CN-Series
Prepare Panorama for CN-Series HSF Deployment
Table of Contents
Expand All
|
Collapse All
CN-Series Firewall Docs
-
- CN-Series System Requirements for the Kubernetes Cluster
- CN-Series System Requirements for On-Premises Kubernetes Deployments
- CN-Series Performance and Scaling
- Create Service Accounts for Cluster Authentication
- Get the Images and Files for the CN-Series Deployment
- Strata Logging Service with CN-Series Firewall
- IOT Security Support for CN-Series Firewall
- Software Cut-through Based Offload on CN-Series Firewall
-
HSF
- Deployment Modes
- HSF
- In-Cloud and On-Prem
-
- CN-Series HSF System Requirements
- Configure Traffic Flow Towards CN-Series HSF
- Test Case: Layer 3 BFD Based CN-GW Failure Handling
- View CN-Series HSF Summary and Monitoring
- Validating the CN-Series HSF Deployment
- Custom Metric Based HPA Using KEDA in EKS Environments
- Configure Dynamic Routing in CN-Series HSF
- Features Not Supported on the CN-Series
Prepare Panorama for CN-Series HSF Deployment
Install the Kubernetes plugin 4.0 on Panorama OS 11.0 and set it up to monitor your
Kubernetes clusters.
The CN-Series HSF configuration and deployment are done through Panorama. Before
deploying the CN-Series HSF, make sure that you have completed the following
prerequisites.
- Deploy a Panorama with software version 11.0 and install the minimum content version.
- Go to PanoramaDynamic Updates for the minimum content release version on PAN-OS 11.0.See PAN-OS Release Notes.
- Go to PanoramaSoftware for the software version.Locate and download the model-specific file for the release version to which you are upgrading. For example, to upgrade an M-Series appliance to Panorama 11.0.0, download the Panorama_m-11.0.0 image; to upgrade a Panorama virtual appliance to Panorama 11.0.0, download the Panorama_pc-11.0.0 image.After a successful download, the Action column changes from Download to Install for the downloaded image.
- Verify that your Panorama is in Panorama mode if you want Panorama to collect the firewall logs.
- Install the Kubernetes plugin 4.0 version on Panorama. If your Panorama appliances are deployed as an HA pair, you must install the Kubernetes plugin on the primary (active) peer first.
- Log in to the Panorama Web Interface and select PanoramaPlugins and click Check Now to get the list of available plugins.
- Select Download and Install the Kubernetes plugin 4.0 version.After you successfully install the plugin, Panorama refreshes and the Kubernetes plugin appears on the Panorama tab.If Panorama is deployed in an HA pair, install the Kubernetes plugin on the secondary (passive) Panorama using the steps described in Step 3.
- Click Commit to Panorama.The commit creates a K8S-CNF-Clustering-Readonly template for use with the CN-Series HSF. It can take up to one minute for the interfaces to display on Panorama. This Template has the network configuration of the preconfigured Cluster Interconnect (CI) link for CN-GW, CN-DB, and CNNGFW pods and Traffic Interconnect (TI) link for CN-GW and CN-NGFW pods. The K8S-CNF-Clustering-Readonly creates 30 logical routers and two interfaces per logical router. The ethernet x/1 are cluster interconnect (CI) links whereas ethernet x/2 are cluster interconnect (TI) links.Make sure that you do not rename the K8S-CNG-Clustering-Readonly template.
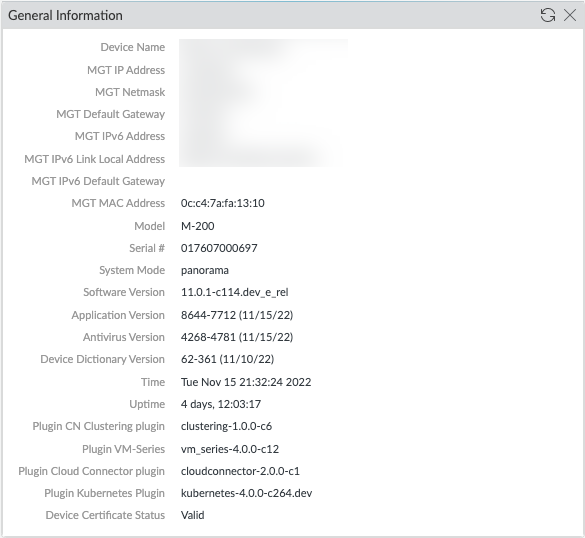
You can verify the General Information widget on the Panorama Dashboard General Information.
