Prisma AIRS
Configure Identity and Access Management
Table of Contents
Expand All
|
Collapse All
Prisma AIRS Docs
Configure Identity and Access Management
Configure IAM roles and permissions for Prisma AIRS AI Model Security, including
custom roles creation and API access setup with minimum required permissions for SDK
usage.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
If you have an active deployment profile but lack IAM
permissions for AI Model Security, it may result in user authentication error. Hence
it is important to have an active deployment profile and IAM permission to access AI
Model Security.
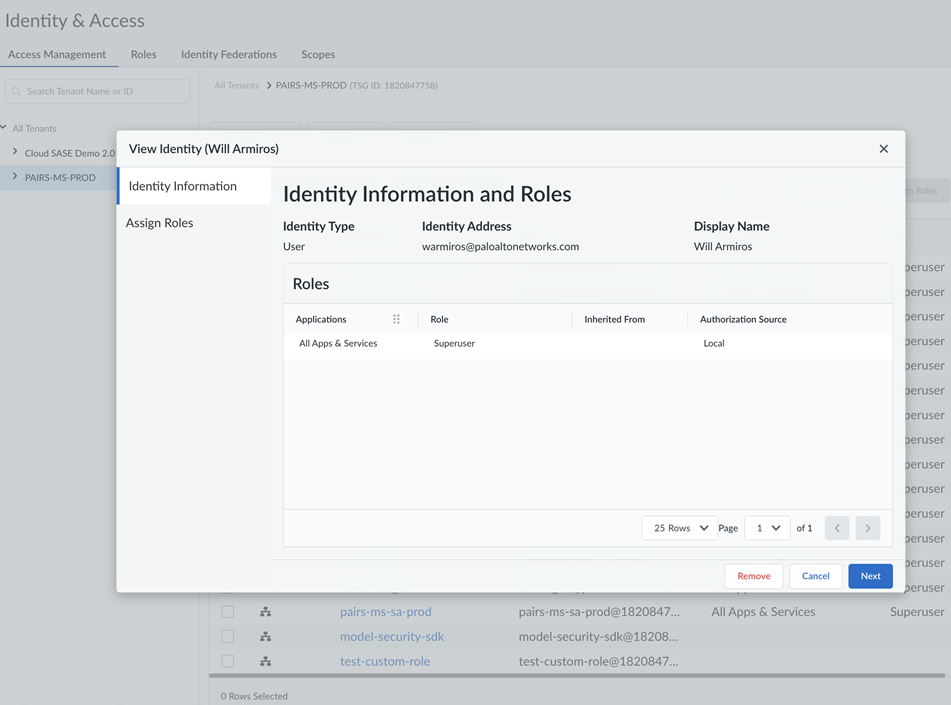
- Navigate to Strata Cloud Manager Identity and Access Management (IAM) settings, Common ServicesIdentity & Access.Navigate to Identity & AccessAccess Management and select the tenant from the tenants list. Verify the Identity Information for the selected tenant to ensure that the Role assigned is either Superuser for all apps and services, or a custom role with access to AI Model Security.
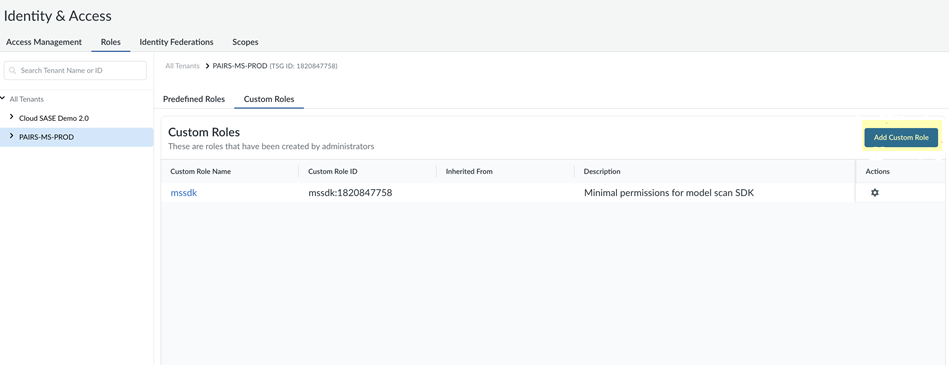
![]() (Optional) (Administrator Only) Create a custom role.
