CN-Series
Upgrade the CN-Series Firewall—Rolling Update
Table of Contents
Expand All
|
Collapse All
CN-Series Firewall Docs
-
-
-
- Deployment Modes
- In-Cloud and On-Prem
-
-
-
Upgrade the CN-Series Firewall—Rolling Update
Deploy an additional CN-MGMT statefulset to complete
a rolling update of the CN-NGFW pods.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Use one of the following options to perform
a rolling update, upgrade or downgrade to a supported PAN-OS version.
- Rolling Update where you upgrade the CN-MGMT StatefulSet and then upgrade the CN-NGFW pods.
- When you use this option, review the Compare the Old and New PAN-CN-MGMT.yaml and make sure that you update the relevant section of the yaml file.
Before
you begin, ensure the CN-Series YAML file version is compatible
with the PAN-OS version.
- PAN-OS 10.1.2 or later requires YAML 2.0.2
- PAN-OS 10.1.0 and 10.1.1 require YAML 2.0.0 or 2.0.1
Rolling Update
This process enables you to first upgrade
the CN-MGMT StatefulSet and then upgrade the CN-NGFW pods. The disruption
to application traffic is minimal because the CN-NGFW pods are functioning
during the CN-MGMT StatefulSet upgrade, and the rolling update for
the CN-NGFW pods occurs one instance of the CN-NGFW pod at a time.
If
you have a large Kubernetes cluster with a significant number of
CN-NGFW pods and want a faster upgrade, you can schedule a maintenance
window to delete the CN-NGFW yaml and upgrade all CN-NGFW pods at
once.
During the CN-MGMT upgrade, logging is impacted. Additionally,
both kubectl logs and System log messages are generated for temporary
version mismatch and connection restarts between the CN-NGFW and
the CN-MGMT pods.
- Upgrade the CN-MGMT StatefulSet.
- Use one of the following options.
- Option 1— Update the image name in the pan-cn-mgmt.yaml and apply the changes.containers: - name: pan-mgmt image:<your-private-registry-image-path-new-image>kubectl apply -f pan-cn-mgmt.yamlOption 2—Use kubectl. When using kubectl, you are not updating the yaml files and therefore must keep track of the image used for the upgrade.kubectl -n kube-system set image sts/pan-mgmt-sts pan-mgmt=<your-private-registry-image-path-new-image>
- Verify that the CN-MGMT StatefulSet is deployed.
- Use kubectl -n kube-system get sts/pan-mgmt-sts -o wide
- Check the status of the upgrade.kubectl exec -it pan-mgmt-sts-0 -n kube-system -- su adminadmin@pan-mgmt-sts-0> show jobs alladmin@pan-mgmt-sts-0.Basc-cluster-180> show jobs all Enqueued Dequeued ID PositionInQ Type Status Result Completed ------------------------------------------------------------------------------------------------------------------------------------------ 2020/08/25 14:11:11 14:11:11 2 AutoCom FIN OK 14:11:44
- Upgrade the CN-NGFW pods.
- Use one of the following options.
- Option1— Update the image name in the pan-cn-ngfw.yaml and apply the changes.containers: - name: pan-ngfw-container image:<your-private-registry-image-path-new-image>kubectl apply -f pan-cn-ngfw.yamlOption 2—Use kubectl. When using kubectl, you are not updating the yaml files and therefore must keep track of the image used for the upgrade.
- In CN-Series as a DaemonSet deployment, use:kubectl -n kube-system set image ds/pan-ngfw-ds pan-ngfw-container=<your-private-registry-image-path-new-image>In CN-Series as a Kubernetes Service deployment, use:kubectl -n kube-system set image deployment/pan-ngfw-dep pan-ngfw-container=<your-private-registry-image-path-new-image>
- Check the status of the upgrade.Use kubectl -n kube-system get ds/pan-ngfw-ds -o wideIn a CN-Series as a Kubernetes Service deployment, use kubectl -n kube-system get deployment/pan-ngfw-dep -o wide
- Required only if the images are updated for the PAN-OS
version Update the init container and pan-cni images.
