile and edit it. To ensure availability for business-critical applications,
transition Anti-Spyware Profiles Safely to Best
Practices. Edit the profile to enable DNS sinkhole and packet capture (PCAP) to help you track
down endpoints that attempt to resolve malicious domains. Retain the default
Action to reset the connection when the firewall detects
a medium, high, or critical severity threat, and enable single PCAP for those
threats.
Allow traffic only to sanctioned DNS servers. Use the DNS Security service to prevent connections to
malicious DNS servers.
If you treat internal applications differently than external applications, you
might need an Anti-Spyware profile for internet-facing traffic and a different
Anti-Spyware profile for internal traffic.
Don’t enable PCAP for informational activity because it generates a relatively high
volume of traffic and isn't usually useful compared to PCAPs for potential threats.
Apply extended PCAP instead of single PCAP to high-value traffic to which you apply
the alert Action. Apply PCAP using the same logic you use to
decide what traffic to log and take PCAPs of the traffic you log. Apply single PCAP
to traffic you block. The default number of packets that extended PCAP records and
sends to the management plane is five packets, which is the recommended value. In
most cases, capturing five packets provides enough information to analyze a threat.
If too much PCAP traffic goes to the management plane, then capturing more than five
packets might result in dropping PCAPs.
Packet captures consume management plane resources. Check system resources (for
example, DashboardSystem Resources) to understand usage before and after you implement packet
capture to ensure that your system has sufficient resources to take all the
packet captures you want.
Configure DNS Policies to protect your network from DNS queries to malicious domains.
For best security use the DNS Security service to secure your DNS traffic.
Otherwise, use locally available, downloadable DNS signature sets (packaged with the
antivirus and WildFire updates).
Sinkhole malicious traffic instead of blocking it to identify potentially compromised
hosts that attempt to access suspicious domains by tracking the hosts and preventing
them from accessing those domains. For domain categories that pose a greater threat,
configure a higher log severity level and/or packet capture settings to help
determine if the attack was successful, identity the attack methods, and provide
better overall context.
Configure the default Palo Alto Networks DNS and the individual DNS signature source categories (PAN-OS
10.0 and later):
| DNS Signature Source | Log Severity | Policy Action | Packet Capture |
|---|---|---|---|
Palo Alto Networks Content | |||
default-paloalto-dns | default | sinkhole | extended-capture |
DNS Security | |||
Command And Control Domains | high (default) | sinkhole | extended-capture |
Dynamic DNS Hosted Domains | informational (default) | sinkhole | single-packet |
Grayware Domains | low (default) | sinkhole | single-packet |
Malware Domains | medium (default) | sinkhole | single-packet |
Parked Domains | informational (default) | sinkhole | disable (default) |
Phishing Domains | low (default) | sinkhole | single-packet |
Proxy Avoidance and Anonymizers | low (default) | sinkhole | single-packet |
Newly Registered Domains | informational (default) | sinkhole | single-packet |
Ad Tracking Domains | informational (default) | sinkhole | single-packet |
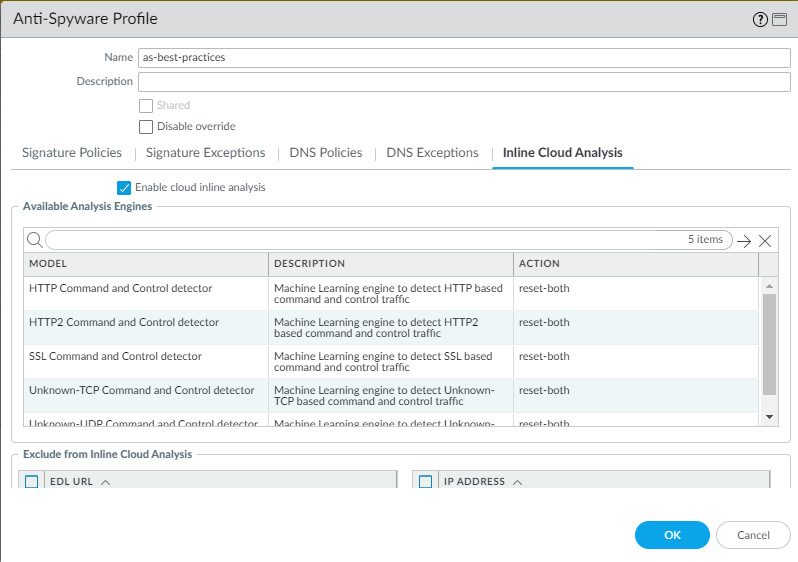
For Inline Cloud Analysis (requires Advanced Threat Prevention
subscription), Enable cloud inline analysis on all outbound
traffic. Set the Action to reset-both
for all models.
