Strata Cloud Manager
Insights: Feature Adoption
Table of Contents
Expand All
|
Collapse All
Strata Cloud Manager Docs
Insights: Feature Adoption
Learn how to monitor the security features you’re using.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
→ The features and capabilities available to you in Strata Cloud Manager depend on which license(s) you are
using.
|
- Click InsightsFeature Adoption to get started.
What does this dashboard show you?
- The dashboard shows the aggregated data for all firewalls onboarded to your tenant and are also sending telemetry data.
- For the Feature Adoption Dashboard to function correctly with a firewall managed by Panorama, you need to onboard both Panorama and the firewall. Additionally, you need to enable telemetry for Panorama.
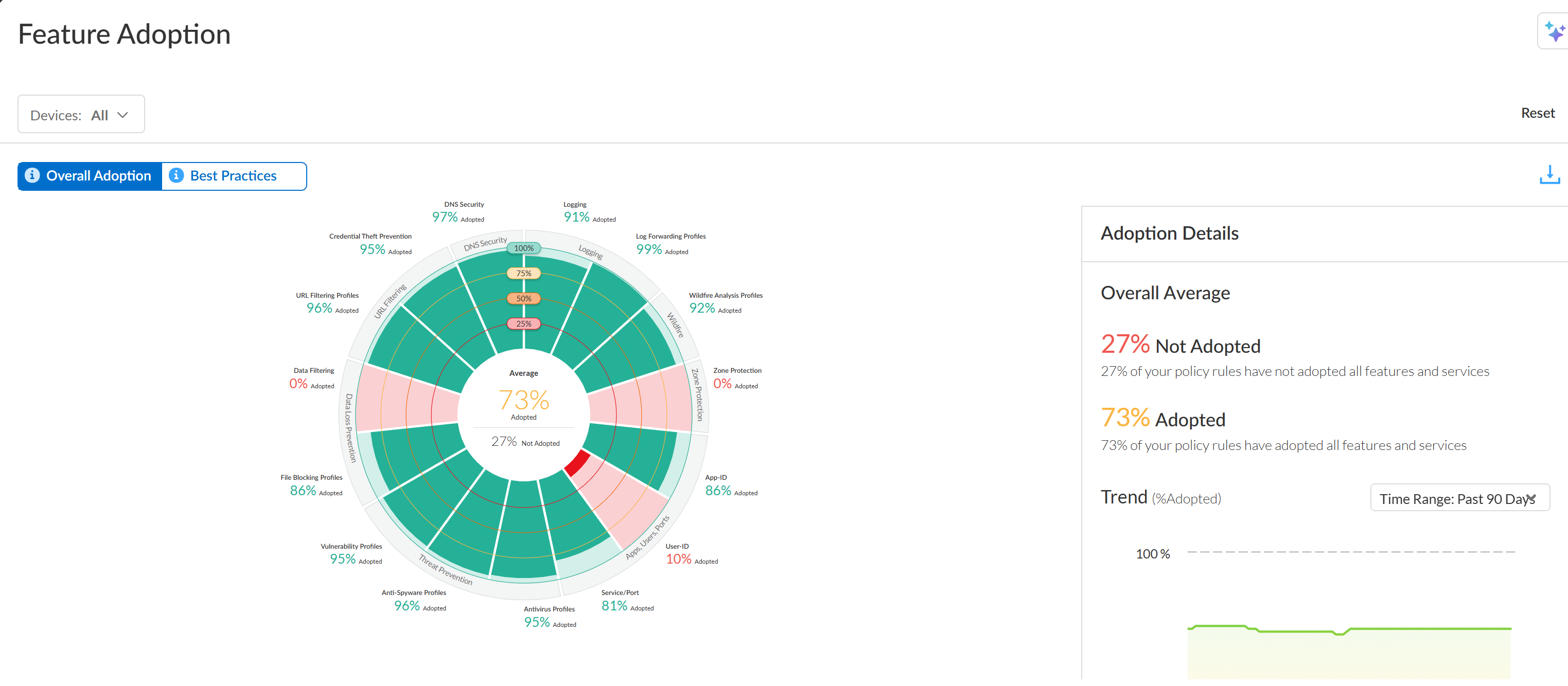
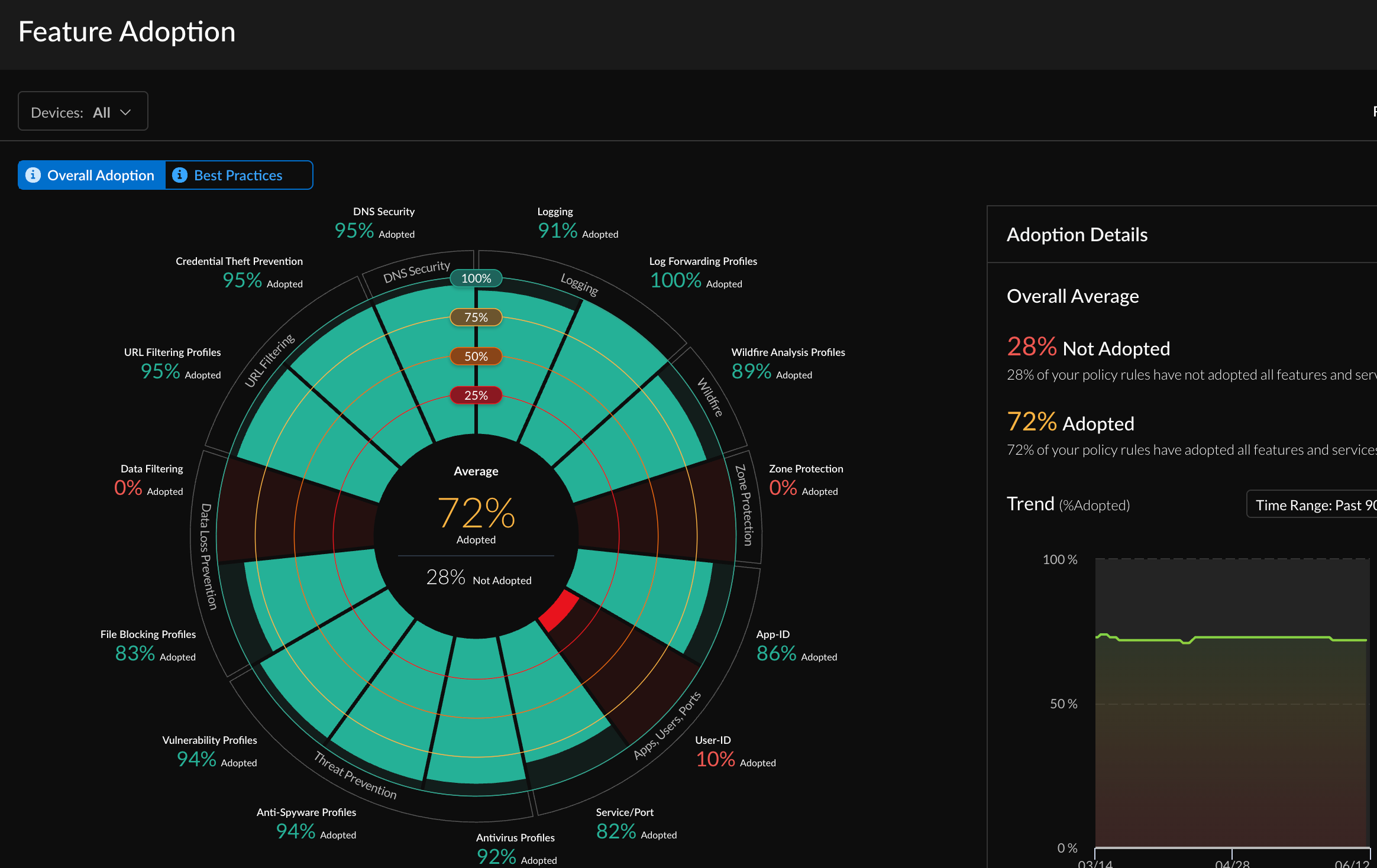
The Feature Adoption dashboard shows you the security
features that you are using in your deployment, and you can use it to identify
gaps in adoption. This helps you make sure that you are getting the
most out of your Palo Alto Networks security subscriptions and firewall
features.
