Download PDF
Cloud NGFW for AWS
Configure Zone-based Policy Rules
Table of Contents
Expand All
|
Collapse All
Cloud NGFW for AWS Docs
Configure Zone-based Policy Rules
Reduce the attack surface by using Cloud NGFW to segment the network into functional
and organizational zones.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Segmenting the network into functional and organizational zones reduces its
attack surface—the portion exposed to potential attackers. Security zones protect
your network by segmenting it into smaller, more easily managed areas and
controlling traffic access to them.
In self-managed Palo Alto Networks firewalls (such as VM-Series), a
security zone comprises one or more physical or virtual firewall interfaces and the
network segments connected to the zone’s interfaces. You first define zones and then
associate the physical and virtual interfaces to those zones. Finally, you use these
zones in the security policy rules that you author.
However, Cloud NGFW automatically sets up the networking constructs for you. You no
longer need to worry about configuring interfaces and associating them with the
zones you create. You can author zone-based policy rules in Panorama and enforce
them on Cloud NGFW.
Cloud NGFW Zones
Cloud NGFW allows you to classify your VPC traffic using Private and Public
zones to simplify policy enforcement.
- The Private zone includes your hybrid cloud network defined by private traffic range prefixes. This network encompasses your VPCs on AWS and your on-premises network (connected via Direct Connect or VPN).
- The Public zone comprises all prefixes outside your hybrid cloud network (the public internet).
Control this classification by appropriately specifying the private traffic range
prefixes for the endpoint on which the traffic enters the Cloud NGFW resource.
Source and Destination Zones
Cloud NGFW automatically assigns the Source Zone as Private
if the traffic session has a source IP address within the private traffic range prefixes defined
for the endpoint on which the traffic enters the Cloud NGFW resource. Otherwise,
Cloud NGFW assigns the source zone as Public.
Similarly, Cloud NGFW automatically assigns the Destination Zone as
Private if the traffic session has a destination IP address within the
private traffic range prefixes defined for the endpoint on which the traffic enters
the Cloud NGFW resource. Otherwise, Cloud NGFW assigns the destination zone as
Public.
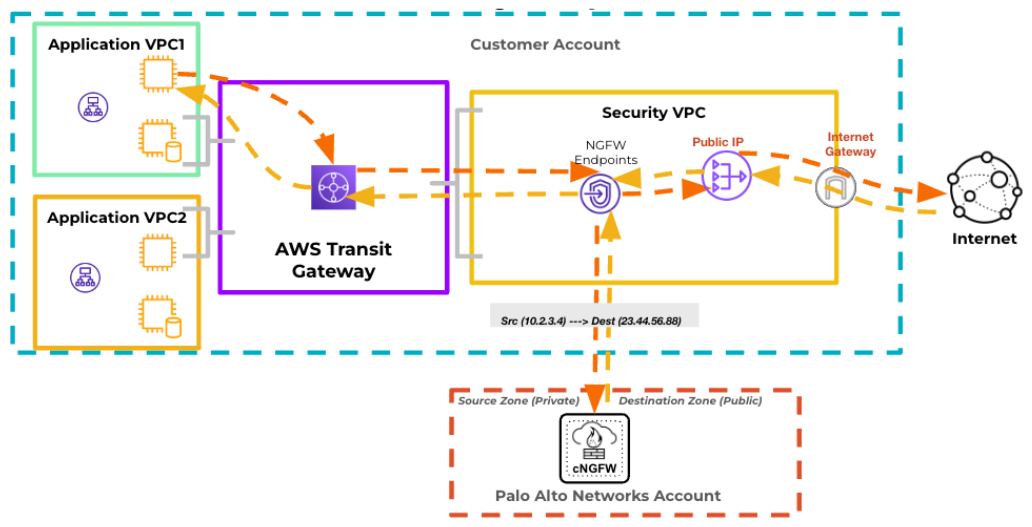
For example, Cloud NGFW assigns the source(Ingress) zone as Private and the
destination zone as Public for a session with a source IP address as 10.2.3.4 and
destination IP address as 23.44.55.66.