- Modify the Init container image in the pan-cn-mgmt.yaml
for the CN-MGMT firewall.initContainers: - name: pan-mgmt-init image:<your-private-registry-image-path>
- Edit the image path for the PAN-CNI container image in the pan-cni.yaml.
containers: name: install-pan-cni image:<your-private-registry-image-path>Rolling Update with Additional CN-MGMT StatefulSet
- Before you begin.
- Verify that the nodes in your cluster have the memory and CPU resources required for the additional CN-MGMT StatefulSet.
- (Required for statically provisioned PVs only)
Verify that you have PVs available for the additional CN-MGMT StatefulSet.The pan-cn-pv-local.yaml creates the directories required to deploy the CN-MGMT.
- Set up the new pan-cn-mgmt-configmap.yaml.Edit the PAN_SERVICE_NAME: value to match what you added above in the new pan-cn-mgmt.yaml.apiVersion: v1kind: ConfigMapmetadata:name: pan-ngfw-confignamespace: kube-systemdata:PAN_SERVICE_NAME: pan-mgmt-svc2Retain the same values for the # Panorama settings and # Intended License Bundle type in the new file to reduce any updates on Panorama.
- Set up the new pan-cn-mgmt.yaml file.There are multiple places you need to replace the service names, apps, and labels. See Compare the Old and New PAN-CN-MGMT.yaml.
- Required only if the images are updated for the PAN-OS
version Update the Init container and pan-cni imagesImage path for the Init container image in the pan-cn-mgmt.yaml for the CN-MGMT firewallinitContainers: - name: pan-mgmt-init image: <your-private-registry-image-path>Image path for the PAN-CNI container image that has the CNI binaries and the CNI network config file on each node.containers: name: install-pan-cni image: <your-private-registry-image-path>
- Apply the new CN-MGMT yaml files.kubectl apply -f pan-cn-mgmt-configmap-new.yamlkubectl apply -f pan-cn-mgmt-new.yaml
- Verify that the new CN-MGMT StatefulSet is deployed.kubectl -n kube-system get sts -o wideNAME READY AGE CONTAINERS IMAGESpan-mgmt-sts 2/2 16h pan-mgmt 018147215560.dkr.ecr.ap-southeast-1.amazonaws.com/test/panos_ctnr/10.0.0/b/mp:63pan-mgmt-sts-new 2/2 50m pan-mgmt-new 018147215560.dkr.ecr.ap-southeast-1.amazonaws.com/test/panos_ctnr/10.0.1/b/mp:64
- Edit the CN-NGFW pod yaml files with the new service
name.
- Update the pan-cn-ngfw-configmap.yaml.When you modify the PAN_SERVICE_NAME: value referenced in the pan-cn-ngfw-configmap.yaml to match the value you defined in the pan-cn-mgmt.yaml Service name, the pods that use the new image will connect to the new StatefulSet.apiVersion: v1kind: ConfigMapmetadata:name: pan-ngfw-confignamespace: kube-systemdata:PAN_SERVICE_NAME: pan-mgmt-svc2
- Deploy the pan-cn-ngfw-configmap.yamlkubectl apply -f pan-cn-ngfw-configmap.yaml
- Edit the image path referenced in the pan-cn-ngfw.yaml.For example, you can use kubectl set image ds/pan-cn-ngfw-ds -n kube-system pan-ngfw-container=018147215560.dkr.ecr.ap-southeast-1.amazonaws.com/test/panos_ctnr/10.0.2/b/dp:62
- Check the status of the rolling update.UP-TO-DATE column displays the number of replicas that have been updated successfully.kubectl get ds/pan-ngfw-ds -n kube-system -o wideNAME DESIRED CURRENT READY UP-TO-DATE AVAILABLE NODE SELECTOR AGE CONTAINERS IMAGES SELECTORpan-ngfw 4 4 3 1 3 <none> 16h pan-ngfw-container 018147215560.dkr.ecr.ap-southeast-1.amazonaws.com/test/panos_ctnr/10.0.0/b/dp:22 app=pan-ngfw
- Update the pan-cn-ngfw-configmap.yaml.
