Monitor and Fine-Tune the Policy Rulebase
Table of Contents
Expand all | Collapse all
-
- What Is a Best Practice Internet Gateway Security Policy?
- Why Do I Need a Best Practice Internet Gateway Security Policy?
- How Do I Deploy a Best Practice Internet Gateway Security Policy?
- Create User Groups for Access to Allowed Applications
- Decrypt Traffic for Full Visibility and Threat Inspection
-
- Transition Vulnerability Protection Profiles Safely to Best Practices
- Transition Anti-Spyware Profiles Safely to Best Practices
- Transition Antivirus Profiles Safely to Best Practices
- Transition WildFire Profiles Safely to Best Practices
- Transition URL Filtering Profiles Safely to Best Practices
- Transition File Blocking Profiles Safely to Best Practices
- Create Best Practice Security Profiles for the Internet Gateway
- Monitor and Fine-Tune the Policy Rulebase
- Remove the Temporary Rules
- Maintain the Rulebase
Monitor and Fine-Tune the Policy Rulebase
Creating a best practice security policy is an iterative process. After you define the initial
internet gateway Security policy, monitor traffic that matches the
temporary rules that identify policy gaps and alarming behavior, and tune your
policy accordingly. Monitoring traffic that matches these rules enables you to make
appropriate adjustments to the permanent rules and either make sure all traffic
matches your application allow rules or assess whether you should allow applications
that match no rules.
As you tune your rulebase, you should see less and less traffic that you want to
allow matching the temporary rules. When you no longer see traffic that you want to
allow matching these rules, your positive enforcement allow rules are complete and
you can remove the temporary
rules (the interzone-default deny rule automatically denies traffic that
no rule explicitly allows).
Because monthly content releases add new App-IDs, review the impact App-ID changes have on your
Security policy.
- Create custom reports to monitor traffic that matches rules which identify policy gaps.
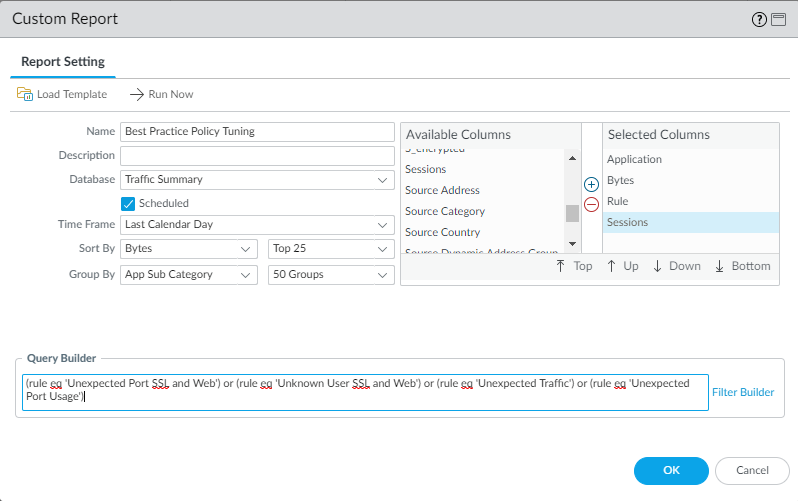
- Select MonitorManage Custom Reports.Add a report and give it a descriptive Name that indicates the policy gap you're investigating.Set the Database to Traffic Summary.Select Scheduled.Add Rule, Application, Bytes, Sessions to the Selected Columns list.Set the desired Time Frame, Sort By, and Group By fields.Define the query to match traffic that matches the rules which find policy gaps and alarming behavior. You can create a single report which details traffic that matches any of the rules (using the or operator) or create individual reports to monitor each rule. The following example queries use the rule names defined in the example policy:
- (rule eq 'Unexpected Port SSL and Web')
- (rule eq 'Unknown User SSL and Web')
- (rule eq 'Unexpected Traffic')
- (rule eq 'Unexpected Port Usage')
![]() Review the report regularly to understand why traffic matches each of the tuning rules. Either update rules to include legitimate applications and users or use the information in the report to assess the application's risk and implement policy reforms.
Review the report regularly to understand why traffic matches each of the tuning rules. Either update rules to include legitimate applications and users or use the information in the report to assess the application's risk and implement policy reforms.