- Get the CN-Series HSF license credits on Panorama.
- Select PanoramaPluginsKubernetesSetupLicenses.
- Select Activate/update using authorization code, and enter the auth code and the total number of dataplane vCPUs needed. You must Create a Deployment Profile to obtain your CN-Series authcode.
 When the CN-Series is deployed with HSF, if the number of pods (CN-NGFW, CN-GW, and CN-DB) deployed exceeds the number of allocated vCPUs, you have a four-hour grace period to add more vCPUs to your deployment profile or delete enough pods. If you do not allocate additional vCPUs or delete unlicensed pods within the four-hour grace period, the unlicensed pods will restart and create traffic disruption. The already licensed pods remain licensed.
When the CN-Series is deployed with HSF, if the number of pods (CN-NGFW, CN-GW, and CN-DB) deployed exceeds the number of allocated vCPUs, you have a four-hour grace period to add more vCPUs to your deployment profile or delete enough pods. If you do not allocate additional vCPUs or delete unlicensed pods within the four-hour grace period, the unlicensed pods will restart and create traffic disruption. The already licensed pods remain licensed. - Verify that the number of available license credits is updated.
- Create a parent Device Group.You must create a device group with necessary policies and objects required for CN-Series HSF. You have to reference this device group when you deploy the CN-Series HSF.
- Go to PanoramaDevice Groups and click Add.
- Enter a unique Name and a Description to identify the device group.
- Select the Parent Device Group (default is Shared) that will be just above the device group you are creating in the device group hierarchy.
- Click OK.The device group name is bootstrapped to the CN-MGMT pod in the cluster. When CN-MGMT pods connect to Panorama with these bootstrap parameters, the device group gets associated with the cluster name in the cluster configuration. For Panorama High Availability (HA), the CN-MGMT pod sends updates to both active and passive Panoramas. Cluster information is automatically populated for the CN-NGFW, CN-DB, and CN-GW pods when they are active.
- Select CommitCommit and Push to commit and push the device group configuration to Panorama.
- Create variable Template to enable traffic flow.
- Go to PanoramaTemplates and click Add.
- Enter a unique Name for the template.
- Add an optional Description.
- Configure the variable template to enable traffic flow.You can configure this template before or after deploying the CN-Series HSF.
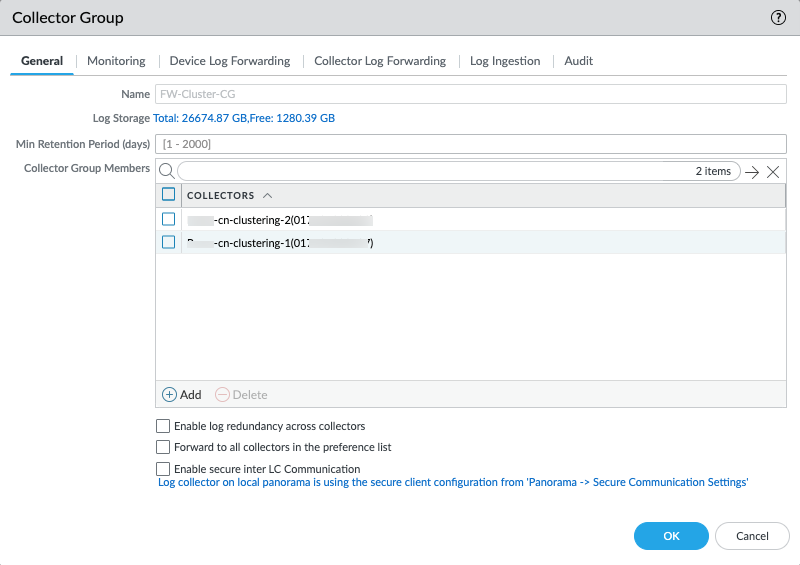
- Create a Log Collector and add it to a Log Collector Group.
- Go to PanoramaCollector Groups and Add a Collector Group.
- Enter a Name for the Collector Group.
- Enter the Minimum Retention Period in days (1 to 2,000) for which the Collector Group will retain firewall logs.By default, the field is blank, which means the Collector Group retains logs indefinitely.
- Add Log Collectors (1 to 16) to the Collector Group Members list.

- Select CommitCommit and Push, to commit and push your changes to Panorama and the Collector Group you configured.
The Panorama authkey will be created and managed by the Kubernetes plugin.