Air-gapped environments can't use Advanced Threat Prevention because it’s a
cloud service and requires a cloud connection.
Best Practice Internet Gateway URL Filtering Profile
Use these URL Filtering security profile settings as a best practice at your
internet gateway.
For the most up-to-date Site Access recommendations, see
URL Categories.
Use Advanced URL Filtering to prevent access
to web content at high risk for malicious activity. Attach a URL Filtering profile to all rules that
allow access to web-based applications to protect against URLs that Palo Alto
Networks has observed hosting malware, potential malware, exploitative content, or
content posing legal risk.
You must enable decryption to take advantage of URL
filtering because you must decrypt traffic to reveal the exact URL so the
firewall can take the appropriate action. At the least, decrypt high- and
medium-risk traffic.
To ensure availability for business-critical applications, Transition URL Filtering Profiles Safely to Best Practices. A best practice URL Filtering
profile blocks access and credential submissions to all known dangerous URL
categories. The goal is to block the following categories:
- Set all actions for malicious URL categories to block for both Site Access and User Credential Submission. Make appropriate exceptions for PEN testing, threat research, and InfoSec as needed:
- command-and-control—URLs and domains that malware or compromised systems use to communicate with an attacker’s remote server.
- compromised-website—Benign or legitimate sites that have been hacked or infected with content such as malicious scripts, viruses, trojans, or executables.
- grayware—These sites don’t meet the definition of a virus or pose a direct security threat, but they influence users to grant remote access or perform other unauthorized actions. Grayware sites include scams, illegal activities, criminal activities, adware, and other unwanted and unsolicited applications, including “typosquatting” domains.
- malware—Sites known to host malware or used for command-and-control activities.
- phishing—Sites known to host credential and personal information phishing pages, including technical support scams and scareware.
- ransomware—Sites that are known to distribute ransomware.
- scanning-activity—Sites that probe for existing vulnerabilities or conduct targeted attacks.
- Some URL categories have the strong potential to be malicious but aren't definitely malicious. Set all actions for these URL categories to block both Site Access and User Credential Submission. Make appropriate exceptions for PEN testing, threat research, and InfoSec as needed:
- dynamic-dns—Systems with dynamically assigned IP addresses that are often used to deliver malware payloads or command-and-control malware.If you have a business purpose for a dynamic DNS domain, then make sure you allow those URLs in your URL Filtering profile.
- encrypted-dns—Sites for DNS resolver service providers, which offer security and privacy for end users by encrypting DNS requests and responses using protocols like DNS over HTTPS (DoH).
- hacking—Sites relating to illegal or questionable access to or use of equipment and software. Includes sites that facilitate the bypass of licensing and digital rights systems.Make exceptions to this category for the appropriate PEN testing and threat research users.
- insufficient-content—Websites and services that present test pages, no content, provide API access not intended for end-user display, or require authentication without displaying any other content.
- newly-registered-domains—Domains that domain generation algorithms often generate or bad actors generate for malicious activity.
- not-resolved—If the PAN-DB cloud is unreachable and the URL isn't in the firewall’s URL Filtering cache, the firewall can't the resolve and identify the URL category.For highest security, enable Hold client request for category lookup to give the firewall more time to resolve the URL category. This extends the time the firewall has to query the category type from the cloud and results in better security but might increase latency.
- parked—Domains that will often be used for credential phishing or personal information theft.
- proxy-avoidance-and-anonymizers—URLs and services often used to bypass content filtering products.
- unknown—Sites not yet identified by Palo Alto Networks (PAN-DB).PAN-DB real-time updates learn unknown sites after the first attempt to access an unknown site, so the firewall identifies unknown URLs quickly and then handles them based on the actual URL category of the site.If availability is critical to your business and you must allow traffic from unknown sites, apply the strictest Security profiles to the traffic and investigate all alerts for the traffic.
- Set the action for Site Access and User Credential Submission to block the following URL categories based on legal or business requirements and potential liability risk. If you don’t block these sites, alert on and apply strict Security profiles to the traffic.
- abused-drugs—Sites that promote illegal and legal drug abuse.
- adult—All sites that contain adult content of any kind, including games and comics as well as sexually explicit material, media, art, forums, and services.
- AI-code-assistant—Sites that provide services to assist with code writing, optimization, and generation using artificial intelligence. This may include platforms that support code completion, bug detection, and code suggestions.
- AI-conversational-assistant—AI-driven conversational assistants that utilize natural language processing (NLP) and machine learning to facilitate human-like interactions. These assistants are designed to support a wide range of tasks through conversational interfaces, typically accepting text and files as input and are designed to provide contextual, interactive support.