The illustration below shows the source and destination zones on traffic via an
endpoint with Egress NAT disabled:
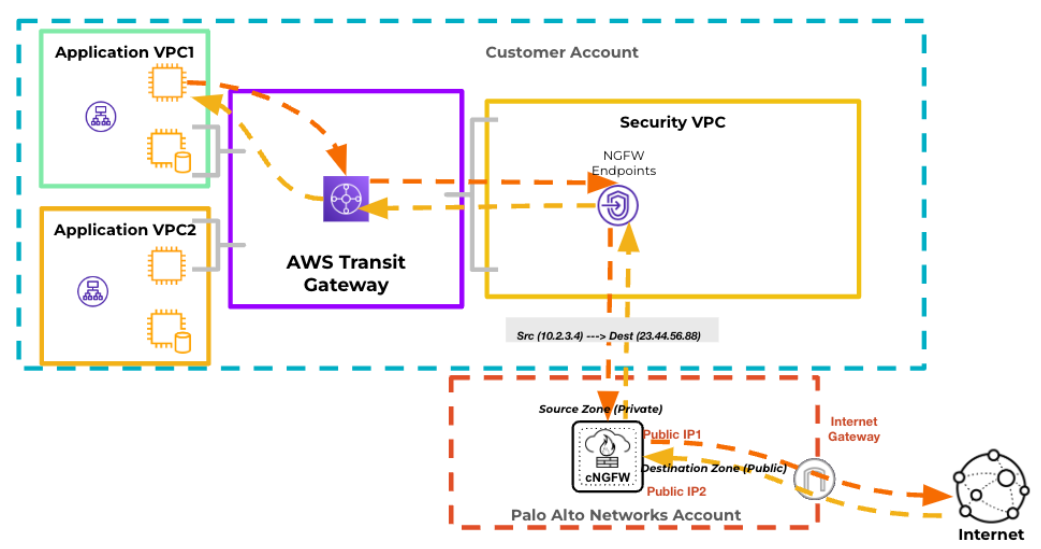
The illustration below shows the source and destination zones on traffic via an
endpoint with Egress NAT enabled:
![]()
Zone Protection
Effective defense against DoS attacks requires a layered approach. The
first layer of defense should be a dedicated, high-volume DDoS protection service
such as AWS Shield to defend against volumetric attacks that the session-based
firewalls are not designed to handle. However, Cloud NGFW uses the Zone Protection
profile to add more granular layers of DoS attack defense and provide visibility
into application traffic that dedicated DDoS services don't provide.
After traffic passes through the dedicated DDoS service (such as AWS
Shield) and enters your VPC, Cloud NGFW applies the Zone Protection profile if one
is attached to the Ingress (source) zone. Cloud NGFW determines the Ingress (source)
zone from the Source IP address of the packet. Zone Protection profiles provide a
broad defense against DoS attacks based on the aggregate traffic entering the zone.
If the Zone Protection profile denies the packet, Cloud NGFW discards the packet and
skips the Security policy lookup. Cloud NGFW applies Zone Protection profiles only
to new sessions (packets that don't match an existing session). Once the session is
established, the Cloud NGFW packet processing engine bypasses the Zone Protection
profile lookup for succeeding packets in that session.
You can attach a Zone Protection profile to the private and public zones using the
Panorama Cloud device group template. A Zone Protection profile protects the Ingress
(or source) zone against the most common flood, reconnaissance, and packet-based
attacks.
- Flood protection. A Zone Protection profile with flood protection configured defends an entire ingress zone against SYN, ICMP, ICMPv6, UDP, and other IP flood attacks.
