Step 3: Create the Application Block Rules
Table of Contents
Expand all | Collapse all
-
- What Is a Best Practice Internet Gateway Security Policy?
- Why Do I Need a Best Practice Internet Gateway Security Policy?
- How Do I Deploy a Best Practice Internet Gateway Security Policy?
- Create User Groups for Access to Allowed Applications
- Decrypt Traffic for Full Visibility and Threat Inspection
-
- Transition Vulnerability Protection Profiles Safely to Best Practices
- Transition Anti-Spyware Profiles Safely to Best Practices
- Transition Antivirus Profiles Safely to Best Practices
- Transition WildFire Profiles Safely to Best Practices
- Transition URL Filtering Profiles Safely to Best Practices
- Transition File Blocking Profiles Safely to Best Practices
- Create Best Practice Security Profiles for the Internet Gateway
- Monitor and Fine-Tune the Policy Rulebase
- Remove the Temporary Rules
- Maintain the Rulebase
Step 3: Create the Application Block Rules
Application block rules protect you from evasive and commonly exploited applications
while you develop and tune your Security policy rulebase. Temporary tuning
rules help find gaps in policy and identify possible attacks. Because
they catch application traffic you didn't know was running on your network, they
allow traffic that could pose security risks. The following block rules explicitly
block potentially malicious applications and protocols that attackers commonly use,
such as public DNS and SMTP, encrypted tunnels, remote access, and non-sanctioned
file-sharing applications.
- Block Quick UDP Internet Connections (QUIC) protocol.
Why Do I Need This Rule? Rule Highlights - Chrome and some other browsers establish sessions using QUIC instead of TLS. QUIC uses proprietary encryption that the firewall can’t decrypt, so potentially dangerous encrypted traffic might enter the network.
- Blocking QUIC forces the browser to fall back to TLS and enables the firewall to decrypt the traffic.
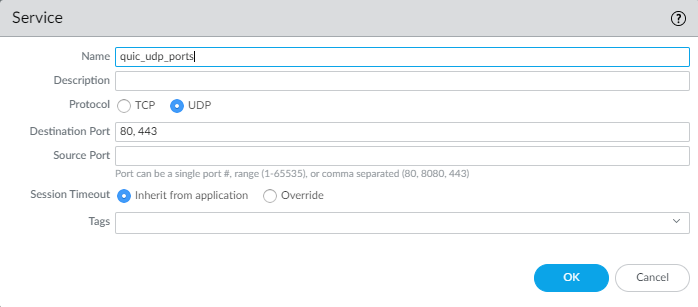
- Create a Service (ObjectsServices) that specifies UDP ports 80 and 443.
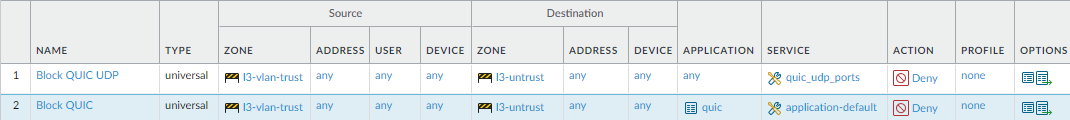
- The first rule blocks QUIC on its UDP service ports (80 and 443) and uses the Service you created to specify those ports.
- The second rule blocks the QUIC application.
The Service specifies the UDP ports to block for QUIC.![]() The first rule specifies the Service you configured for QUIC and the second rule blocks the QUIC application:
The first rule specifies the Service you configured for QUIC and the second rule blocks the QUIC application:![]() Block applications that don't have a legitimate use case.
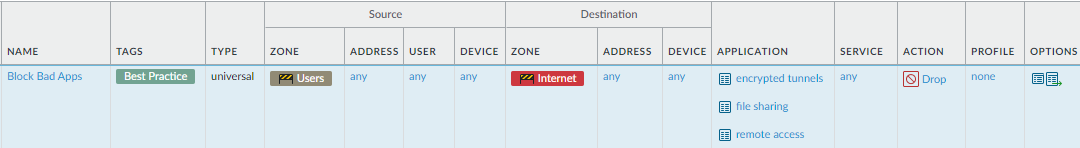
Block applications that don't have a legitimate use case.Why Do I Need This Rule? Rule Highlights - Block potentially malicious applications such as encrypted tunnels, peer-to-peer file sharing, and web-based file sharing applications that IT hasn't sanctioned.
- Because the temporary tuning rules might allow traffic with malicious intent as well as legitimate traffic that doesn't match your policy rules as expected, they could allow risky or malicious traffic. This rule blocks traffic that has no legitimate use case and that an attacker or a negligent user could use.
- Use the Drop Action to silently drop the traffic without sending a signal to the client or the server.
- Enable logging for traffic matching this rule so that you can investigate potential threats and misuse of applications on your network.
- Because this rule is intended to catch malicious traffic, it matches traffic from any user running on any port.
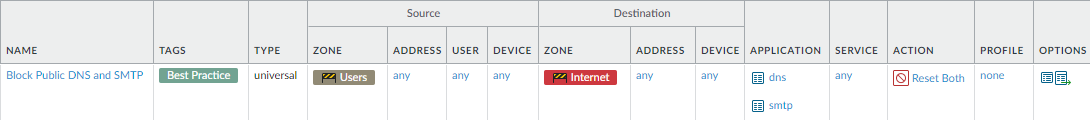
![]() Block public DNS and SMTP applications.Allow traffic only to sanctioned DNS servers. Use the DNS Security service to prevent connections to malicious DNS servers.
Block public DNS and SMTP applications.Allow traffic only to sanctioned DNS servers. Use the DNS Security service to prevent connections to malicious DNS servers.Why Do I Need This Rule? Rule Highlights - Block public DNS/SMTP applications to avoid DNS tunneling, command-and-control traffic, and remote administration applications.
- Use the Reset both client and server Action to send a TCP reset message to both the client-side and server-side devices.
- Enable logging for traffic that matches this rule so that you can investigate potential threats.
![]()