Cloud NGFW for Azure
Update your Panorama Registration
Table of Contents
Expand All
|
Collapse All
Cloud NGFW for Azure Docs
Update your Panorama Registration
Learn how to simplify your Cloud NGFW for Azure Panorama deployment.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
You can modify the Panorama parameters after you have registered the Cloud NGFW with
Panorama. You generate a new registration string in Panorama and update your Cloud
NGFW resource when you make the following changes:
- Migrate a Cloud NGFW resource from one Panorama to another Panorama.
- Add a log collector to Panorama after deploying the Cloud NGFW resource.
- Move the Cloud NGFW to a different cloud device group.
- Modify the Panorama IP address after deploying the Cloud NGFW resource.
- Enable or disable Strata Logging Service (SLS) for an existing Panorama-managed firewall.
- Handle changes in the Panorama serial number or its association with SLS.
Consider the following:
- The update process for SLS configuration changes does not involve a rolling upgrade of the firewall instances. This allows for seamless updates without traffic interruption.
- Palo Alto Networks recommends that you don’t push any configuration changes in Panorama to ensure consistency across all Cloud NGFW resources during the update process.
- The feature currently supports updates to the Panorama IP address, a cloud device group, a template stack, a log collector, and the Strata Logging Service configuration.
- The update process may take long for deployments containing a large number of firewall instances to ensure thorough validation and a smooth transition.
You can generate a new registration string and update the firewall. Enable SLS
support for existing Panorama-managed firewalls and handle changes in Panorama
serial numbers or its association with SLS, and you can also disable SLS for a
firewall.
When a Cloud NGFW for Azure instance is scaled in, a 72-hour
grace period begins before the device is removed from Panorama.
Requirements
To simplify onboarding with your Cloud NGFW resource, you’ll need the following:
- Panorama versions 10.2, 11.0, 11.1, 11.2 or later.
- Azure plugin for Cloud NGFW version 5.2.2 or greater.
Generate a New Registration String
You’ll need to generate a new Panorama registration string from your Panorama
instance to update your Panorama registration in the Azure Portal by following
these steps:
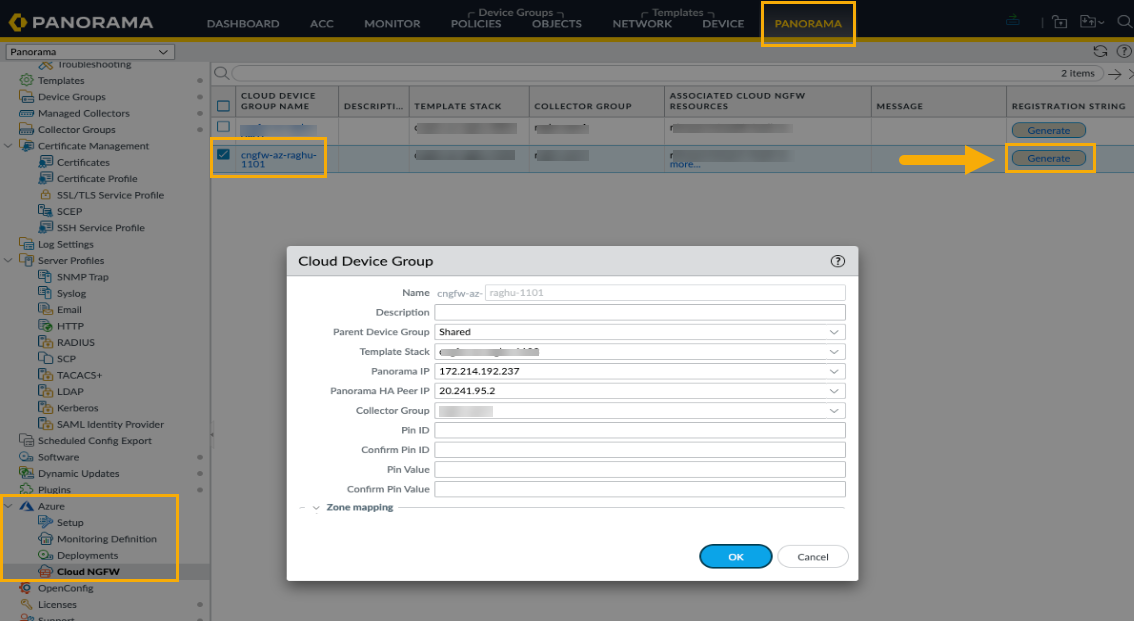
- Log into Panorama.Select the Panorama tab in the upper portion of the web interface.In the Azure plugin section, select Cloud NGFW. Previously created Cloud Device Groups appear if they were established for the Cloud NGFW resource using Azure.Select the Cloud Device Group and make any necessary changes.Click Generate to display the registration string, then commit your changes.