- Reconnaissance Protection. Similar to the military definition of reconnaissance, the network security definition of reconnaissance is when attackers attempt to gain information about your network’s vulnerabilities by secretly probing the network to find weaknesses. Reconnaissance activities are often preludes to a network attack. Enable Reconnaissance Protection on both Private and Public zones to defend against port scans and host sweep.
- Packet-based Attack Protection. Packet-based attacks take many forms. Zone Protection profiles check IP, TCP, ICMP, IPv6, and ICMPv6 packet headers and protect a zone by dropping packets with undesirable characteristics or stripping undesirable options from packets before admitting them to the zone.
Cloud NGFW Zone Mapping
Zones are associated with interfaces on self-managed firewalls such as
VM-Series. However, within Cloud NGFW, the networking infrastructure is
automatically set up for you. This means that you no longer need to worry about
configuring interfaces and associating them with the zones you create (and, in
Panorama Cloud NGFW template stacks and templates, the web interface to configure
interfaces is removed from Panorama—any unnecessary Panorama web interface elements
are removed in Panorama Managed Cloud Device Groups).
However, to enable consistent Security policy enforcement, you must create zone
mappings in your cloud device groups so that Cloud NGFW will know whether to
associate the security zones you have in your Panorama with Cloud NGFWs Private
(internal) or Public (external) zone. These mappings enable Cloud NGFW to enforce
your Security policy rules properly.
In some cases zone
mapping may fail if you are not running the latest version of the AWS plugin
(version 5.3.0). Palo Alto Networks recommends that you do not enable zone-based
policies for existing firewalls that have not been upgraded to the new Egress
NAT AMI using AWS plugin version 5.3.0 or above.
Configure Zone Mapping in Panorama Cloud Device Groups
The following minimum system requirements are needed for zone-based policy
rules:
- AWS plugin version 5.3.0 or above
- PAN-OS version 10.2.8 or above
- Cloud Connector plugin version 2.0.1 or above
To configure zone mapping using the Panorama console:
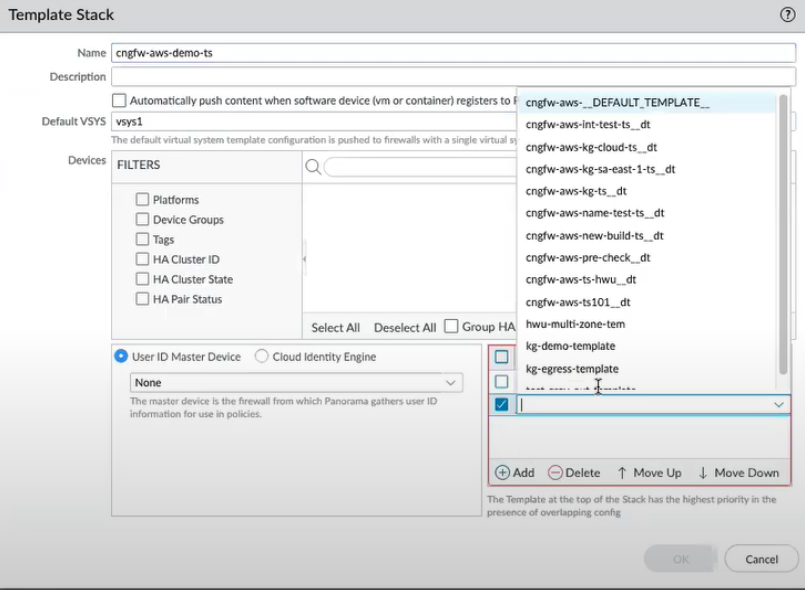
- Add a cloud device group using the Panorama console.Panorama > Templates, and select your Template StackThe AWS plugin associates the template stack with your cloud device group. The AWS plugin creates a default template and adds the Public and Private zones to this template by default.In the Templates section, you can see the default template created by the AWS plugin that will have the same name as your template stack with a suffix __dt appended to its name.
![]() You can also reference your other Panorama templates to the template stack list, click Add, and then select the template.
