Create the Data Center Best Practice WildFire Analysis Profile
Table of Contents
10.0 (EoL)
Expand all | Collapse all
-
- What Is a Data Center Best Practice Security Policy?
- Why Do I Need a Data Center Best Practice Security Policy?
- Data Center Best Practice Methodology
- How Do I Deploy a Data Center Best Practice Security Policy?
- How to Assess Your Data Center
-
- Create the Data Center Best Practice Antivirus Profile
- Create the Data Center Best Practice Anti-Spyware Profile
- Create the Data Center Best Practice Vulnerability Protection Profile
- Create the Data Center Best Practice File Blocking Profile
- Create the Data Center Best Practice WildFire Analysis Profile
- Use Cortex XDR Agent to Protect Data Center Endpoints
- Create Data Center Traffic Block Rules
- Order the Data Center Security Policy Rulebase
- Maintain the Data Center Best Practice Rulebase
- Use Palo Alto Networks Assessment and Review Tools
End-of-Life (EoL)
Create the Data Center Best Practice WildFire Analysis Profile
Protect your data center from unknown threats by sending
them to WildFire for analysis.
The other security profiles detect and block known threats. WildFire protects the data center from unknown threats.
Configure the firewall to forward all unknown files to WildFire for analysis using
the predefined default profile. Unknown threats can hide in many
different file types and successful attacks may not be detected until
long after they have done damage. For example, WildFire can identify
malware loaded onto a staging server before the attacker can do
damage and find vulnerability scanners and lateral movement assistance
tools before attackers achieve their goals. WildFire could have
prevented a number of large-scale enterprise breaches over the past
several years. Any security policy rule that controls traffic that
has, will have, or could have file transfer activity should include
an enabled WildFire Analysis profile.
Set up WildFire appliance content updates to
download and install automatically every minute so that you always
have the most recent support. For example, support for Linux files
and SMB files were first delivered in WildFire appliance content
updates.
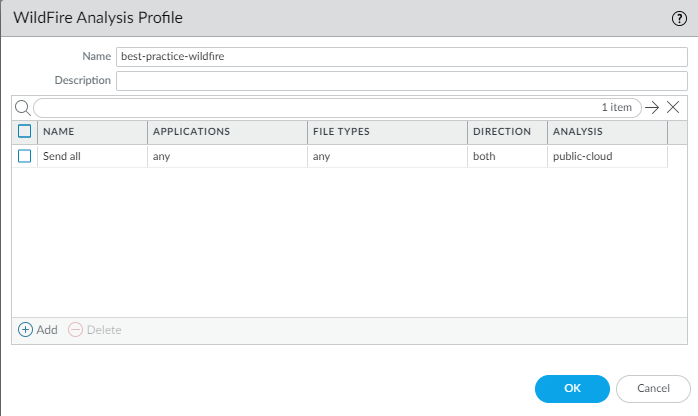
The reason to attach the default WildFire Analysis profile to
all security policy rules that allow traffic is because WildFire provides
the best defense against unknown threats and advanced persistent
threats (APTs). For example:
- Traffic from users to the data center—WildFire identifies unknown malware hosted in the data center such as Confluence or SharePoint.
- Intra data center traffic—WildFire identifies unknown malware spreading among the data center servers, which can prevent the exfiltration of data by discovering the malware before it can do damage.
- Traffic from the data center to the internet—Because this traffic downloads executables for software and operating system updates, it’s critical to run WildFire on all applications to identify malicious behaviors.
Set up alerts for malware through email,
SNMP, or a syslog server so that the firewall immediately notifies you
when it encounters a potential issue. The faster you isolate a compromised
host, the lower the chance that the previously unknown malware has
spread to other data center devices, and the easier it is to remediate
the issue.
If necessary, you can restrict the applications and file types
sent for analysis based on the traffic’s direction.
WildFire Action settings in the Antivirus profile may impact
traffic if the traffic generates a WildFire signature that results
in a reset or a drop action. You can exclude internal traffic such
as software distribution applications through which you deploy custom-built
programs to transition safely to best
practices, because WildFire may identify custom-built programs as
malicious and generate a signature for them. Check MonitorLogsWildFire
Submissions to see if any internal custom-built
programs trigger WildFire signatures.
