Cloud NGFW for Azure
View Traffic and Threat Logs in Strata Logging Service
Table of Contents
Expand All
|
Collapse All
Cloud NGFW for Azure Docs
View Traffic and Threat Logs in Strata Logging Service
Learn how to view traffic and threat logs in Strata Logging Service using Cloud NGFW
for Azure.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Strata Logging Service and Panorama licenses
must be procured outside of Cloud NGFW for Azure integration. This integration
does not automatically grant licenses for using the Strata Logging Service
within Panorama.
If you're using Panorama and are not using Strata Logging
Service for log collection, you can forward logs to another entity, however, you
must enable Strata Logging Service in your logging profile.
For information about the log fields, see the Strata Logging Service Schema
Reference: Traffic, Threat, and Decryption.
Important Considerations
For existing customers who have already deployed the Cloud NGFW in Azure and would
like to use Strata Logging Service:
- Upgrade your current Panorama Plugin for Azure to version 5.2.2.
- Follow the instructions noted in this page.
- Generate the registration string from the Panorama Plugin for Azure; contact Palo Alto Networks support to update the registration string to enable the Strata Logging Service.
For new users who are deploying the Cloud NGFW resource and would like to use
the Strata Logging Service, consider the following:
- You must use Panorama to enable log forwarding to the Strata Logging Service.
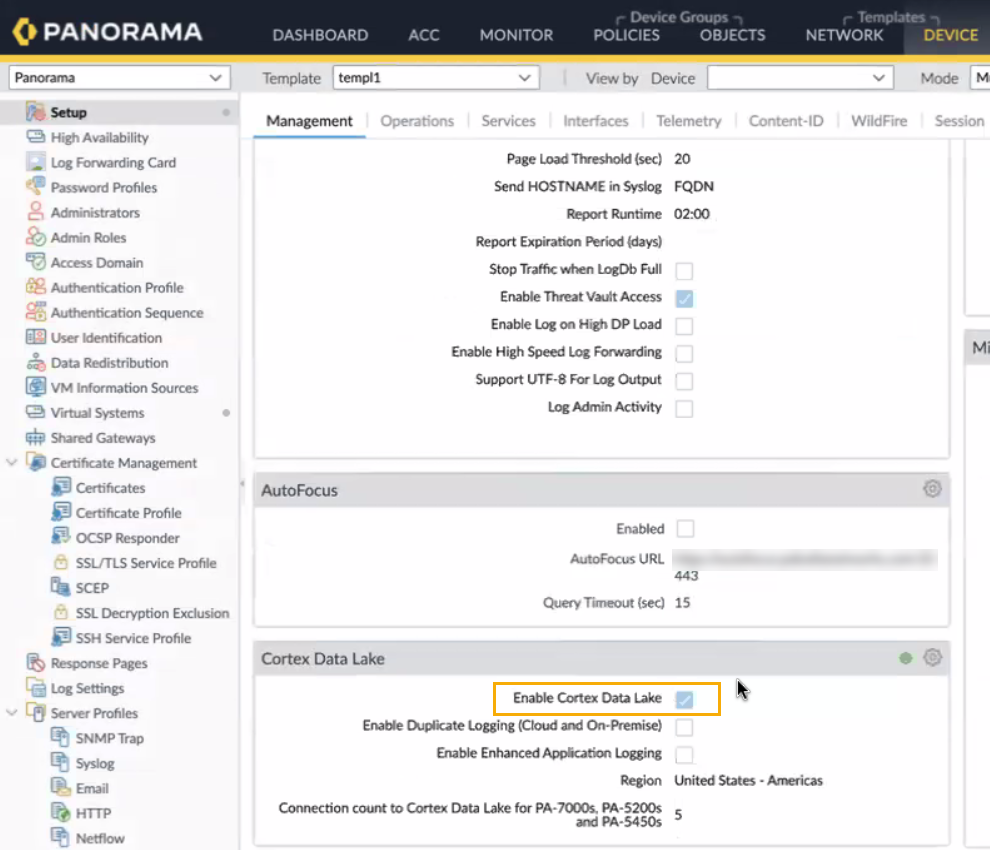
The Panorama web interface continues to show Cortex Data Lake, rather than the updated product name, Strata Logging Service.
![]()
- You must use the Panorama for Azure plugin version 5.2.2 (or later).
- If your Panorama is setup in a HA pair, both Panorama serial numbers should be registered to the same CSP account, and should also be associated with the same Strata Logging Service.
