AI Access Security
Discover Risks Posed by GenAI Apps by App Users
Table of Contents
Expand All
|
Collapse All
AI Access Security Docs
Discover Risks Posed by GenAI Apps by App Users
Discover the risks posed by risky users accessing generative AI (GenAI)
apps.
- Log in to Strata Cloud Manager.Select InsightsAI Access to view the AI Access Security Insights dashboard.This displays the top GenAI apps that risky users accessed to help narrow your focus.Click Review use case for the GenAI app Use Case associated with the GenAI app your risky users are accessing.The AI Access Security Insights dashboard displays the GenAI app accessed on your network by use case by default and displays the following high-level information about your top GenAI app users. Click on the user count o view the User Name or IP Address and the number of GenAI Applications that user accessed.
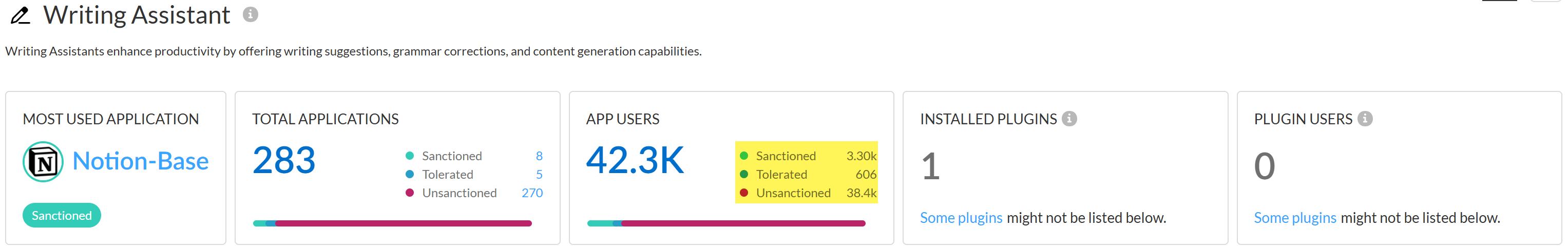
- User BreakdownThis provides a summary of the total number of users accessing any GenAI app associated with the selected GenAI use case. AI Access Security includes a breakdown of how many users accessed Sanctioned, Tolerated, and Unsanctioned apps.Click total App Users count to view a list of all users who accessed or were blocked from accessing a GenAI app associated with the selected use case.
![]()
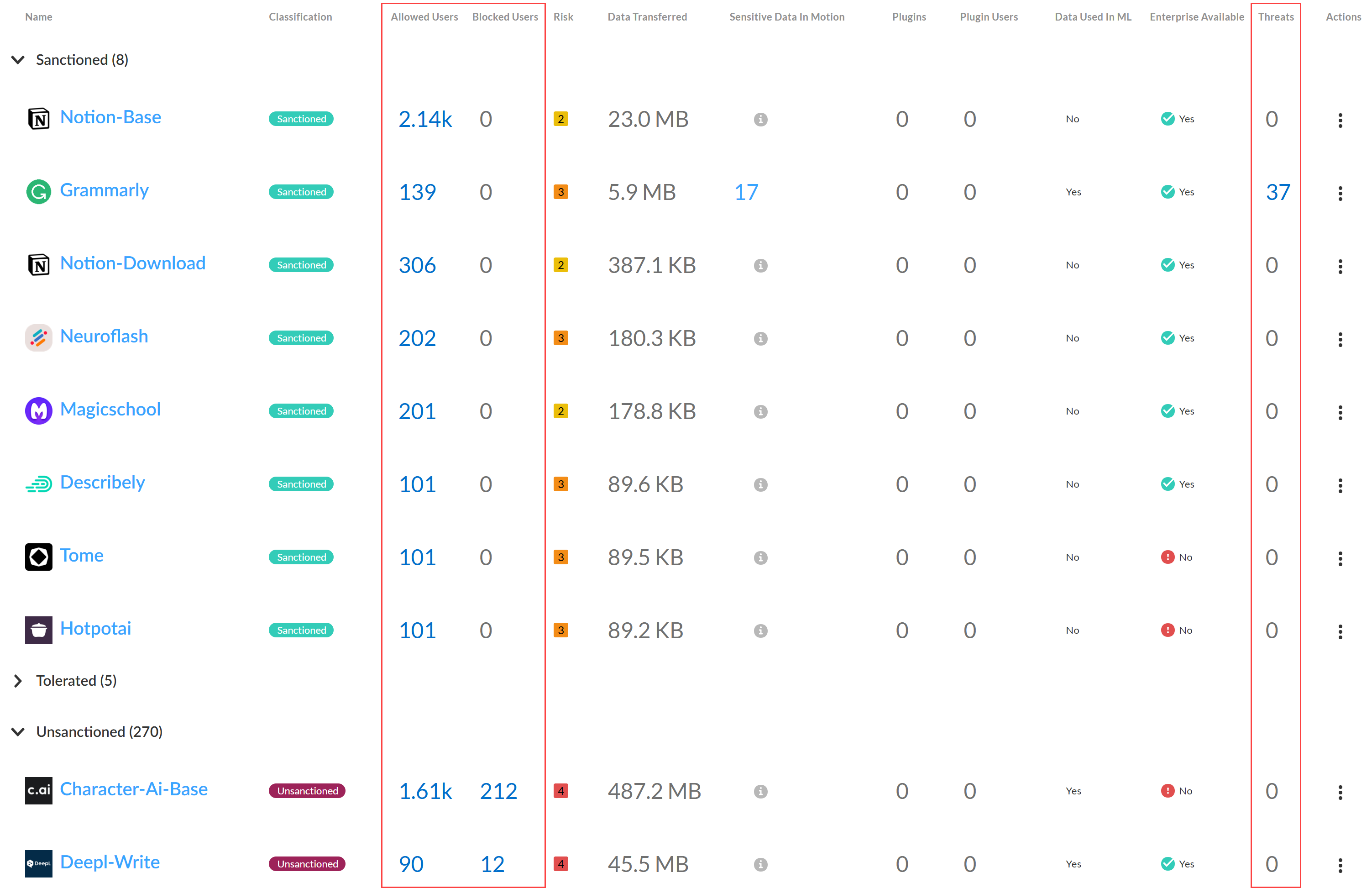
- Users by GenAI Use CaseThis provides a summary of the total number of users accessing each individual GenAI app associated with the selected GenAI use case. The Sanctioned, Tolerated, and Unsanctioned GenAI apps are listed with the total user count for each individual app.Review the Allowed Users and Blocked Users counts to measure the effectiveness of your GenAI app security and access policy rules.
- Allowed Users—Total number of users allowed to access the GenAI app. Use this information to measure the effectiveness of your Security policy rule by verifying that the allowed user count matches your expectations, or to gauge the adoption rate of a GenAI app newly allowed for use by your organization.
- Blocked Users—Total number of used blocked from accessing the GenAI app. Use this information to verify whether you configured Security policy rules controlling access for a specific GenAI app correctly, or to understand if users in your organization are accessing unsanctioned GenAI apps.