- Verify that the CN-NGFW pods are deployed.kubectl -n kube-system get pods -l app=pan-ngfwNAME READY STATUS RESTARTS AGEpan-ngfw-ds-8b5gp 1/1 Running 0 40mpan-ngfw-ds-h8xc6 1/1 Running 0 40mpan-ngfw-ds-sn62b 1/1 Running 0 40mpan-ngfw-ds-vxfqp 1/1 Running 0 40m
- Get the Serial Number for the CN-MGMT pods.kubectl exec -it pan-mgmt-sts-0 -n kube-system -- su adminWarning: Your device is still configured with the default admin account credentials. Please change your password prior to deployment.admin@pan-mgmt-sts-0>
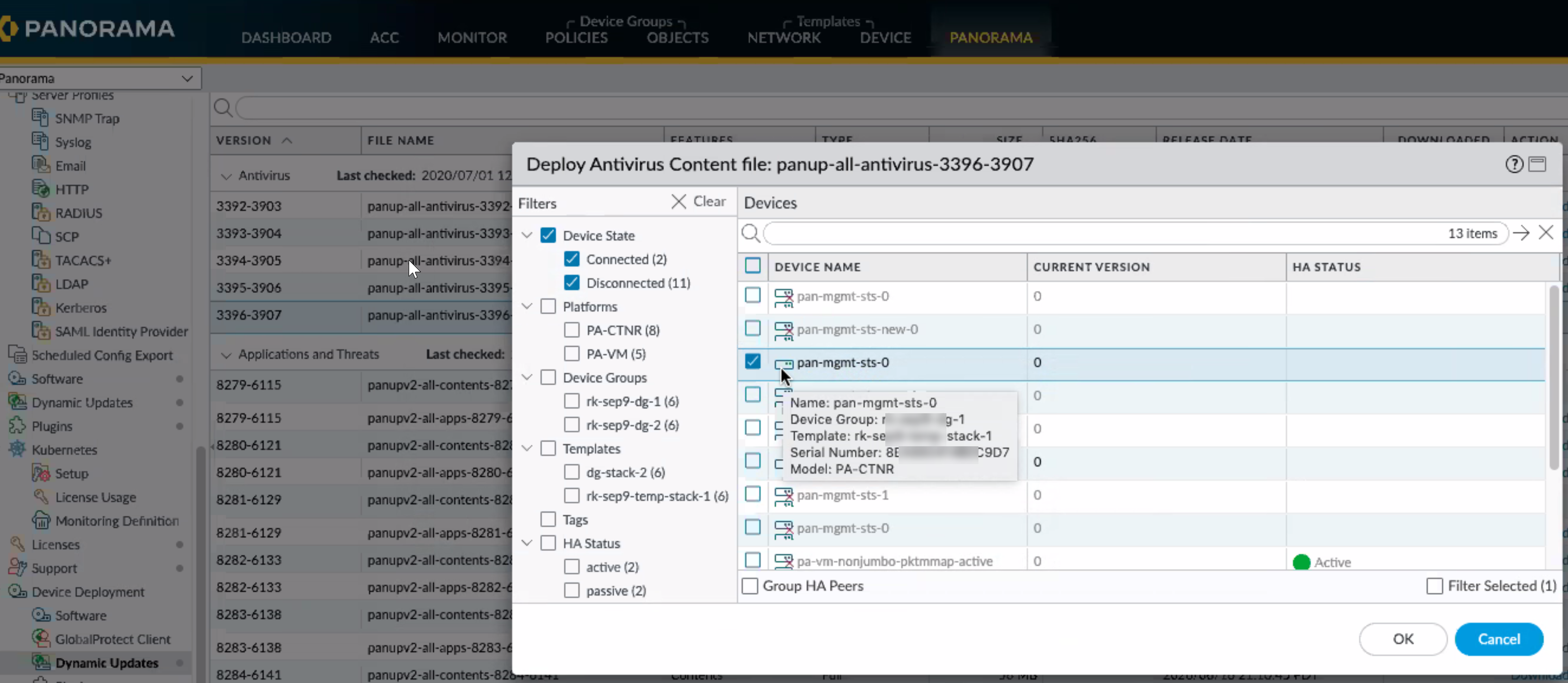
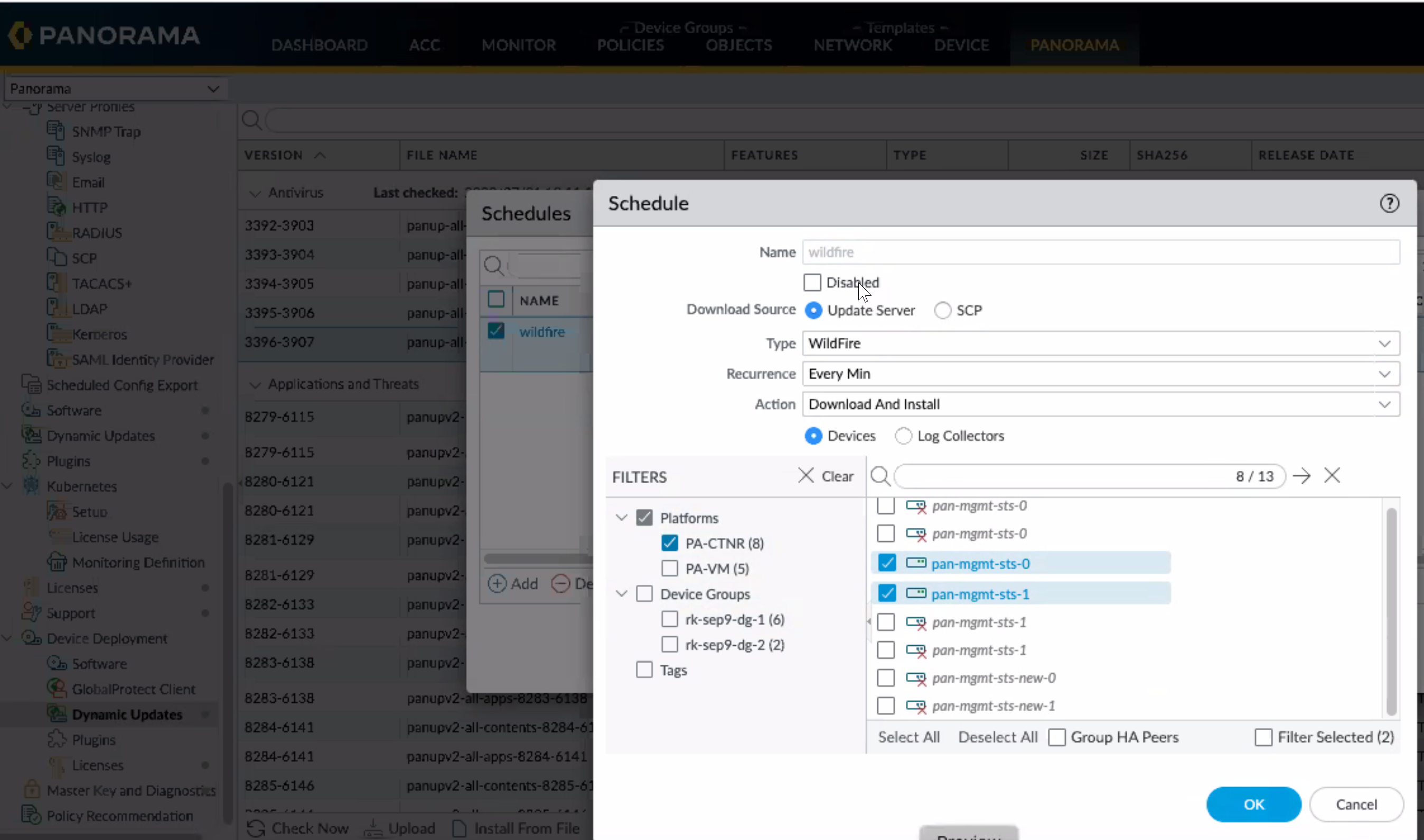
- Install the dynamic content updates for the subscriptions
you have purchased.You can either install it manually or set up a schedule. Verify the serial numbers of the CN-MGMT pods when selecting them for the dynamic updates.or on a recurring schedule.