How to use this dashboard
- To focus on the feature adoption for a specific set of firewalls, you can filter the chart based on device group, including Panorama-managed devices. You can also see historical adoption trend charts.
![]()
- When you generate an On-Demand BPA report using a TSF, adoption information from your TSF is reflected on the Feature Adoption dashboard. (PAN-OS 9.1 and above TSFs)
- You can export adoption data in .csv format for use in third-party applications such as Microsoft Excel
Select the section for a feature on the chart to view which policy rules lack that feature.Select a rule to view its details without needing to leave the app.Identify gaps in adoption
This dashboard shows where your security policy is strong and where there are gaps in capability adoption that you can focus on improving. To gain maximum visibility into traffic and maximum protection against attacks, set goals for security capability adoption and use the following recommendations as a best practice baseline. Assess your current posture against the baseline to identify gaps in security policy capability adoption.Adoption Summary helps identify devices, zones, and areas where you can improve security policy capability adoption. You can review adoption information by Device Group, Serial Number & Vsys, Zones, Areas of Architecture, Tags, Rule Details, and Zone Mappings. Filter on Device Group to narrow the scope and identify gaps.In InsightsFeature Adoption, select Overall Adoption to check the adoption rates of the following capabilities. Select Best Practices to see the adoption rates of these capabilities that adhere to Palo Alto Networks best practices. Use this information as gap identification criteria—if the actual adoption rate doesn’t match the recommendations, plan to close the gap:- Apply WildFire Analysis, Antivirus, Anti-Spyware, Vulnerability, and File Blocking profiles to all rules that allow traffic, with a target of 100% or almost 100% adoption. If you don’t apply a profile to an allow rule, ensure that there is a good business reason not to apply the profile.Configuring security profiles on all allow rules enables the firewall to inspect decrypted traffic for threats, regardless of application or service/port. After updating the configuration, you can run the BPA for non-telemetry devices to measure progress and to catch new rules that don’t have security profiles attached.You can apply WildFire profiles to rules without a WildFire license. Coverage is limited to PE files, but this still provides useful visibility into unknown malicious files.
- In the Anti-Spyware profile, apply DNS Sinkhole to all rules to prevent compromised internal hosts from sending DNS queries for malicious and custom domains, to identify and track the potentially compromised hosts, and to avoid gaps in DNS inspection. Enabling DNS Sinkhole protects your network without affecting availability, so you can and should enable it right away.
- Apply URL Filtering and Credential Theft (phishing) Protection to all outbound internet traffic.
In the Adoption Summary’s Apps, Users, Ports summary, check the adoption rates of the following capabilities. Use the recommendations as gap identification criteria—if the actual adoption rate doesn’t match the recommendations, plan to close the gap:- Apply App-ID to as close to 100% of the rules as possible. Apply User-ID to all rules with source zones or address ranges that have a user presence (some zones may not have user sources; for example, sources in data center zones should be servers and not users). Leverage App-ID and User-ID to create policies that allow appropriate users to sanctioned (and tolerated) applications. Explicitly block malicious and unwanted applications.
- Target 100% or close to 100% service/port adoption—don’t allow applications on non-standard ports unless there’s a good business reason for it.
In the Adoption Summary’s Logging summary, check the adoption rates of the following capabilities. Use the recommendations as gap identification criteria—if the actual adoption rate doesn’t match the recommendations, plan to close the gap:- Target at or close to 100% adoption for Logging and Log Forwarding.
- Configure Zone protection profiles on all zones.
In summary:FeatureAdoption GoalWildFire As close to 100% of Security policy rules as possible Antivirus As close to 100% of Security policy rules as possible Anti-Spyware As close to 100% of Security policy rules as possible Vulnerability As close to 100% of Security policy rules as possible File Blocking As close to 100% of Security policy rules as possible URL Filtering and Credential Theft All outbound internet traffic App-ID As close to 100% of Security policy rules as possible User-ID All rules with source zones or address ranges that have a user presence Service/port As close to 100% of Security policy rules as possible Logging As close to 100% of Security policy rules as possible Log Forwarding As close to 100% of Security policy rules as possible Zone protection All zones