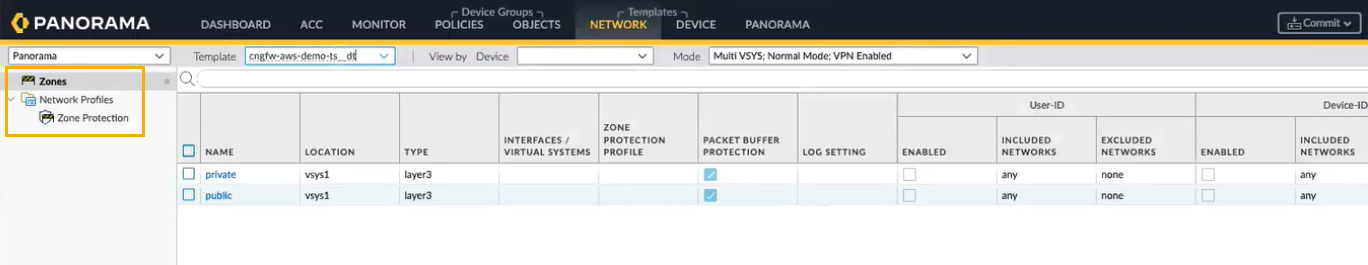
You can also reference your other Panorama templates to the template stack list, click Add, and then select the template.![]() Create a Zone Protection profile and associate it to your default Private and Public zones of your default template. To create the Zone Protection profile:
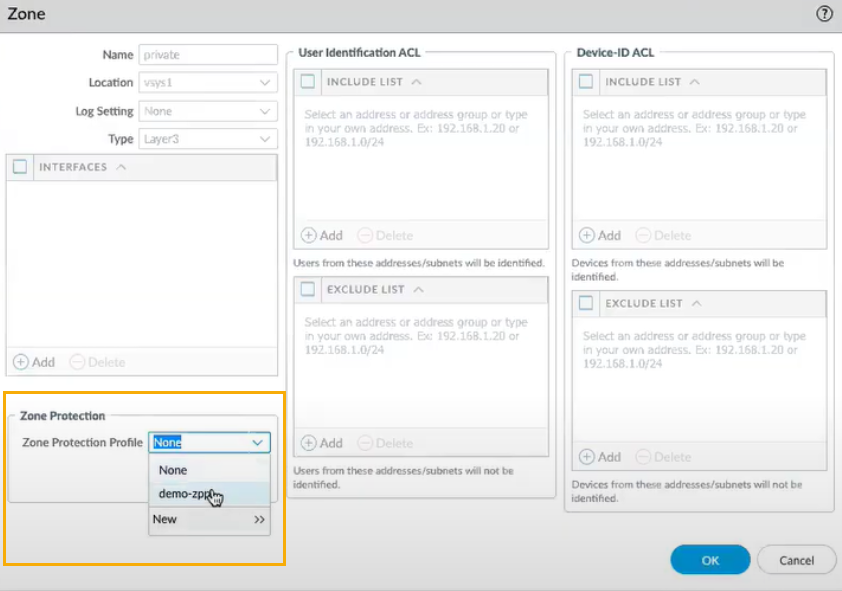
Create a Zone Protection profile and associate it to your default Private and Public zones of your default template. To create the Zone Protection profile:- In the Panorama console, go to Network > Zone Protection.Click Add.Enter a Name and Description to your Zone Protection profile.Select the Zone Protection services.Click OK.After creating the Zone Protection profiles, perform the following steps to associate your Private and Public zones of your default template:In the Panorama console, select the Networks tab.Select your Template.Go to Zones.
![]() Click Private and select the Zone Protection Profile for your Private Zone.