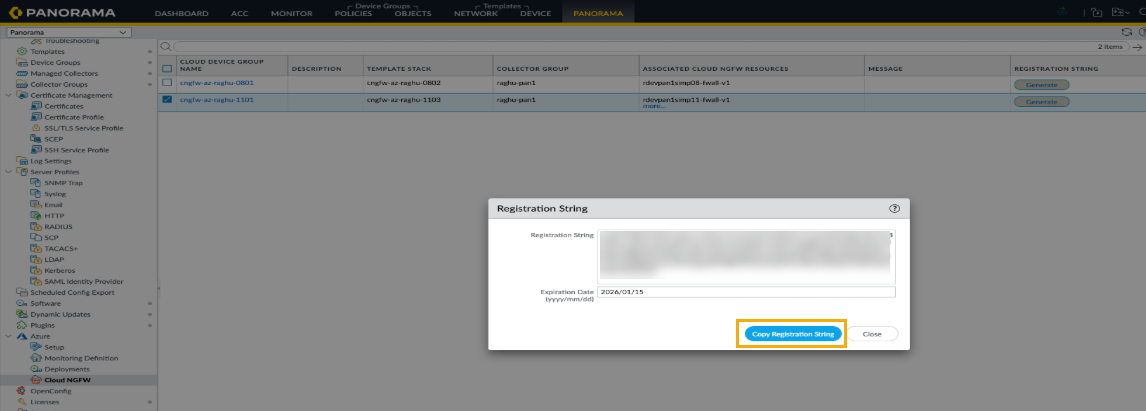
![]() In the Registration String screen, click Copy Registration String.
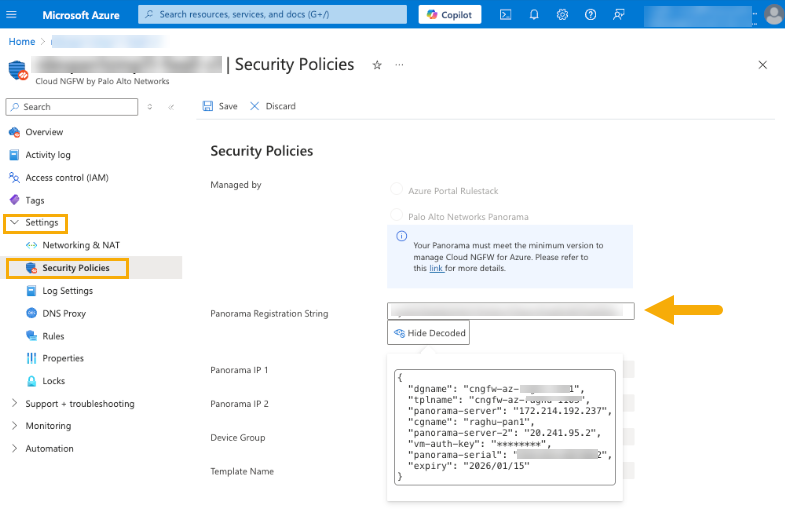
In the Registration String screen, click Copy Registration String.![]() Log in to the Azure Portal.Select the Cloud NGFW, then navigate to Settings > Security Policies to update the generated configuration string.
Log in to the Azure Portal.Select the Cloud NGFW, then navigate to Settings > Security Policies to update the generated configuration string.![]() The system automatically processes the update then creates a dry-run instance to validate the changes before applying them to your firewall instances through a rolling upgrade process.If the dry-run process fails:
The system automatically processes the update then creates a dry-run instance to validate the changes before applying them to your firewall instances through a rolling upgrade process.If the dry-run process fails:- Changes revert to the previous configuration, and any scale-out picks up the previous configuration.
- The Panorama web interface indicates that Health Status is Degraded, and the Provision Status indicates a Accepted or Succeeded.
If the dry run succeeds, the rolling upgrade process for the existing firewall begins:- The Health Status appears as Healthy.
- Incremental firewall resources are picked up by the rolling upgrade process; with 20% of the resources updated. The remaining 80% continue to process traffic.
- If any failures occur during the rolling upgrade process, the Palo Alto Networks support team is alerted.
The following table illustrates the states associated with the Health Status:Config String Update Provision State Health Status Health Reason Accepted Degraded - Config string verification failed - not able to connect to Panorama
- Unable to apply config string to FW - not able to connect to Panorama
Succeeded Healthy Config string successfully applied Generate a New Registration String to Update Firewall for SLS
To enable, disable, or modify the Strata Logging Service (SLS) for an existing firewall, you will need to generate a new Panorama registration string from your Panorama instance and update your Cloud NGFW resource in the Azure Portal.Prerequisites:- You have an existing Panorama-managed Cloud NGFW for Azure.
- You have access to your Panorama appliance and the Azure portal.
To generate a new registration string to update firewall for SLS, do the following:- Log into Panorama and navigate to the appropriate settings to generate a new registration string. This may involve associating or disassociating the Panorama with an SLS instance.Copy the new registration string from Panorama.Log in to the Azure Portal and navigate to your Cloud NGFW resource.Go to Settings > Security Policies.Paste the new registration string into the Panorama Registration String field.Save the changes. The firewall will then be updated with the new SLS configuration. After the update, you can verify the firewall's health status. A healthy status indicates that the SLS configuration has been successfully applied. If there are any configuration issues, such as a mismatch between the Panorama and SLS association, the firewall status will show as Degraded with an error message detailing the issue.
Migrate a Panorama Instance
Use this procedure to migrate one Panorama instance to another Panorama:- Log in to your first Panorama instance.Select Panorama>Setup>Operations and click Save named Panorama configuration snapshot.Select Panorama>Setup>Operations and click Export named Panorama configuration snapshot. Save the file with a .XML extension.Log in to your second Panorama instance.Select Panorama>Setup>Operations and click Import named Panorama configuration snapshot; load the file you previously created in step 3.Select Panorama>Setup>Operations and click Load named Panorama configuration snapshot.Generate the registration string and update the existing firewall.