For example, consider the Grammarly GenAI app below. Your organization classified this GenAI app as Sanctioned for use by specific users within your organization. In this case, your security administrator clicked the Allowed Users count and verified that all users accessing the GenAI app are allowed to do so.Conversely, your security administrator sees that over 1,600 users accessed the Character-Ai-base app. Your security administrators classified this GenAI app as Unsanctioned and intended to restrict all access with your organization. In this case, your security administrator should review your Security policy rulebase and individual Security policy rules controlling access to the Character-Ai-base app to confirm it was positioned correctly within your Security policy rulebase and to confirm it was configured correctly to block all access.
![]() Create a custom Security policy rule to control access to a GenAI app for specific users.For example, based on your investigation you discover that a large number of users are accessing the bing-ai-uploading GenAI app. While this is a Sanctioned GenAI, it's only sanctioned for a specific set of users within your organization. You can decide to write a policy rule to explicitly block access to users who should not have access to this GenAI app to prevent misuse and a Security policy rule to explicitly allow access to users who are approved to access the GenAI app. Alternatively, you can write a policy rule to allow access for all users but implement data loss and threat prevention measures to prevent exfiltration of sensitive data and prevent threats such as malicious and phishing URLs, malicious files, or malware.
Create a custom Security policy rule to control access to a GenAI app for specific users.For example, based on your investigation you discover that a large number of users are accessing the bing-ai-uploading GenAI app. While this is a Sanctioned GenAI, it's only sanctioned for a specific set of users within your organization. You can decide to write a policy rule to explicitly block access to users who should not have access to this GenAI app to prevent misuse and a Security policy rule to explicitly allow access to users who are approved to access the GenAI app. Alternatively, you can write a policy rule to allow access for all users but implement data loss and threat prevention measures to prevent exfiltration of sensitive data and prevent threats such as malicious and phishing URLs, malicious files, or malware.