Advanced Threat Prevention Powered by Precision AI®
Configure Inline Cloud Analysis (Strata Cloud Manager)
Table of Contents
Configure Inline Cloud Analysis (Strata Cloud Manager)
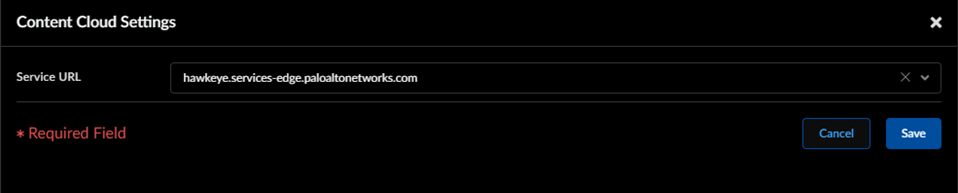
- To take advantage of inline cloud analysis, you must have an active Prisma Access subscription, which provides access to Advanced Threat Prevention features. For information about the applications and services offered with Prisma Access, refer to All Available Apps and Services.To verify subscriptions for which you have currently active licenses, Check What’s Supported With Your License. For more information about license activation and related processes, refer to: Get Started with Common Services: License Activation, Subscription, Tenant Management, & Product Management.If you are accessing Advanced Threat Prevention through a FedRAMP Moderate or High license, refer to NGFW FedRAMP Moderate and High Support for information about licensing and activation.Use the credentials associated with your Palo Alto Networks support account and log in to the Strata Cloud Manager on the hub.To take advanced of inline cloud analysis, you must have a persistent, active cloud connection used by Prisma Access to handle inline cloud analysis service requests. When the Advanced Threat Prevention license is enabled, Prisma Access performs PAN-DB URL categorization lookups as part of its internal processing, independent of any URL Filtering license or explicit cloud inline configuration. This is facilitated by the Cloud Content FQDN. The default FQDN connects to hawkeye.services-edge.paloaltonetworks.com and then resolves to the closest cloud services server. You can override the automatic server selection by specifying a regional cloud content server that best meets your data residency and performance requirements.The Cloud Content FQDN is a globally used resource and affects how other services that rely on this connection sends traffic payloads.Verify that the firewall uses the correct Content Cloud FQDN (ManageConfigurationNGFW and Prisma AccessDeviceDevice SetupContent-IDContent Cloud Settings) for your region and change the FQDN as necessary:
![]()
- US Central (Iowa, US)—us.hawkeye.services-edge.paloaltonetworks.com
- Europe (Frankfurt, Germany)—eu.hawkeye.services-edge.paloaltonetworks.com
- APAC (Singapore)—apac.hawkeye.services-edge.paloaltonetworks.com
- India (Mumbai)—in.hawkeye.services-edge.paloaltonetworks.com
- UK (London, England)—uk.hawkeye.services-edge.paloaltonetworks.com
- France (Paris, France)—fr.hawkeye.services-edge.paloaltonetworks.com
- Japan (Tokyo, Japan)—jp.hawkeye.services-edge.paloaltonetworks.com
- Australia (Sydney, Australia)—au.hawkeye.services-edge.paloaltonetworks.com
- Canada (Montréal, Canada)—ca.hawkeye.services-edge.paloaltonetworks.com
- Switzerland (Zürich, Switzerland)—ch.hawkeye.services-edge.paloaltonetworks.com
- Israel (Tel Aviv, Israel)—il.hawkeye.services-edge.paloaltonetworks.com
- FedRAMP Moderate—Refer to the product entry PanOS Cloud Component
- FedRAMP High—Refer to the product entry PanOS CC (Cloud Component)FedRAMP (Moderate and High) currently does not support the following Advanced Threat Prevention features:
- Exfiltration Shield
- UTCP & UUDP Models
- CVE Mapping
- PCAP retrieval for malicious detections
Update or create a new Anti-Spyware security profile to enable inline cloud analysis (to analyze traffic for advanced C2 [command-and-control] and spyware threats in real-time).- Select ConfigurationNGFW and Prisma AccessSecurity ServicesAnti-Spyware.
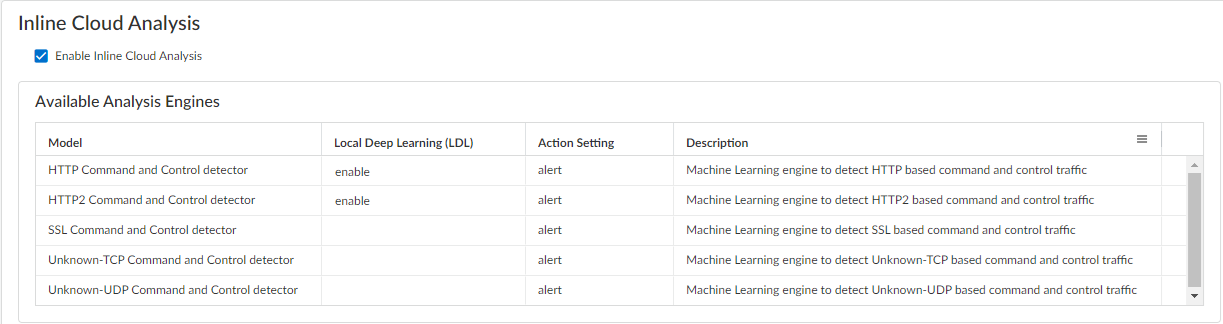
- Select your Anti-Spyware security profile and navigate to the Inline Cloud Analysis panel and Enable Inline Cloud Analysis.
