Step 1: Create Rules Based on Trusted Threat Intelligence Sources
Table of Contents
Expand all | Collapse all
-
- What Is a Best Practice Internet Gateway Security Policy?
- Why Do I Need a Best Practice Internet Gateway Security Policy?
- How Do I Deploy a Best Practice Internet Gateway Security Policy?
- Create User Groups for Access to Allowed Applications
- Decrypt Traffic for Full Visibility and Threat Inspection
-
- Transition Vulnerability Protection Profiles Safely to Best Practices
- Transition Anti-Spyware Profiles Safely to Best Practices
- Transition Antivirus Profiles Safely to Best Practices
- Transition WildFire Profiles Safely to Best Practices
- Transition URL Filtering Profiles Safely to Best Practices
- Transition File Blocking Profiles Safely to Best Practices
- Create Best Practice Security Profiles for the Internet Gateway
- Monitor and Fine-Tune the Policy Rulebase
- Remove the Temporary Rules
- Maintain the Rulebase
Step 1: Create Rules Based on Trusted Threat Intelligence Sources
Block traffic from hosts that Palo Alto Networks and trusted third-party sources have proven
malicious. An Advanced Threat Prevention license (or an active legacy Threat
Prevention license) includes built-in external dynamic lists (EDLs)
that contain known malicious IP addresses. Use EDLs in policy to block malicious
traffic. Palo Alto Networks compiles and dynamically updates the lists based on the
latest threat intelligence. Firewalls receive and implement Dynamic Updates without
the need for a reboot.
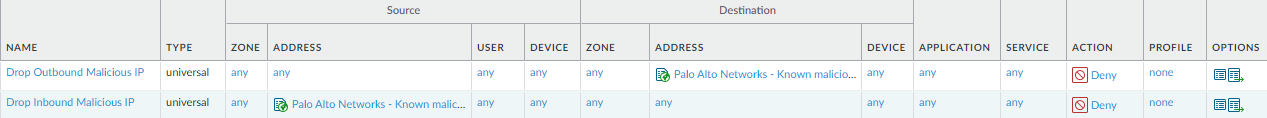
- Block traffic to and from IP addresses that Palo Alto Networks identifies as malicious.
Why Do I Need These Rules? Rule Highlights - This rule protects you against IP addresses that Palo Alto Networks has proven to be used almost exclusively to distribute malware, initiate command-and-control activity, and launch attacks.
- One rule blocks outbound traffic to known malicious IP addresses, while the other rule blocks inbound traffic to those addresses.
- Set the external dynamic list Palo Alto Networks - Known malicious IP addresses as the Destination address for the outbound traffic rule, and as the Source address for the inbound traffic rule.
- Deny traffic that matches these rules.
- Enable logging for traffic matching these rules so you can investigate potential threats on your network.
- Because these rules stop malicious traffic, they protect traffic from any user running on any port.
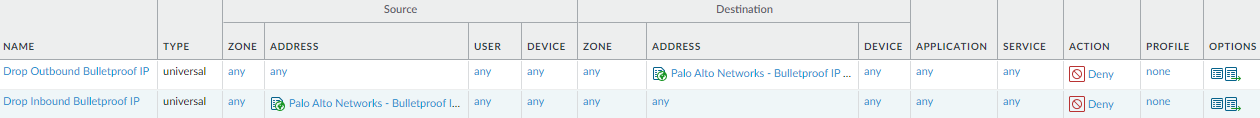
![]() Block traffic to and from Bulletproof hosting providers.
Block traffic to and from Bulletproof hosting providers.Why Do I Need These Rules? Rule Highlights - This rule protects you against IP addresses that Palo Alto Networks has shown to belong to Bulletproof hosting providers.Bulletproof hosting providers have no or limited restrictions on content and don’t log events. Bulletproof sites are ideal places from which to launch command-and-control (C2) attacks and illegal activity because anything goes and nothing is tracked.
- One rule blocks outbound traffic to known Bulletproof hosting IP addresses, while another rule blocks inbound traffic to those addresses.
- Set the external dynamic list Palo Alto Networks - Bulletproof IP addresses as the Destination address for the outbound traffic rule, and as the Source address for the inbound traffic rule.
- Deny traffic that matches these rules.
- Enable logging for traffic matching these rules so that you can investigate potential threats on your network.
- Because these rules stop malicious traffic, they protect traffic from any user running on any port.
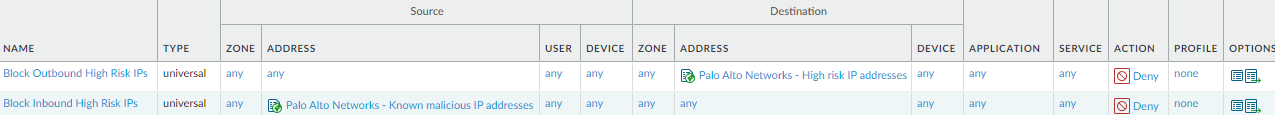
![]() Block and log traffic to and from high-risk IP addresses from trusted threat advisories.
Block and log traffic to and from high-risk IP addresses from trusted threat advisories.Why Do I Need These Rules? Rule Highlights Although Palo Alto Networks has no direct evidence of the maliciousness of the IP addresses in the high-risk IP address feed, threat advisories have linked them to malicious behavior.- Block and log the traffic as shown in this example.
- If you must allow a high-risk IP address for business reasons, create a Security policy rule with strict Security profiles that allows only that IP address and place it in front of the high-risk IP address block rule in the rulebase. Closely monitor and log any high-risk IP addresses that you choose to allow.
- One rule logs blocked outbound traffic to high-risk IP addresses and another rule logs blocked inbound traffic to those addresses.
- Set the external dynamic list Palo Alto Networks - High risk IP addresses as the Destination address for the outbound traffic rule and as the Source address for the inbound traffic rule.
- If you allow the traffic, apply best practices Security profiles.
- Because these rules stop malicious traffic, they protect traffic from any user running on any port, for any application.
![]() Similarly, create two rules that block and log traffic to and from Tor exit nodes, which are often (but not always) associated with malicious activity, especially in enterprise environments, using the Palo Alto Networks - Tor exit IP addresses external dynamic list.
Similarly, create two rules that block and log traffic to and from Tor exit nodes, which are often (but not always) associated with malicious activity, especially in enterprise environments, using the Palo Alto Networks - Tor exit IP addresses external dynamic list.