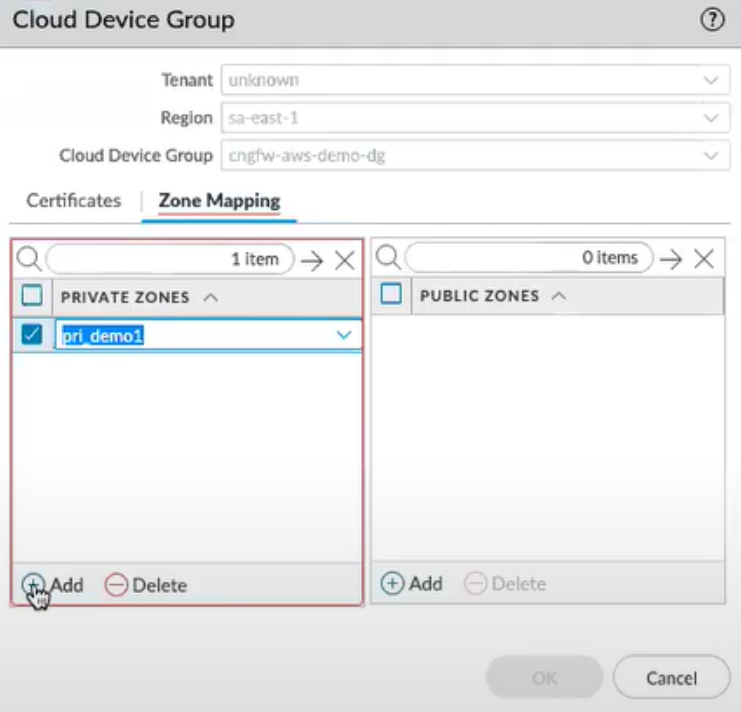
Click Private and select the Zone Protection Profile for your Private Zone.![]() Click Public and select the Zone Protection Profile for your Public zone.Navigate back to your cloud device group. Go to the Zone Mapping tab.You can see the list of Panorama templates that you have referenced to the template stack list. You can map the Panorama zones to the default Private and Public zones that are created by the AWS plugin.
Click Public and select the Zone Protection Profile for your Public zone.Navigate back to your cloud device group. Go to the Zone Mapping tab.You can see the list of Panorama templates that you have referenced to the template stack list. You can map the Panorama zones to the default Private and Public zones that are created by the AWS plugin.![]() Configure security policy rules for cloud device groups in Panorama. You can then use the above mapped Panorama security zones, default Private or Public zones in your security policies as source or destination zones. For more information, see the Apply Policy section.Private-to-Public, Public-to-Private, Private-to-Private, any-to-any, Private-to-Any are the allowed zone-based policy rules in the Panorama Cloud device groups. Any other combination of Source and destination security zones isn't supported in your security rules.Commit and Push your changes on Panorama.Log in to your Cloud NGFW console to verify your XML file containing Private and Public zone mapping pushed from Panorama to the respective cloud device group.Go to Rulestacks, select your cloud device group, and click View XML to display information on newly added Private and Public zones from Panorama to the cloud device group.Using the steps given in the above procedure, you can also configure zone-based policy rules for your existing cloud device groups adding the existing templates from the template stack, and then configure security policy rules for those cloud device groups in Panorama.
Configure security policy rules for cloud device groups in Panorama. You can then use the above mapped Panorama security zones, default Private or Public zones in your security policies as source or destination zones. For more information, see the Apply Policy section.Private-to-Public, Public-to-Private, Private-to-Private, any-to-any, Private-to-Any are the allowed zone-based policy rules in the Panorama Cloud device groups. Any other combination of Source and destination security zones isn't supported in your security rules.Commit and Push your changes on Panorama.Log in to your Cloud NGFW console to verify your XML file containing Private and Public zone mapping pushed from Panorama to the respective cloud device group.Go to Rulestacks, select your cloud device group, and click View XML to display information on newly added Private and Public zones from Panorama to the cloud device group.Using the steps given in the above procedure, you can also configure zone-based policy rules for your existing cloud device groups adding the existing templates from the template stack, and then configure security policy rules for those cloud device groups in Panorama.