(Optional) (Administrator Only) Create a custom role.- To create a new custom role and assign it to their identity, select Roles and then Custom Roles.
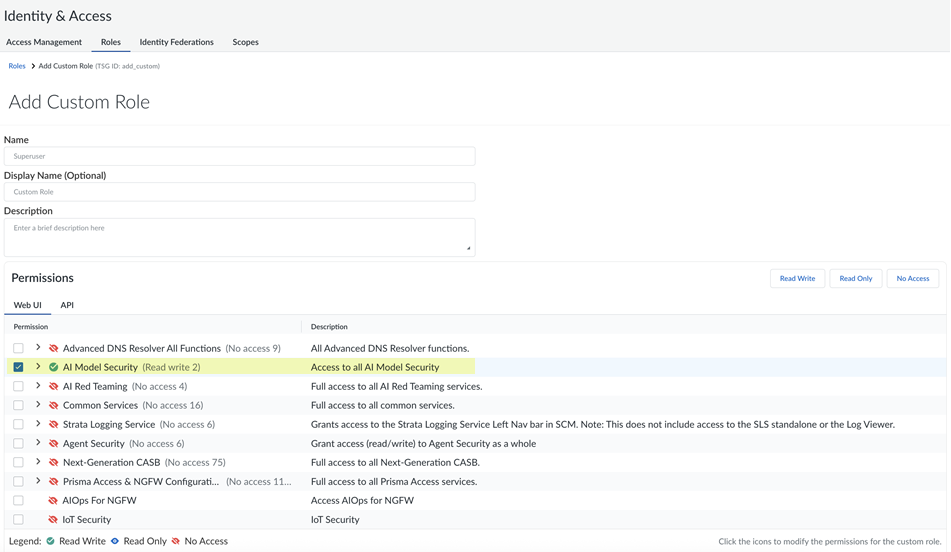
![]() Enable AI Model Security.
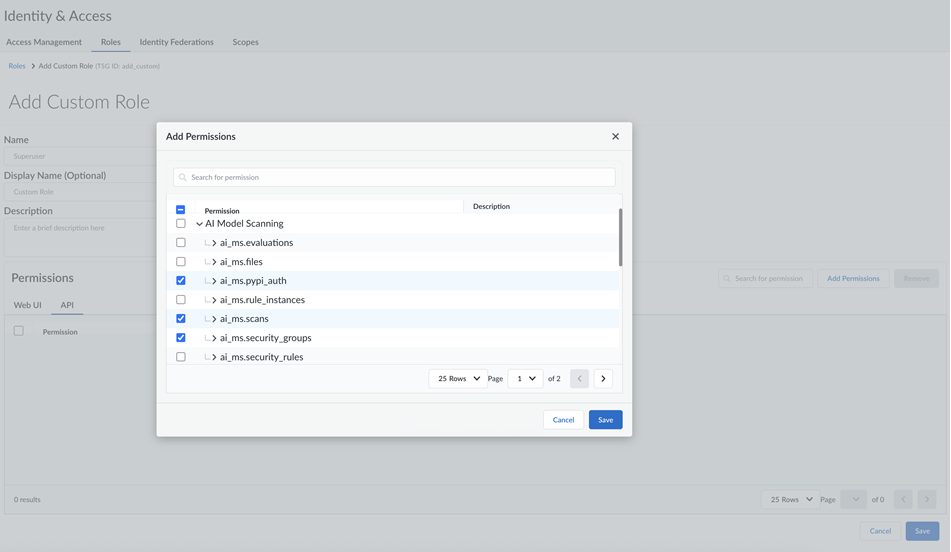
Enable AI Model Security.![]() If you need a service account with API access, select API and Add permissions and assign the minimum permissions.To use SDK, you need at least the following permissions: ai_ms_pypi_auth, ai_ms.scans, and ai_ms.security_groups.