To use Strata Logging Service with Cloud NGFW for Azure:
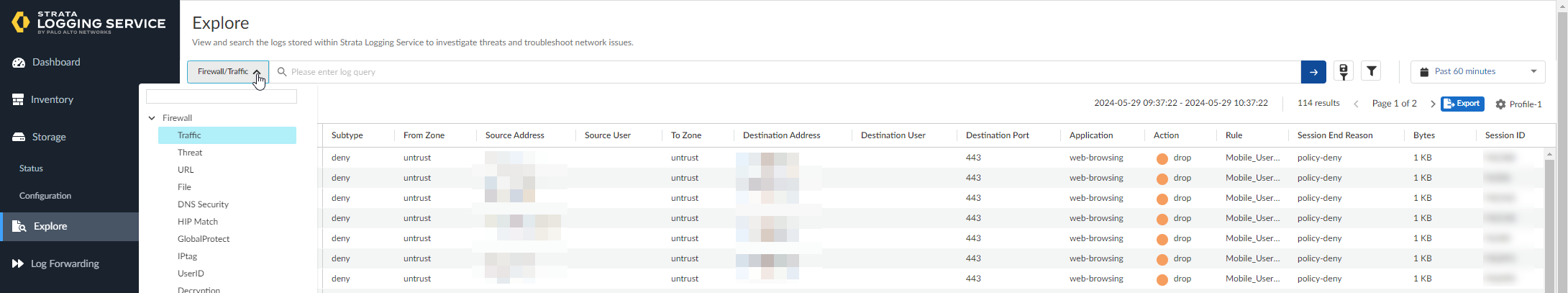
- Log in to your Strata Logging Service instance.Select Explore.
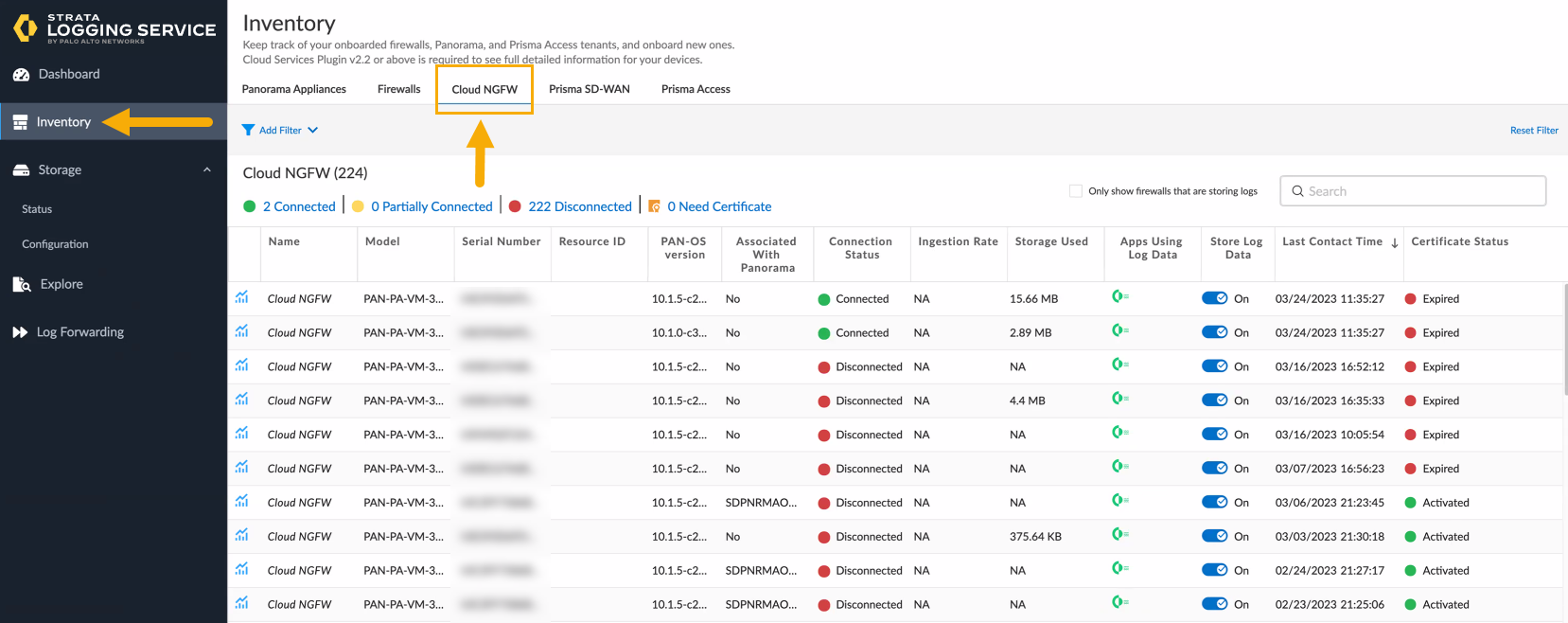
![]() From the query drop-down, you can select the type of logs. Each page displays 100 logs. However, you can use the Strata Logging Service Queries to refine the information displayed.Select Inventory to display information about onboarded firewalls.In the Inventory page, select Cloud NGFW.