![]()
- Select enable for each available analysis engine with a Local Deep Learning (LDL) option. There are currently two analysis engines available with an optional LDL mode: HTTP Command and Control detector and HTTP2 Command and Control detector.
- Specify an Action to take when a threat is detected using a corresponding analysis engine.The default action for each analysis engine is alert, however, Palo Alto Networks recommends setting all actions to Reset-Both for the best security posture.
- Allow—The request is allowed and no log entry is generated.
- Alert—The request is allowed and a Threat log entry is generated.
- Drop—Drops the request; a reset action is not sent to the host/application.
- Reset-Client—Resets the client-side connection.
- Reset-Server—Resets the server-side connection.
- Reset-Both—Resets the connection on both the client and server ends.
- Click Save to exit the Anti-Spyware security profile configuration dialog and Commit your changes.
(Optional) Add URL and/or IP address exceptions to your Anti-Spyware profile if Inline Cloud Analysis produces false-positives. You can add exceptions by specifying an EDL URL containing a series of URLs or a custom URL category or an IP address list defined in an EDL or within an Address object.- IP address-based EDLs exclude based on the following criteria:
- Destination IP addresses are excluded for traffic flowing from CTS (client-to-server).
- Source IP addresses are excluded for traffic flowing from STC (server-to-client).
- Only create IP address and URL exceptions when the identified threats do not pose a danger, such as in the case of a false-positive.
Add an External Dynamic Lists or [IP] Addresses object exception.- Select ConfigurationNGFW and Prisma AccessSecurity ServicesAnti-Spyware.
- Select an Anti-Spyware profile for which you want to exclude specific URLs or IP addresses and then go to the Inline Cloud Analysis pane.
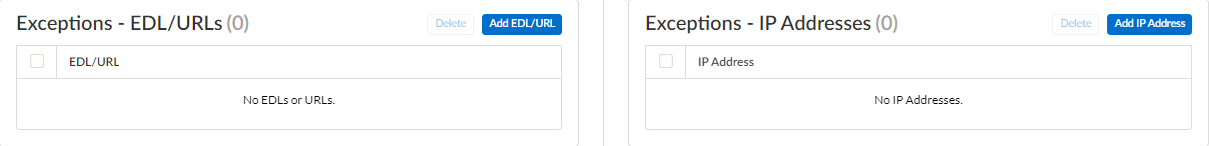
- Add EDL/URL or Add IP Address, depending on the type of exception you want to add, and then select a preexisting URL or IP address external dynamic list. If none is available, create a new external dynamic list policy object. For IP address exceptions, you can, optionally, select an Addresses object list.
![]()
- Click Save to save the Anti-Spyware profile and Commit your changes.
Update or create a new Vulnerability Protection Security profile to enable inline cloud analysis (to analyze traffic for command injection and SQL injection vulnerabilities in real-time).- Select an existing Vulnerability Protection security profile or Add Profile to create a new one (ManageConfigurationVulnerability Protection).
- Select your Vulnerability Protection profile and then go to Inline Cloud Analysis and Enable cloud inline analysis.
- Specify an Action to take when a vulnerability exploit is detected using a corresponding analysis engine. There are currently two analysis engines available: SQL Injection and Command Injection.
- Allow—The request is allowed and no log entry is generated.
- Alert—The request is allowed and a Threat log entry is generated.
- Reset-Client—Resets the client-side connection.
- Reset-Server—Resets the server-side connection.
- Reset-Both—Resets the connection on both the client and server ends.
- Click Save to exit the Vulnerability Protection Profile configuration dialog and Commit your changes.
(Optional) Add URL and/or IP address exceptions to your Vulnerability Protection profile if Inline Cloud Analysis produces false-positives. You can add exceptions by specifying an EDL URL containing a series of URLs or a custom URL category or an IP address list defined in an EDL or within an Address object.- IP address-based EDLs exclude based on the following criteria:
- Destination IP addresses are excluded for traffic flowing from STC (server-to-client).
- Source IP addresses are excluded for traffic flowing from CTS (client-to-server).
- Only create IP address and URL exceptions when the identified threats do not pose a danger, such as in the case of a false-positive.
Add an External Dynamic Lists or [IP] Addresses object exception.- Select ManageConfigurationVulnerability Protection to return to your Vulnerability Protection profile.
- Select a Vulnerability profile for which you want to exclude specific URLs and/or IP addresses and then select Inline Cloud Analysis.
- Add an EDL/URL or IP Address, depending on the type of exception you want to add, and then select a pre-existing URL or IP address external dynamic list. If none are available, create a new external dynamic list. For IP address exceptions, you can optionally, select an Addresses object list.Vulnerability profiles that are configured as Shared on Panorama-managed firewalls cannot have IP address objects added to the Inline Cloud Analysis exceptions list.
- Click Save to save the Vulnerability Protection profile and Commit your changes.
(Optional) Monitor Advanced Threat Prevention