![]()
![]()
Compare the Old and New PAN-CN-MGMT.yaml
Review the different places where you need to update the service names, apps, and labels within the yaml file when you deploy a new CN-MGMT StatefulSet. Old New apiVersion: v1kind: Servicemetadata:name: pan-mgmt-svcapiVersion: v1kind: Servicemetadata:name: pan-mgmt-svc2namespace: kube-systemlabels:app: pan-mgmt-svcnamespace: kube-systemlabels:app: pan-mgmt-svc2spec:ports:- protocol: UDPport: 4500name: ipsecselector:appname: pan-mgmt-stsspec:ports:- protocol: UDPport: 4500name: ipsecselector:appname: pan-mgmt-sts-newapiVersion: apps/v1kind: StatefulSetmetadata:name: pan-mgmt-stsapiVersion: apps/v1kind: StatefulSetmetadata:name: pan-mgmt-sts-newnamespace: kube-systemspec:selector:matchLabels:appname: pan-mgmt-stsserviceName: pan-mgmt-svc# Replicas are for fault-tolerance. Max 2 replicas supported.replicas: 2updateStrategy:type: RollingUpdatepodManagementPolicy: Paralleltemplate:metadata:labels:app: pan-mgmtappname: pan-mgmt-stsnamespace: kube-systemspec:selector:matchLabels:appname: pan-mgmt-sts-newserviceName: pan-mgmt-svc2# Replicas are for fault-tolerance. Max 2 replicas supported.replicas: 2updateStrategy:type: RollingUpdatepodManagementPolicy: Paralleltemplate:metadata:labels:app: pan-mgmtappname: pan-mgmt-sts-newlabelSelector:matchExpressions:- key: "appname"operator: Invalues:pan-mgmt-stslabelSelector:matchExpressions:- key: "appname"operator: Invalues:pan-mgmt-sts-newtopologyKey: "kubernetes.io/hostname"initContainers:- name: pan-mgmt-initmountPath: /var/log/pan/envFrom:configMapRef:name: pan-mgmt-configtopologyKey: "kubernetes.io/hostname"initContainers:- name: pan-mgmt-initmountPath: /var/log/pan/envFrom:configMapRef:name: pan-mgmt-new-config# sw-secret in pan-cn-ngfw.yaml and hard-coded in ipsec.confvalue: pan-fwcontainers:name: pan-mgmtimage: 018147215560.dkr.ecr.ap-southeast-1.amazonaws.com/test/panos_ctnr/10.0.0/b/mp:63# sw-secret in pan-cn-ngfw.yaml and hard-coded in ipsec.confvalue: pan-fwcontainers:name: pan-mgmt-newimage: 018147215560.dkr.ecr.ap-southeast-1.amazonaws.com/test/panos_ctnr/10.0.1/b/mp:64volumesname: dshmenvFrom:configMapRef:name: pan-mgmt-configvolumesname: dshmenvFrom:configMapRef:name: pan-mgmt-new-config - Edit the image path for the PAN-CNI container image in the pan-cni.yaml.
- Modify the Init container image in the pan-cn-mgmt.yaml
for the CN-MGMT firewall.
- Use one of the following options.