From the query drop-down, you can select the type of logs. Each page displays 100 logs. However, you can use the Strata Logging Service Queries to refine the information displayed.Select Inventory to display information about onboarded firewalls.In the Inventory page, select Cloud NGFW.![]()
Forward Logs to Strata Logging Service
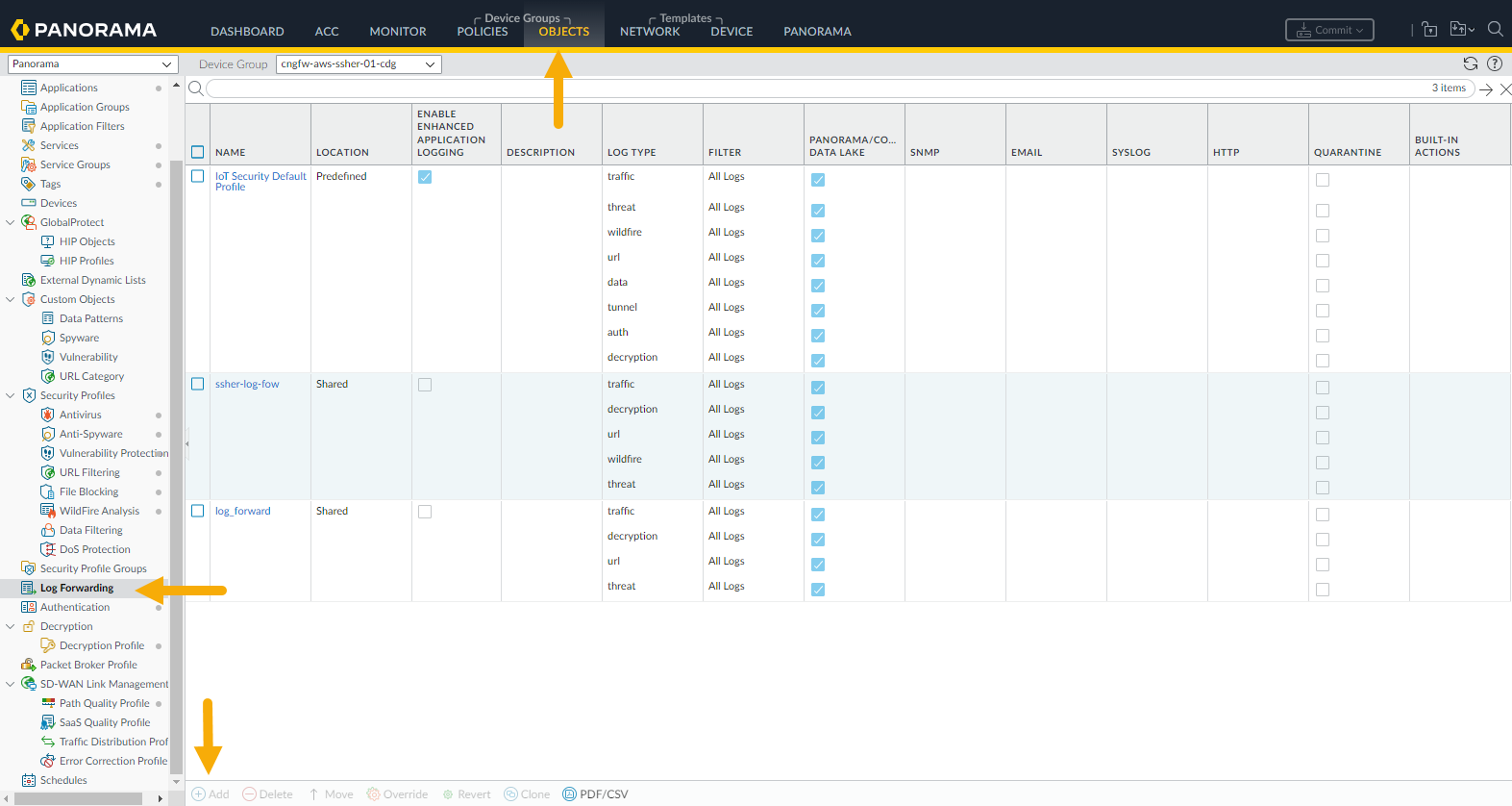
To forward logs to Strata Logging Service:- In the Panorama console, select Objects under Device Groups.Select Log Forwarding.Click Add to create a new log forwarding match list profile.
![]() In the Log Forwarding Profile Match List screen, specify a name for the log.Select a Log Type from the drop-down.Select Panorama/Strata Logging Service as the Forward Method.
In the Log Forwarding Profile Match List screen, specify a name for the log.Select a Log Type from the drop-down.Select Panorama/Strata Logging Service as the Forward Method.![]() Click OK.Commit and push your change.
Click OK.Commit and push your change.Forward Logs without Strata Logging Service
If you're using Panorama and are not using Strata Logging Service for log collection, you can forward logs to another entity.- In the Panorama console, select Objects under Device Groups.Select Log Forwarding.Click Add to create a new log forwarding match list profile.In the Log Forwarding Profile Match List screen, specify a name for the log.Select a Log Type from the drop-down.Enable Strata Logging Service in your logging profile even if you don't intend to send logs directly to it.Click OK.Commit and push your change.