- AI-writing-assistant—Sites that leverage artificial intelligence and machine learning to enhance productivity by providing text-based content generation capabilities across industries such as marketing, eCommerce, SEO, and education. These platforms improve efficiency and streamline tasks like SEO-optimized writing, customer service and prompt generation, while also supporting a broad range of content creation needs from creative writing and academic assistance to marketing and customer review management.
- AI-data-and-workflow-optimizer—Data optimization sites that utilize artificial intelligence to provide functionalities such as automated data cleaning, transformation, and analysis, as well as streamlining and managing repetitive workflow tasks to improve efficiency and productivity.
- AI-platform-service—Sites that provide comprehensive tools and services for GenAI application development, including chatbot creation, model training, deployment, and optimization, as well as access to pre-trained models and code libraries. These platforms streamline the development process, facilitate collaboration, and enable developers to focus on core application logic without managing infrastructure or building models from scratch.
- AI-meeting-assistant—Sites that leverage artificial intelligence to provide meeting assistance services such as summarizing key points, highlighting action items, and generating follow-up task lists.
- copyright-infringement—Domains with illegal content that poses a liability risk.
- extremism—Websites promoting terrorism, racism, child exploitation, etc.
- gambling—Lottery and gambling sites.
- peer-to-peer—Peer-to-peer sharing of torrents, download programs, media files, or other software applications. (Doesn't include shareware or freeware sites.)
- questionable—Sites that promote tasteless humor, offensive content targeting specific demographics.
- weapons—Sale, review, descriptions of, or instructions regarding weapons and their use.
Also consider how you want to handle the cryptocurrency and alcohol-and-tobacco URL categories. Either alert on them and apply strict Security profiles to the traffic or block them, depending on your business needs. - Block User Credential Submission for the high-risk category. (Don’t block Site Access for the high-risk category.)
In addition to blocking known bad categories, alert on all other categories so you
have visibility into the sites your users visit. If you need to phase in a block
policy rule, set categories to continue and create a custom response page to educate
users about your acceptable use policies and alert them to the fact they are
visiting a site that might pose a threat. This paves the way for you to block the
categories after a monitoring period.

Disable Log Container Page Only in the profile, which is
enabled by default. If you only log container pages, you lose visibility into
functional applications such as posting, uploading, downloading, etc. Disable
Log Container Page Only to see the complete log so that
you see the real functional application.
If your environment is a school that takes federal funding, enable Safe
Search Enforcement (legal requirement).
If you run PAN-OS 9.0.4 or later, enable the option to hold client requests (enter
config then set deviceconfig setting ctd
hold-client-request yes) to ensure that the firewall handles user
web requests as securely as possible. By default, the firewall allows requests while
it looks up an uncached URL category in PAN-DB and then enforces the appropriate
policy rule when the server responds. Hold requests during this lookup to maximize
security (this might increase latency but is the most secure option). For details,
see Configure URL Filtering.
What If I Can’t Block All of the Recommended Categories?
If users need access to sites in blocked categories for business purposes, create
an allow list for just the specific sites in a rule that allows only the
necessary users and applications, if you feel the risk is justified. Understand
local laws and regulations that govern the types of sites you can block, can’t
block, and must block. On risky categories for which you decide to allow access,
set up credential phishing protection
to ensure that users don't submit corporate credentials to a site that might
host a phishing attack.
If you allow traffic to malicious and potentially malicious URL categories or to
websites that pose potential liability issues, the risks include:
- Malicious URL categories:
- command-and-control—Command-and-control URLs and domains used by malware or compromised systems to surreptitiously communicate with an attacker's remote server to receive malicious commands or exfiltrate data.
- compromised-website—Benign or legitimate sites that have been hacked or infected with content such as malicious scripts, viruses, trojans, or executables.
- grayware—Websites and services that don't meet the definition of a virus but are malicious or questionable and might degrade device performance and cause security risks. Prior to content release version 8206, the firewall placed grayware in either the malware or questionable URL category. If you're unsure about whether to block grayware, start by alerting on grayware, investigate the alerts, and then decide whether to block grayware or continue to alert on grayware.
- malware—Sites known to host malware or used for command and control (C2) traffic and that might exhibit Exploit Kits.
- phishing—Known to host credential phishing pages or phishing for personal identification.
- ransomware—Sites that are known to distribute ransomware.
- scanning-activity—Sites that probe for existing vulnerabilities or conduct targeted attacks.