If you need a service account with API access, select API and Add permissions and assign the minimum permissions.To use SDK, you need at least the following permissions: ai_ms_pypi_auth, ai_ms.scans, and ai_ms.security_groups.![]() Enter the Name and Description for the custom role and Save the changes.Create a service account.A service account is used to provide the credentials needed for generating an access token. You also assign roles to service accounts to identify what API actions they can take.Before you create a service account, you must have created at least one tenant service group (TSG). The service account is added as a user to that TSG.You can create the service account using any of the following two methods:
Enter the Name and Description for the custom role and Save the changes.Create a service account.A service account is used to provide the credentials needed for generating an access token. You also assign roles to service accounts to identify what API actions they can take.Before you create a service account, you must have created at least one tenant service group (TSG). The service account is added as a user to that TSG.You can create the service account using any of the following two methods:- By using the Strata Cloud Manager web interface.
- By using the Identity and Access Management APIs. To create a service account using the Identity and Access Management API, you must have already created at least one service account using the User Interface, and then obtained an access token for that account.To create a service account using the Identity and Access Management API, use the create a Service Account API. The Client ID and Client Secret for this account is returned in the response payload:{ "id": "xxxxxxxxxxxxxxxxxxxxx", "name": "xxxxxxxxxx", "tsg_id": "1111111111", "contact_email": "user@example.com", "identity_email": "xxxxxxxxxx@1111111111.iam.panServiceAccounts.com", "description": "Descriptive text", "client_id": "xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx", "client_secret": "xxxxxxxxxxxxxxxxxxxxx" }
- The new service account is created within the TSG that is identified in the access token used on the request to create the service account. If you don't want to use your root TSG for this purpose, create a new TSG before you create your service account.
- No matter which approach you choose for creating a service account, make sure to store the Client Secret immediately, as it cannot be retrieved once the account creation process is complete.
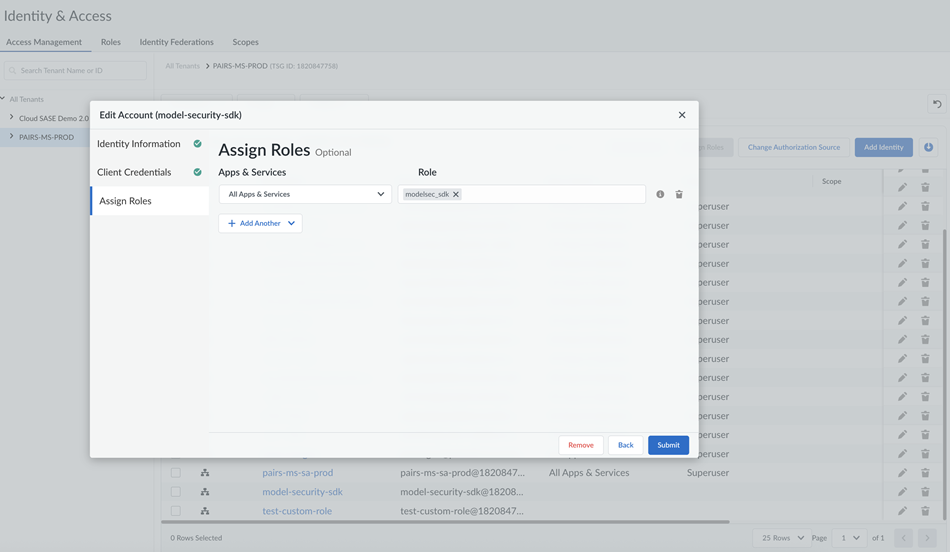
- Select Assign Roles and verify if the custom role that you created appears in the Apps & Services list.
![]()