- Potentially malicious URL categories:
- dynamic-dns—Hosts and domain names for systems with dynamically assigned IP addresses and which are oftentimes used to deliver malware payloads or C2 traffic. Also, dynamic DNS domains don't go through the same vetting process as domains that are registered by a reputable domain registration company, and are therefore less trustworthy.
- encrypted-dns—Sites for DNS resolver service providers, which offer security and privacy for end users by encrypting DNS requests and responses using protocols like DNS over HTTPS (DoH).
- hacking—Sites relating to illegal or questionable access to or use of equipment and software. Includes sites that facilitate the bypass of licensing and digital rights systems.Make exceptions to this category for the appropriate PEN testing and threat research users.
- insufficient-content—Websites and services that present test pages, no content, provide API access not intended for end-user display, or require authentication without displaying any other content.
- newly-registered-domain—Newly registered domains are often generated purposely or by domain generation algorithms and used for malicious activity.
- not-resolved—If the PAN-DB cloud is unreachable and the URL isn't in the firewall’s URL Filtering cache, the firewall can't resolve and identify the URL category.For highest security, enable Hold client request for category lookup to give the firewall more time to resolve the URL category. This extends the time the firewall has to query the category type from the cloud and results in better security but might increase latency.
- parked—Domains registered by individuals, oftentimes later found to be used for credential phishing. These domains might be similar to legitimate domains, for example, pal0alto0netw0rks.com, with the intent of phishing for credentials or personal identify information. Or, they might be domains that an individual purchases rights to in the hopes that it might be valuable someday, such as panw.net.
- proxy-avoidance-and-anonymizers—URLs and services often used to bypass content filtering products.
- unknown—Sites that have not yet been identified by PAN-DB. If availability is critical to your business and you must allow the traffic, alert on unknown sites, apply the best practice Security profiles to the traffic, and investigate the alerts.PAN-DB Real-Time Updates learns unknown sites after the first attempt to access an unknown site, so unknown URLs are identified quickly and become known URLs that the firewall can then handle based on the actual URL category.
- URL categories with potential liability risk:
- abused-drugs—Websites that promote the abuse of legal and illegal drugs, the sale and use of drug paraphernalia, and manufacturing or selling drugs.
- adult—Websites that might not be appropriate in the workplace.
- AI-code-assistant—Sites that provide services to assist with code writing, optimization, and generation using artificial intelligence. This may include platforms that support code completion, bug detection, and code suggestions.
- AI-conversational-assistant—AI-driven conversational assistants that utilize natural language processing (NLP) and machine learning to facilitate human-like interactions. These assistants are designed to support a wide range of tasks through conversational interfaces, typically accepting text and files as input and are designed to provide contextual, interactive support.
- AI-writing-assistant—Sites that leverage artificial intelligence and machine learning to enhance productivity by providing text-based content generation capabilities across industries such as marketing, eCommerce, SEO, and education. These platforms improve efficiency and streamline tasks like SEO-optimized writing, customer service and prompt generation, while also supporting a broad range of content creation needs from creative writing and academic assistance to marketing and customer review management.
- AI-data-and-workflow-optimizer—Data optimization sites that utilize artificial intelligence to provide functionalities such as automated data cleaning, transformation, and analysis, as well as streamlining and managing repetitive workflow tasks to improve efficiency and productivity.
- AI-platform-service—Sites that provide comprehensive tools and services for GenAI application development, including chatbot creation, model training, deployment, and optimization, as well as access to pre-trained models and code libraries. These platforms streamline the development process, facilitate collaboration, and enable developers to focus on core application logic without managing infrastructure or building models from scratch.
- AI-meeting-assistant—Sites that leverage artificial intelligence to provide meeting assistance services such as summarizing key points, highlighting action items, and generating follow-up task lists.
- copyright-infringement—Domains with illegal content, such as content that allows the illegal download of software or other intellectual property, which poses a potential liability risk. This category was introduced to enable adherence to child protection laws required in the education industry as well as laws in countries that require internet providers to prevent users from sharing copyrighted material through their service.
- extremism—Websites promoting terrorism, racism, fascism, or other extremist views discriminating against people or groups of different ethnic backgrounds, religions, or other beliefs. This category was introduced to enable adherence to child protection laws required in the education industry. In some regions, laws and regulations might prohibit allowing access to extremist sites, and allowing access might pose a liability risk.
- gambling—Lottery or gambling websites that facilitate the exchange of real or virtual money. Also websites that provide tutorials, advice, or other information about gambling, including betting odds and pools.
- peer-to-peer—Websites that clients for or access to peer-to-peer sharing of torrents, download programs, media files, or other software applications, primarily to protect against BitTorrent download capabilities. Does not include shareware or freeware sites.
- questionable—Websites containing potentially offensive content targeting specific demographics of individuals or groups, criminal activity, illegal activity, and get rich quick schemes.
- weapons—Websites that sell, review, describe, or provide instructions about weapons and their use that might not be appropriate in the workplace.
The default URL Filtering profile blocks the malware, phishing, and
command-and-control URL categories, but not the rest of the categories
recommended categories to block. The default URL Filtering profile also
blocks the abused-drugs, adult, gambling, questionable, and weapons URL
categories. Whether to block these URL categories depends on your business
requirements. For example, a university probably won’t restrict student
access to most of these sites because availability is important, but a
business that values security first might block all of them.
URL Filtering Examples
URL Filtering works with file blocking,
decryption, external dynamic lists (EDLs), logging, and other security
capabilities to create granular policies that can go beyond simply blocking or
allowing entire URL categories. Use the URL Filtering safe transition
steps to evaluate what sites you want to allow and what sites you
want to block, then implement policies that fit your business requirements. For
example:
- Use risk-based URL categories (high-risk, medium-risk, and low-risk) in combination with other URL categories to target decryption or to target blocking traffic. For example, you can:
- Block traffic to high-risk websites in the financial-services category.
- Decrypt all high-risk and medium-risk web traffic.
- Decrypt high-risk and medium-risk traffic to specific URL categories if the firewall doesn't have sufficient resources to decrypt all the traffic you want to decrypt.
- Log all user agents and referrers, all URLs, and all file downloads for high-risk and medium-risk category domains to increase visibility.
- Allow access to categories such as personal-sites-and-blogs while applying a File Blocking profile to the traffic to prevent downloading risky content such as .exe, .scr, and other potentially malicious files.
- Use the predefined Palo Alto Networks - Bulletproof IP addresses external dynamic list to prevent access to sites hosted on Bulletproof ISPs, especially if you allow access to high-risk or medium-risk finance sites.
- Use combinations of URL categories to simplify policy.
Best Practice Internet Gateway WildFire Analysis Profile
Use these WildFire Analysis security profile settings as a best practice at your
internet gateway.
Forward files to WildFire for analysis to protect your network from unknown threats.
Without this protection, attackers can infiltrate your network and exploit
vulnerabilities in the applications your employees use everyday. Because WildFire
protects against unknown threats, it's your best defense against advanced persistent
threats (APTs).
Set up WildFire appliance content updates
to download and install automatically in real-time so that you always have the most
recent support.
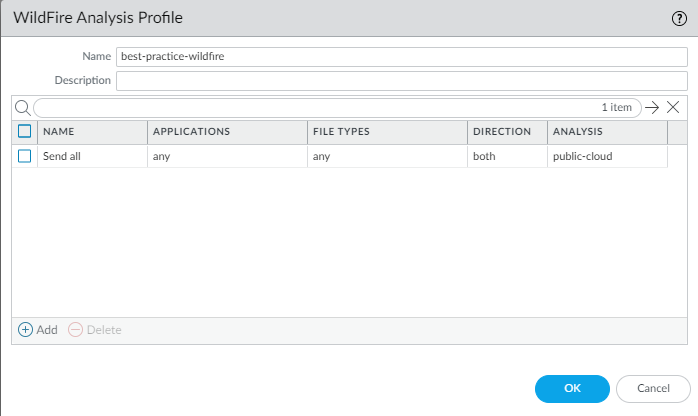
The best practices WildFire Analysis profile sends all files
in both directions (upload and download) to WildFire for analysis. Specifically,
make sure you are sending all PE files (if you’re not blocking them in accord with
file blocking best practices), Adobe Flash and Reader files (PDF, SWF), Microsoft
Office files (PowerPoint, Excel, Word, RTF), Java files (Java, .CLASS), and Android
files (.APK).
Set up alerts for malware through email,
SNMP, or a syslog server so that the firewall immediately notifies you when it
encounters a potential issue. The faster you isolate a compromised host, the lower
the chance the previously unknown malware has spread to other data center devices,
and the easier it is to remediate the issue.
If necessary, you can restrict the applications and file types sent for analysis
based on the traffic’s direction.
WildFire Action settings in the Antivirus profile might impact traffic if the
traffic generates a WildFire signature that results in a reset or a drop action.
You can exclude internal traffic such as software distribution applications
through which you deploy custom-built programs to transition safely to best
practices (otherwise, WildFire might identify custom-built programs as malicious
and generate a signature for them). Check MonitorLogsWildFire Submissions to see if any internal custom-built programs trigger WildFire
signatures.
